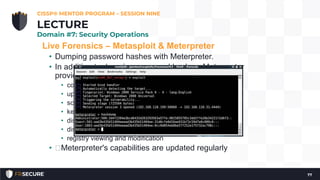
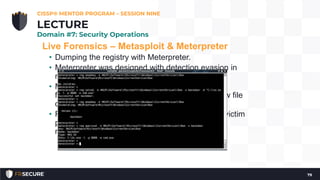
This document summarizes a CISSP mentor program session from May 13, 2019. It discusses assessing access control and software testing methods. The session covers penetration testing methodology and tools, vulnerability testing, and security assessments. Penetration testing involves planning, reconnaissance, scanning, vulnerability assessment, exploitation, and reporting. Vulnerability scanning checks for issues like missing patches and configuration errors. Security assessments take a holistic approach to evaluating multiple controls across domains.