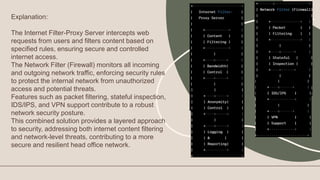
Here is a suggested network design with key services for the given scenario:
Firewall: Cisco ASA or Fortinet FortiGate
- Provides network security and controls inbound/outbound traffic
- Stateful packet inspection, intrusion prevention, VPN support
Central Authentication Server: Windows Active Directory
- Manages user authentication, authorization and accounts centrally
- Integrates with other servers and services for single sign-on
Telephony Server: Asterisk or FreePBX
- Hosts VoIP phone system functionality
- Provides features like call routing, conferencing, voicemail
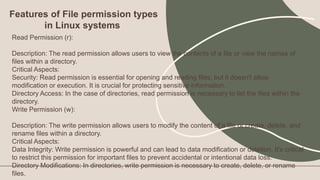
File Server: Windows Server
- Shares files and storage on the network
- Provides features like permissions, backup, redundancy