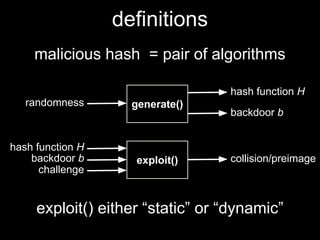
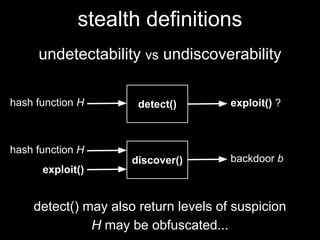
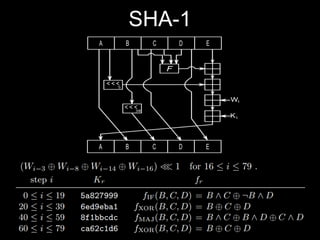
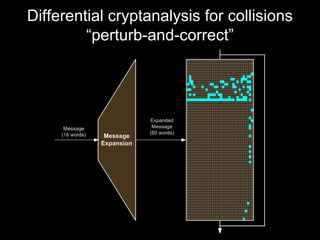
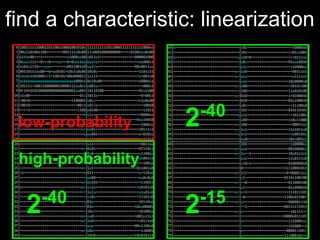
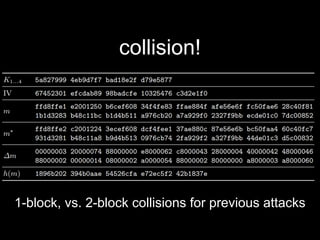
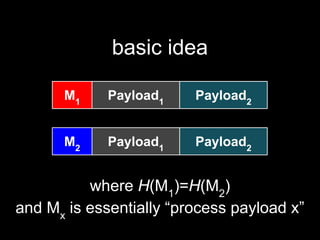
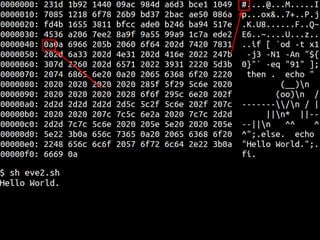
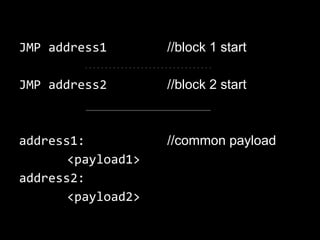
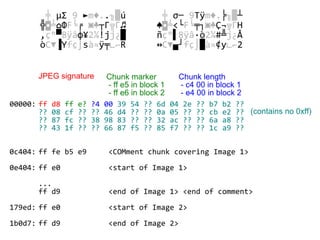
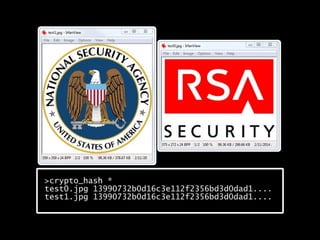
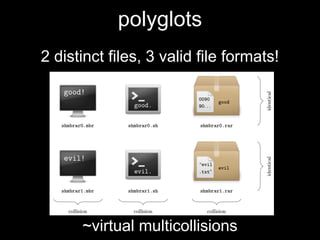
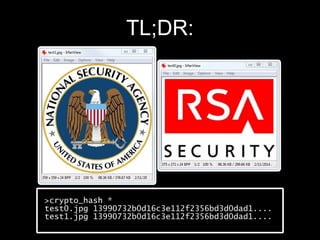
The document details methods of backdooring the SHA-1 hash function, exploring how covert backdoors might exploit collisions and preimages for malicious purposes. It discusses various types of backdoors and potential implications for SHA-1 and newer hash functions like SHA-256, concluding that while SHA-1's security hasn't improved, the design might not have been influenced by backdooring methods. The authors analyze techniques and examples to demonstrate vulnerabilities without necessarily enhancing attacks on the original SHA-1.












![not an implementation backdoor
example: RC4 C implementation (Wagner/Biondi)
#define TOBYTE(x) (x) & 255
#define SWAP(x,y) do { x^=y; y^=x; x^=y; } while (0)
static unsigned char A[256];
static int i=0, j=0;
unsigned char encrypt_one_byte(unsigned char c) {
int k;
i = TOBYTE(i+1);
j = TOBYTE(j + A[i]);
SWAP(A[i], A[j]);
k = TOBYTE(A[i] + A[j]);
return c ^ A[k];
}](https://image.slidesharecdn.com/malsha1lv-140805043944-phpapp02/85/SHA-1-backdooring-exploitation-14-320.jpg)