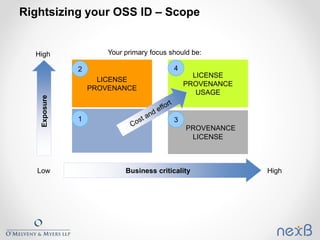
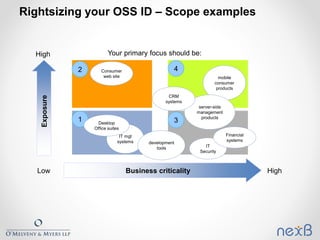
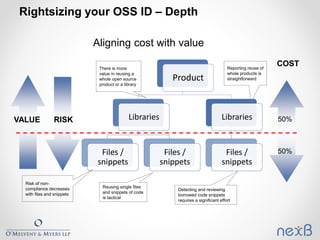
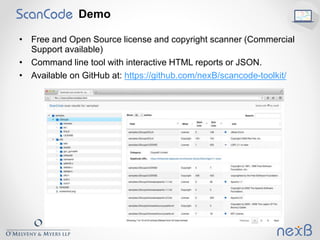
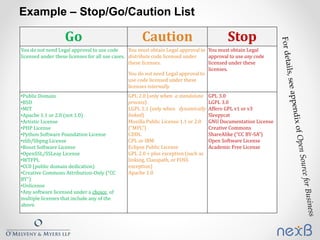
The document outlines best practices for identifying and managing open source software (OSS) components in organizations, emphasizing the need for compliance with various licenses. It details methods for creating inventories, assessing risks, and resolving legal concerns while navigating the complexities of OSS licensing. Additionally, it reviews tools and techniques for effective OSS identification and suggests strategies for rightsizing the identification process based on business criticality and exposure.








![How does Scanning work? [2]
High confidence for identification with scanning
• Evidence in the code itself is primary
• Will not detect two cases:
o Copyright or license notices intentionally removed (rare)
o Snippets where developer did not provide comments or clues about origin of the
snippet
Interpretation typically required to:
• Conclude overall license at component level when files have
different notices
• Research clues
The quality of identification depends on who interprets the data -
can often be performed by a developer who understands the
codebase](https://image.slidesharecdn.com/rightsizingopensourcesoftwareidentification-nexbommwebinarfinal-150915213005-lva1-app6891/85/Rightsizing-Open-Source-Software-Identification-12-320.jpg)

![How does Matching work? [2]
All matches except an exact or string match at the package or
library level typically requires interpretation of the matching
pattern
The finer the matching (e.g.. snippets), the higher the risk of
irrelevant matches (false matches)
Code can be generated by tools, leading to fake similarities
Snippet matches typically require extensive (and costly) human
review
• Commonly re-used code may have hundreds of matches (or more)
• Snippet matches need to be evaluated in context of the type of code
and the domain to determine most likely match](https://image.slidesharecdn.com/rightsizingopensourcesoftwareidentification-nexbommwebinarfinal-150915213005-lva1-app6891/85/Rightsizing-Open-Source-Software-Identification-14-320.jpg)
![How does Matching work? [3]
More coarse-grained matching has a risk of missing some
detection (false positives)
The quality of identification depends on:
• Who interprets the matches
• The quality of the origin and license data in the OSS repository used
to create the OSS index. Bigger is not always better.](https://image.slidesharecdn.com/rightsizingopensourcesoftwareidentification-nexbommwebinarfinal-150915213005-lva1-app6891/85/Rightsizing-Open-Source-Software-Identification-15-320.jpg)