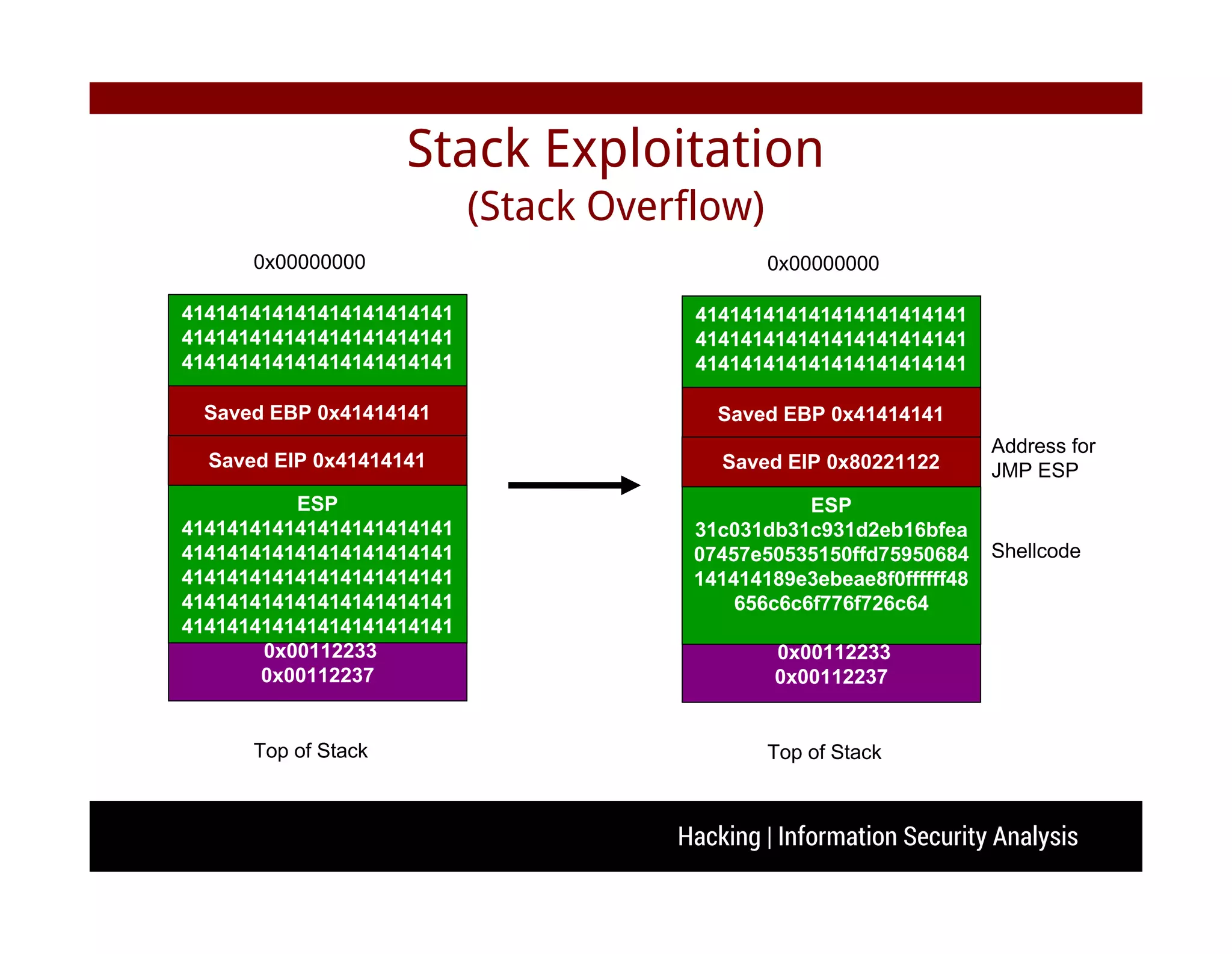
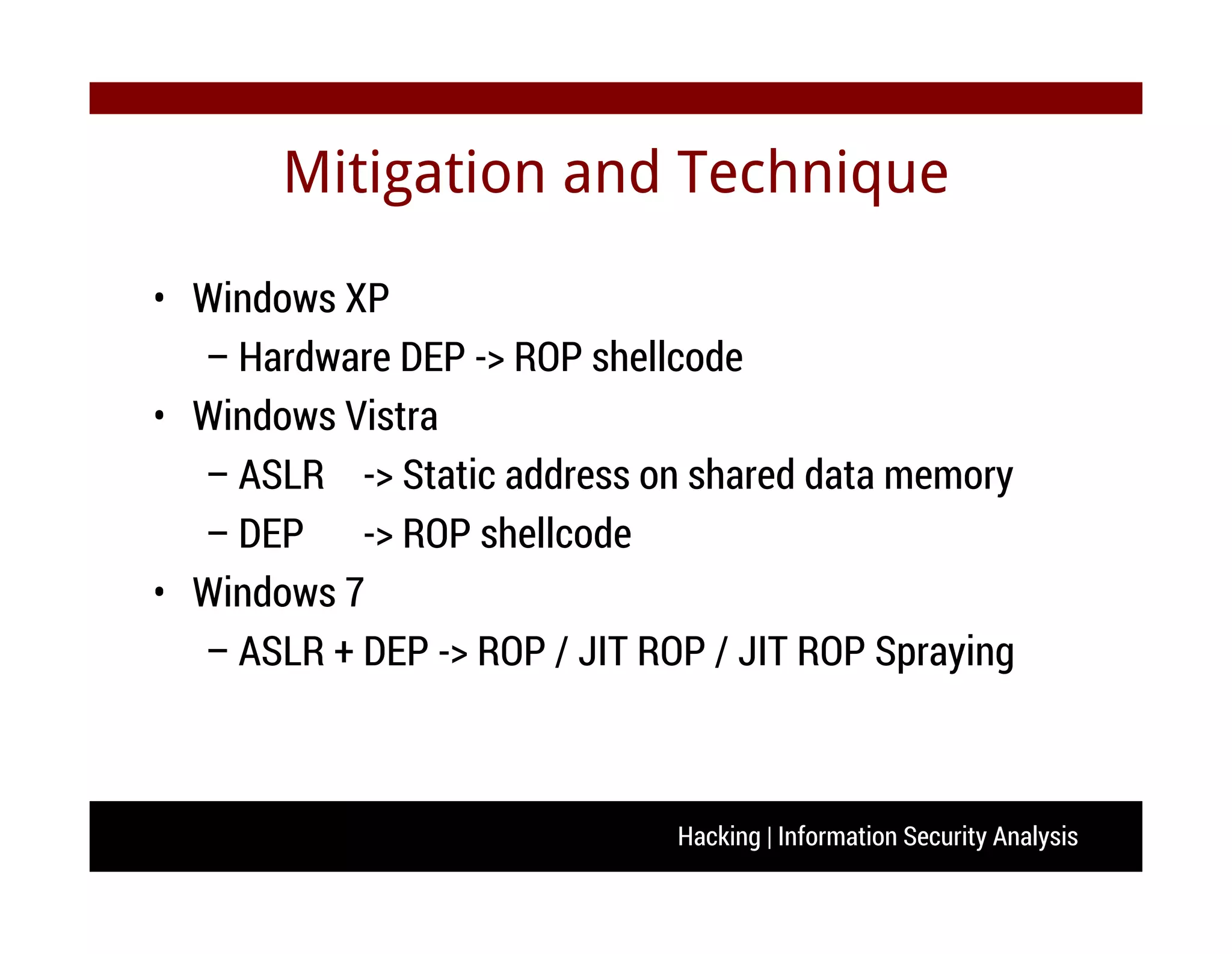
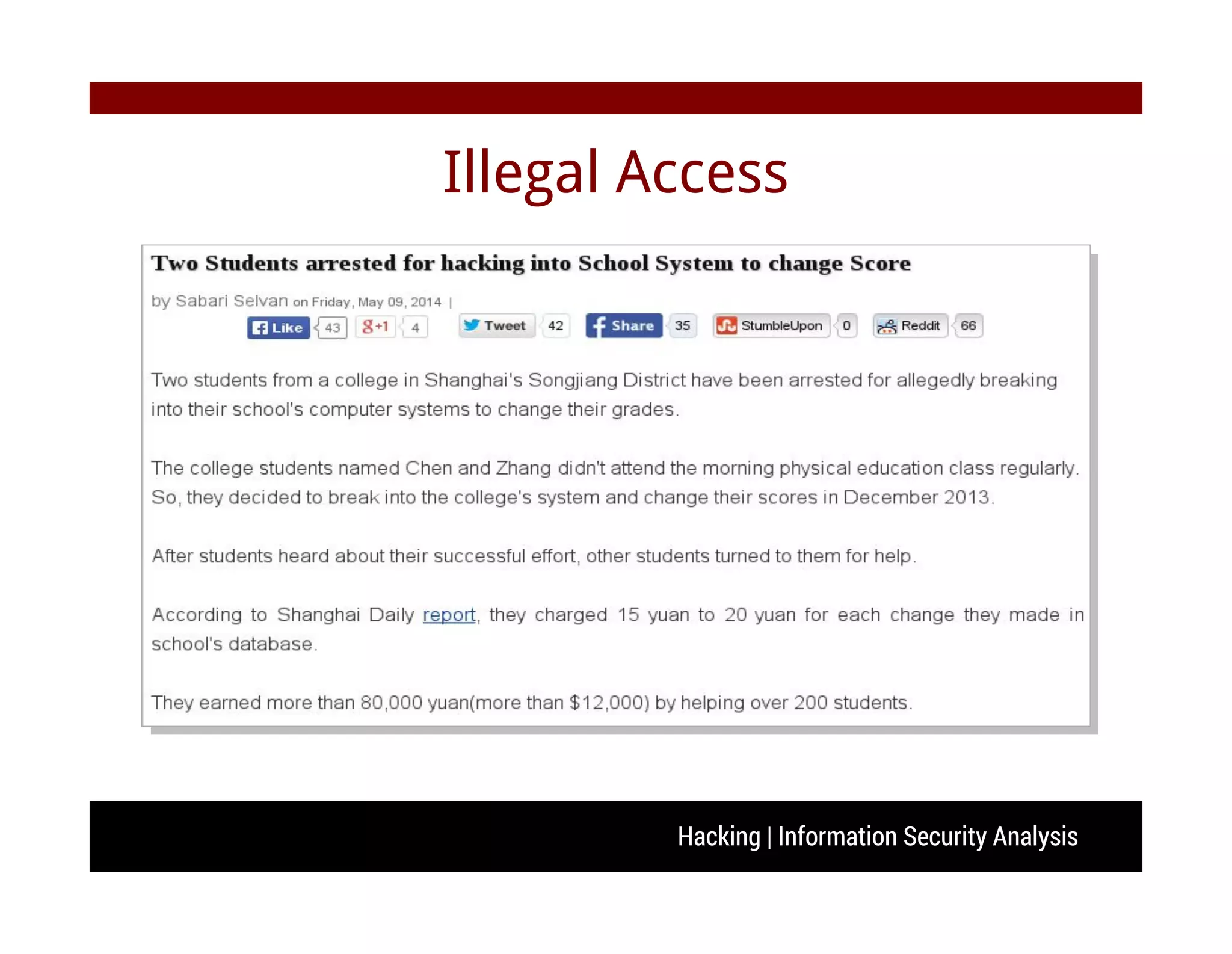
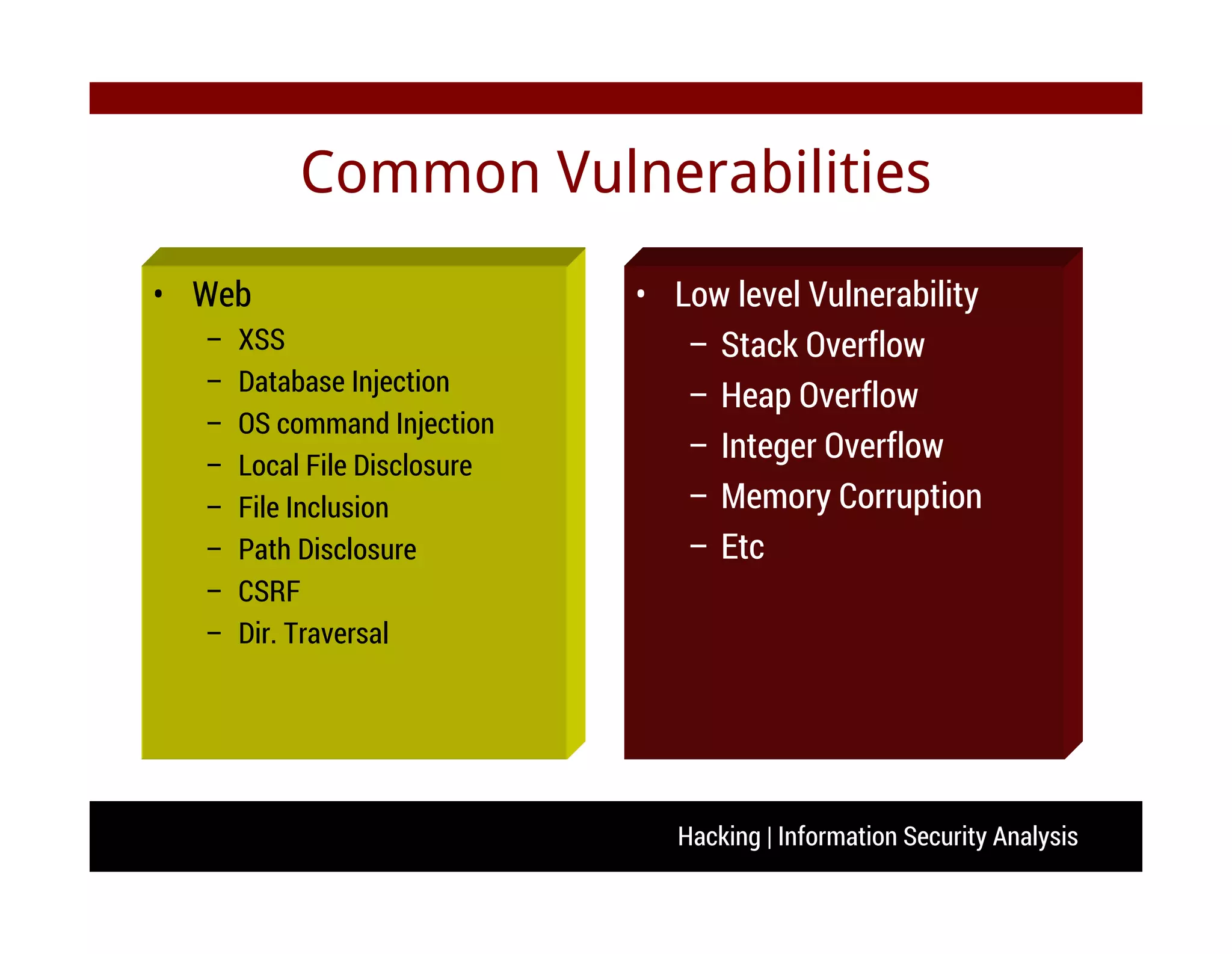
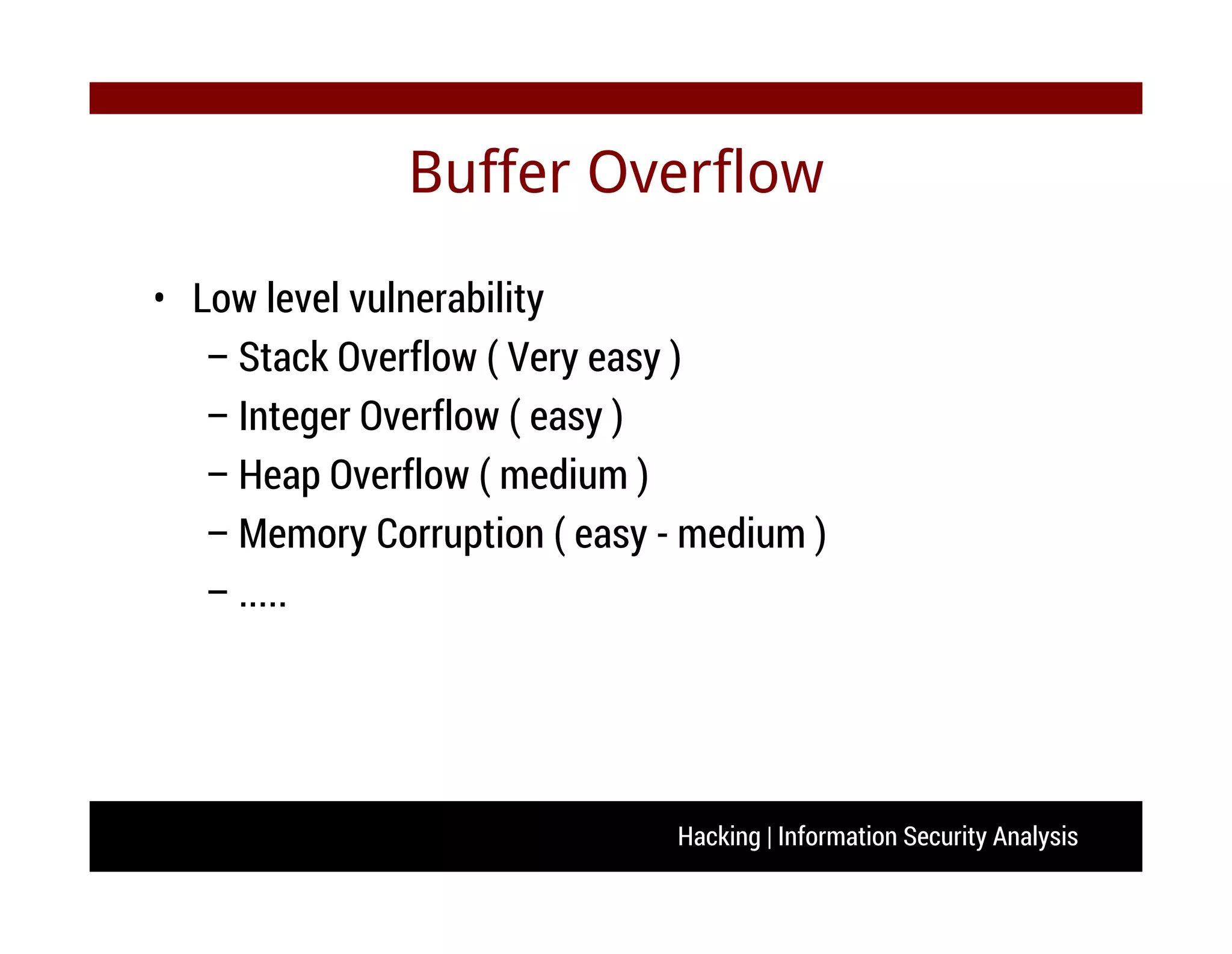
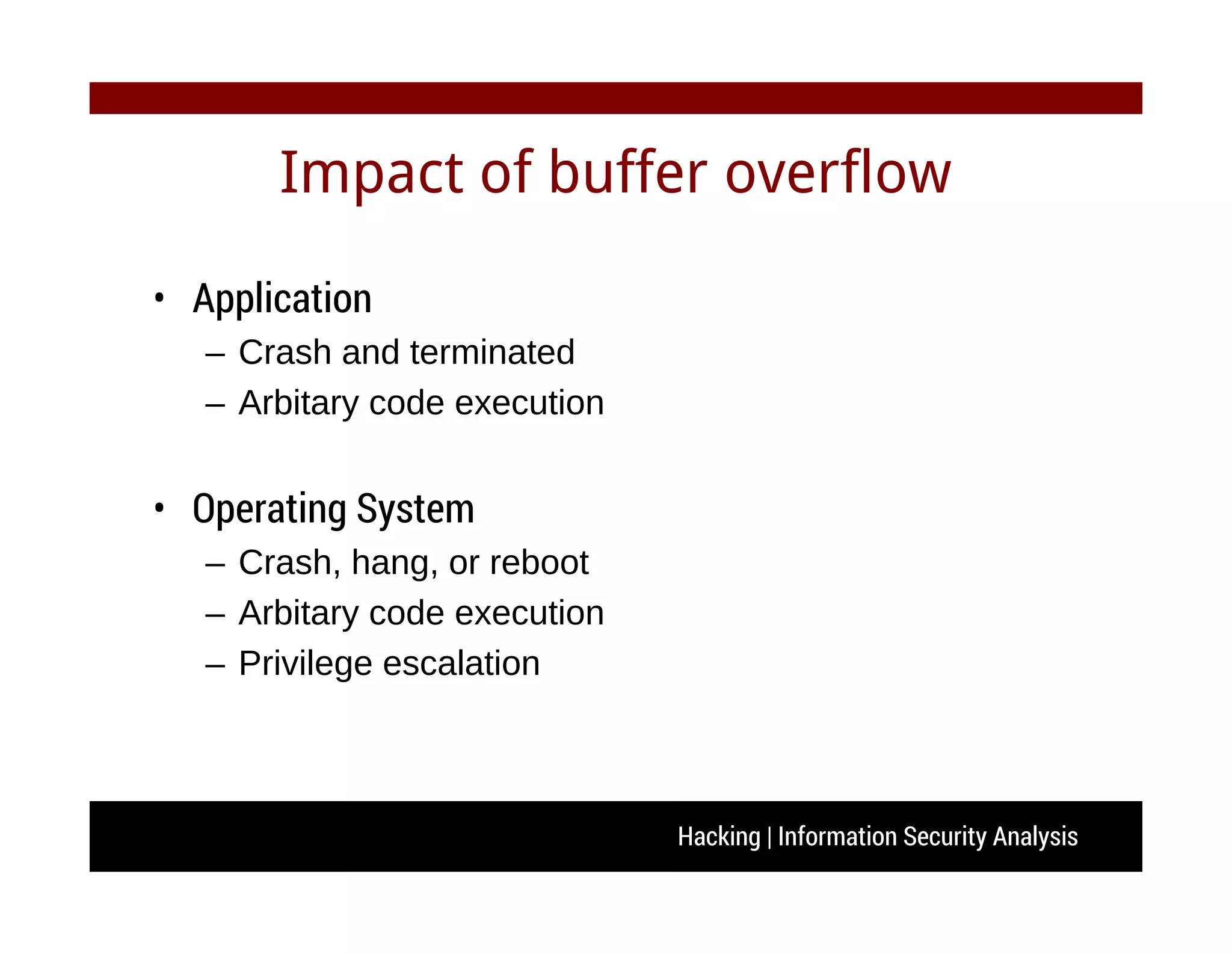
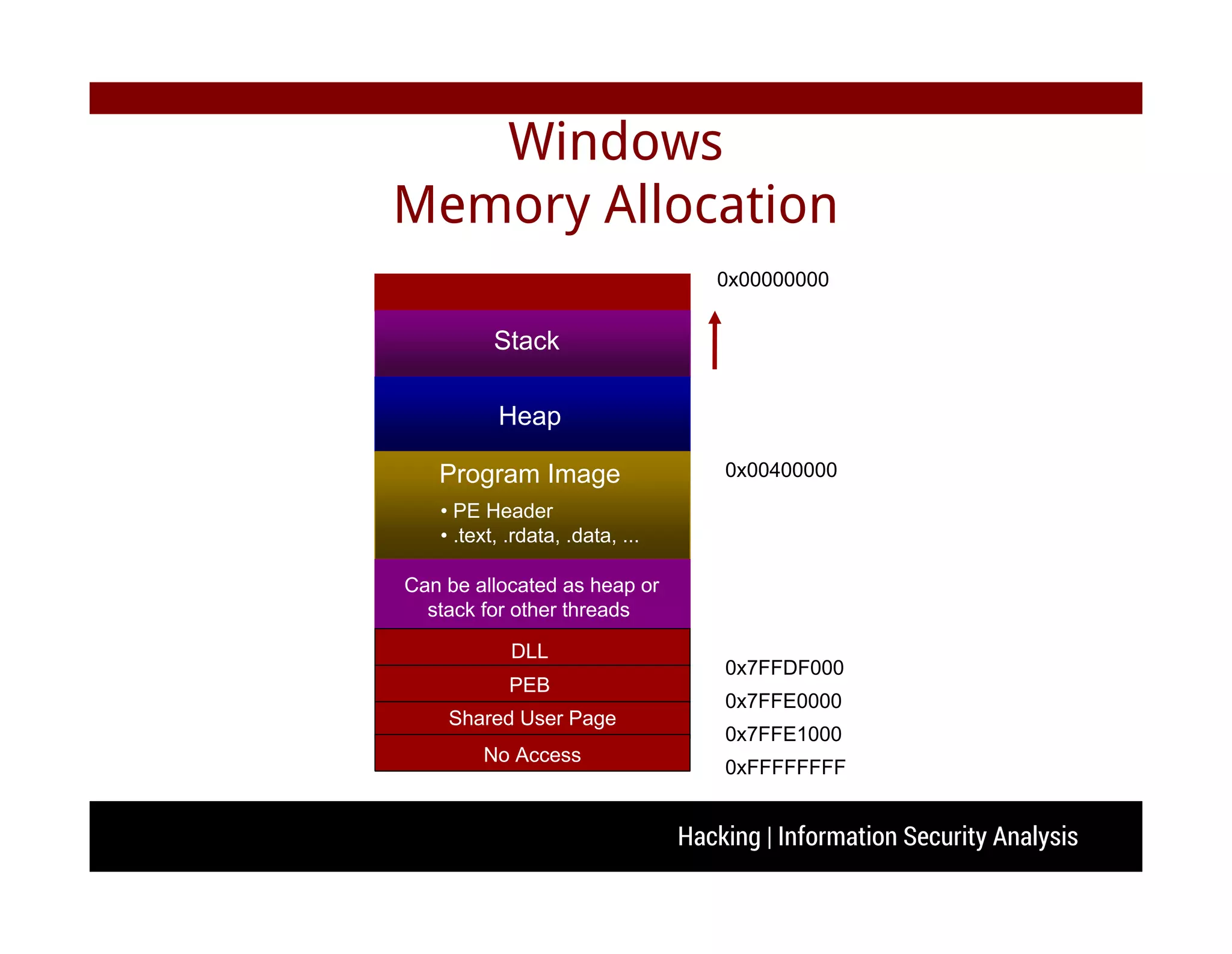
The document discusses hacking and information security analysis. It covers various hacking techniques like cyber spying, fraud/forgery, and illegal access. It then discusses common vulnerabilities like buffer overflows, SQL injections, and cross-site scripting attacks. The document provides examples of stack-based buffer overflows and how they can be exploited to hijack a program's execution flow and potentially execute arbitrary code. It also discusses mitigation techniques used by modern operating systems and counter-techniques employed by hackers.





![Hacking | Information Security Analysis
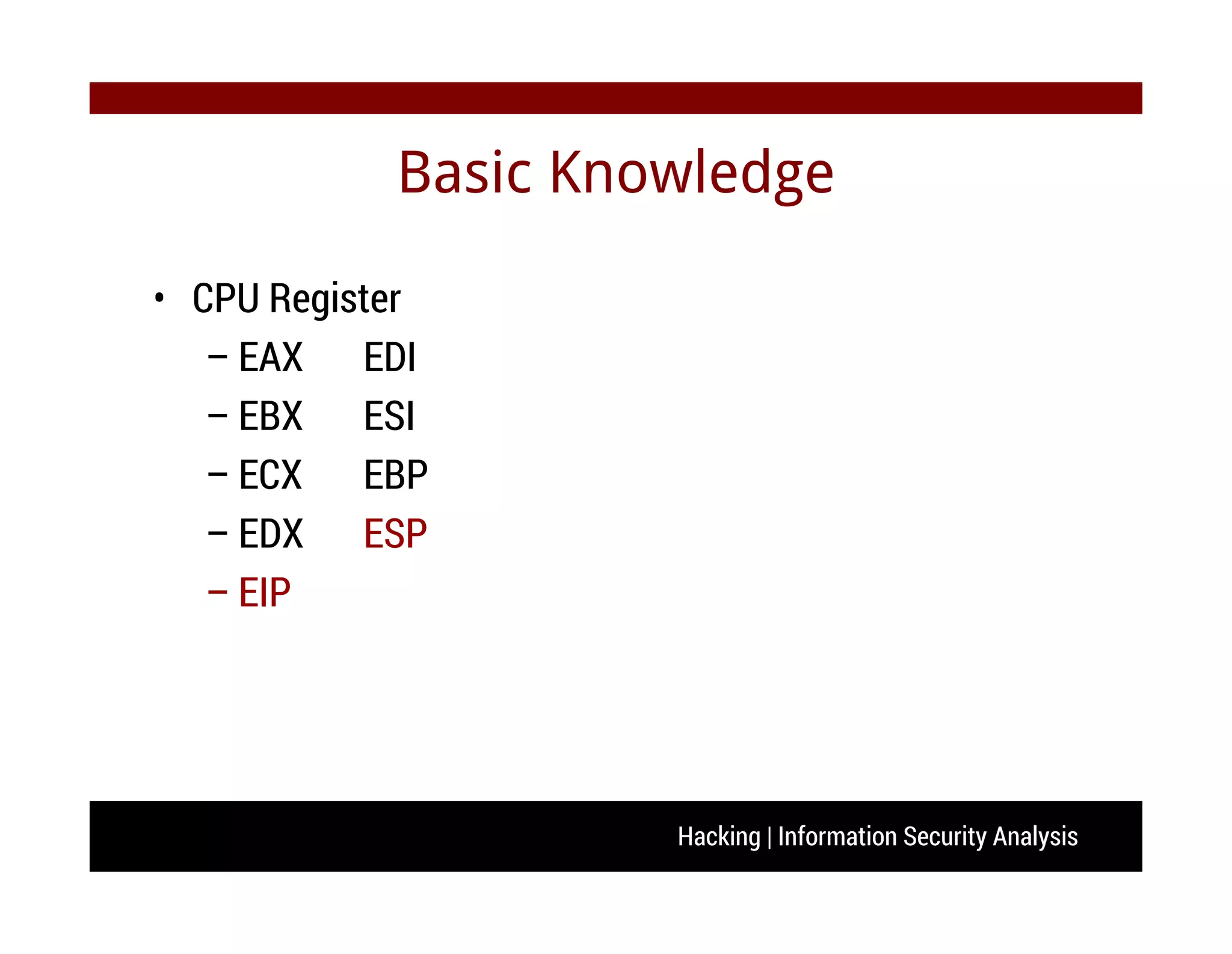
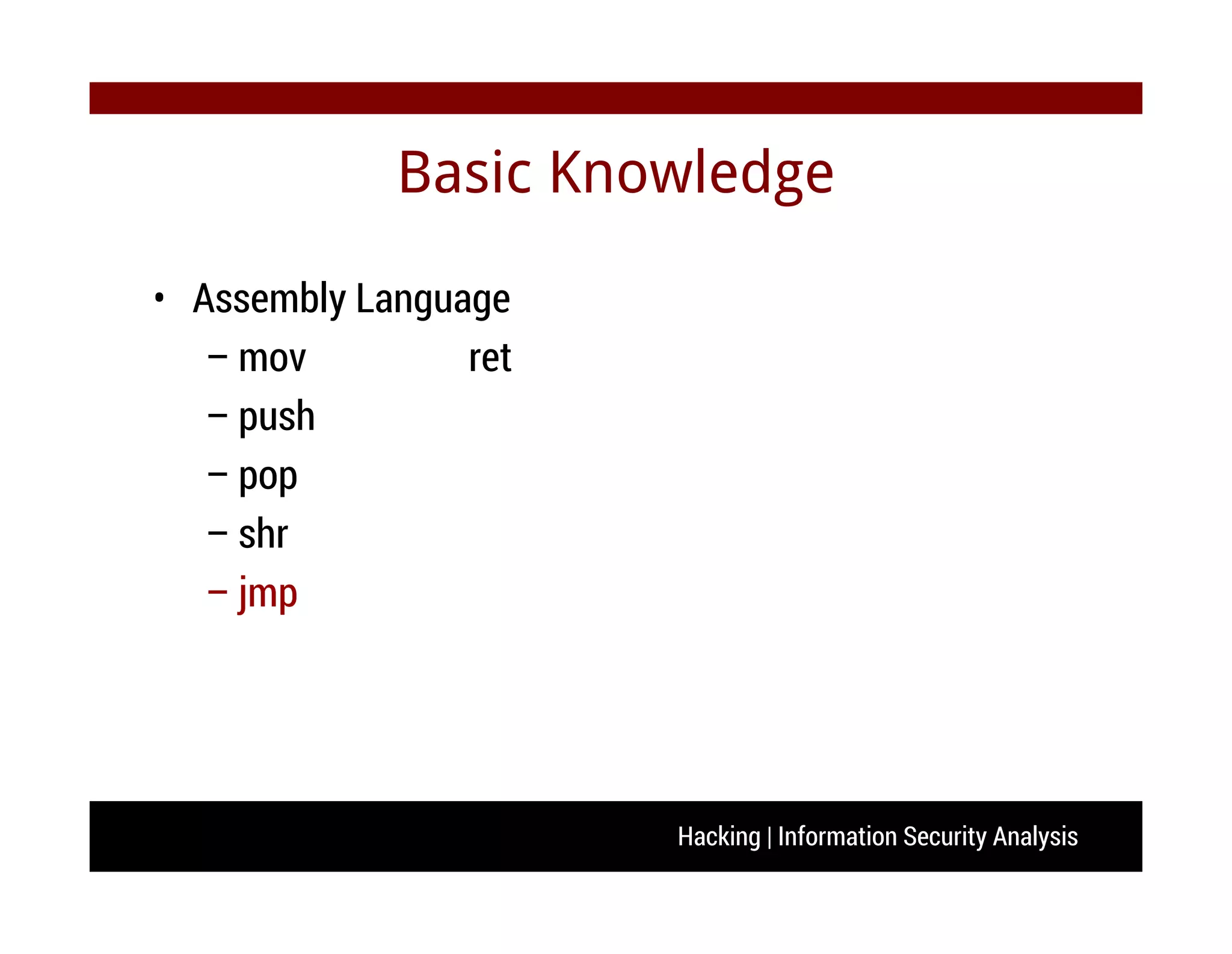
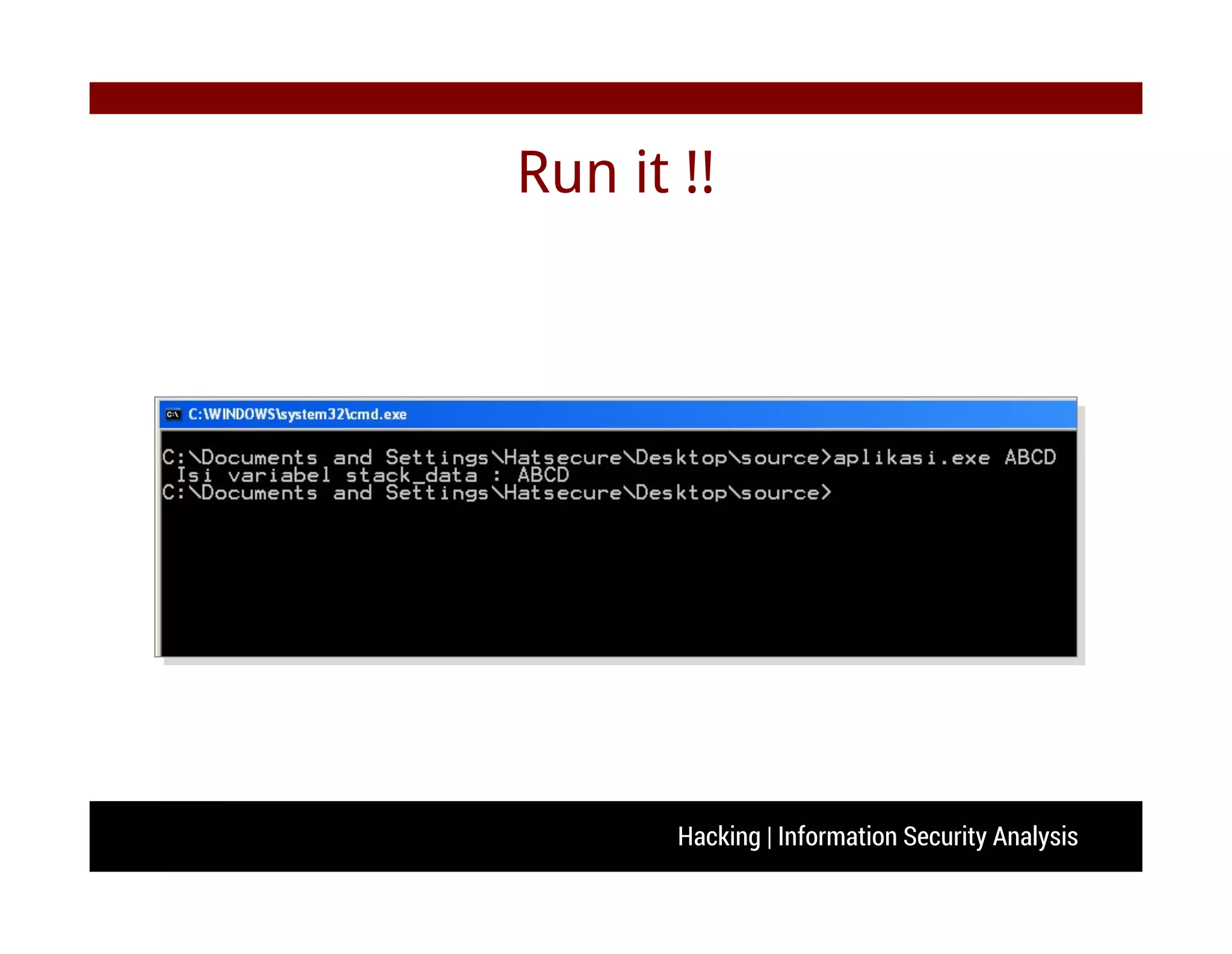
C++ from beginner
#include <stdio.h>
void vulnerable(char *Buffer){
char stack_data[128];
strcpy (stack_data, Buffer);
printf( " Isi variabel stack_data : %s ", stack_data);
}
int main(int argc, char **argv){
vulnerable(argv[1]);
return 0;
}](https://image.slidesharecdn.com/seminar-140621015100-phpapp02/75/Seminar-Hacking-Security-Analysis-17-2048.jpg)
![Hacking | Information Security Analysis
Stack Allocation
#include <stdio.h>
#include <string.h>
void vulnerable(char *Buffer){
char stack_data[128];
strcpy (stack_data, Buffer);
printf( " Isi variabel stack_data : %s ", stack_data);
}
int main(int argc, char **argv){
vulnerable(argv[1]);
return 0;
}
CPU Register (Example)
• EIP = 0x01234567 => address of main()
0x00000000
Top of Stack](https://image.slidesharecdn.com/seminar-140621015100-phpapp02/75/Seminar-Hacking-Security-Analysis-19-2048.jpg)
![Hacking | Information Security Analysis
Stack Allocation
#include <stdio.h>
#include <string.h>
void vulnerable(char *Buffer){
char stack_data[128];
strcpy (stack_data, Buffer);
printf( " Isi variabel stack_data : %s ", stack_data);
}
int main(int argc, char **argv){
vulnerable(argv[1]);
return 0;
}
0x00000000
Top of Stack
CPU Register (Example)
• EIP = 0x01234571 => address of vulnerable()](https://image.slidesharecdn.com/seminar-140621015100-phpapp02/75/Seminar-Hacking-Security-Analysis-20-2048.jpg)
![Hacking | Information Security Analysis
Stack Allocation
#include <stdio.h>
#include <string.h>
void vulnerable(char *Buffer){
char stack_data[128];
strcpy (stack_data, Buffer);
printf( " Isi variabel stack_data : %s ", stack_data);
}
int main(int argc, char **argv){
vulnerable(argv[1]);
return 0;
}
0x00000000
Top of Stack
CPU Register (Example)
• EIP = 0x01234585 => stack_data[128]](https://image.slidesharecdn.com/seminar-140621015100-phpapp02/75/Seminar-Hacking-Security-Analysis-21-2048.jpg)
![Hacking | Information Security Analysis
Stack Allocation
#include <stdio.h>
#include <string.h>
void vulnerable(char *Buffer){
char stack_data[128];
strcpy (stack_data, Buffer);
printf( " Isi variabel stack_data : %s ", stack_data);
}
int main(int argc, char **argv){
vulnerable(argv[1]);
return 0;
}
0x00000000
Top of Stack
CPU Register (Example)
• EIP = 0x01234544 => address of strcpy()
<Space for stack_data>
ESP
<ptr to argv[1]>
Saved EBP 0x00112233
Saved EIP 0x00112237](https://image.slidesharecdn.com/seminar-140621015100-phpapp02/75/Seminar-Hacking-Security-Analysis-22-2048.jpg)
![Hacking | Information Security Analysis
Stack Allocation
#include <stdio.h>
#include <string.h>
void vulnerable(char *Buffer){
char stack_data[128];
strcpy (stack_data, Buffer);
printf( " Isi variabel stack_data : %s ", stack_data);
}
int main(int argc, char **argv){
vulnerable(argv[1]);
return 0;
}
0x00000000
Top of Stack
ABCD
ESP
<ptr to argv[1]>
Saved EBP 0x00112233
Saved EIP 0x00112237
CPU Register (Example)
• EIP = 0x01234548 => address of printf()](https://image.slidesharecdn.com/seminar-140621015100-phpapp02/75/Seminar-Hacking-Security-Analysis-23-2048.jpg)
![Hacking | Information Security Analysis
Stack Allocation
#include <stdio.h>
#include <string.h>
void vulnerable(char *Buffer){
char stack_data[128];
strcpy (stack_data, Buffer);
printf( " Isi variabel stack_data : %s ", stack_data);
}
int main(int argc, char **argv){
vulnerable(argv[1]);
return 0;
}
0x00000000
Top of Stack
ESP
<ptr to argv[1]>
Saved EBP 0x00112233
Saved EIP 0x00112237
CPU Register (Example)
• EIP = 0x01234552 => restore saved EIP -> EIP](https://image.slidesharecdn.com/seminar-140621015100-phpapp02/75/Seminar-Hacking-Security-Analysis-24-2048.jpg)
![Hacking | Information Security Analysis
Stack Allocation
#include <stdio.h>
#include <string.h>
void vulnerable(char *Buffer){
char stack_data[128];
strcpy (stack_data, Buffer);
printf( " Isi variabel stack_data : %s ", stack_data);
}
int main(int argc, char **argv){
vulnerable(argv[1]);
return 0;
}
0x00000000
Top of Stack
ESP
<ptr to argv[1]>
CPU Register (Example)
• EIP = 0x01234599 => exit(0)](https://image.slidesharecdn.com/seminar-140621015100-phpapp02/75/Seminar-Hacking-Security-Analysis-25-2048.jpg)
![Hacking | Information Security Analysis
Stack Allocation
#include <stdio.h>
#include <string.h>
void vulnerable(char *Buffer){
char stack_data[128];
strcpy (stack_data, Buffer);
printf( " Isi variabel stack_data : %s ", stack_data);
}
int main(int argc, char **argv){
vulnerable(argv[1]);
return 0;
}
0x00000000
Top of Stack](https://image.slidesharecdn.com/seminar-140621015100-phpapp02/75/Seminar-Hacking-Security-Analysis-26-2048.jpg)
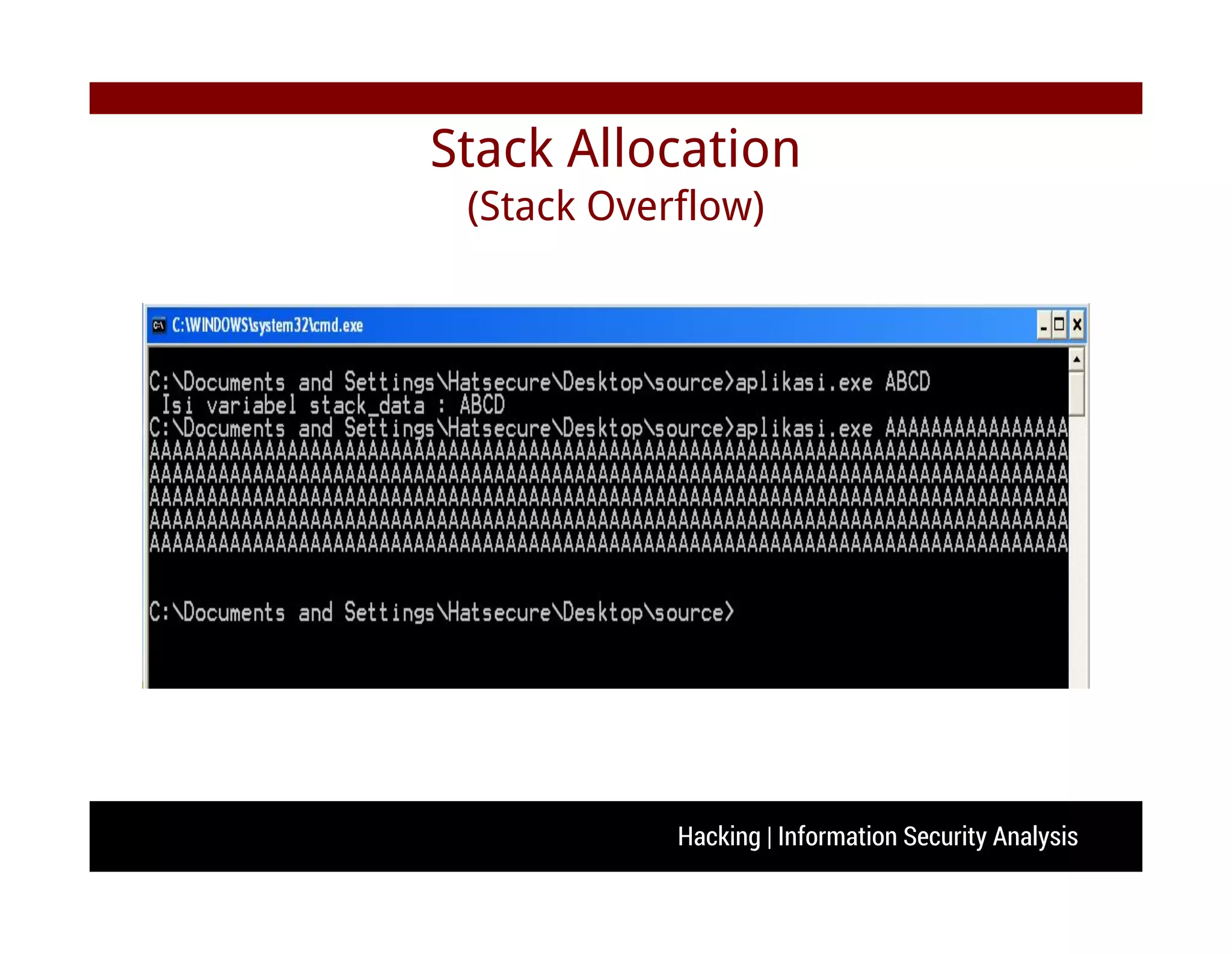
![Hacking | Information Security Analysis
Stack Allocation
(Stack Overflow)
#include <stdio.h>
#include <string.h>
void vulnerable(char *Buffer){
char stack_data[128];
strcpy (stack_data, Buffer);
printf( " Isi variabel stack_data : %s ", stack_data);
}
int main(int argc, char **argv){
vulnerable(argv[1]);
return 0;
}
0x00000000
Top of Stack
CPU Register (Example)
• EIP = 0x012345 => address of strcpy()
<Space for stack_data>
ESP
<ptr to argv[1]>
Saved EBP 0x00112233
Saved EIP 0x00112237](https://image.slidesharecdn.com/seminar-140621015100-phpapp02/75/Seminar-Hacking-Security-Analysis-28-2048.jpg)
![Hacking | Information Security Analysis
Stack Allocation
(Stack Overflow)
#include <stdio.h>
#include <string.h>
void vulnerable(char *Buffer){
char stack_data[128];
strcpy (stack_data, Buffer);
printf( " Isi variabel stack_data : %s ", stack_data);
}
int main(int argc, char **argv){
vulnerable(argv[1]);
return 0;
}
0x00000000
Top of Stack
414141414141414141414141
414141414141414141414141
414141414141414141414141
Saved EBP 0x41414141
Saved EIP 0x41414141
ESP
414141414141414141414141
414141414141414141414141
414141414141414141414141
414141414141414141414141
414141414141414141414141
0x00112233
0x00112237
CPU Register (Example)
• EIP = 0x01234548 => address of printf()](https://image.slidesharecdn.com/seminar-140621015100-phpapp02/75/Seminar-Hacking-Security-Analysis-29-2048.jpg)
![Hacking | Information Security Analysis
Stack Allocation
#include <stdio.h>
#include <string.h>
void vulnerable(char *Buffer){
char stack_data[128];
strcpy (stack_data, Buffer);
printf( " Isi variabel stack_data : %s ", stack_data);
}
int main(int argc, char **argv){
vulnerable(argv[1]);
return 0;
}
0x00000000
Top of Stack
ESP
414141414141414141414141
414141414141414141414141
414141414141414141414141
414141414141414141414141
414141414141414141414141
0x00112233
0x00112237
Saved EBP 0x41414141
Saved EIP 0x41414141
CPU Register (Example)
• EIP = 0x41414141 => restore saved EIP -> EIP](https://image.slidesharecdn.com/seminar-140621015100-phpapp02/75/Seminar-Hacking-Security-Analysis-30-2048.jpg)
![Hacking | Information Security Analysis
Stack Allocation
#include <stdio.h>
#include <string.h>
void vulnerable(char *Buffer){
char stack_data[128];
strcpy (stack_data, Buffer);
printf( " Isi variabel stack_data : %s ", stack_data);
}
int main(int argc, char **argv){
vulnerable(argv[1]);
return 0;
}
0x00000000
Top of Stack
ESP
414141414141414141414141
414141414141414141414141
414141414141414141414141
414141414141414141414141
414141414141414141414141
0x00112233
0x00112237
CPU Register (Example)
• EIP = 0x41414141
Access Volation when executing 0x41414141](https://image.slidesharecdn.com/seminar-140621015100-phpapp02/75/Seminar-Hacking-Security-Analysis-31-2048.jpg)