This document provides an overview of computer security and privacy. It begins with defining key terms like security, privacy, threats, and vulnerabilities. It then discusses the evolution of computer security, highlighting important early cases from the 1970s-1990s. The document outlines different types of computer security like security by design, secure operating systems, and secure coding. It also covers privacy issues and some salient computer security cases from Ethiopia and globally to demonstrate the history and importance of the topic.


![Computer Security
• Computer Security is a Branch of Computer Technology
• It is Information security as applied to computers and
networks.
• The objectives- Protection of information from
Theft,
Corruption,
Damage from disaster,
Definition
Security: The prevention and protection of computer assets
from unauthorized access, use, alteration, degradation,
destruction, and other threats.
“ The term computer system security means the collective
processes and mechanisms by which sensitive and valuable
information and services are protected from publication,
tamper [ alter ]or collapse by unauthorized activities or
untrustworthy individuals and unplanned events
respectively.](https://image.slidesharecdn.com/chapter1a-130424064316-phpapp01/85/Chapter-1-a-3-320.jpg)




![Computer Security VS Network Security
Computer Security
• Computer Security is confined
to securing the Computer as
an individual system.
• The provisions and policies
adopted to protect
information and property from
Theft, Corruption, or Natural
Disaster while allowing the
information and property to
remain accessible and
productive to its intended
users. [ Security at gate, Safe
place, Authorization of
people, Building]
Network security
• Network security on the
other hand deals with
provisions and policies
adopted to prevent and
monitor unauthorized access,
misuse, modification, or
denial of the computer
network and network-
accessible resources.](https://image.slidesharecdn.com/chapter1a-130424064316-phpapp01/85/Chapter-1-a-9-320.jpg)



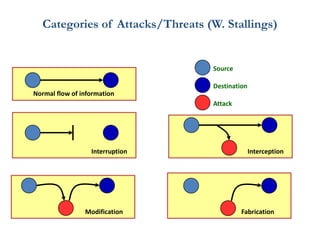






![Salient Security Cases
• Salient Security Cases
The Federal Bureau of Investigation (FBI) made one of its first
arrests related to computer hacking in the early 1980s.
A group of hackers known as the 414s, named after their area code
in Milwaukee, Wisconsin, were indicted for attacking 60 different
computer systems including the Los Alamos National Laboratory
and the Memorial Sloan-Kettering Cancer Center.
Internet Worm (Morris worm )
November 2, 1988 a worm attacked more than 60,000 computers around
the USA
The worm attacks computers, and when it has installed itself, it
multiplies itself, freezing the computer
It exploited UNIX security holes in Sendmail
A nationwide effort enabled to solve the problem within 12 hours
Robert Morris [ A Professor at the MIT] became the first person to be
indicted under the Computer Fraud and Abuse Act.
He was sentenced to three years of probation, 400 hours of community service
and a fine of $10,050](https://image.slidesharecdn.com/chapter1a-130424064316-phpapp01/85/Chapter-1-a-22-320.jpg)




![Salient Security Cases Contd…
Early Efforts
• 1960s: Marked as the beginning of true computer
security
• 1970s: Research and modeling
Identifying security requirements
Formulating security policy models
Defining recommended guidelines and controls
Development of secure systems
• European Council adopted a convention on Cyber-
crime in 2001.
• The World Summit for Information Society
considered computer security and privacy as a subject
of discussion in 2003 and 2005.
• The Ethiopian Penal Code [EPC] of 2005 has articles
on data and computer related crimes.](https://image.slidesharecdn.com/chapter1a-130424064316-phpapp01/85/Chapter-1-a-27-320.jpg)




![Types of Computer Security Contd…
Security Architecture [ i.e. IT infrastructure
Arch.)
• Security Architecture can be defined as the
design artifacts that describe how the security
controls (security countermeasures) are
positioned, and how they relate to the overall
Information technology architecture.
• A countermeasure is an
action, process, device, or system that can
prevent, or mitigate [lessen] the effects
of, threats to a computer, server or network. [
• System's quality
attributes, confidentiality, integrity*(validity), av
ailability, accountability and assurance [ Real](https://image.slidesharecdn.com/chapter1a-130424064316-phpapp01/85/Chapter-1-a-32-320.jpg)