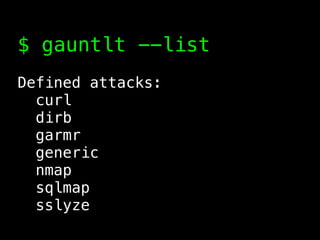
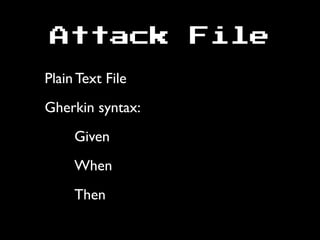
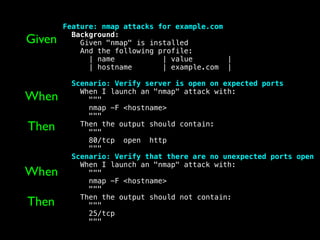
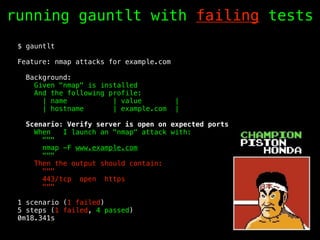
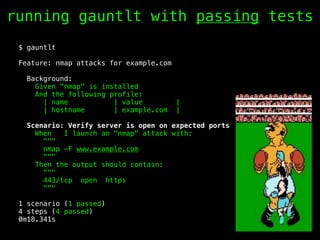
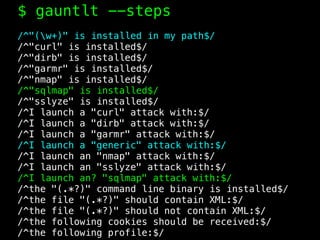
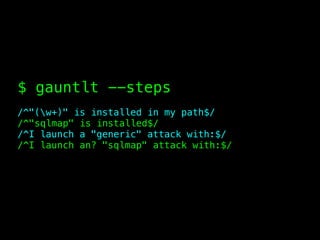
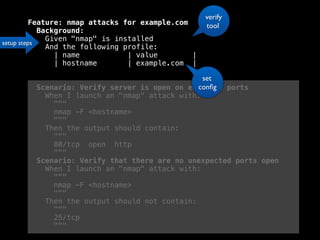
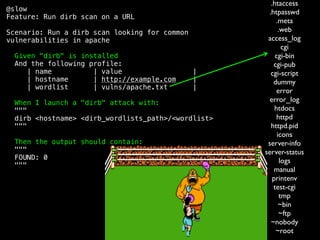
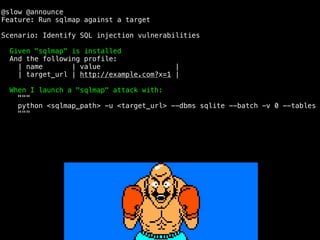
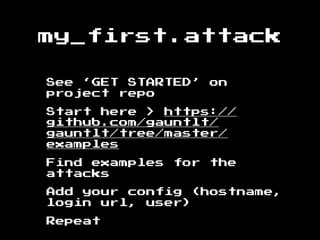
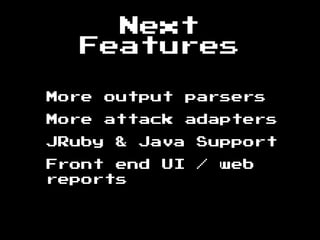
The document discusses the evolution of information security, highlighting the need for collaboration between development, operations, and security through the Rugged DevOps philosophy and the Gauntlt tool. Gauntlt facilitates communication between these teams and enables automated security testing using a variety of tools and behaviors, while promoting behavior-driven development. The document also emphasizes the importance of robust security practices and provides guidance on utilizing Gauntlt for security testing in software development.






![“[RISK ASSESSMENT]
INTRODUCES A DANGEROUS
FALLACY: THAT
STRUCTURED INADEQUACY
IS ALMOST AS GOOD AS
ADEQUACY AND THAT
UNDERFUNDED SECURITY
EFFORTS PLUS RISK
MANAGEMENT ARE ABOUT
AS GOOD AS PROPERLY
FUNDED SECURITY WORK”](https://image.slidesharecdn.com/ruggedbyexamplewithgauntlt-130807165129-phpapp02/85/Gauntlt-Rugged-By-Example-9-320.jpg)