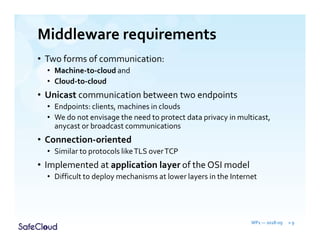
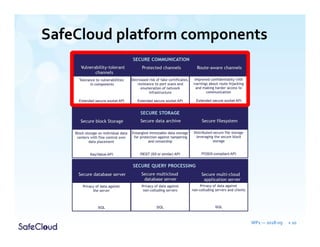
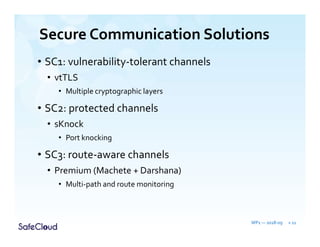
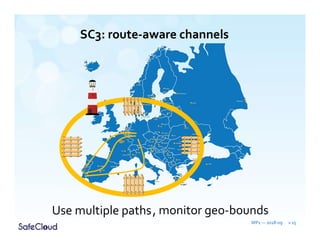
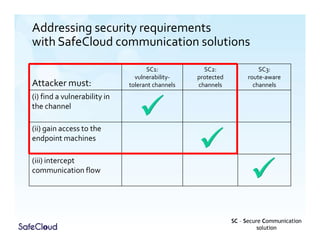
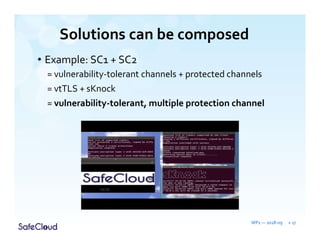
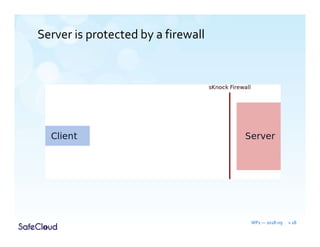
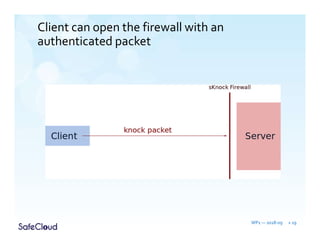
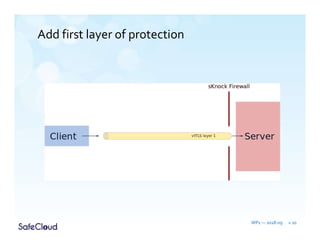
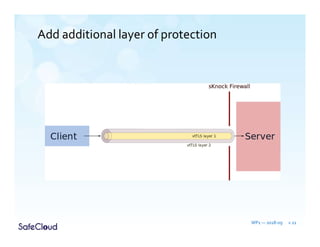
The document outlines the objectives and solutions for enhancing secure communication within the SafeCloud platform, focusing on middleware services that protect data privacy and security during cloud communications. It describes various secure communication solutions, including vulnerability-tolerant channels, protected channels, and route-aware channels, while emphasizing the importance of robustness against advanced adversaries. The achievements and scientific contributions of the SafeCloud project are also summarized, highlighting completed tasks, deliverables, and evaluations of implemented solutions.










![All tasks completed
• T1.1 — Communication architecture [M1-M6]
• T1.2 —Vulnerability-tolerant channels [M1-30]
• T1.3 — Protected service provisioning [M1-30]
• T1.4 — Route monitoring [M1-30]
• T1.5 — Multi-path communication [M1-30]
WP1 — 2018-09 » 24](https://image.slidesharecdn.com/safecloudwp1overview-180927142702/85/SafeCloud-Secure-Communication-solutions-WP1-overview-24-320.jpg)
![All deliverables completed
• D1.1 — Private communication middleware
architecture [M6; IN-ID]
• D1.2 — First version of the private communication
middleware components [M18; IN-ID]
• D1.3 — Final version of the private communication
middleware [M30; IN-ID]
WP1 — 2018-09 » 25](https://image.slidesharecdn.com/safecloudwp1overview-180927142702/85/SafeCloud-Secure-Communication-solutions-WP1-overview-25-320.jpg)