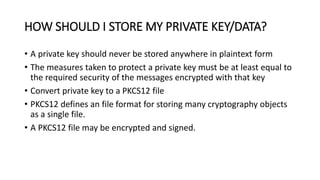
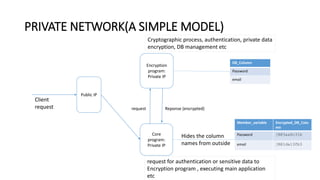
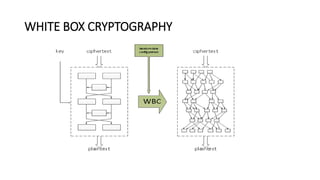
Private keys and sensitive data should be stored securely and not in plaintext. Options for storage include encrypting the private key into a PKCS12 file, storing it in the user's keystore protected by access controls, executing cryptographic processes on a private network with secure protocols, using white box cryptography which obscures the key, or storing on external hardware devices.