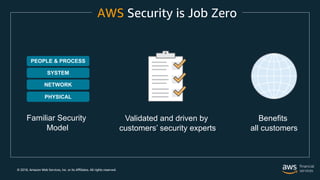
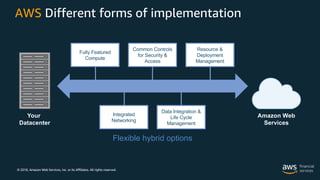
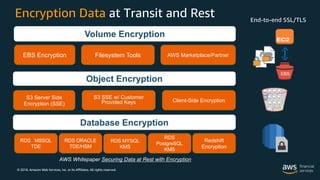
The document outlines the security and compliance features of Amazon Web Services (AWS), emphasizing the importance of customer-driven security models and the capabilities offered to businesses for secure cloud operations. It details various AWS services and tools that ensure privacy, data protection, and compliance with security standards. The document also highlights examples of organizations successfully leveraging AWS for enhanced security and operational efficiency.