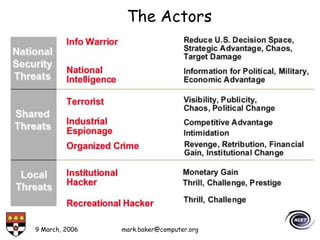
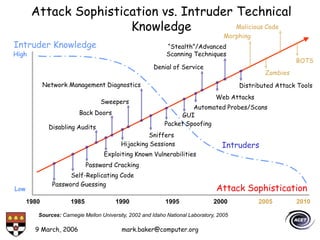
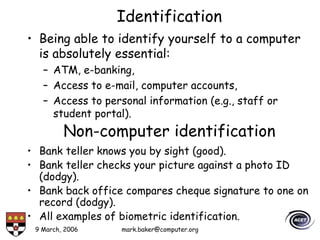
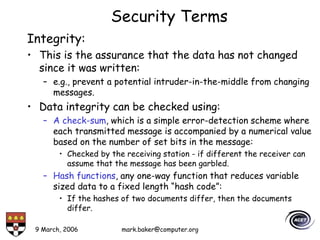
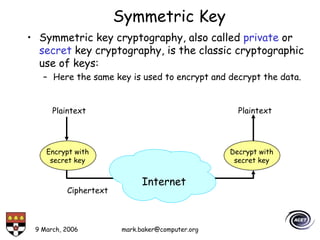
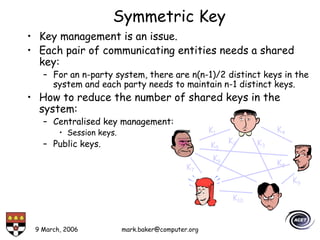
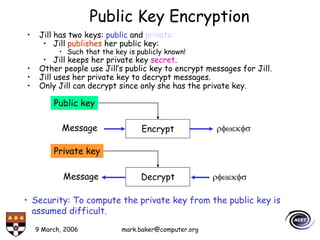
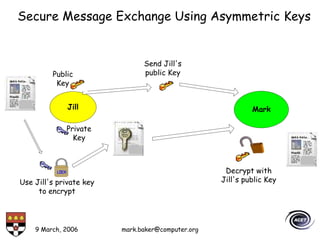
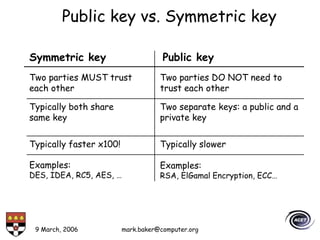
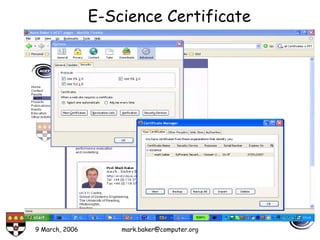
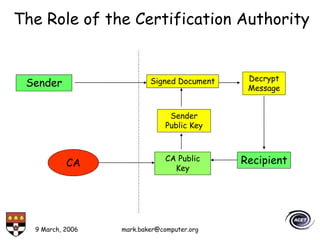
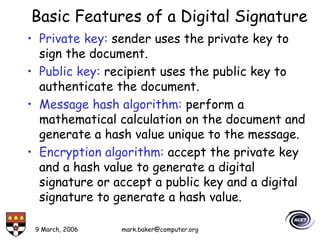
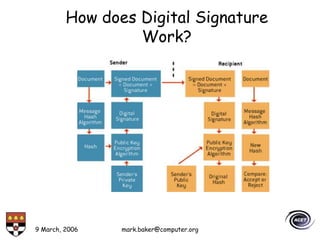
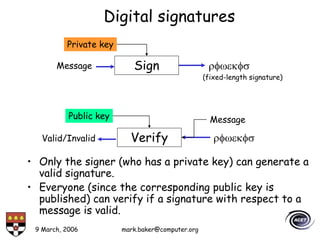
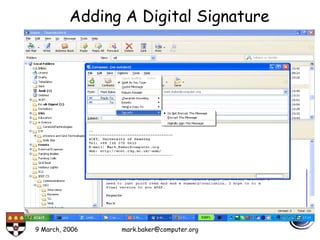
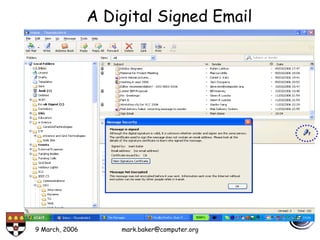
The document discusses basic security concepts such as confidentiality, integrity, authentication, authorization, and encryption. It outlines security concerns like unauthorized access, masquerading, and monitoring of network traffic. Factors contributing to security risks include increased internet use, lack of awareness, unencrypted network traffic, and software bugs. The document defines common security terms and components, including symmetric and asymmetric encryption, public key infrastructure involving certificates and signatures, and access control lists for authorization. Security objectives are listed as confidentiality, integrity, and availability.