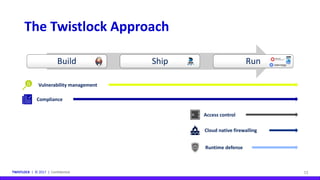
This document discusses shift-left security, which involves moving security practices earlier into the software development lifecycle to proactively address risks rather than reactively. It notes that only 20% of organizations consistently integrate security early in DevOps processes. Shift-left security is important because traditional security teams cannot keep up with development speeds. The document outlines how to implement shift-left security through automating security practices, using control gates, and learning from production environments. It argues containers help shift security left through their minimal, declarative, and predictable nature which simplifies security requirements and policy automation.