Risk Assessment KPIs and KRIs:
•Download as PPTX, PDF•
0 likes•77 views
Evaluate the performance and risks in assessing and managing organizational risks to make informed decisions.
Report
Share
Report
Share
Recommended
Threat Intelligence KPIs and KRIs

This document outlines categories of potential issues that can arise in a threat intelligence program. It identifies 15 key risk indicators (KRIs) across 7 categories: data collection, threat analysis, intelligence sharing, indicators, response, regulatory compliance, and reporting. Addressing these KRIs can help organizations track the effectiveness and risks of their threat intelligence efforts.
Risk-Management-Maturity-Model.pdf

This document outlines a risk management maturity model with five levels across several areas of risk management. At level 1, there is little risk management practice and risks are not well identified, analyzed, or planned for. At level 2, some basic risk management processes are used inconsistently. At level 3, standard risk management processes are used but still have some gaps. Level 4 involves thorough and consistent risk management processes integrated with project management. Level 5 represents optimized risk management where processes are tailored to projects and risk information is systematically used, archived and learned from.
GRC Program KPIs and KRIs

GRC Program KPIs and KRIs:
Track the effectiveness and potential risks of Governance, Risk, and Compliance (GRC) initiatives to maintain regulatory compliance and mitigate risks.
Vulnerability Management KPIs and KRIs

This document outlines key performance indicators and key risk indicators for vulnerability management across various categories. It identifies 19 metrics for measuring the effectiveness of vulnerability detection and scanning, vulnerability assessment, patch management, asset classification, reporting and analytics, compliance and auditing, incident response, vulnerability scanning, vendor and third-party risk management, and training and awareness programs. Example metrics include vulnerability remediation rates, patch compliance rates, accuracy of vulnerability reporting, and timeliness of incident response.
Incident Response KPIs and KRIs

Incident Response KPIs and KRIs:
Academy.skillweed.com
Measure the efficiency and risks of incident response processes to minimize the impact of security incidents.
Risk Mgt Training Slides.pptx

This document provides an introduction to risk management. It outlines the aims to explain why risk management is relevant and its components through the risk management cycle. The cycle includes identifying risks, assessing their impact and likelihood, evaluating existing controls, taking action if needed, and monitoring and reporting risks. Risks are categorized into financial, operational, reputational, governance, compliance, and strategic groupings. A risk register is used to record risk details like description, controls, impact, likelihood, further actions, and owners. Tips for success include involving staff, ensuring controls are effective, and designating risk owners. Reasons for risk management failure include limited scope and lack of management support.
Risk Mgt Training Slides.pdf

This document provides an introduction to risk management. It outlines the aims to explain why risk management is relevant and its components. It describes the risk management cycle as a 5 step process: 1) define objectives and strategy, 2) identify risks, 3) evaluate controls, 4) take action, and 5) monitor and report. It also discusses categorizing risks, creating a risk register to record risk details, and tips for effective risk management.
Risk Managment Training - Theory and Practice

This document provides an introduction to risk management. It outlines the aims to explain why risk management is relevant and its components. It describes the risk management cycle as a 5 step process: 1) define objectives and strategy, 2) identify risks, 3) evaluate controls, 4) take action, and 5) monitor and report. It also discusses categorizing risks, creating a risk register to record risk details, and tips for effective risk management.
Recommended
Threat Intelligence KPIs and KRIs

This document outlines categories of potential issues that can arise in a threat intelligence program. It identifies 15 key risk indicators (KRIs) across 7 categories: data collection, threat analysis, intelligence sharing, indicators, response, regulatory compliance, and reporting. Addressing these KRIs can help organizations track the effectiveness and risks of their threat intelligence efforts.
Risk-Management-Maturity-Model.pdf

This document outlines a risk management maturity model with five levels across several areas of risk management. At level 1, there is little risk management practice and risks are not well identified, analyzed, or planned for. At level 2, some basic risk management processes are used inconsistently. At level 3, standard risk management processes are used but still have some gaps. Level 4 involves thorough and consistent risk management processes integrated with project management. Level 5 represents optimized risk management where processes are tailored to projects and risk information is systematically used, archived and learned from.
GRC Program KPIs and KRIs

GRC Program KPIs and KRIs:
Track the effectiveness and potential risks of Governance, Risk, and Compliance (GRC) initiatives to maintain regulatory compliance and mitigate risks.
Vulnerability Management KPIs and KRIs

This document outlines key performance indicators and key risk indicators for vulnerability management across various categories. It identifies 19 metrics for measuring the effectiveness of vulnerability detection and scanning, vulnerability assessment, patch management, asset classification, reporting and analytics, compliance and auditing, incident response, vulnerability scanning, vendor and third-party risk management, and training and awareness programs. Example metrics include vulnerability remediation rates, patch compliance rates, accuracy of vulnerability reporting, and timeliness of incident response.
Incident Response KPIs and KRIs

Incident Response KPIs and KRIs:
Academy.skillweed.com
Measure the efficiency and risks of incident response processes to minimize the impact of security incidents.
Risk Mgt Training Slides.pptx

This document provides an introduction to risk management. It outlines the aims to explain why risk management is relevant and its components through the risk management cycle. The cycle includes identifying risks, assessing their impact and likelihood, evaluating existing controls, taking action if needed, and monitoring and reporting risks. Risks are categorized into financial, operational, reputational, governance, compliance, and strategic groupings. A risk register is used to record risk details like description, controls, impact, likelihood, further actions, and owners. Tips for success include involving staff, ensuring controls are effective, and designating risk owners. Reasons for risk management failure include limited scope and lack of management support.
Risk Mgt Training Slides.pdf

This document provides an introduction to risk management. It outlines the aims to explain why risk management is relevant and its components. It describes the risk management cycle as a 5 step process: 1) define objectives and strategy, 2) identify risks, 3) evaluate controls, 4) take action, and 5) monitor and report. It also discusses categorizing risks, creating a risk register to record risk details, and tips for effective risk management.
Risk Managment Training - Theory and Practice

This document provides an introduction to risk management. It outlines the aims to explain why risk management is relevant and its components. It describes the risk management cycle as a 5 step process: 1) define objectives and strategy, 2) identify risks, 3) evaluate controls, 4) take action, and 5) monitor and report. It also discusses categorizing risks, creating a risk register to record risk details, and tips for effective risk management.
Risk Mgt Training Slides (1).pptx

This document provides an introduction to risk management. It outlines the aims to explain why risk management is relevant and its components through the risk management cycle. It describes defining objectives and goals, identifying risks, evaluating existing controls, taking action to treat risks, and ongoing monitoring. Risks are categorized as financial, operational, reputational, governance, compliance, and strategic. A risk register is presented as a tool to record risk details like description, controls, impact, likelihood, risk owner and further actions. Tips and common reasons for risk management failure are also discussed.
Presentation on QRM

1. Quality Risk Management (QRM) is a systematic process that organizes information to support risk-based decisions. It involves identifying hazards, analyzing risks associated with hazards, and managing risks.
2. Several tools can be used for risk analysis including Failure Mode and Effects Analysis (FMEA) which analyzes potential risks and their effects. Risk is evaluated by considering severity, probability of occurrence, detection, and calculating a Risk Priority Number (RPN).
3. Appropriate control measures should be identified to reduce risks to an acceptable level. Residual risk after controls is implemented should be re-evaluated.
Risk Mgt Training Slides STUDENT.pptx

This document provides an introduction to risk management. It outlines the key components of a risk management process, including defining objectives, identifying and assessing risks, evaluating existing controls, taking action to address risks, and ongoing monitoring. The risk management cycle involves 5 steps: 1) defining objectives and strategy, 2) identifying risks, 3) evaluating controls, 4) taking action, and 5) monitoring and reporting. Risks can be categorized in different ways, such as financial, operational, reputational, governance, and strategic. A risk register is used to record risk details like description, impact, likelihood, owner, and further actions needed. Regular review and involvement of stakeholders is advised for effective risk management.
Risk management and green events

The document discusses risk management for events. It defines risk and explains that risk needs to be managed to reduce surprises, allocate resources effectively, support decision making, and comply with regulations. A risk management process is then outlined that involves identifying the event and stakeholders, risks and their causes, controls for each risk, performing a risk analysis, evaluating risks, writing a risk management plan, implementing and communicating the plan, and monitoring and reviewing. Typical risk factors for events are also provided across various categories like people, infrastructure, weather, and activities.
Risk management

It is said that a leader’s job is to take people where they have not been before. Leaders often have to take risks - leading their organisation into unfamiliar territory – but the risks are always calculated and the decisions always informed. Wanting always to play safe and not risk making any mistakes does not sit comfortably with good leadership. As Drucker says, ‘People who don’t take risks generally make about two big mistakes a year. People who do take risks generally make about two big mistakes a year.’
RMF KPIs and KRIs

RMF KPIs and KRIs:
Academy.skillweed.com
Gauge the performance and risks related to the Risk Management Framework (RMF) for securing information systems.
Risk management in healthcare

Risk Management Training Slides.
Slides prepared based on "The Healthcare Quality Handbook" by Janet A Brown. Very useful health care quality reference for CPHQ exam preparation. For more slides, contact ckmujeeb@hotmail.com
SIEM KPIs and KRIs

SIEM KPIs and KRIs:
Academy.skillweed.com
Assess the performance and risks associated with Security Information and Event Management (SIEM) systems for proactive threat detection and response.
Fundamentals of Project Planning, Scheduling, Monitoring & Control

Fundamentals of Project Planning, Scheduling, Monitoring & ControlAssociation for Project Management
Feedback from the survey undertaken by the attendees
The attendees at each table were provided with a topic related to Project Planning, Scheduling, Monitoring & Control and were asked to list their top 5 ‘good practice’ lessons learned.
Topics: Planning, Change Management, Reporting, Scope, Schedule Management, Risk Management
Change Management 1. Early stakeholder engagement 2. Configuration Control 3. Analyse impacts 4. Risk Management 5. Leadership 6. Evaluation / lessons learned 7. Cost control
Project managment 10

The document discusses the key processes in project risk management: planning risk management, identifying risks, performing qualitative and quantitative risk analysis, planning risk responses, and monitoring and controlling risks. It provides details on each process, including inputs, tools and techniques, and outputs. The overall aim is to understand how to approach risk management in projects by identifying risks, analyzing them, developing responses, and continuously monitoring risks and the effectiveness of responses throughout the project lifecycle.
FedRAMP Compliance KPIs and KRIs

FedRAMP Compliance KPIs and KRIs:
Academy.skillweed.com
Monitor the performance and risks associated with Federal Risk and Authorization Management Program (FedRAMP) compliance for secure cloud services.
Presentation Guildmore Risk Mgt Mar 2014

Risk assessment is a systematic approach to identifying hazards and controlling risks. It involves establishing the context, identifying risks, analyzing and assessing their likelihood and potential impact, prioritizing them, treating risks by avoiding, reducing, transferring or retaining them, and communicating and monitoring the process on an ongoing basis. Maintaining a risk register that lists risks, analyses them, and assigns treatment options can help prevent failures and demonstrate that risks were properly managed if issues later occur.
Reliability

Risk assessment is the process of identifying risks, determining their impact and probability, and associating controls. It measures potential loss and the likelihood of loss occurring. Common types of risk assessment include qualitative, which uses terms like high, medium, low, and quantitative, which uses dollars and formulas. Performing a risk assessment involves defining its purpose, identifying the system or product, selecting an approach, gathering information, developing scenarios, estimating risks, and producing a report. Elements of good risk assessments include clear instructions, segmented questions, simplified responses, commentary areas, support contacts, focus on leaders and executors, and feedback.
Link NCA: Nutrition Causal Analysis

The document provides an overview of the Link NCA methodology, which is a structured and participatory study used to understand the causes of undernutrition in a local context. The methodology involves a 5-step process: 1) preparatory phase, 2) identifying risk factors and pathways, 3) community surveys, 4) synthesizing results and building consensus, and 5) communicating results and planning responses. The goal is to develop multi-sector interventions and programs to prevent undernutrition by understanding its main pathways and risk factors in a given area. Since 2010, over 15 Link NCA studies have been conducted globally to identify the most appropriate nutrition-sensitive responses.
Risk minimisation activities - identification and application

This presentation provides an overview of the principles for selecting and implementing risk minimisation tools
Risk minimisation activities associated with risk management plans

This presentation provides an overview of risk minimisation activities for medicines and the tools or activities that may be used in a risk management plan.
Risk Management

This was a presentation I put together based off of Rita Mulcahy's PMP Exam Prep 7th edition on Risk Management
Clinical risk management

1) Clinical risk management (CRM) aims to improve healthcare quality and safety by identifying and preventing circumstances that put patients at risk of harm.
2) Risk management involves risk identification, analysis, treatment, and control to minimize chances of errors and learn from past issues.
3) All healthcare staff have responsibilities for risk management including reporting incidents, identifying risks, and practicing risk prevention in their daily work.
Clinical Risk Management

1) Clinical risk management (CRM) aims to improve healthcare quality and safety by identifying and preventing circumstances that put patients at risk of harm.
2) Risk management involves risk identification, analysis, treatment, and control to minimize chances of errors and learn from past issues.
3) All healthcare staff have responsibilities for risk management including reporting incidents, identifying risks, and practicing risk prevention in their daily work.
Ihor Pavlenko: PMO Risk Management (UA )

Ihor Pavlenko: PMO Risk Management (UA)
Lemberg PMO School 2023
Website – https://lembs.com/pmoschool
Youtube – https://www.youtube.com/startuplviv
FB – https://www.facebook.com/pmdayconference
GDPR Compliance KPIs and KRIs

GDPR Compliance KPIs and KRIs:
Academy.skillweed.com
Evaluate the performance and risks related to complying with the General Data Protection Regulation (GDPR) to protect data privacy.
Data Privacy KPIs and KRIs

Data Privacy KPIs and KRIs:
Academy.skillweed.com
Monitor the performance and risks related to data privacy measures to ensure compliance with data protection regulations.
More Related Content
Similar to Risk Assessment KPIs and KRIs:
Risk Mgt Training Slides (1).pptx

This document provides an introduction to risk management. It outlines the aims to explain why risk management is relevant and its components through the risk management cycle. It describes defining objectives and goals, identifying risks, evaluating existing controls, taking action to treat risks, and ongoing monitoring. Risks are categorized as financial, operational, reputational, governance, compliance, and strategic. A risk register is presented as a tool to record risk details like description, controls, impact, likelihood, risk owner and further actions. Tips and common reasons for risk management failure are also discussed.
Presentation on QRM

1. Quality Risk Management (QRM) is a systematic process that organizes information to support risk-based decisions. It involves identifying hazards, analyzing risks associated with hazards, and managing risks.
2. Several tools can be used for risk analysis including Failure Mode and Effects Analysis (FMEA) which analyzes potential risks and their effects. Risk is evaluated by considering severity, probability of occurrence, detection, and calculating a Risk Priority Number (RPN).
3. Appropriate control measures should be identified to reduce risks to an acceptable level. Residual risk after controls is implemented should be re-evaluated.
Risk Mgt Training Slides STUDENT.pptx

This document provides an introduction to risk management. It outlines the key components of a risk management process, including defining objectives, identifying and assessing risks, evaluating existing controls, taking action to address risks, and ongoing monitoring. The risk management cycle involves 5 steps: 1) defining objectives and strategy, 2) identifying risks, 3) evaluating controls, 4) taking action, and 5) monitoring and reporting. Risks can be categorized in different ways, such as financial, operational, reputational, governance, and strategic. A risk register is used to record risk details like description, impact, likelihood, owner, and further actions needed. Regular review and involvement of stakeholders is advised for effective risk management.
Risk management and green events

The document discusses risk management for events. It defines risk and explains that risk needs to be managed to reduce surprises, allocate resources effectively, support decision making, and comply with regulations. A risk management process is then outlined that involves identifying the event and stakeholders, risks and their causes, controls for each risk, performing a risk analysis, evaluating risks, writing a risk management plan, implementing and communicating the plan, and monitoring and reviewing. Typical risk factors for events are also provided across various categories like people, infrastructure, weather, and activities.
Risk management

It is said that a leader’s job is to take people where they have not been before. Leaders often have to take risks - leading their organisation into unfamiliar territory – but the risks are always calculated and the decisions always informed. Wanting always to play safe and not risk making any mistakes does not sit comfortably with good leadership. As Drucker says, ‘People who don’t take risks generally make about two big mistakes a year. People who do take risks generally make about two big mistakes a year.’
RMF KPIs and KRIs

RMF KPIs and KRIs:
Academy.skillweed.com
Gauge the performance and risks related to the Risk Management Framework (RMF) for securing information systems.
Risk management in healthcare

Risk Management Training Slides.
Slides prepared based on "The Healthcare Quality Handbook" by Janet A Brown. Very useful health care quality reference for CPHQ exam preparation. For more slides, contact ckmujeeb@hotmail.com
SIEM KPIs and KRIs

SIEM KPIs and KRIs:
Academy.skillweed.com
Assess the performance and risks associated with Security Information and Event Management (SIEM) systems for proactive threat detection and response.
Fundamentals of Project Planning, Scheduling, Monitoring & Control

Fundamentals of Project Planning, Scheduling, Monitoring & ControlAssociation for Project Management
Feedback from the survey undertaken by the attendees
The attendees at each table were provided with a topic related to Project Planning, Scheduling, Monitoring & Control and were asked to list their top 5 ‘good practice’ lessons learned.
Topics: Planning, Change Management, Reporting, Scope, Schedule Management, Risk Management
Change Management 1. Early stakeholder engagement 2. Configuration Control 3. Analyse impacts 4. Risk Management 5. Leadership 6. Evaluation / lessons learned 7. Cost control
Project managment 10

The document discusses the key processes in project risk management: planning risk management, identifying risks, performing qualitative and quantitative risk analysis, planning risk responses, and monitoring and controlling risks. It provides details on each process, including inputs, tools and techniques, and outputs. The overall aim is to understand how to approach risk management in projects by identifying risks, analyzing them, developing responses, and continuously monitoring risks and the effectiveness of responses throughout the project lifecycle.
FedRAMP Compliance KPIs and KRIs

FedRAMP Compliance KPIs and KRIs:
Academy.skillweed.com
Monitor the performance and risks associated with Federal Risk and Authorization Management Program (FedRAMP) compliance for secure cloud services.
Presentation Guildmore Risk Mgt Mar 2014

Risk assessment is a systematic approach to identifying hazards and controlling risks. It involves establishing the context, identifying risks, analyzing and assessing their likelihood and potential impact, prioritizing them, treating risks by avoiding, reducing, transferring or retaining them, and communicating and monitoring the process on an ongoing basis. Maintaining a risk register that lists risks, analyses them, and assigns treatment options can help prevent failures and demonstrate that risks were properly managed if issues later occur.
Reliability

Risk assessment is the process of identifying risks, determining their impact and probability, and associating controls. It measures potential loss and the likelihood of loss occurring. Common types of risk assessment include qualitative, which uses terms like high, medium, low, and quantitative, which uses dollars and formulas. Performing a risk assessment involves defining its purpose, identifying the system or product, selecting an approach, gathering information, developing scenarios, estimating risks, and producing a report. Elements of good risk assessments include clear instructions, segmented questions, simplified responses, commentary areas, support contacts, focus on leaders and executors, and feedback.
Link NCA: Nutrition Causal Analysis

The document provides an overview of the Link NCA methodology, which is a structured and participatory study used to understand the causes of undernutrition in a local context. The methodology involves a 5-step process: 1) preparatory phase, 2) identifying risk factors and pathways, 3) community surveys, 4) synthesizing results and building consensus, and 5) communicating results and planning responses. The goal is to develop multi-sector interventions and programs to prevent undernutrition by understanding its main pathways and risk factors in a given area. Since 2010, over 15 Link NCA studies have been conducted globally to identify the most appropriate nutrition-sensitive responses.
Risk minimisation activities - identification and application

This presentation provides an overview of the principles for selecting and implementing risk minimisation tools
Risk minimisation activities associated with risk management plans

This presentation provides an overview of risk minimisation activities for medicines and the tools or activities that may be used in a risk management plan.
Risk Management

This was a presentation I put together based off of Rita Mulcahy's PMP Exam Prep 7th edition on Risk Management
Clinical risk management

1) Clinical risk management (CRM) aims to improve healthcare quality and safety by identifying and preventing circumstances that put patients at risk of harm.
2) Risk management involves risk identification, analysis, treatment, and control to minimize chances of errors and learn from past issues.
3) All healthcare staff have responsibilities for risk management including reporting incidents, identifying risks, and practicing risk prevention in their daily work.
Clinical Risk Management

1) Clinical risk management (CRM) aims to improve healthcare quality and safety by identifying and preventing circumstances that put patients at risk of harm.
2) Risk management involves risk identification, analysis, treatment, and control to minimize chances of errors and learn from past issues.
3) All healthcare staff have responsibilities for risk management including reporting incidents, identifying risks, and practicing risk prevention in their daily work.
Ihor Pavlenko: PMO Risk Management (UA )

Ihor Pavlenko: PMO Risk Management (UA)
Lemberg PMO School 2023
Website – https://lembs.com/pmoschool
Youtube – https://www.youtube.com/startuplviv
FB – https://www.facebook.com/pmdayconference
Similar to Risk Assessment KPIs and KRIs: (20)
Fundamentals of Project Planning, Scheduling, Monitoring & Control

Fundamentals of Project Planning, Scheduling, Monitoring & Control
Risk minimisation activities - identification and application

Risk minimisation activities - identification and application
Risk minimisation activities associated with risk management plans

Risk minimisation activities associated with risk management plans
More from Bim Akinfenwa
GDPR Compliance KPIs and KRIs

GDPR Compliance KPIs and KRIs:
Academy.skillweed.com
Evaluate the performance and risks related to complying with the General Data Protection Regulation (GDPR) to protect data privacy.
Data Privacy KPIs and KRIs

Data Privacy KPIs and KRIs:
Academy.skillweed.com
Monitor the performance and risks related to data privacy measures to ensure compliance with data protection regulations.
BCDR KPIs and KRIs

BCDR KPIs and KRIs:
Academy.skillweed.com
Monitor the performance and risks of Business Continuity and Disaster Recovery (BCDR) plans to ensure resilience in disruptions.
Operational Technology (OT) Facility KPIs and KRIs

OT Facility KPIs and KRIs:
Academy.skillweed.com
Assess the performance and risks associated with Operational Technology (OT) facilities to maintain reliability and security.
Cloud Deployment KPIs and KRIs

Cloud Deployment KPIs and KRIs:
Track the effectiveness and risks in deploying and managing cloud resources for reliability and security.
Asset Management KPIs and KRIs

The document outlines key performance indicators (KPIs) and key risk indicators (KRIs) for evaluating an organization's asset management performance across several categories. It includes 20 KPIs across areas like asset discovery, utilization, lifecycle management, tracking, maintenance, depreciation, compliance, and security. Each KPI lists 1-2 related KRIs that indicate potential risks to watch out for. The overall goal is to help organizations optimize asset utilization, security, and lifecycle management through monitoring these critical metrics.
Third-Party Vendor Risk Management KPIs and KRIs

Third-Party Vendor Risk Management KPIs and KRIs:
Monitor and assess the performance and risks associated with third-party vendors to ensure they meet security and compliance standards.
Cyber IAM KPIs and KRIs

Cyber IAM KPIs and KRIs:
Academy.skillweed.com
Gauge the performance and risks associated with Cyber Identity and Access Management (IAM) strategies to secure digital identities and access rights.
SOX Section 404 KPIs and KRIs

SOX Section 404 KPIs and KRIs:
Assess the effectiveness and risks in complying with Sarbanes-Oxley Act (SOX) Section 404 to ensure accurate financial reporting.
Data Governance KPIs and KRIs

Data governance issues are grouped into several categories: data quality, data classification, data ownership, data access control, data privacy compliance, data retention and purging, data audit and monitoring, data documentation, data governance training, and overall data governance key performance and risk indicators. Common issues include inaccurate or missing data, unclassified or misclassified data, undefined data owners, unauthorized data access, non-compliance with privacy laws and policies, data retained past retention periods, infrequent audits, incomplete documentation, and lack of training and policy awareness.
NERC-CIP Compliance KPIs and KRIs

NERC-CIP Compliance KPIs and KRIs:
Monitor the performance and risks of complying with North American Electric Reliability Corporation Critical Infrastructure Protection (NERC-CIP) standards for electric infrastructure security.
SDLC KPIs and KRIs

SDLC KPIs and KRIs:
Academy.skillweed.com
Measure the performance and risks associated with the Software Development Life Cycle (SDLC) to deliver high-quality software.
IT General Controls Key Performance Indicator & Key Risk Indicator

Explore the world of IT General Controls through this informative presentation on Key Performance Indicators (KPIs) and Key Risk Indicators (KRIs). In this comprehensive slideshow, we delve into the critical aspects of ITGCs, shedding light on how KPIs and KRIs play a pivotal role in ensuring the effectiveness and security of your organization's IT systems.
Key Topics Covered:
Understanding IT General Controls (ITGCs)
Importance of Monitoring ITGCs
Key Performance Indicators (KPIs) for ITGCs
Identifying and Defining KPIs
Key Risk Indicators (KRIs) in ITGCs
Setting Up Effective KPIs and KRIs
Real-world Examples and Case Studies
Benefits of Implementing KPIs and KRIs
Ensuring Compliance and Security
Best Practices for Managing ITGCs
Unlock the potential of IT General Controls with actionable insights into KPIs and KRIs that will help you enhance your organization's IT governance, risk management, and compliance strategies. Don't miss this opportunity to bolster your IT control framework and stay ahead in the ever-evolving landscape of technology.
Key metrics and process in cyber security case scenario

Key metrics and process in cybersecurity -Threat Assessment, Vulnerability Assessment, Endpoint security, Identify Assess Management.
In Good company: 10 People who failed but Never Quit. You can WIN also!

In Good company: 10 People who failed but Never Quit. You can also turn your challenges into victory today
5 Reasons Africa Cant be ignored

5 Reasons Africa Cant be ignored. Key: Human Resources,Quality of life,Economic growth, Business Opportunities,Competition.
Future of wearable devices 2016

This document discusses wearable technology trends for 2016 and beyond. It provides an overview of the history and types of wearables, and their applications in tracking physical activity and managing diseases. Benefits of wearables include increased productivity and life expectancy. The growing wearables market is projected to reach $41 billion by 2020. While prices need to drop and form factors expand for broader adoption, wearables from Apple and Fitbit currently dominate the market. Employers are also implementing wearable wellness programs. The future of wearables lies in continued price decreases and the rise of the "quantified self" through self-tracking technologies.
Our Aspiration for the Africa we want: Agenda 2063 

This document profiles an individual named Akin Akingbade, who is a poet, co-founder of PANLinked.com which is a professional database of African professionals, has partnered with the African Union on capacity building, mentors many start-ups, has experience in content management strategy as a manager at Ernst & Young working with over 70 Fortune 500 companies, has co-authored articles, and authored a poetry book called "Lord, I have a question" and is working on a book called "Think it Build it".
5 Quotes to get over the lonely days

5 Quotes to get over the lonely days. This five quotes will inspire you and make the impossible possible.
Project status one page

This document provides a status update for the PANLINKED project, including details on completed and upcoming milestones. The Iteration 0 deliverable was completed on schedule on September 18th and included developing EPICS, user stories, and Scrum planning. Upcoming activities are Iterations 1 and 2 starting on September 22nd and October 7th respectively. No issues or roadblocks were reported.
More from Bim Akinfenwa (20)
Operational Technology (OT) Facility KPIs and KRIs

Operational Technology (OT) Facility KPIs and KRIs
IT General Controls Key Performance Indicator & Key Risk Indicator

IT General Controls Key Performance Indicator & Key Risk Indicator
Key metrics and process in cyber security case scenario

Key metrics and process in cyber security case scenario
In Good company: 10 People who failed but Never Quit. You can WIN also!

In Good company: 10 People who failed but Never Quit. You can WIN also!
Our Aspiration for the Africa we want: Agenda 2063 

Our Aspiration for the Africa we want: Agenda 2063
Recently uploaded
Let's Integrate MuleSoft RPA, COMPOSER, APM with AWS IDP along with Slack

Discover the seamless integration of RPA (Robotic Process Automation), COMPOSER, and APM with AWS IDP enhanced with Slack notifications. Explore how these technologies converge to streamline workflows, optimize performance, and ensure secure access, all while leveraging the power of AWS IDP and real-time communication via Slack notifications.
Uni Systems Copilot event_05062024_C.Vlachos.pdf

Unlocking Productivity: Leveraging the Potential of Copilot in Microsoft 365, a presentation by Christoforos Vlachos, Senior Solutions Manager – Modern Workplace, Uni Systems
Taking AI to the Next Level in Manufacturing.pdf

Read Taking AI to the Next Level in Manufacturing to gain insights on AI adoption in the manufacturing industry, such as:
1. How quickly AI is being implemented in manufacturing.
2. Which barriers stand in the way of AI adoption.
3. How data quality and governance form the backbone of AI.
4. Organizational processes and structures that may inhibit effective AI adoption.
6. Ideas and approaches to help build your organization's AI strategy.
Unlock the Future of Search with MongoDB Atlas_ Vector Search Unleashed.pdf

Discover how MongoDB Atlas and vector search technology can revolutionize your application's search capabilities. This comprehensive presentation covers:
* What is Vector Search?
* Importance and benefits of vector search
* Practical use cases across various industries
* Step-by-step implementation guide
* Live demos with code snippets
* Enhancing LLM capabilities with vector search
* Best practices and optimization strategies
Perfect for developers, AI enthusiasts, and tech leaders. Learn how to leverage MongoDB Atlas to deliver highly relevant, context-aware search results, transforming your data retrieval process. Stay ahead in tech innovation and maximize the potential of your applications.
#MongoDB #VectorSearch #AI #SemanticSearch #TechInnovation #DataScience #LLM #MachineLearning #SearchTechnology
HCL Notes und Domino Lizenzkostenreduzierung in der Welt von DLAU

Webinar Recording: https://www.panagenda.com/webinars/hcl-notes-und-domino-lizenzkostenreduzierung-in-der-welt-von-dlau/
DLAU und die Lizenzen nach dem CCB- und CCX-Modell sind für viele in der HCL-Community seit letztem Jahr ein heißes Thema. Als Notes- oder Domino-Kunde haben Sie vielleicht mit unerwartet hohen Benutzerzahlen und Lizenzgebühren zu kämpfen. Sie fragen sich vielleicht, wie diese neue Art der Lizenzierung funktioniert und welchen Nutzen sie Ihnen bringt. Vor allem wollen Sie sicherlich Ihr Budget einhalten und Kosten sparen, wo immer möglich. Das verstehen wir und wir möchten Ihnen dabei helfen!
Wir erklären Ihnen, wie Sie häufige Konfigurationsprobleme lösen können, die dazu führen können, dass mehr Benutzer gezählt werden als nötig, und wie Sie überflüssige oder ungenutzte Konten identifizieren und entfernen können, um Geld zu sparen. Es gibt auch einige Ansätze, die zu unnötigen Ausgaben führen können, z. B. wenn ein Personendokument anstelle eines Mail-Ins für geteilte Mailboxen verwendet wird. Wir zeigen Ihnen solche Fälle und deren Lösungen. Und natürlich erklären wir Ihnen das neue Lizenzmodell.
Nehmen Sie an diesem Webinar teil, bei dem HCL-Ambassador Marc Thomas und Gastredner Franz Walder Ihnen diese neue Welt näherbringen. Es vermittelt Ihnen die Tools und das Know-how, um den Überblick zu bewahren. Sie werden in der Lage sein, Ihre Kosten durch eine optimierte Domino-Konfiguration zu reduzieren und auch in Zukunft gering zu halten.
Diese Themen werden behandelt
- Reduzierung der Lizenzkosten durch Auffinden und Beheben von Fehlkonfigurationen und überflüssigen Konten
- Wie funktionieren CCB- und CCX-Lizenzen wirklich?
- Verstehen des DLAU-Tools und wie man es am besten nutzt
- Tipps für häufige Problembereiche, wie z. B. Team-Postfächer, Funktions-/Testbenutzer usw.
- Praxisbeispiele und Best Practices zum sofortigen Umsetzen
Ocean lotus Threat actors project by John Sitima 2024 (1).pptx

Ocean Lotus cyber threat actors represent a sophisticated, persistent, and politically motivated group that poses a significant risk to organizations and individuals in the Southeast Asian region. Their continuous evolution and adaptability underscore the need for robust cybersecurity measures and international cooperation to identify and mitigate the threats posed by such advanced persistent threat groups.
Fueling AI with Great Data with Airbyte Webinar

This talk will focus on how to collect data from a variety of sources, leveraging this data for RAG and other GenAI use cases, and finally charting your course to productionalization.
Microsoft - Power Platform_G.Aspiotis.pdf

Revolutionizing Application Development
with AI-powered low-code, presentation by George Aspiotis, Sr. Partner Development Manager, Microsoft
National Security Agency - NSA mobile device best practices

Threats to mobile devices are more prevalent and increasing in scope and complexity. Users of mobile devices desire to take full advantage of the features
available on those devices, but many of the features provide convenience and capability but sacrifice security. This best practices guide outlines steps the users can take to better protect personal devices and information.
CAKE: Sharing Slices of Confidential Data on Blockchain

Presented at the CAiSE 2024 Forum, Intelligent Information Systems, June 6th, Limassol, Cyprus.
Synopsis: Cooperative information systems typically involve various entities in a collaborative process within a distributed environment. Blockchain technology offers a mechanism for automating such processes, even when only partial trust exists among participants. The data stored on the blockchain is replicated across all nodes in the network, ensuring accessibility to all participants. While this aspect facilitates traceability, integrity, and persistence, it poses challenges for adopting public blockchains in enterprise settings due to confidentiality issues. In this paper, we present a software tool named Control Access via Key Encryption (CAKE), designed to ensure data confidentiality in scenarios involving public blockchains. After outlining its core components and functionalities, we showcase the application of CAKE in the context of a real-world cyber-security project within the logistics domain.
Paper: https://doi.org/10.1007/978-3-031-61000-4_16
20240605 QFM017 Machine Intelligence Reading List May 2024

Everything I found interesting about machines behaving intelligently during May 2024
Columbus Data & Analytics Wednesdays - June 2024

Columbus Data & Analytics Wednesdays, June 2024 with Maria Copot 20
TrustArc Webinar - 2024 Global Privacy Survey

How does your privacy program stack up against your peers? What challenges are privacy teams tackling and prioritizing in 2024?
In the fifth annual Global Privacy Benchmarks Survey, we asked over 1,800 global privacy professionals and business executives to share their perspectives on the current state of privacy inside and outside of their organizations. This year’s report focused on emerging areas of importance for privacy and compliance professionals, including considerations and implications of Artificial Intelligence (AI) technologies, building brand trust, and different approaches for achieving higher privacy competence scores.
See how organizational priorities and strategic approaches to data security and privacy are evolving around the globe.
This webinar will review:
- The top 10 privacy insights from the fifth annual Global Privacy Benchmarks Survey
- The top challenges for privacy leaders, practitioners, and organizations in 2024
- Key themes to consider in developing and maintaining your privacy program
Removing Uninteresting Bytes in Software Fuzzing

Imagine a world where software fuzzing, the process of mutating bytes in test seeds to uncover hidden and erroneous program behaviors, becomes faster and more effective. A lot depends on the initial seeds, which can significantly dictate the trajectory of a fuzzing campaign, particularly in terms of how long it takes to uncover interesting behaviour in your code. We introduce DIAR, a technique designed to speedup fuzzing campaigns by pinpointing and eliminating those uninteresting bytes in the seeds. Picture this: instead of wasting valuable resources on meaningless mutations in large, bloated seeds, DIAR removes the unnecessary bytes, streamlining the entire process.
In this work, we equipped AFL, a popular fuzzer, with DIAR and examined two critical Linux libraries -- Libxml's xmllint, a tool for parsing xml documents, and Binutil's readelf, an essential debugging and security analysis command-line tool used to display detailed information about ELF (Executable and Linkable Format). Our preliminary results show that AFL+DIAR does not only discover new paths more quickly but also achieves higher coverage overall. This work thus showcases how starting with lean and optimized seeds can lead to faster, more comprehensive fuzzing campaigns -- and DIAR helps you find such seeds.
- These are slides of the talk given at IEEE International Conference on Software Testing Verification and Validation Workshop, ICSTW 2022.
Cosa hanno in comune un mattoncino Lego e la backdoor XZ?

ABSTRACT: A prima vista, un mattoncino Lego e la backdoor XZ potrebbero avere in comune il fatto di essere entrambi blocchi di costruzione, o dipendenze di progetti creativi e software. La realtà è che un mattoncino Lego e il caso della backdoor XZ hanno molto di più di tutto ciò in comune.
Partecipate alla presentazione per immergervi in una storia di interoperabilità, standard e formati aperti, per poi discutere del ruolo importante che i contributori hanno in una comunità open source sostenibile.
BIO: Sostenitrice del software libero e dei formati standard e aperti. È stata un membro attivo dei progetti Fedora e openSUSE e ha co-fondato l'Associazione LibreItalia dove è stata coinvolta in diversi eventi, migrazioni e formazione relativi a LibreOffice. In precedenza ha lavorato a migrazioni e corsi di formazione su LibreOffice per diverse amministrazioni pubbliche e privati. Da gennaio 2020 lavora in SUSE come Software Release Engineer per Uyuni e SUSE Manager e quando non segue la sua passione per i computer e per Geeko coltiva la sua curiosità per l'astronomia (da cui deriva il suo nickname deneb_alpha).
“Building and Scaling AI Applications with the Nx AI Manager,” a Presentation...

“Building and Scaling AI Applications with the Nx AI Manager,” a Presentation...Edge AI and Vision Alliance
For the full video of this presentation, please visit: https://www.edge-ai-vision.com/2024/06/building-and-scaling-ai-applications-with-the-nx-ai-manager-a-presentation-from-network-optix/
Robin van Emden, Senior Director of Data Science at Network Optix, presents the “Building and Scaling AI Applications with the Nx AI Manager,” tutorial at the May 2024 Embedded Vision Summit.
In this presentation, van Emden covers the basics of scaling edge AI solutions using the Nx tool kit. He emphasizes the process of developing AI models and deploying them globally. He also showcases the conversion of AI models and the creation of effective edge AI pipelines, with a focus on pre-processing, model conversion, selecting the appropriate inference engine for the target hardware and post-processing.
van Emden shows how Nx can simplify the developer’s life and facilitate a rapid transition from concept to production-ready applications.He provides valuable insights into developing scalable and efficient edge AI solutions, with a strong focus on practical implementation.Programming Foundation Models with DSPy - Meetup Slides

Prompting language models is hard, while programming language models is easy. In this talk, I will discuss the state-of-the-art framework DSPy for programming foundation models with its powerful optimizers and runtime constraint system.
Mind map of terminologies used in context of Generative AI

Mind map of common terms used in context of Generative AI.
Full-RAG: A modern architecture for hyper-personalization

Mike Del Balso, CEO & Co-Founder at Tecton, presents "Full RAG," a novel approach to AI recommendation systems, aiming to push beyond the limitations of traditional models through a deep integration of contextual insights and real-time data, leveraging the Retrieval-Augmented Generation architecture. This talk will outline Full RAG's potential to significantly enhance personalization, address engineering challenges such as data management and model training, and introduce data enrichment with reranking as a key solution. Attendees will gain crucial insights into the importance of hyperpersonalization in AI, the capabilities of Full RAG for advanced personalization, and strategies for managing complex data integrations for deploying cutting-edge AI solutions.
Recently uploaded (20)
Let's Integrate MuleSoft RPA, COMPOSER, APM with AWS IDP along with Slack

Let's Integrate MuleSoft RPA, COMPOSER, APM with AWS IDP along with Slack
Unlock the Future of Search with MongoDB Atlas_ Vector Search Unleashed.pdf

Unlock the Future of Search with MongoDB Atlas_ Vector Search Unleashed.pdf
HCL Notes und Domino Lizenzkostenreduzierung in der Welt von DLAU

HCL Notes und Domino Lizenzkostenreduzierung in der Welt von DLAU
Ocean lotus Threat actors project by John Sitima 2024 (1).pptx

Ocean lotus Threat actors project by John Sitima 2024 (1).pptx
National Security Agency - NSA mobile device best practices

National Security Agency - NSA mobile device best practices
CAKE: Sharing Slices of Confidential Data on Blockchain

CAKE: Sharing Slices of Confidential Data on Blockchain
20240605 QFM017 Machine Intelligence Reading List May 2024

20240605 QFM017 Machine Intelligence Reading List May 2024
Cosa hanno in comune un mattoncino Lego e la backdoor XZ?

Cosa hanno in comune un mattoncino Lego e la backdoor XZ?
“Building and Scaling AI Applications with the Nx AI Manager,” a Presentation...

“Building and Scaling AI Applications with the Nx AI Manager,” a Presentation...
Programming Foundation Models with DSPy - Meetup Slides

Programming Foundation Models with DSPy - Meetup Slides
Mind map of terminologies used in context of Generative AI

Mind map of terminologies used in context of Generative AI
Full-RAG: A modern architecture for hyper-personalization

Full-RAG: A modern architecture for hyper-personalization
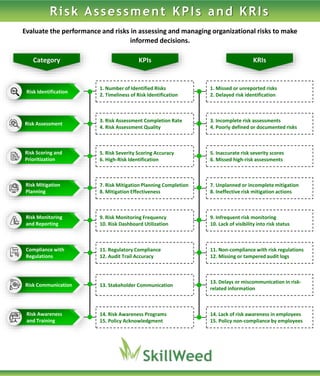
Risk Assessment KPIs and KRIs:
- 1. Risk Identification 1. Number of Identified Risks 2. Timeliness of Risk Identification 1. Missed or unreported risks 2. Delayed risk identification Risk Assessment 3. Risk Assessment Completion Rate 4. Risk Assessment Quality 3. Incomplete risk assessments 4. Poorly defined or documented risks Risk Scoring and Prioritization 5. Risk Severity Scoring Accuracy 6. High-Risk Identification 5. Inaccurate risk severity scores 6. Missed high-risk assessments Risk Mitigation Planning 7. Risk Mitigation Planning Completion 8. Mitigation Effectiveness 7. Unplanned or incomplete mitigation 8. Ineffective risk mitigation actions Risk Monitoring and Reporting 9. Risk Monitoring Frequency 10. Risk Dashboard Utilization 9. Infrequent risk monitoring 10. Lack of visibility into risk status Compliance with Regulations 11. Regulatory Compliance 12. Audit Trail Accuracy 11. Non-compliance with risk regulations 12. Missing or tampered audit logs Risk Communication 13. Stakeholder Communication 13. Delays or miscommunication in risk- related information Risk Awareness and Training 14. Risk Awareness Programs 15. Policy Acknowledgment 14. Lack of risk awareness in employees 15. Policy non-compliance by employees Category KPIs KRIs Risk Assessment KPIs and KRIs Evaluate the performance and risks in assessing and managing organizational risks to make informed decisions.