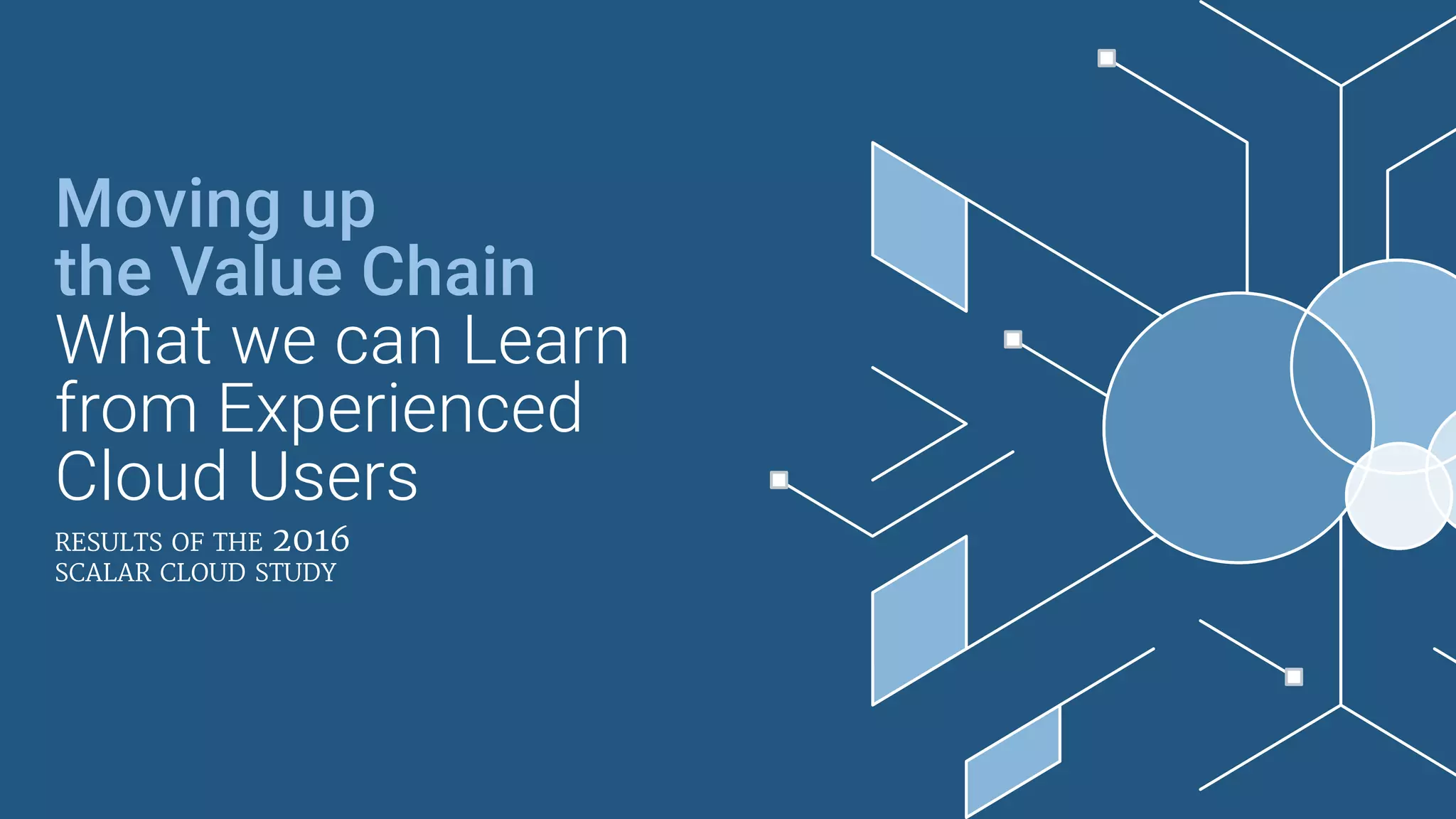
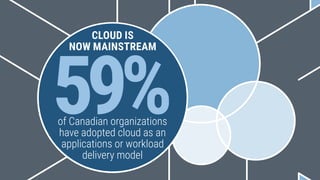
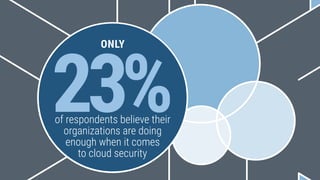
The document summarizes the findings of a 2016 cloud study that interviewed 211 IT and business decision makers from Canadian organizations about their cloud adoption. It found that 59% have adopted cloud, but 48% lack a formal cloud security policy. While security remains a top concern, it is no longer seen as a barrier to cloud. Only 23% feel they are doing enough on cloud security. Both cloud workloads and budgets are expected to increase in the next 1-3 years. Experienced cloud users emphasize the importance of planning, assessment and having a formal roadmap for successful cloud migration.