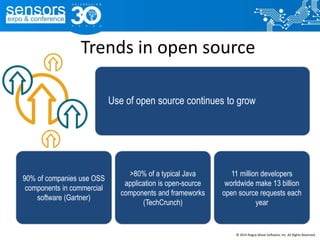
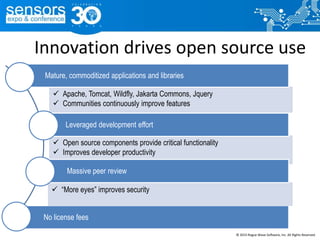
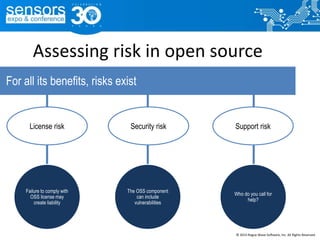
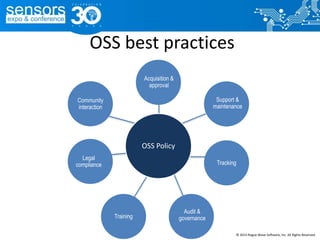
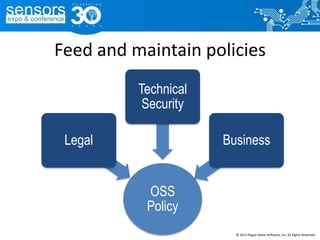
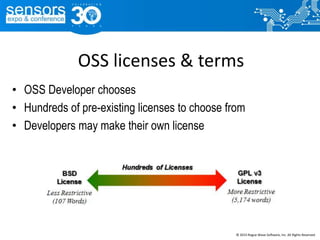
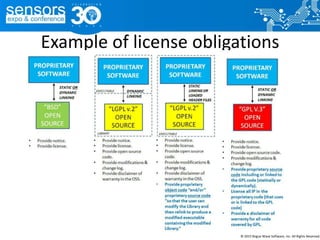
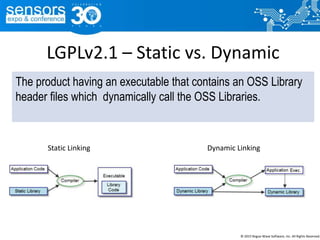
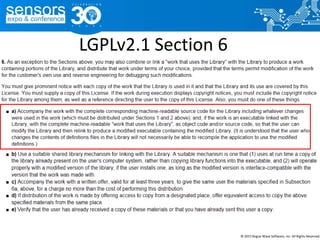
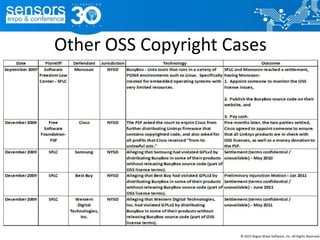
The document outlines best practices for utilizing open source software (OSS) from a legal perspective, emphasizing the growing adoption of OSS in commercial applications and the associated risks, such as license compliance and security vulnerabilities. It discusses the importance of establishing OSS policies, conducting audits for license identification, and understanding legal obligations linked to various OSS licenses. Key recommendations include developing an OSS process, managing risks effectively, and ensuring legal compliance while leveraging OSS technology.