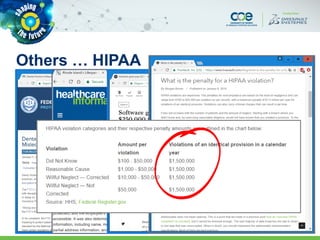
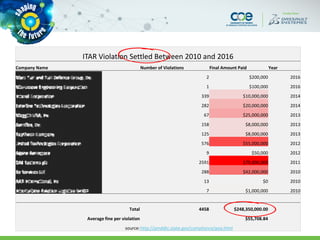
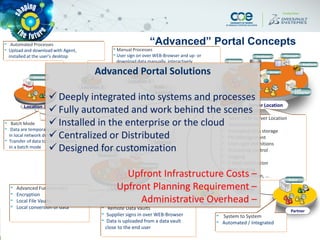
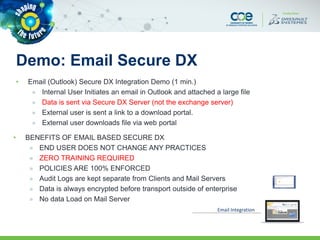
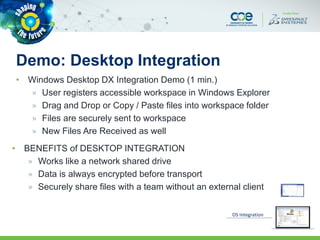
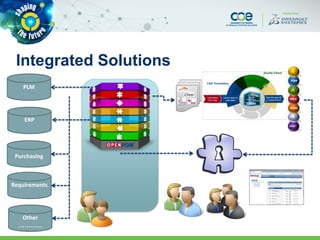
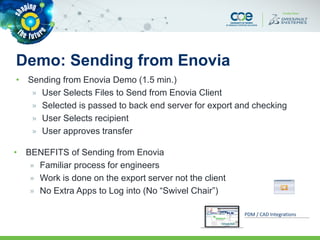
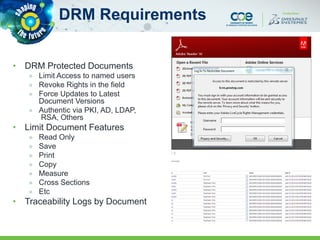
The document discusses secure methods for exchanging CATIA data outside an enterprise, highlighting the risks of information leakage and the importance of safeguarding intellectual property. It reviews various options for secure data exchange, including integration with existing user workflows and back-end systems, while emphasizing the need for user-friendly solutions to ensure compliance. Additionally, it provides case studies and practical recommendations for implementation, including the importance of using DRM solutions to protect data post-transfer.