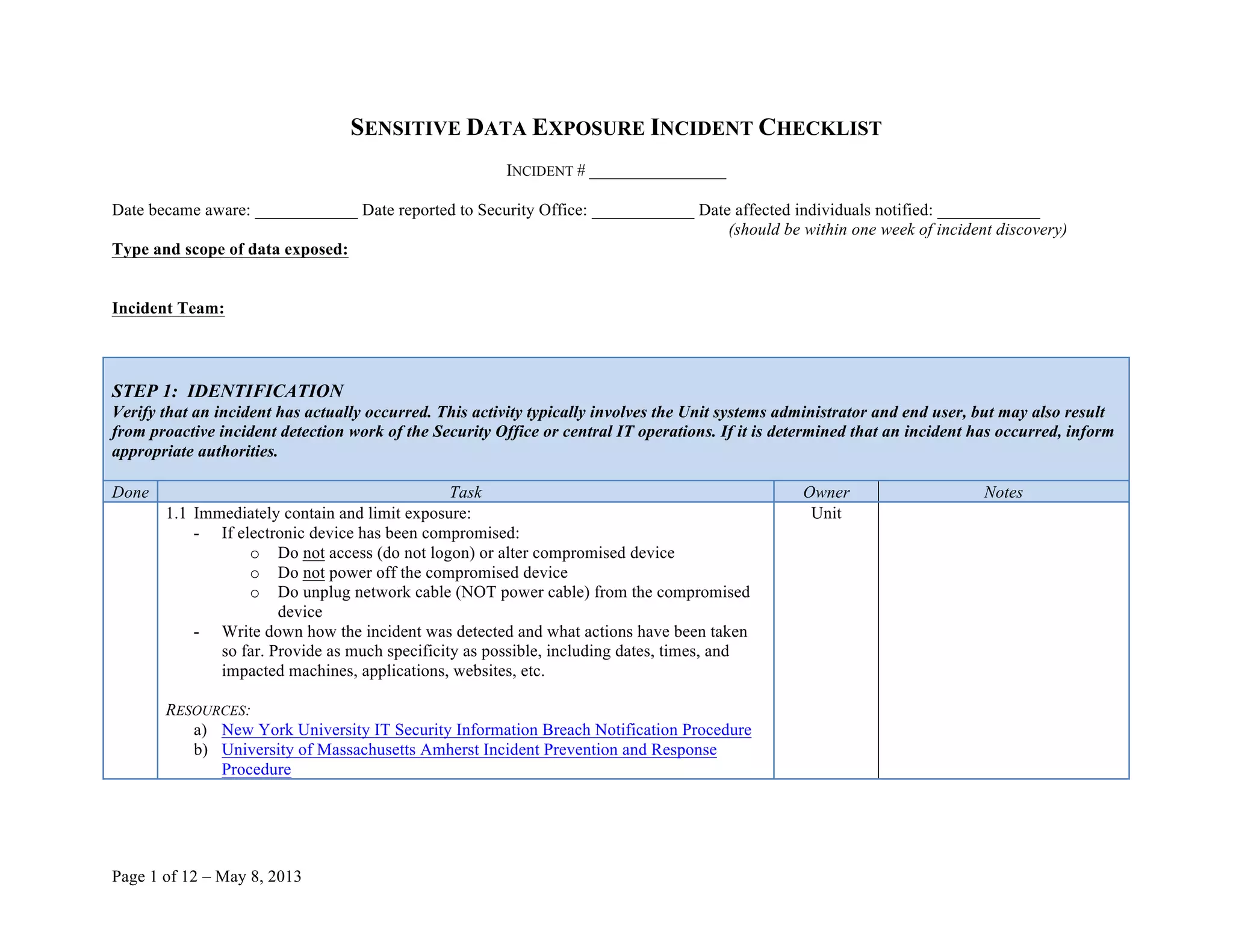
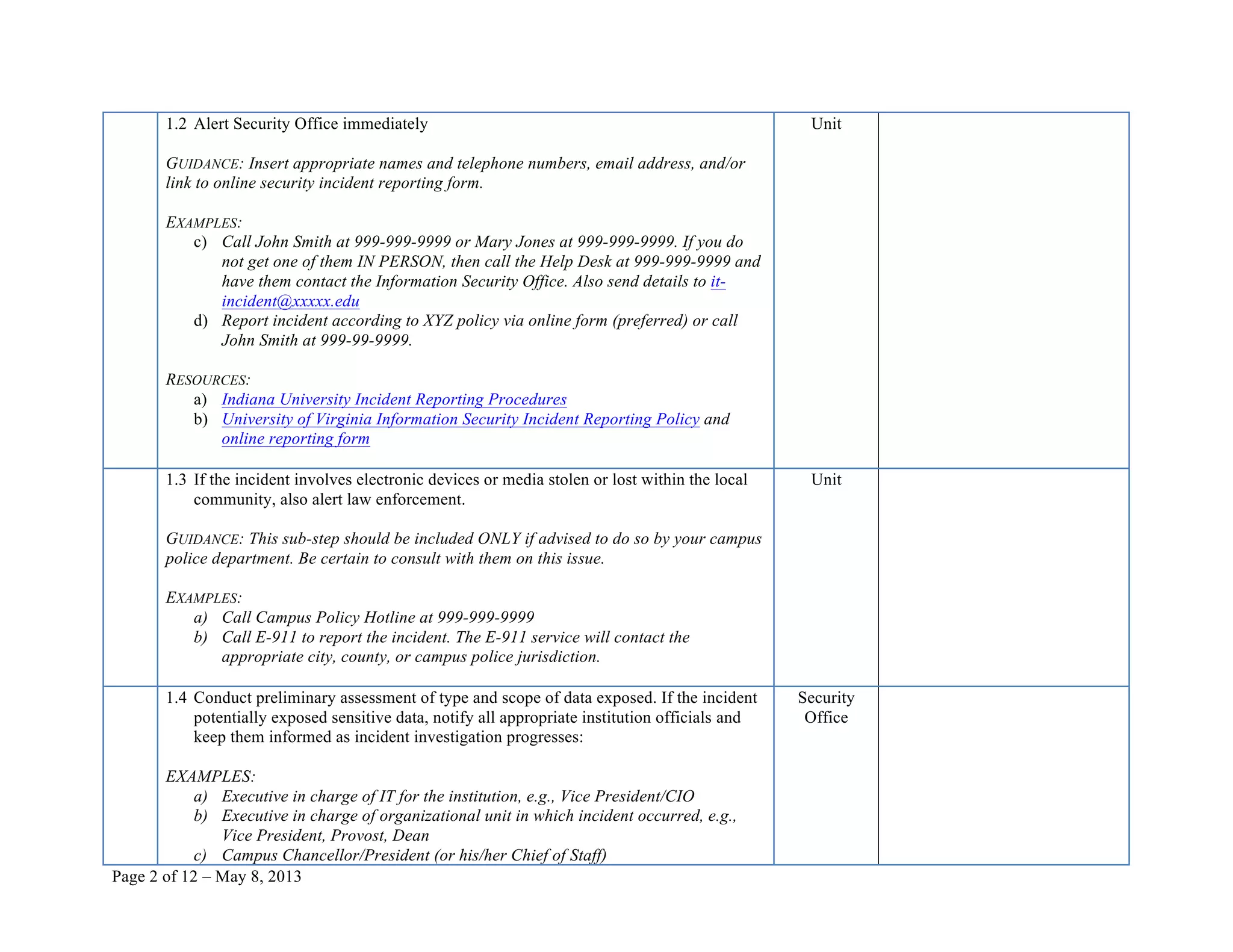
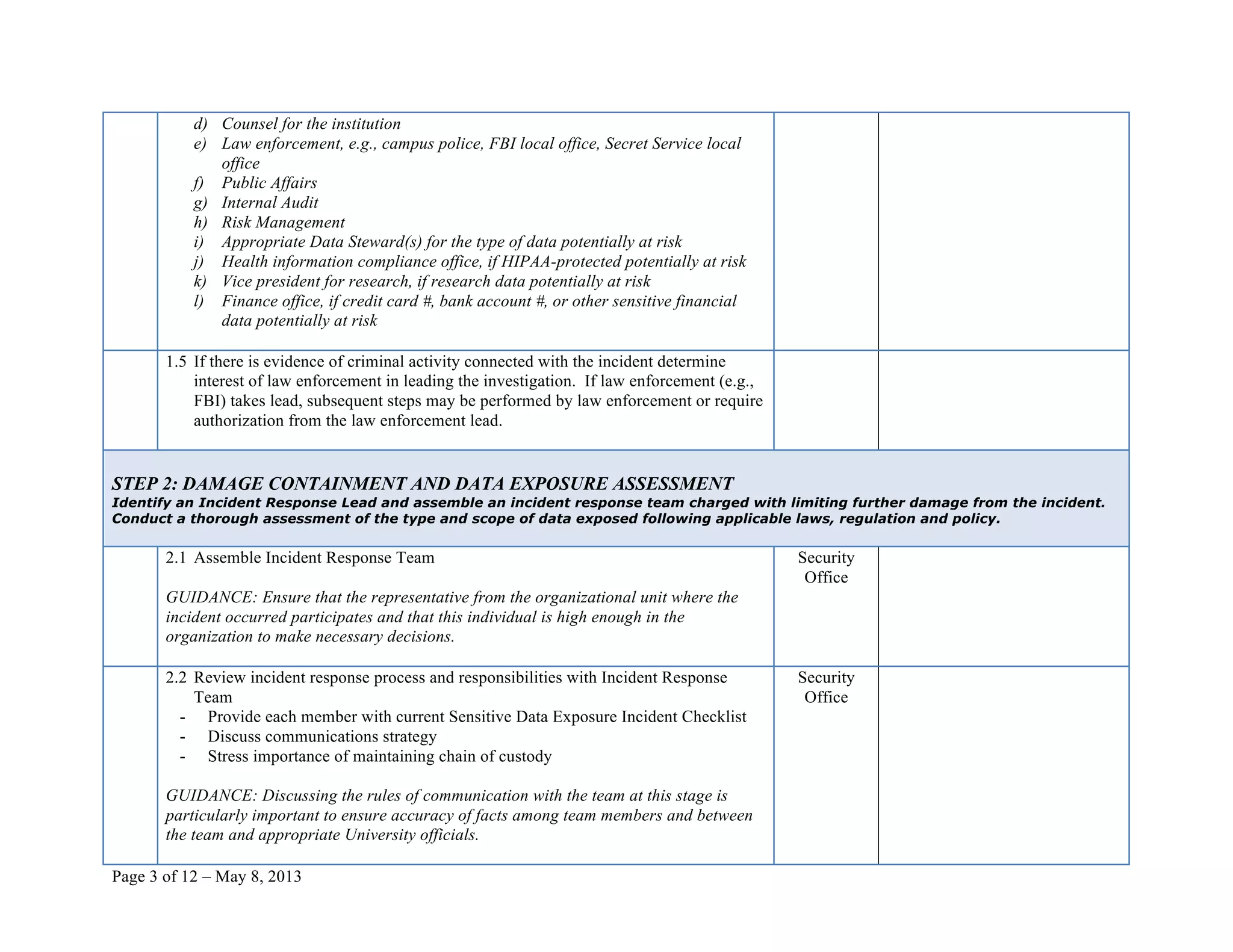
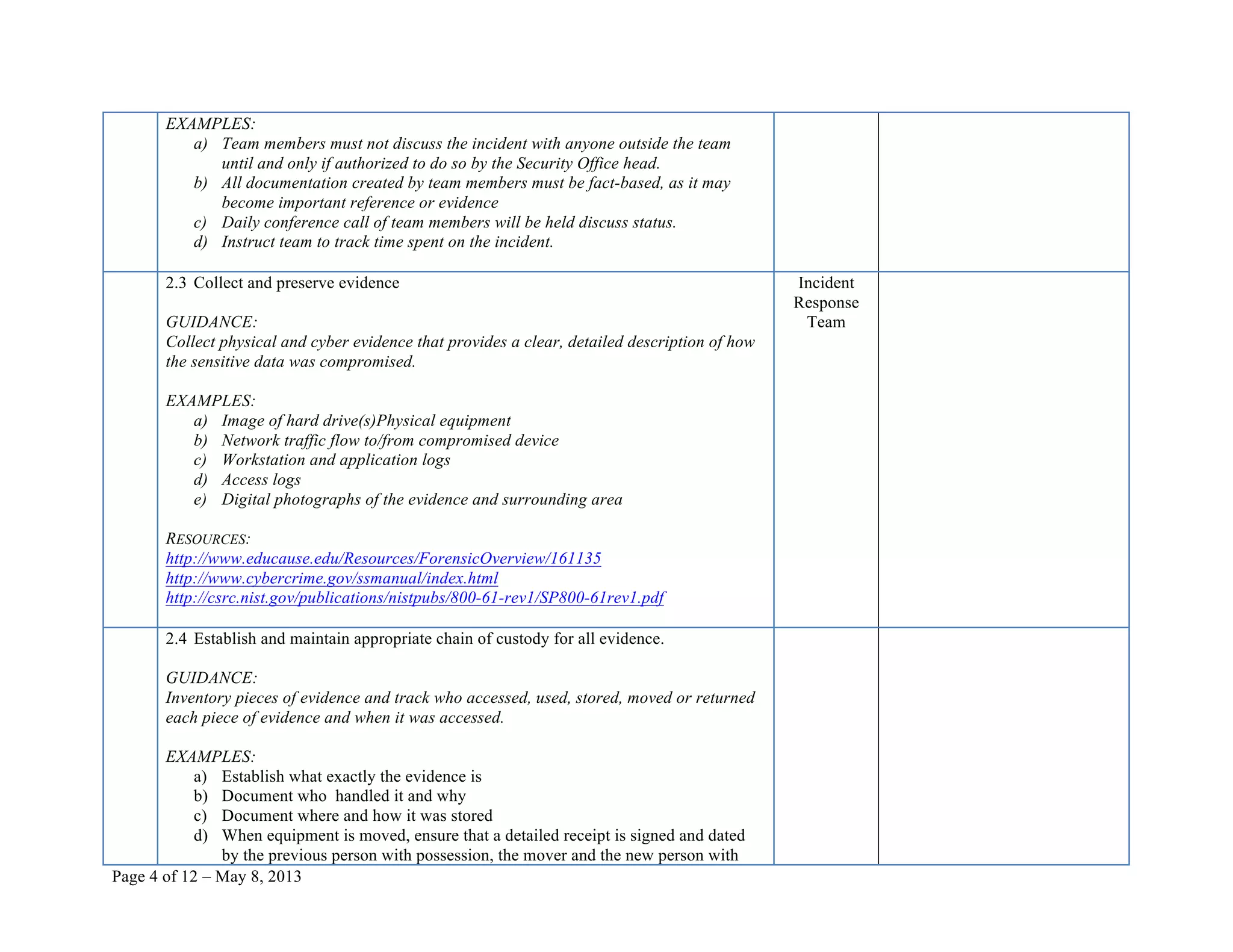
This document provides a checklist for responding to a sensitive data exposure incident with 12 steps. It details actions to identify and contain the incident, assess the damage and data exposure, eradicate vulnerabilities and recover systems, notify affected individuals, and follow up. The checklist contains over 100 sub-steps and references resources to help guide the incident response process.