Embed presentation
Downloaded 67 times

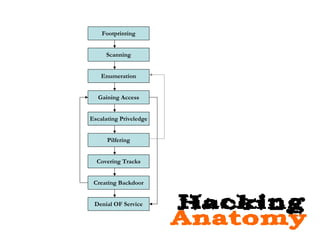



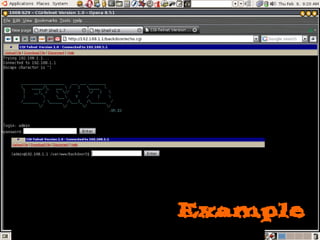
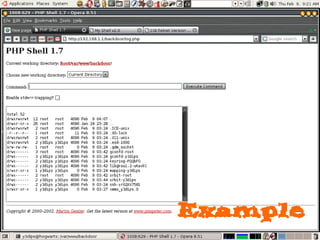
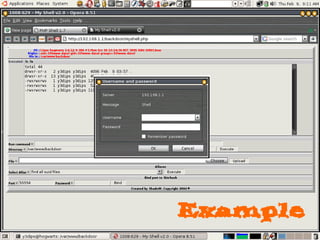
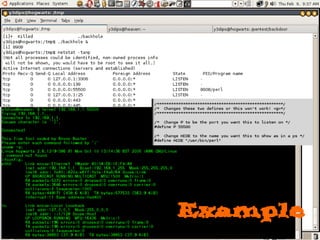
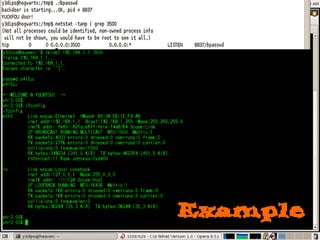
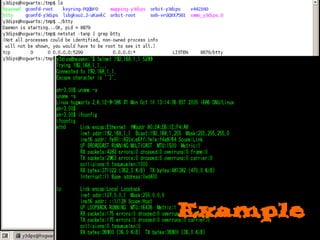



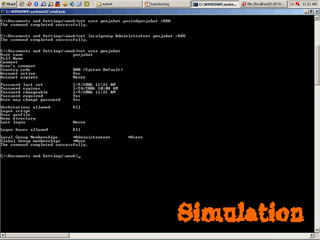



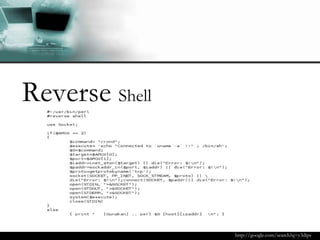
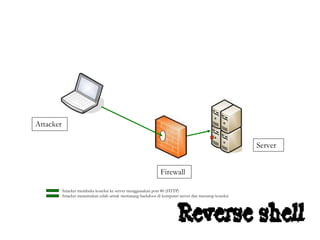
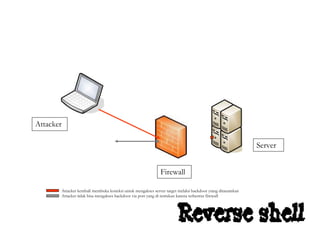
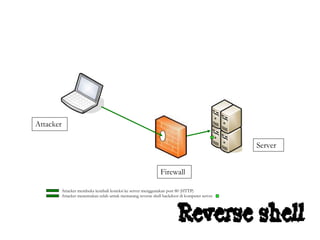
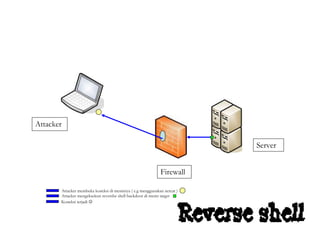
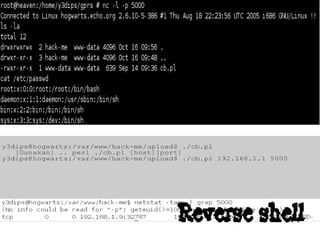



Dokumen tersebut membahas tentang backdoor, yaitu metode untuk mem-bypass otentikasi dan keamanan akses secara remote ke suatu mesin tanpa batasan. Backdoor dapat berupa program yang diinstal, modifikasi program/file, berbasis aplikasi, atau program yang dijalankan seperti bindshell.


























