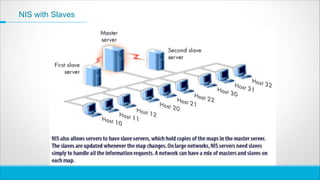
The document discusses the concepts and methods for sharing system files across networked servers, focusing on Unix and Linux environments. It examines different approaches such as Network File System (NFS), push and pull systems for configuration file distribution, and highlights the lightweight directory access protocol (LDAP) and network information service (NIS) as tools for managing user data and configurations. Additionally, it underscores the advantages and limitations of each system, including security considerations and best practices for implementation.