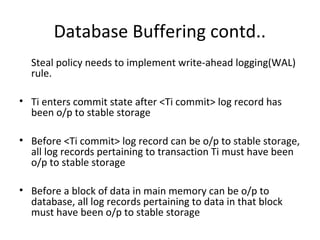
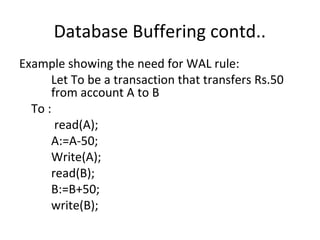
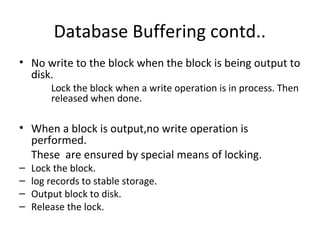
This document discusses database buffering policies and write-ahead logging. It describes the no-force and no-steal policies, noting advantages like faster commits but also disadvantages like buffers filling with updated pages. The no-steal policy does not write modified blocks until transaction commit, while the steal policy may write blocks even if the transaction has not committed. It also explains that write-ahead logging is needed with steal policies to ensure consistency if a crash occurs, by requiring all log records be written to stable storage before committing a transaction or writing data blocks.