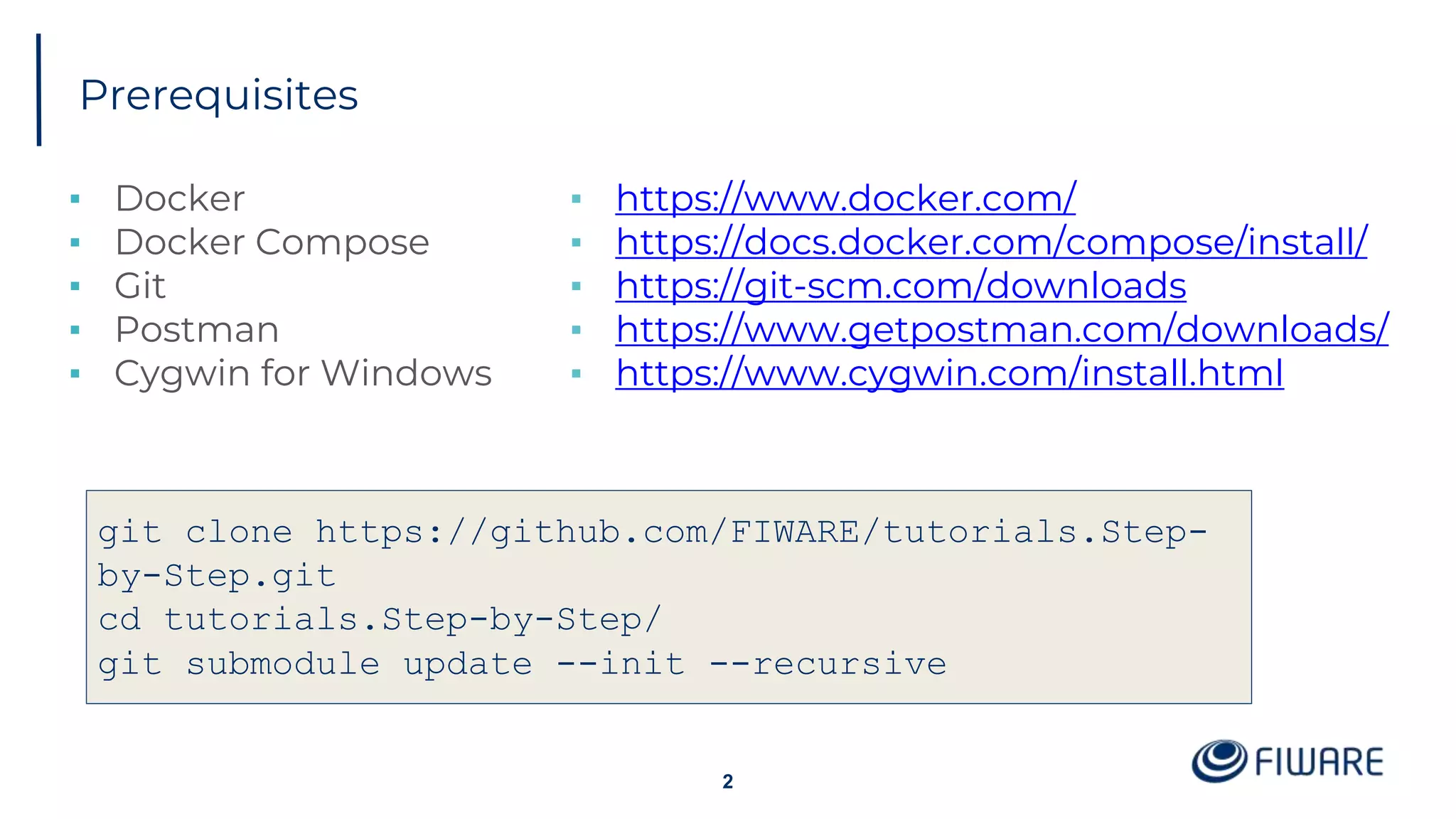
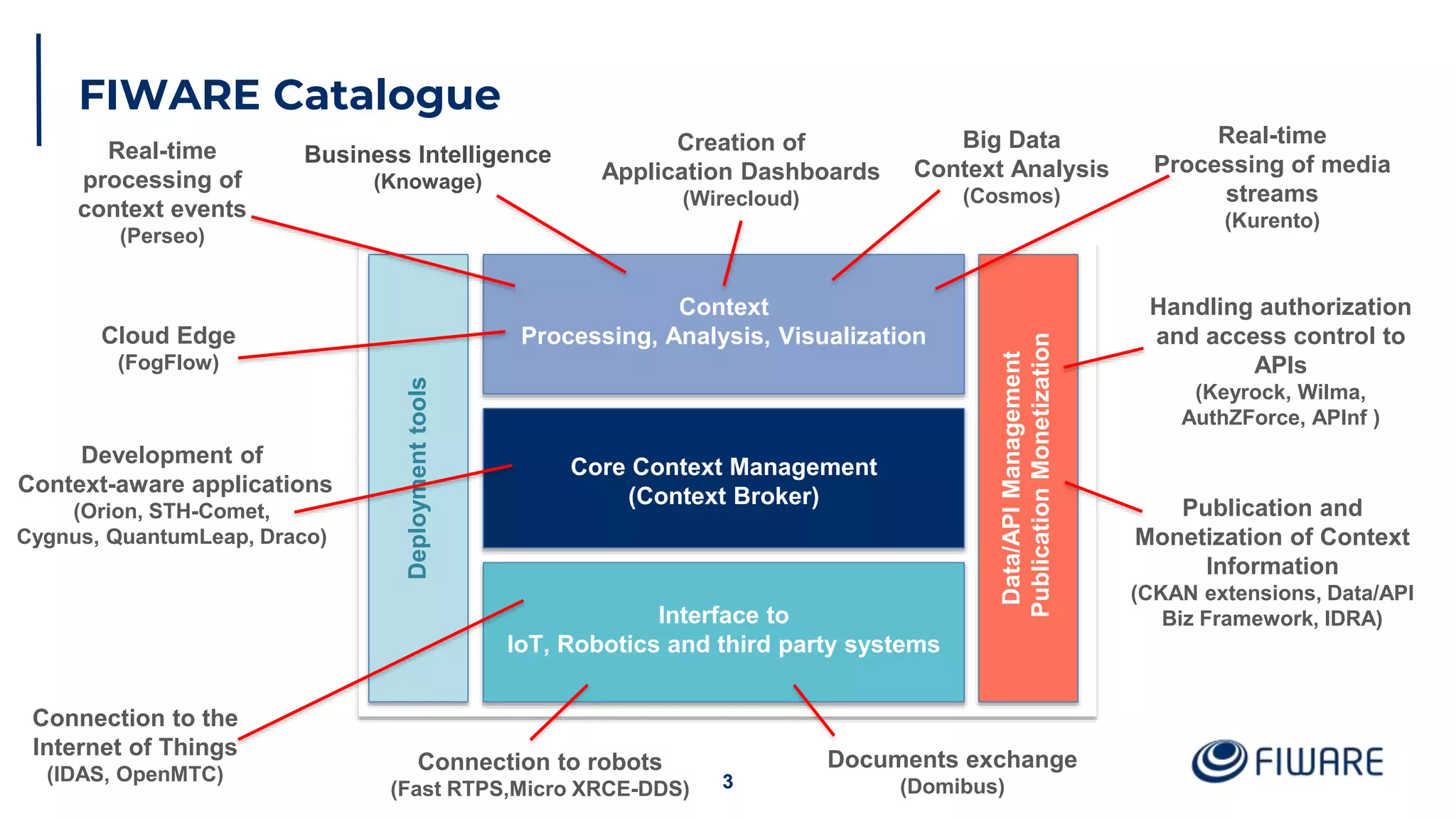
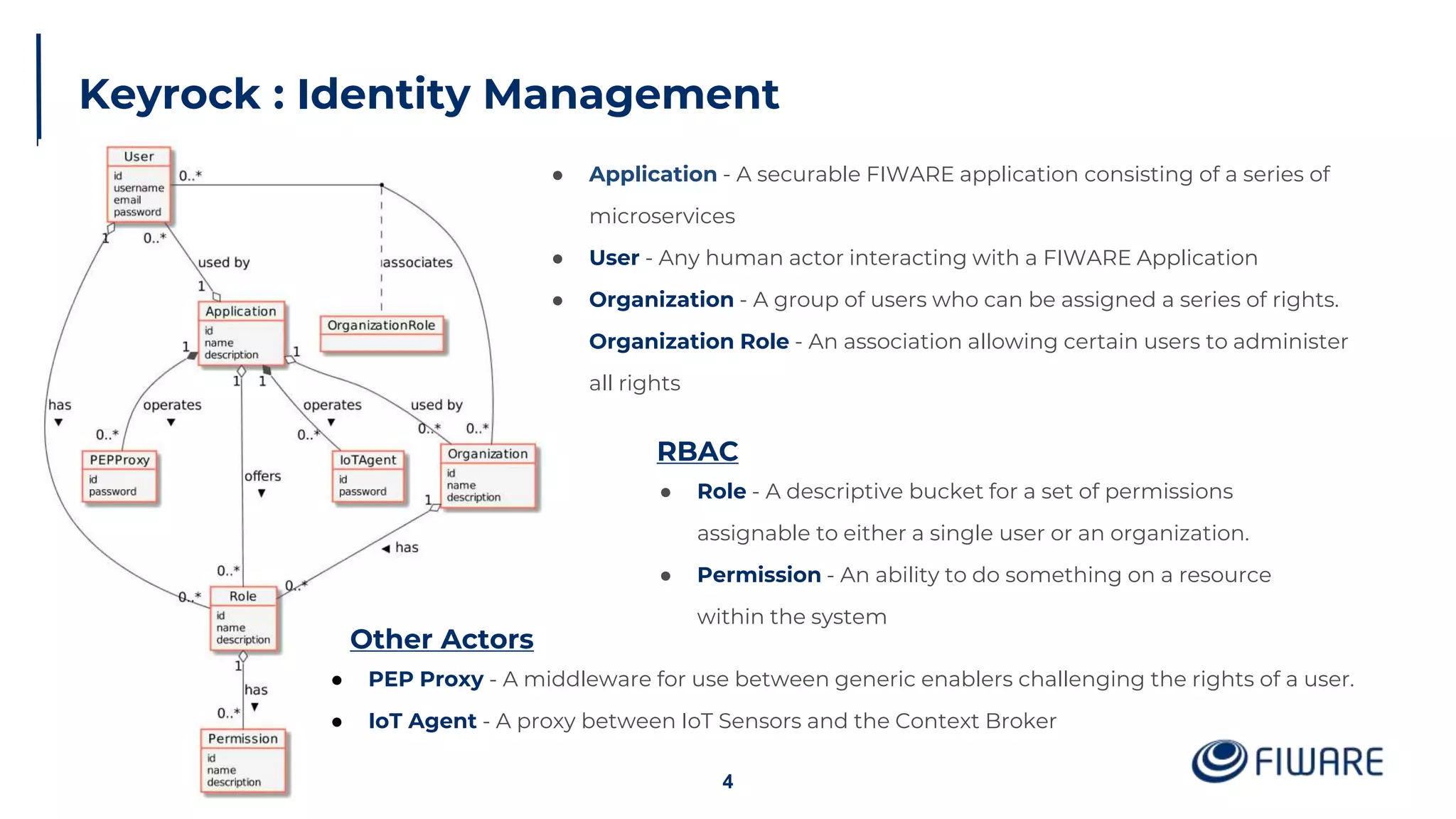
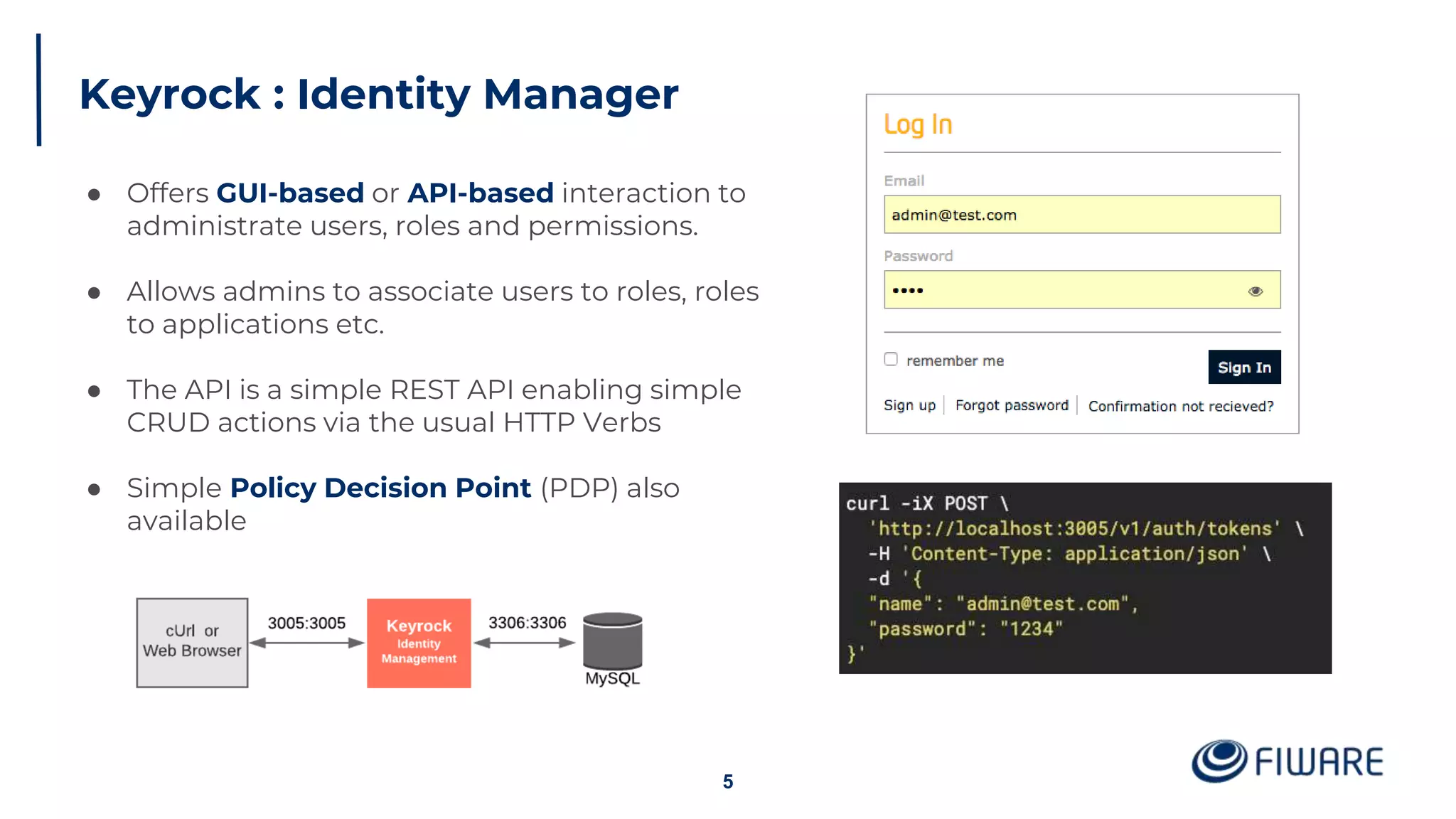
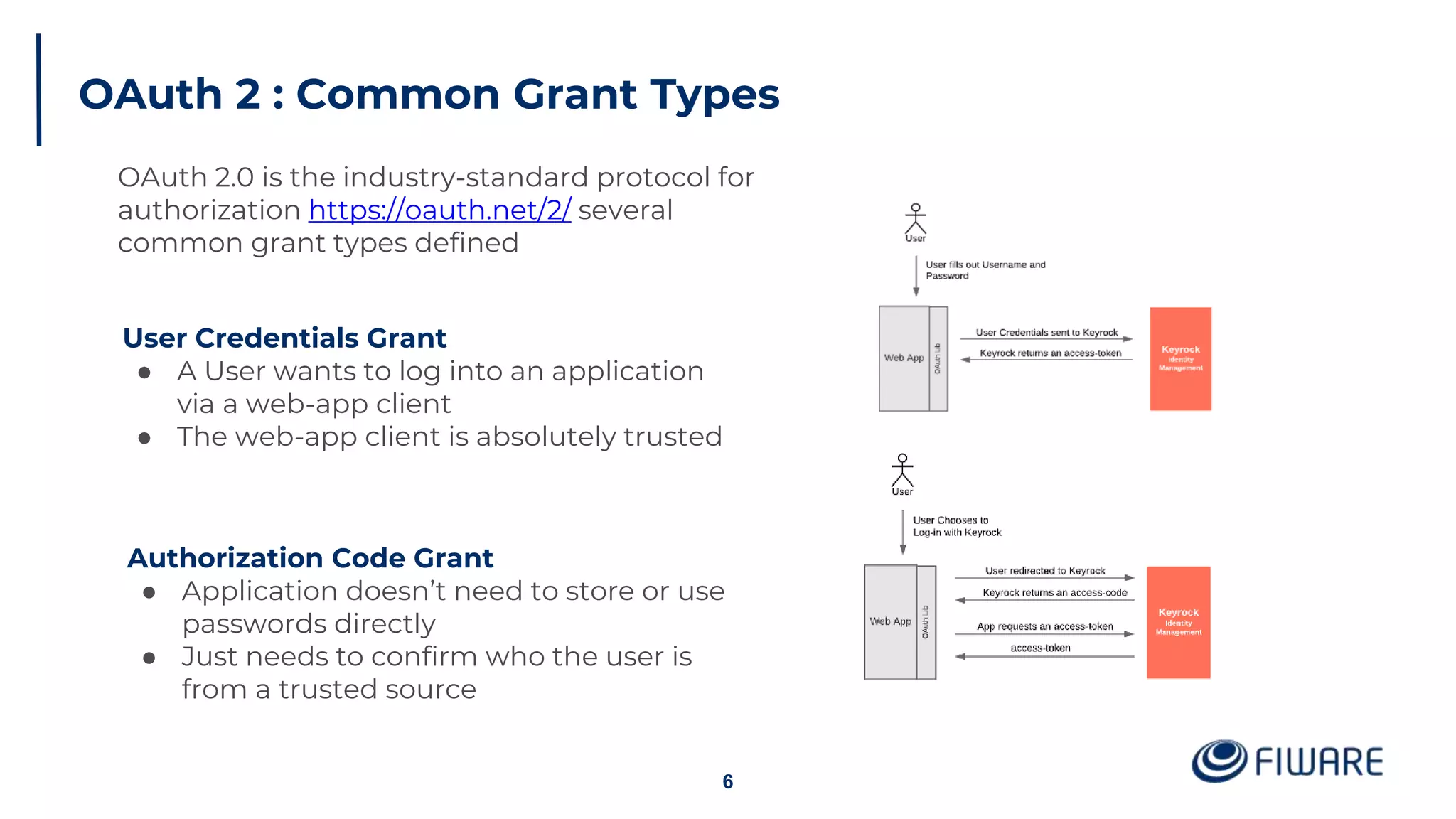
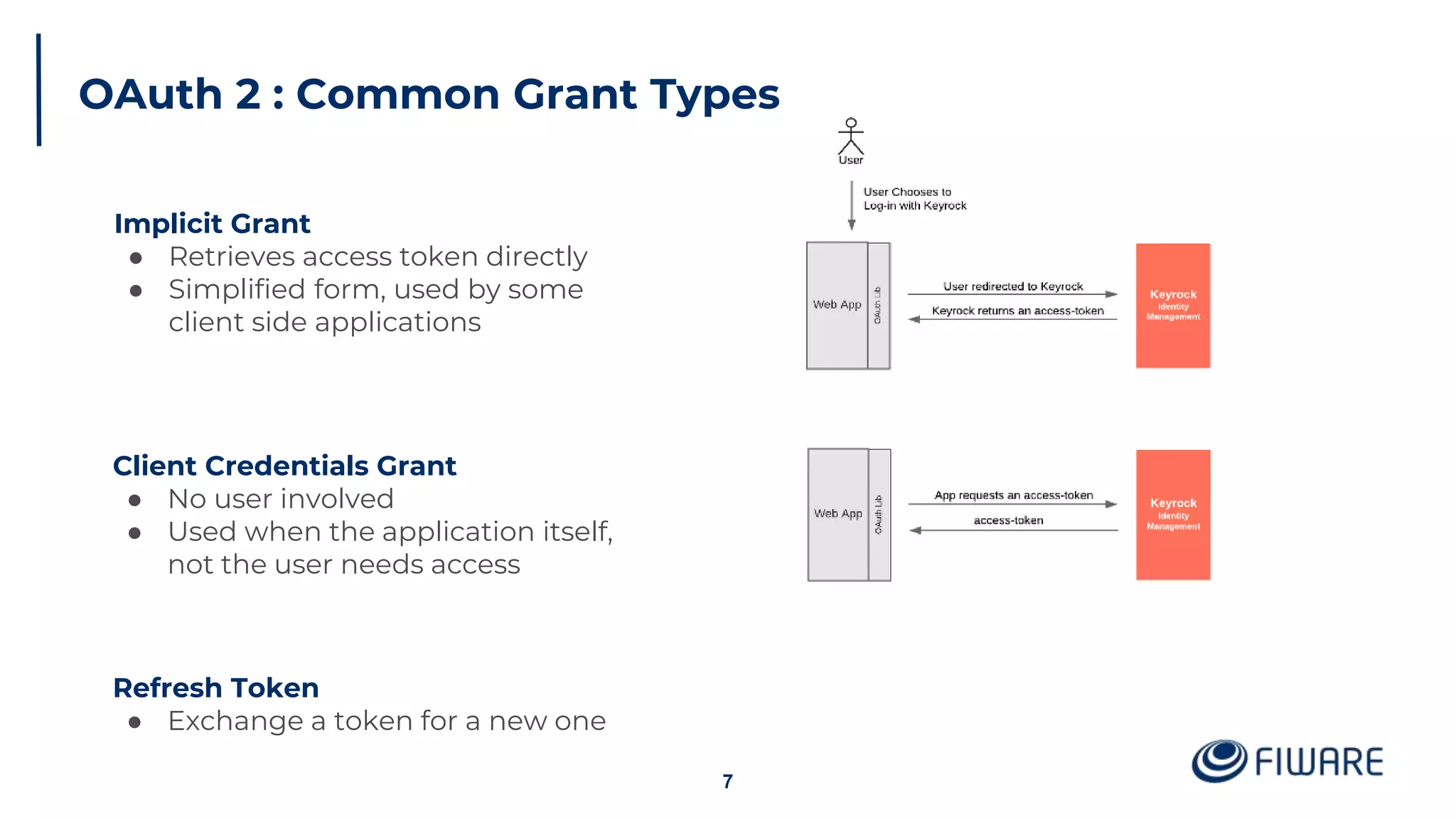
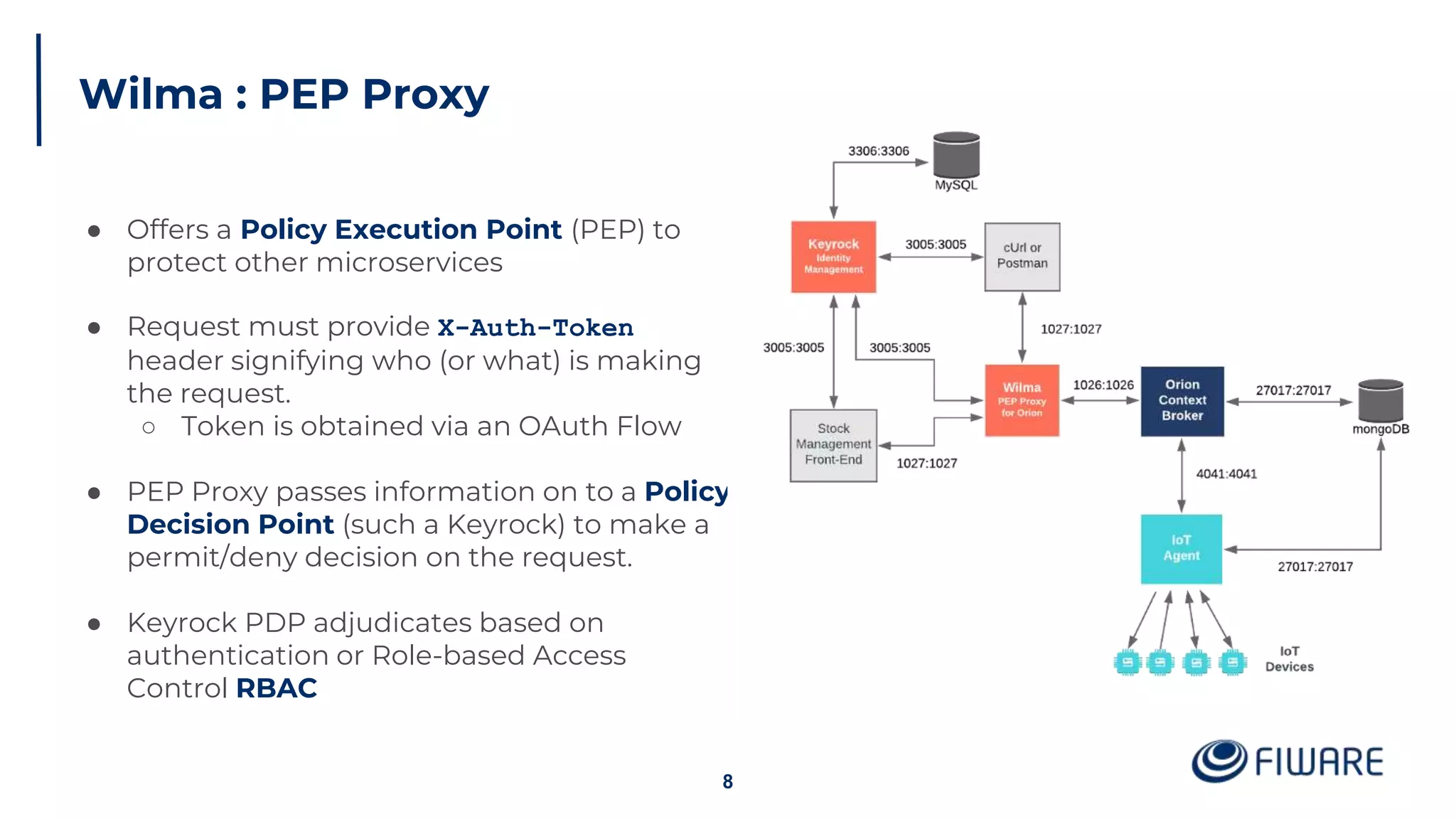
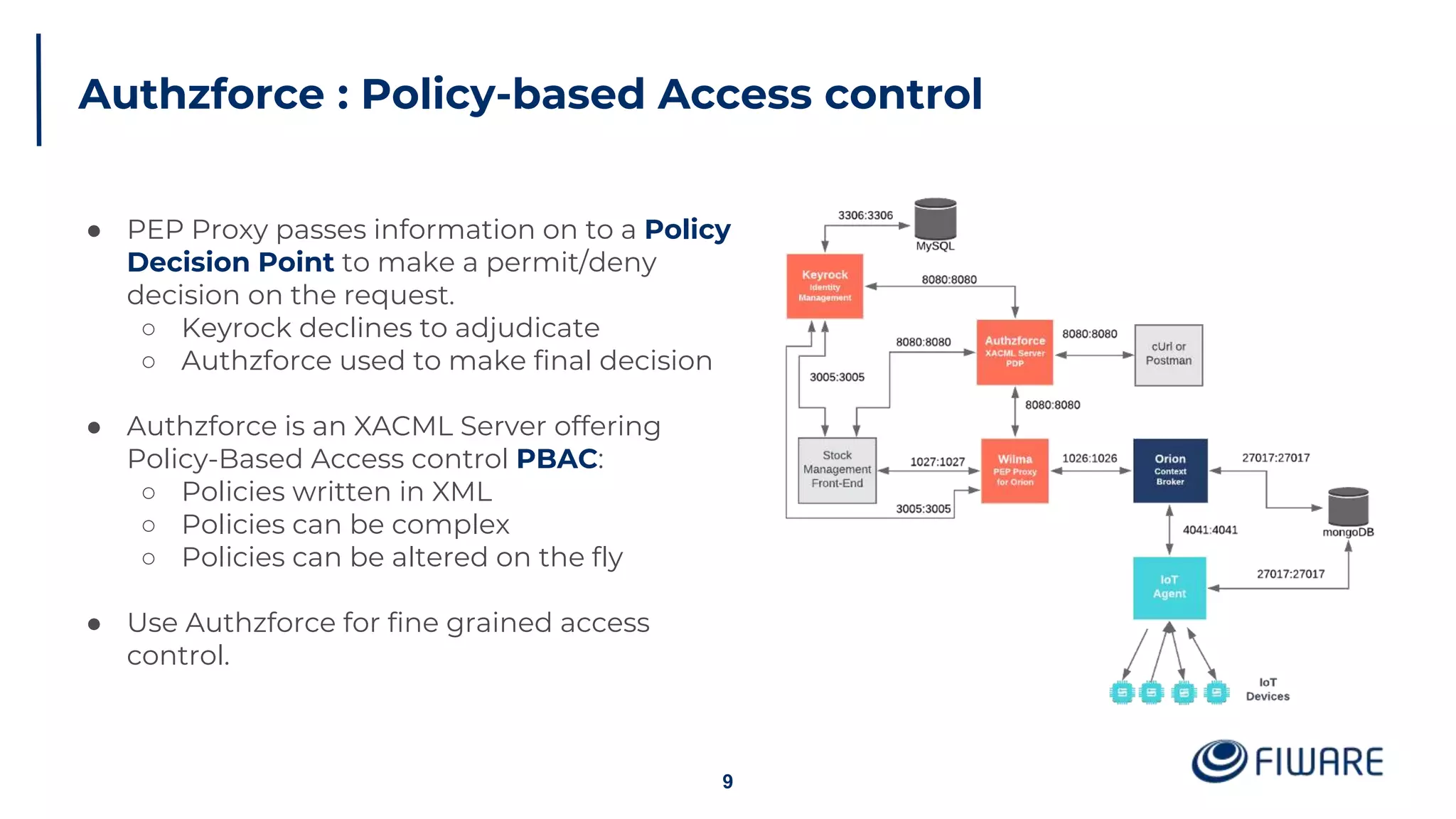
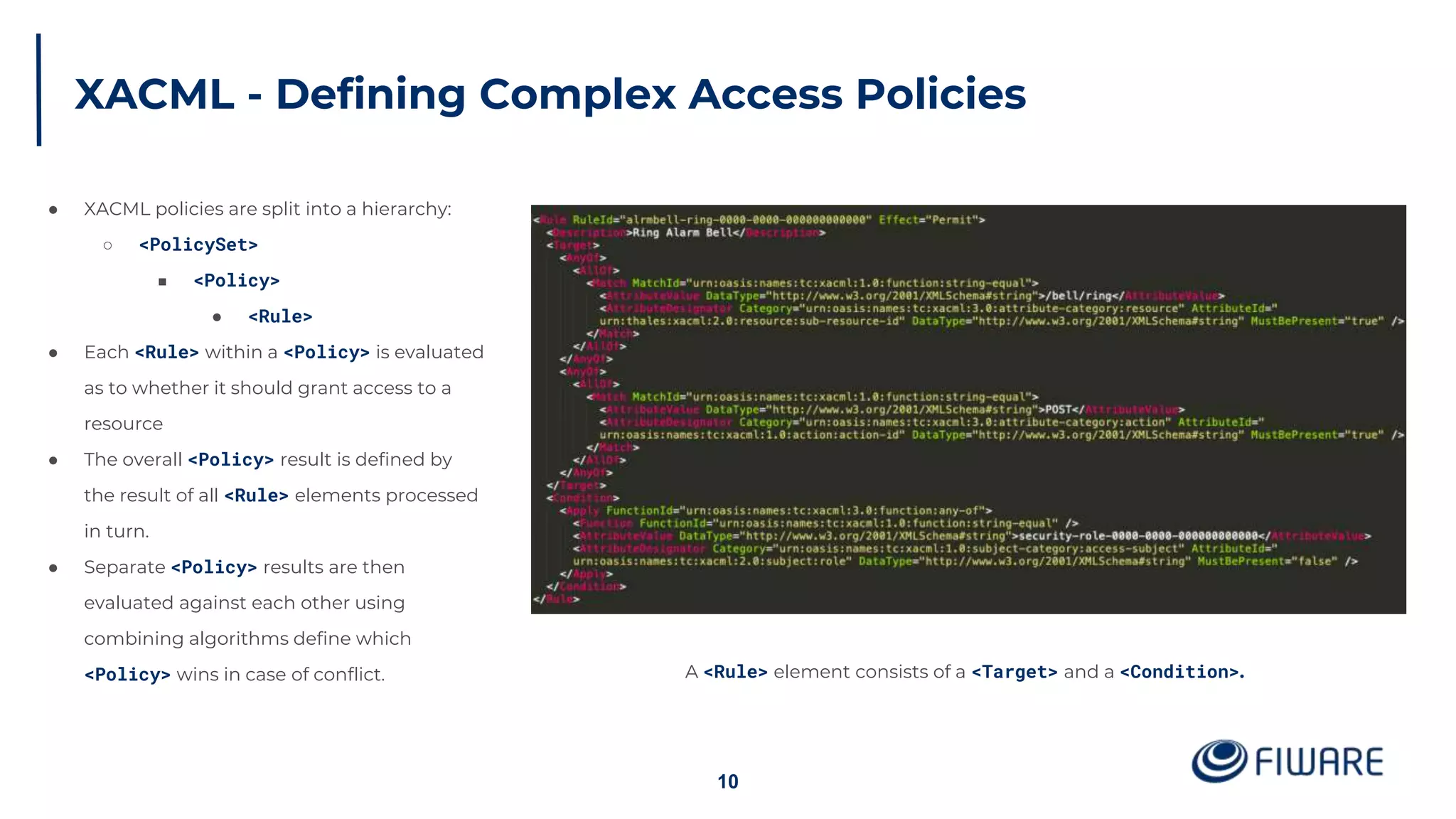
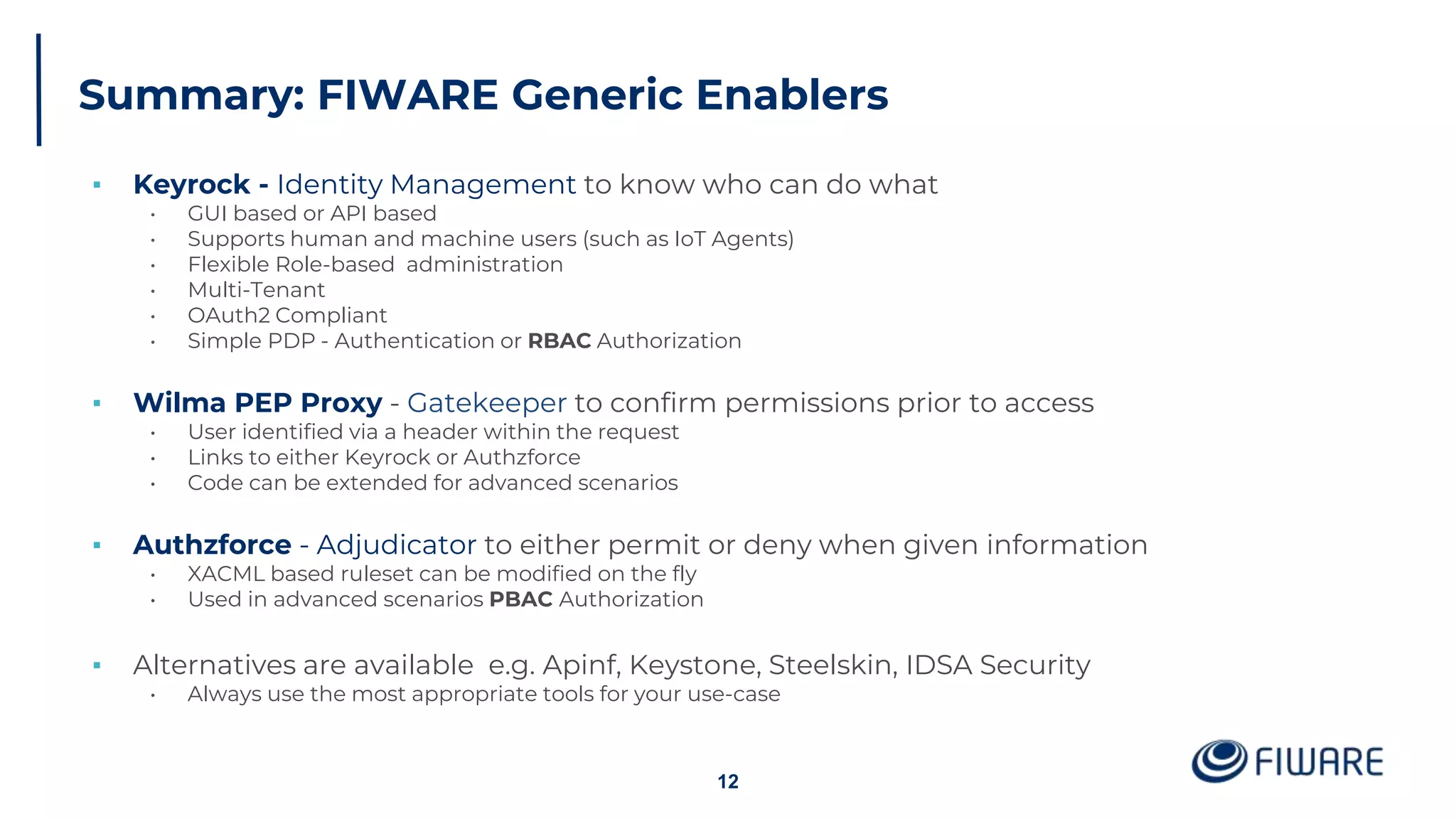
The document provides an overview of identity management and access control within FIWARE architectures, detailing components like Keyrock, Wilma, and AuthzForce. It explains key concepts such as authentication, authorization, RBAC, and PBAC, along with OAuth2 grant types and the role of PEP and PDP in access management. Additionally, it outlines prerequisites for setting up a secure FIWARE application environment.