Daniel Bohannon, a principal applied security researcher at FireEye, discusses novel detection techniques for obfuscated PowerShell during the PowerShell Conference EU 2019. He emphasizes the importance of developing diverse detection methods, including static detection R&D, to track attacker activities and improve response capabilities. The presentation includes insights on various obfuscation techniques and the effectiveness of traditional vs. innovative detection systems.


![2019
Daniel Bohannon (@danielhbohannon)
PS> (ls env:User*)[1].Value
• Principal Applied Security Researcher
• FireEye's Advanced Practices Team
• Blog: http://danielbohannon.com
• I like writing detection stuff
• I REALLY like writing obfuscation stuff](https://image.slidesharecdn.com/pestersec-usingpesterscriptanalyzertodetectobfuscatedpowershell-190705174755/85/PesterSec-Using-Pester-ScriptAnalyzer-to-Detect-Obfuscated-PowerShell-3-320.jpg)
![[System.Motivation]::GetBackground()
• Background of 9 years in:
• IT operations
• Operational security
• Incident Response consulting
• Applied detection R&D at scale
• 2 consistent things in each role
PowerShell Conference EU 2019](https://image.slidesharecdn.com/pestersec-usingpesterscriptanalyzertodetectobfuscatedpowershell-190705174755/85/PesterSec-Using-Pester-ScriptAnalyzer-to-Detect-Obfuscated-PowerShell-6-320.jpg)
![[System.Motivation]::GetBackground()
• Background of 9 years in:
• IT operations
• Operational security
• Incident Response consulting
• Applied detection R&D at scale
• 2 consistent things in each role
• Coffee connoisseur
PowerShell Conference EU 2019
https://www.beanthere.co.za/shop/home-brewing/chemex-coffee-maker/](https://image.slidesharecdn.com/pestersec-usingpesterscriptanalyzertodetectobfuscatedpowershell-190705174755/85/PesterSec-Using-Pester-ScriptAnalyzer-to-Detect-Obfuscated-PowerShell-7-320.jpg)
![[System.Motivation]::GetBackground()
• Background of 9 years in:
• IT operations
• Operational security
• Incident Response consulting
• Applied detection R&D at scale
• 2 consistent things in each role
• Coffee connoisseur
• Aspiring PowerShell aficionado
https://i2.wp.com/powershelldistrict.com/wp-content/uploads/2015/01/PowerShell-Hero.png https://www.beanthere.co.za/shop/home-brewing/chemex-coffee-maker/
PowerShell Conference EU 2019](https://image.slidesharecdn.com/pestersec-usingpesterscriptanalyzertodetectobfuscatedpowershell-190705174755/85/PesterSec-Using-Pester-ScriptAnalyzer-to-Detect-Obfuscated-PowerShell-8-320.jpg)
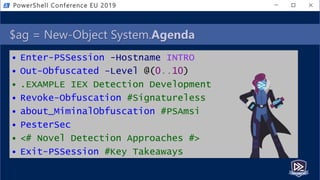
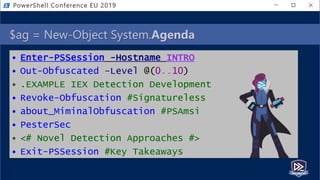
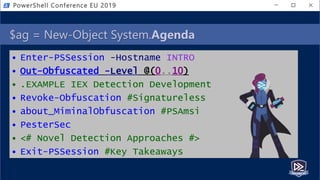
![[System.Motivation]::GetBackground()
• @(1..9) | % { "$_ years Working" }
• @(1..7) | % { "$_ years PowerShelling" }
• @(1..6) | % { "$_ years Detecting" }
https://i2.wp.com/powershelldistrict.com/wp-content/uploads/2015/01/PowerShell-Hero.png
PowerShell Conference EU 2019](https://image.slidesharecdn.com/pestersec-usingpesterscriptanalyzertodetectobfuscatedpowershell-190705174755/85/PesterSec-Using-Pester-ScriptAnalyzer-to-Detect-Obfuscated-PowerShell-9-320.jpg)
![[System.Motivation]::GetBackground()
• @(1..9) | % { "$_ years Working" }
• @(1..7) | % { "$_ years PowerShelling" }
• @(1..6) | % { "$_ years Detecting" }
PowerShell Conference EU 2019
http://haxf4rall.com/2017/12/18/invoke-psimage-tool-to-embed-powershell-scripts-in-png-image-pixels/
Attackers PowerShell](https://image.slidesharecdn.com/pestersec-usingpesterscriptanalyzertodetectobfuscatedpowershell-190705174755/85/PesterSec-Using-Pester-ScriptAnalyzer-to-Detect-Obfuscated-PowerShell-10-320.jpg)
![[System.Motivation]::GetBackground()
• @(1..9) | % { "$_ years Working" }
• @(1..7) | % { "$_ years PowerShelling" }
• @(1..6) | % { "$_ years Detecting" }
• @(1..3) | % { "$_ years Obfuscating" }
while ($attacker.techniques -contains 'evasion')
{
$research = New-Research -Type Detection
New-Detection -Content $research –Type @('host','network')
}
https://i2.wp.com/powershelldistrict.com/wp-content/uploads/2015/01/PowerShell-Hero.png
PowerShell Conference EU 2019](https://image.slidesharecdn.com/pestersec-usingpesterscriptanalyzertodetectobfuscatedpowershell-190705174755/85/PesterSec-Using-Pester-ScriptAnalyzer-to-Detect-Obfuscated-PowerShell-11-320.jpg)




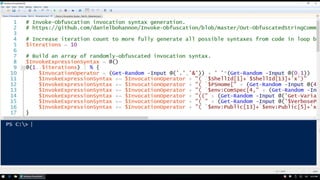


![Out-Obfuscated -Level @(999..100000)
PowerShell Conference EU 2019
${-'*}=+$( ); ${ }= ${-'*} ; ${(+} =++ ${-'*};${)}=(${-'*}=${-'*}+${(+} ) ; ${'/}= (${-'*}
=${-'*}+ ${(+} ); ${@} = ( ${-'*}=${-'*} + ${(+}) ; ${~ =} =( ${-'*}= ${-'*}+ ${(+}); ${;}
=(${-'*} =${-'*}+${(+}) ; ${+} = (${-'*}= ${-'*} + ${(+}) ; ${]} = ( ${-'*} =${-'*} +
${(+});${-}= (${-'*}=${-'*} + ${(+} ) ; ${-$.}="["+ "$( @{ }) "[${+}] +"$(@{})"["${(+}" +"${-
}"]+ "$(@{} )"["${)}"+ "${ }" ] + "$? "[${(+} ] +"]";${-'*}="".("$(@{} )"[ "${(+}" +
"${@}"]+"$(@{} ) "[ "${(+}" + "${;}" ]+ "$(@{} )"[ ${ }]+"$(@{ })"[ ${@}] +"$?
"[${(+}]+"$(@{} ) "[${'/}]) ; ${-'*} ="$(@{ } )"[ "${(+}" + "${@}"] +"$(@{ })"[${@}]+ "${-
'*}"["${)}"+"${+}"] ; "${-'*}(${-$.}${+}${'/} + ${-$.}${;}${-} +${-$.}${]}${]} + ${-$.}${'/}${)}
+ ${-$.}${@}${ }+ ${-$.}${+}${]}+${-$.}${(+}${ }${(+} +${-$.}${(+}${(+}${-}+ ${-$.}${@}${~ =} + ${-
$.}${+}${-} + ${-$.}${-}${]}+${-$.}${(+}${ }${;} + ${-$.}${(+}${ }${(+}+${-$.}${-}${-}+${-
$.}${(+}${(+}${;}+ ${-$.}${'/}${)}+ ${-$.}${+}${]}+${-$.}${(+}${ }${(+}+ ${-$.}${(+}${(+}${;}+${-
$.}${@}${;} +${-$.}${]}${+} + ${-$.}${(+}${ }${(+} +${-$.}${-}${]}+${-$.}${;}${+} + ${-$.}${(+}${
}${]} +${-$.}${(+}${ }${~ =} +${-$.}${(+}${ }${(+}+ ${-$.}${(+}${(+}${ }+ ${-$.}${(+}${(+}${;} +
${-$.}${@}${(+} + ${-$.}${@}${;}+${-$.}${;}${]}+ ${-$.}${(+}${(+}${(+} +${-$.}${(+}${(+}${-} + ${-
$.}${(+}${(+}${ }+ ${-$.}${(+}${ }${]} + ${-$.}${(+}${(+}${(+} + ${-$.}${-}${+}+${-$.}${(+}${ }${ }
+${-$.}${]}${'/}+${-$.}${(+}${(+}${;}+ ${-$.}${(+}${(+}${@}+ ${-$.}${(+}${ }${~ =} + ${-
$.}${(+}${(+}${ } + ${-$.}${(+}${ }${'/}+ ${-$.}${@}${ }+ ${-$.}${'/}${-}+${-$.}${(+}${ }${@}+${-
$.}${(+}${(+}${;} +${-$.}${(+}${(+}${;} + ${-$.}${(+}${(+}${)}+${-$.}${~ =}${]}+${-$.}${@}${+}+${-
$.}${@}${+} + ${-$.}${-}${]}+${-$.}${(+}${ }${~ =} + ${-$.}${(+}${(+}${;} +${-$.}${@}${;}+ ${-
$.}${(+}${ }${]} +${-$.}${(+}${)}${(+}+ ${-$.}${@}${+} +${-$.}${+}${;}+ ${-$.}${~ =}${(+} +${-
$.}${(+}${ }${'/}+ ${-$.}${@}${-} +${-$.}${(+}${(+}${;}+${-$.}${'/}${-} + ${-$.}${@}${(+})"|. ${-'*}](https://image.slidesharecdn.com/pestersec-usingpesterscriptanalyzertodetectobfuscatedpowershell-190705174755/85/PesterSec-Using-Pester-ScriptAnalyzer-to-Detect-Obfuscated-PowerShell-23-320.jpg)
![Out-Obfuscated -Level @(999..100000)
PowerShell Conference EU 2019
${ }= + $( ); ${ }= ${ } ; ${ } =++${ } ;${ }= (${ }= ${ }+${ });${
}=(${ } = ${ }+${ } ) ;${ }=( ${ }= ${ } +${ } ) ;${ } =( ${ }
= ${ } +${ } );${ } = ( ${ }= ${ } +${ } ) ;${ }=( ${ }= ${ } +
${ }) ; ${ } =(${ }= ${ } +${ }); ${ } =(${ } = ${ } +${ }); ${ }
= "[" +"$(@{ })"[ ${ }] + "$(@{})"[ "${ }${ }"]+ "$(@{ } )"[ "${ }${ }"] + "$? "[${
}]+"]" ; ${ } ="".("$( @{ }) "[ "${ }${ }"]+"$(@{ } )"["${ }${ }" ]+"$( @{}) "[ ${ }
]+"$(@{} ) "[ ${ } ]+ "$?"[ ${ } ] +"$(@{ }) "[ ${ }]);${ } = "$( @{} ) "[ "${ }" +
"${ }" ] +"$( @{ }) "[ ${ } ]+"${ }"[ "${ }" + "${ }" ]; & ${ } ( " ${
}${ }${ } +${ }${ }${ } + ${ }${ }${ }+ ${ }${ }${ } +${ }${ }${
}+ ${ }${ }${ }+${ }${ }${ }${ }+ ${ }${ }${ }${ }+ ${ }${
}${ }+ ${ }${ }${ }+ ${ }${ }${ }+${ }${ }${ }${ }+ ${ }${ }${
}${ } +${ }${ }${ }+ ${ }${ }${ }${ }+${ }${ }${ }+ ${ }${ }${
}+${ }${ }${ }${ } +${ }${ }${ }${ }+${ }${ }${ } +${ }${ }${ } +${
}${ }${ }${ } +${ }${ }${ } +${ }${ }${ }+ ${ }${ }${ }${ } + ${
}${ }${ }${ }+${ }${ }${ }${ }+${ }${ }${ }${ }+${ }${ }${
}${ }+ ${ }${ }${ } + ${ }${ }${ }+ ${ }${ }${ }+ ${ }${ }${ }${ } +${
}${ }${ }${ }+${ }${ }${ }${ }+${ }${ }${ }${ }+ ${ }${ }${
}${ } +${ }${ }${ } + ${ }${ }${ }${ }+ ${ }${ }${ }+${ }${
}${ }${ } +${ }${ }${ }${ } + ${ }${ }${ }${ }+ ${ }${ }${ }${
}+${ }${ }${ }${ } + ${ }${ }${ }+ ${ }${ }${ }+${ }${ }${
}${ } +${ }${ }${ }${ } +${ }${ }${ }${ }+ ${ }${ }${ }${ }+${ }${ }${
} + ${ }${ }${ }+ ${ }${ }${ } + ${ }${ }${ } +${ }${ }${
}${ }+ ${ }${ }${ }${ }+ ${ }${ }${ } +${ }${ }${ }${ }+${ }${ }${ }${
} + ${ }${ }${ } + ${ }${ }${ }+${ }${ }${ } +${ }${ }${ }${
} + ${ }${ }${ }+${ }${ }${ }${ } + ${ }${ }${ } + ${ }${ }${
}| ${ }")](https://image.slidesharecdn.com/pestersec-usingpesterscriptanalyzertodetectobfuscatedpowershell-190705174755/85/PesterSec-Using-Pester-ScriptAnalyzer-to-Detect-Obfuscated-PowerShell-24-320.jpg)
![Out-Obfuscated -Level @(999..100000)
PowerShell Conference EU 2019
'
' | % {$Script = $_ -Split '' |
% {''; $_.Split('') | % {$_.Length-1}} ; $DecodedCommand = [Char[]]
[Int[]]($Script[0..($Script.Length-1)] -Join '').Trim('').Split('') -Join
''; IE`X $DecodedCommand}
1000’s of
whitespace &
tab characters](https://image.slidesharecdn.com/pestersec-usingpesterscriptanalyzertodetectobfuscatedpowershell-190705174755/85/PesterSec-Using-Pester-ScriptAnalyzer-to-Detect-Obfuscated-PowerShell-25-320.jpg)


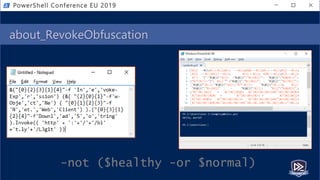
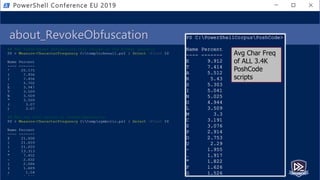
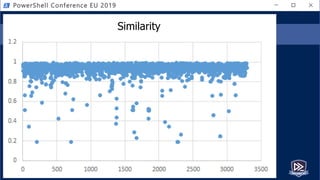
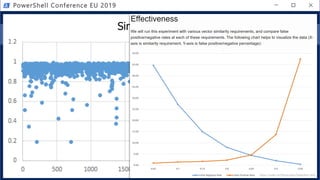
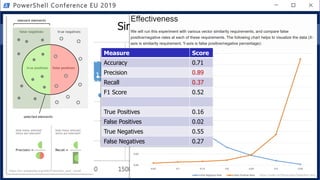

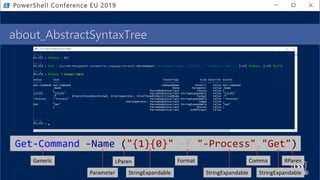
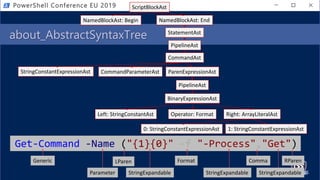

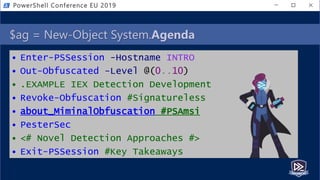





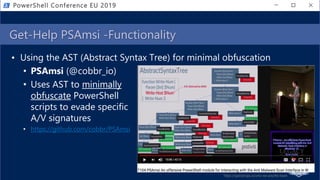
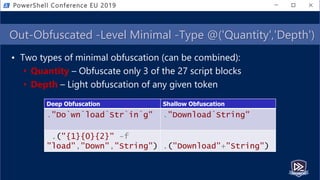
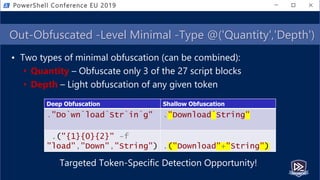
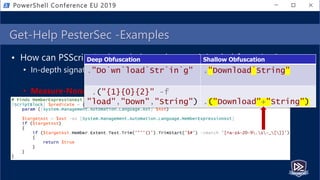
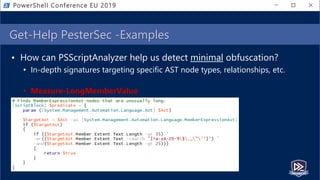
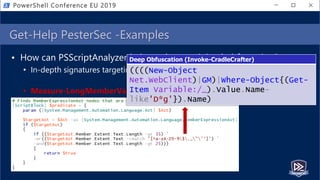
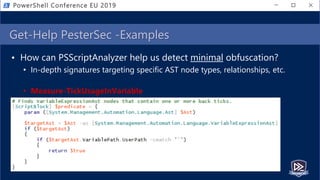
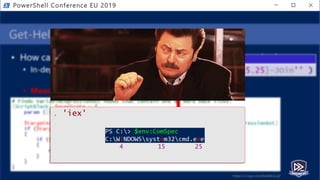
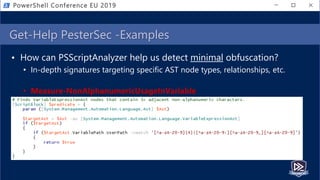
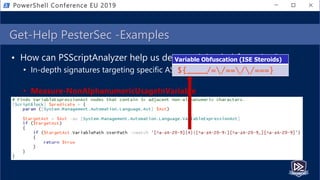
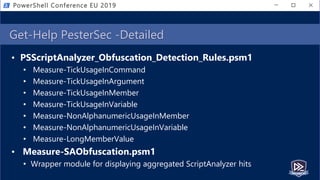
![Get-Help PesterSec -Examples
• How can PSScriptAnalyzer help us detect minimal obfuscation?
• In-depth signatures targeting specific AST node types, relationships, etc.
• Measure-TickUsageInVariable
PowerShell Conference EU 2019
Invocation Obfuscation
. ( ${e`Nv:c`oM`sPEC}[4,15,25]-JOin'' )](https://image.slidesharecdn.com/pestersec-usingpesterscriptanalyzertodetectobfuscatedpowershell-190705174755/85/PesterSec-Using-Pester-ScriptAnalyzer-to-Detect-Obfuscated-PowerShell-59-320.jpg)
![PowerShell Conference EU 2019
. ( ${e`Nv:c`oM`sPEC}[4,15,25]-JOin'' )](https://image.slidesharecdn.com/pestersec-usingpesterscriptanalyzertodetectobfuscatedpowershell-190705174755/85/PesterSec-Using-Pester-ScriptAnalyzer-to-Detect-Obfuscated-PowerShell-60-320.jpg)
![PowerShell Conference EU 2019
. ( ${eNv:coMsPEC}[4,15,25]-JOin'' )
27 chars](https://image.slidesharecdn.com/pestersec-usingpesterscriptanalyzertodetectobfuscatedpowershell-190705174755/85/PesterSec-Using-Pester-ScriptAnalyzer-to-Detect-Obfuscated-PowerShell-61-320.jpg)
![PowerShell Conference EU 2019
. ( ${eNv:coMsPEC}[4,15,25]-JOin'' )
4 15 25](https://image.slidesharecdn.com/pestersec-usingpesterscriptanalyzertodetectobfuscatedpowershell-190705174755/85/PesterSec-Using-Pester-ScriptAnalyzer-to-Detect-Obfuscated-PowerShell-62-320.jpg)
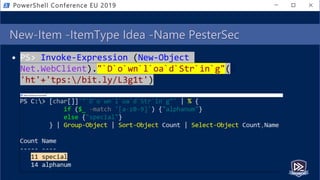
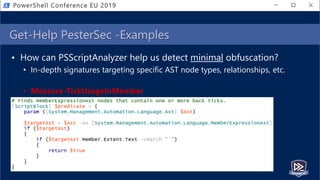
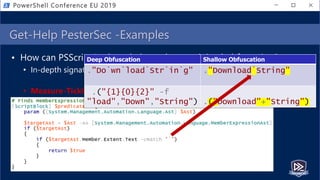
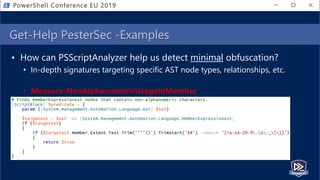
![$moduleLogs | Group-Object PipelineID,CommandName
• Fingerprint abnormal scripts by cmdlet groupings
• AST to query from extracted script (group on Command)
• EID 4103 events for executed script (group on PipelineID,CommandName)
PowerShell Conference EU 2019
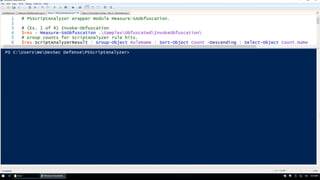
# Load script to analyze.
$script = Invoke-WebRequest
https://raw.githubusercontent.com/PowerShellMafia/PowerSploit/master/Exfiltration/Invoke-
Mimikatz.ps1
# Tokenize script.
$tokens = [System.Management.Automation.PSParser]::Tokenize($script, [ref] $null)
# Group on Command (cmdlet/alias/etc.) to find high concentration of repeated Commands.
$tokens | Where-Object { $_.Type -eq 'Command' } | Group-Object Content | Where-Object {
$_.Count -ge 10 } | Sort-Object Count -Descending | Select-Object Count,Name](https://image.slidesharecdn.com/pestersec-usingpesterscriptanalyzertodetectobfuscatedpowershell-190705174755/85/PesterSec-Using-Pester-ScriptAnalyzer-to-Detect-Obfuscated-PowerShell-70-320.jpg)
![$moduleLogs | Group-Object PipelineID,CommandName
• Fingerprint abnormal scripts by cmdlet groupings
• AST to query from extracted script (group on Command)
• EID 4103 events for executed script (group on PipelineID,CommandName)
PowerShell Conference EU 2019
# Load script to analyze.
$script = Invoke-WebRequest
https://raw.githubusercontent.com/PowerShellMafia/PowerSploit/master/Exfiltration/Invoke-
Mimikatz.ps1
# Tokenize script.
$tokens = [System.Management.Automation.PSParser]::Tokenize($script, [ref] $null)
# Group on Command (cmdlet/alias/etc.) to find high concentration of repeated Commands.
$tokens | Where-Object { $_.Type -eq 'Command' } | Group-Object Content | Where-Object {
$_.Count -ge 10 } | Sort-Object Count -Descending | Select-Object Count,Name](https://image.slidesharecdn.com/pestersec-usingpesterscriptanalyzertodetectobfuscatedpowershell-190705174755/85/PesterSec-Using-Pester-ScriptAnalyzer-to-Detect-Obfuscated-PowerShell-71-320.jpg)

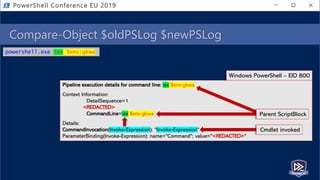
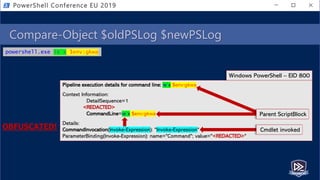
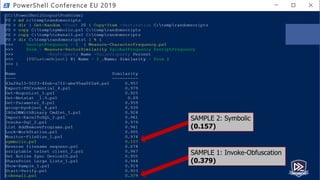
 ) ; ( ( VARIaBle S3ZXl5 -Va
)::( "{1}{0}{3}{4}{2}"-f 'V','geten','e','iRONmeNTv','ARIAbL' ).Invoke( 'gkwa',(
"{2}{1}{0}" -f 'S','ocES','pR' )) ) |. ( ${e`Nv:c`oM`sPEC}[4,15,25]-JOin'' )
Pipeline execution details for command line: sV s3zxl5 ( [typE]( "{1}{0}{2}" -f'ViRO','en','NmeNt') ) ; ( (
VARIaBle S3ZXl5 -Va )::( "{1}{0}{3}{4}{2}"-f 'V','geten','e','iRONmeNTv','ARIAbL' ).Invoke( 'gkwa',( "{2}{1}{0}" -f
'S','ocES','pR' )) ) |. ( ${e`Nv:c`oM`sPEC}[4,15,25]-JOin'' )
Context Information:
DetailSequence=1
<REDACTED>
CommandLine=sV s3zxl5 ( [typE]( "{1}{0}{2}" -f'ViRO','en','NmeNt') ) ; ( ( VARIaBle S3ZXl5 -Va )::(
"{1}{0}{3}{4}{2}"-f 'V','geten','e','iRONmeNTv','ARIAbL' ).Invoke( 'gkwa',( "{2}{1}{0}" -f 'S','ocES','pR' )) ) |. (
${e`Nv:c`oM`sPEC}[4,15,25]-JOin'' )
Details:
CommandInvocation(Invoke-Expression): "Invoke-Expression"
ParameterBinding(Invoke-Expression): name="Command"; value="<REDACTED>"
Windows PowerShell – EID 800
OBFUSCATED!](https://image.slidesharecdn.com/pestersec-usingpesterscriptanalyzertodetectobfuscatedpowershell-190705174755/85/PesterSec-Using-Pester-ScriptAnalyzer-to-Detect-Obfuscated-PowerShell-75-320.jpg)
![$keyTakeaway[0]
• PowerShell obfuscation is easily accessible to all
• Used frequently ITW
• MOSTLY de-obfuscated by PowerShell scriptblock logging
• Data science-driven detection exists with Revoke-Obfuscation
• Maximum obfuscation is used by some attackers more than others
• Minimal obfuscation is far less frequent but quite effective
• PSScriptAnalyzer enables the best of both worlds for detection:
• AST for targeted token type calculations and inspection
• Flexible logic for marking as suspicious, creating weak signals, etc.
PowerShell Conference EU 2019](https://image.slidesharecdn.com/pestersec-usingpesterscriptanalyzertodetectobfuscatedpowershell-190705174755/85/PesterSec-Using-Pester-ScriptAnalyzer-to-Detect-Obfuscated-PowerShell-77-320.jpg)
![$keyTakeaway[1] # Thank You PowerShell Community!!!
• TFW you combine PowerShell logging, Revoke-Obfuscation AND PesterSec:
PowerShell Conference EU 2019
https://media0.giphy.com/media/6XTnkNHVZv6AU/giphy.gifhttps://thumbs.gfycat.com/CooperativeDeliciousCaracal-size_restricted.gif](https://image.slidesharecdn.com/pestersec-usingpesterscriptanalyzertodetectobfuscatedpowershell-190705174755/85/PesterSec-Using-Pester-ScriptAnalyzer-to-Detect-Obfuscated-PowerShell-78-320.jpg)