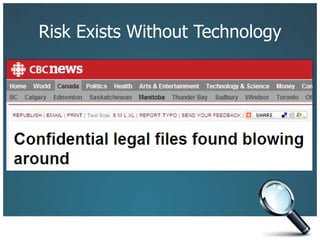
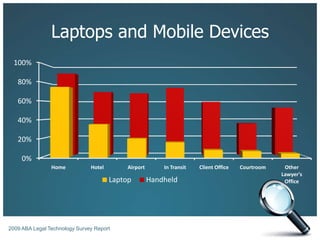
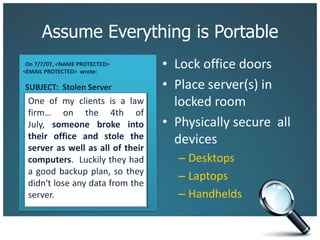
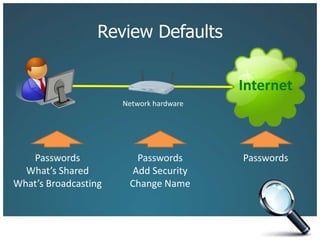
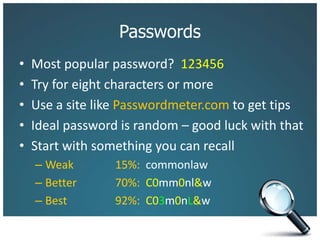
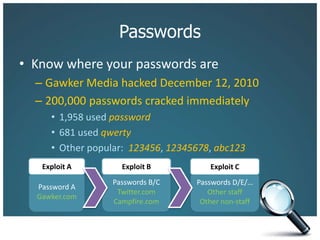
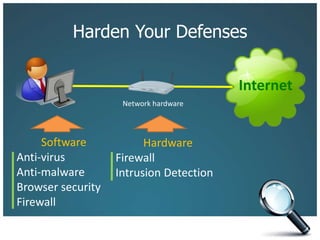
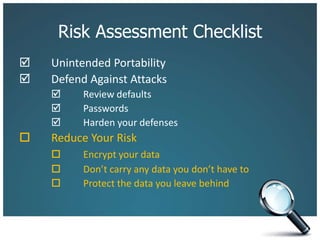
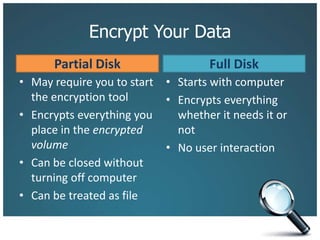
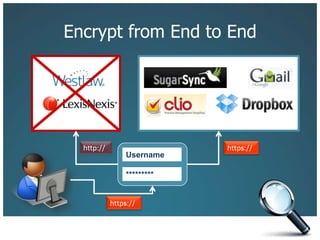
The document discusses the risks associated with technology in maintaining confidentiality, particularly for legal professionals. It emphasizes the need for robust security measures, such as using strong and unique passwords, encrypting data, and secure backups, as well as the management of mobile devices to prevent data loss or theft. Ultimately, it calls for careful planning and awareness in handling sensitive information in a digital environment.