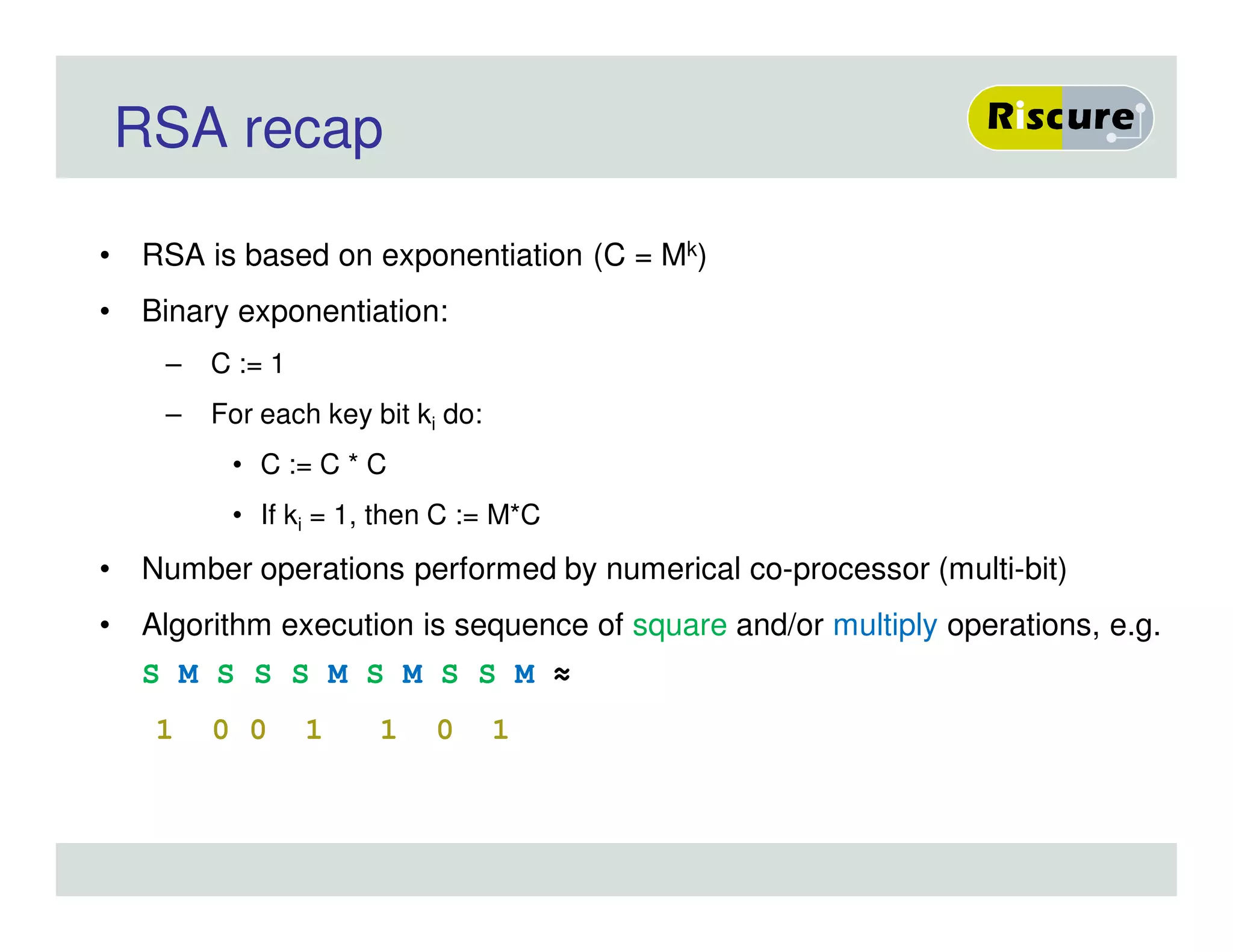
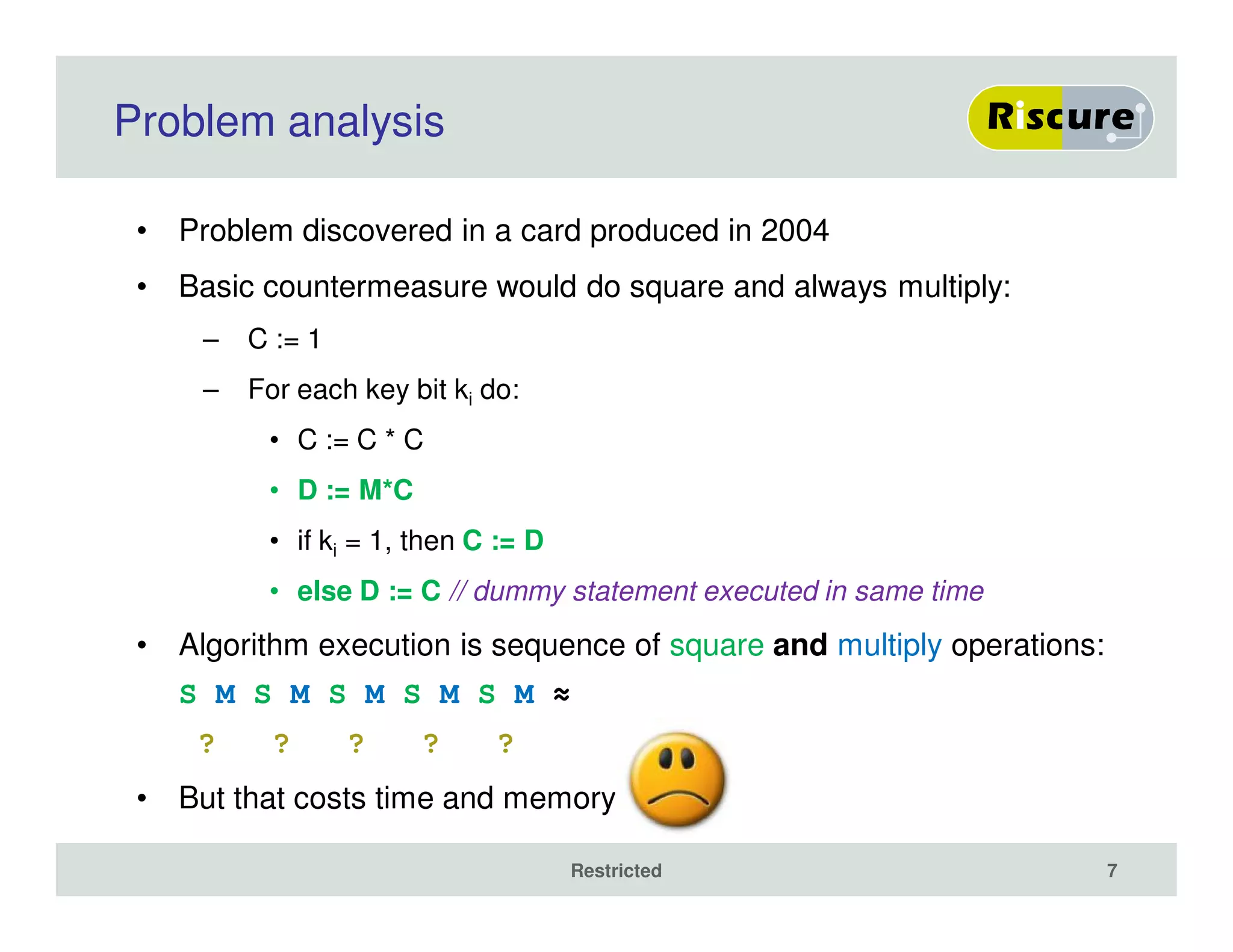
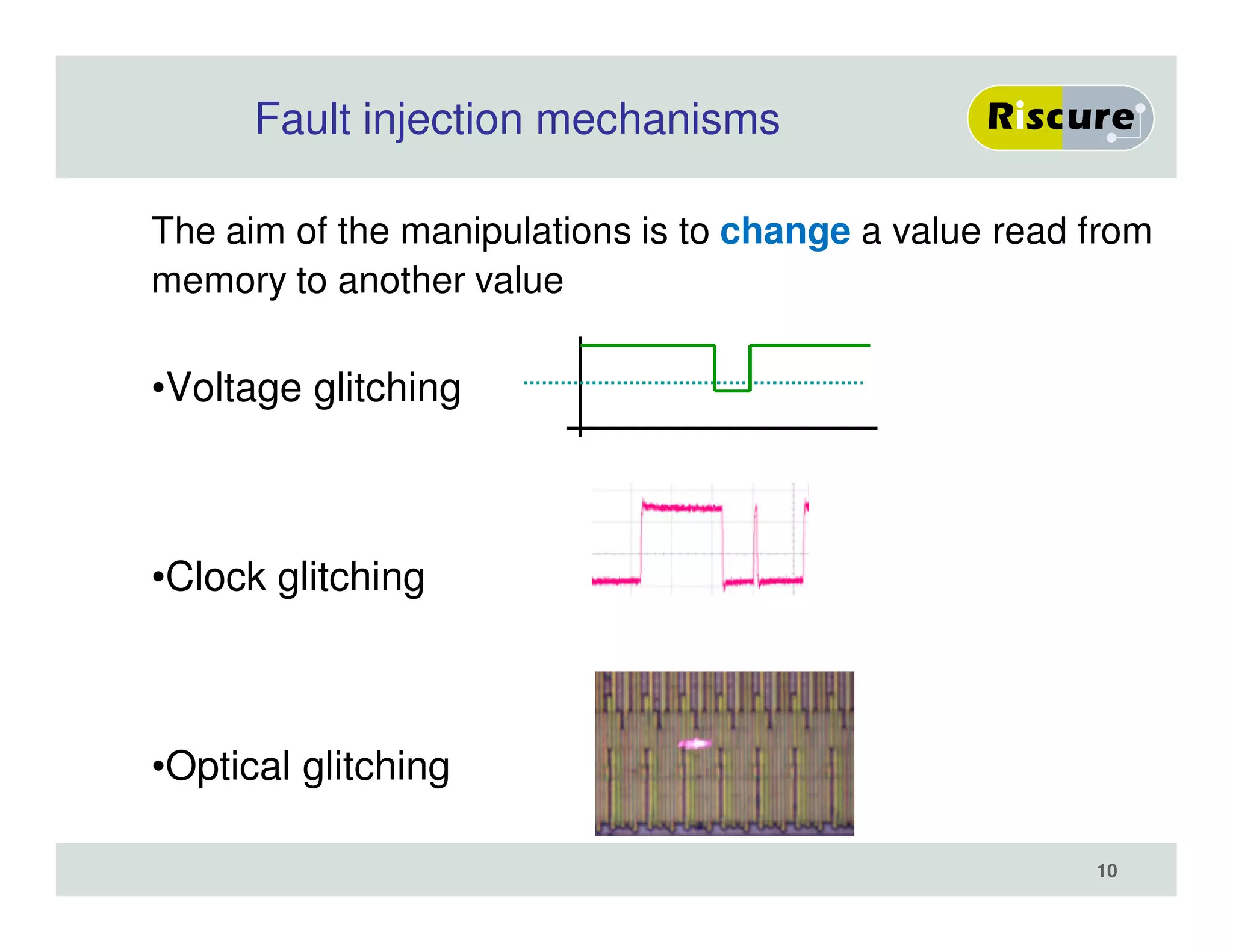
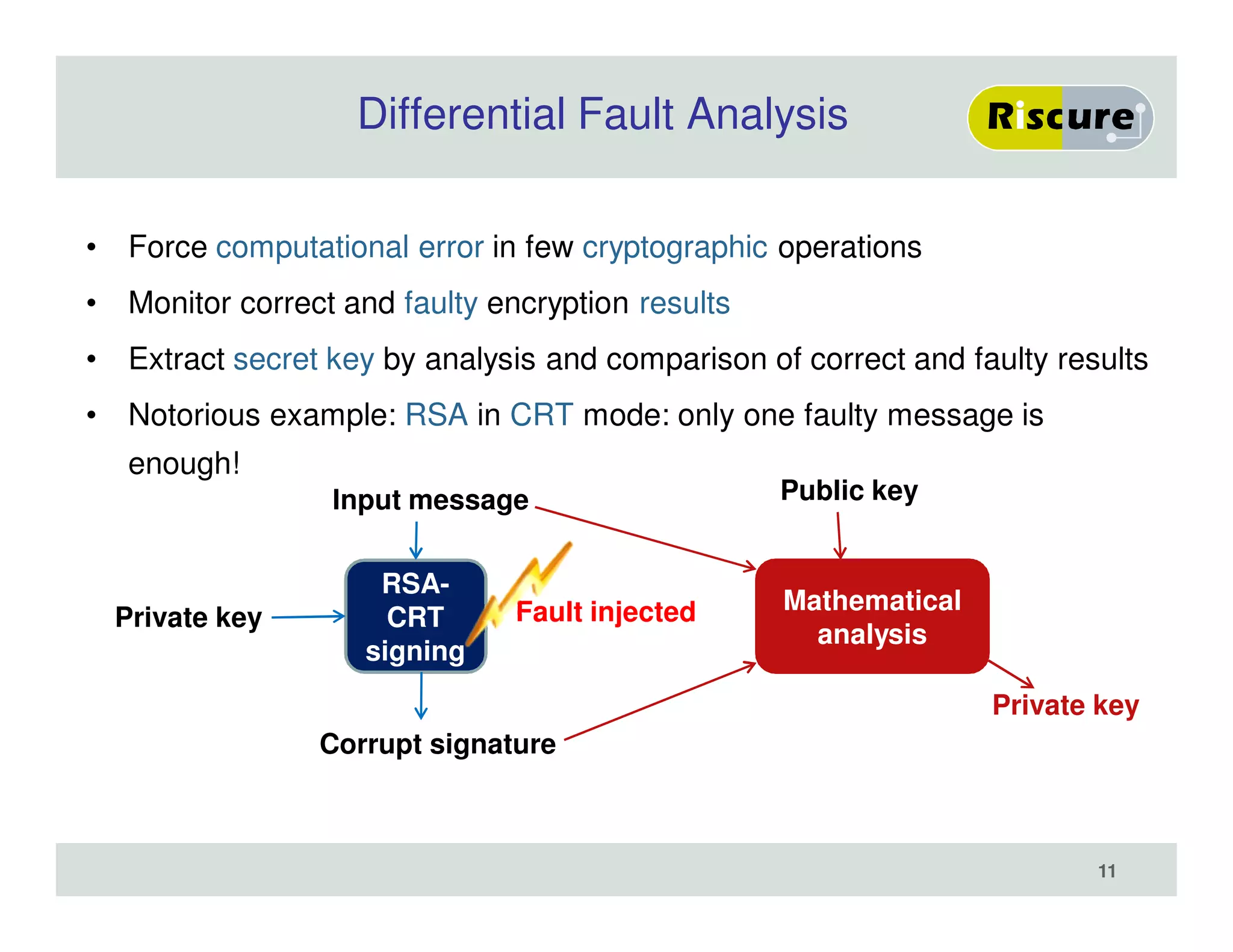
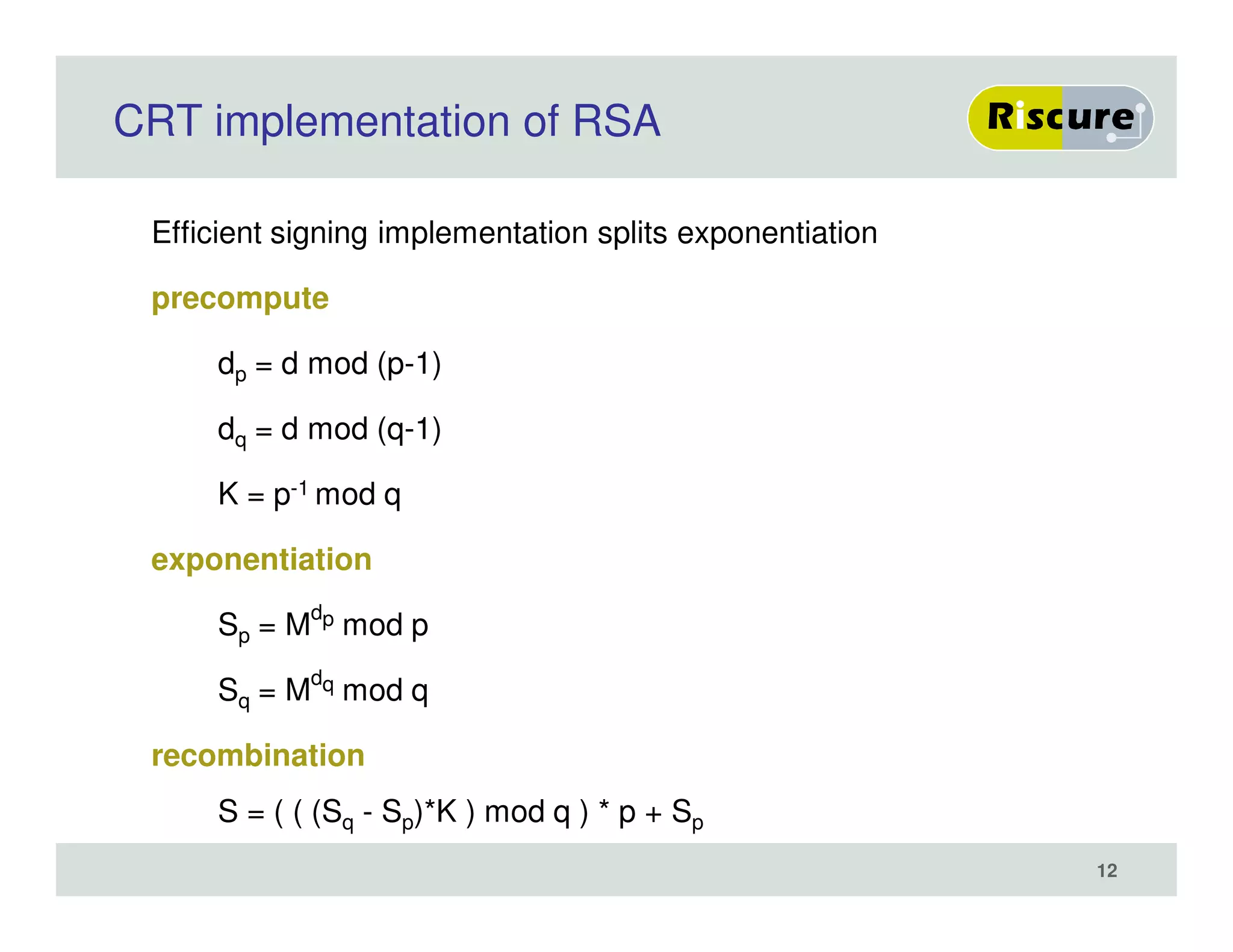
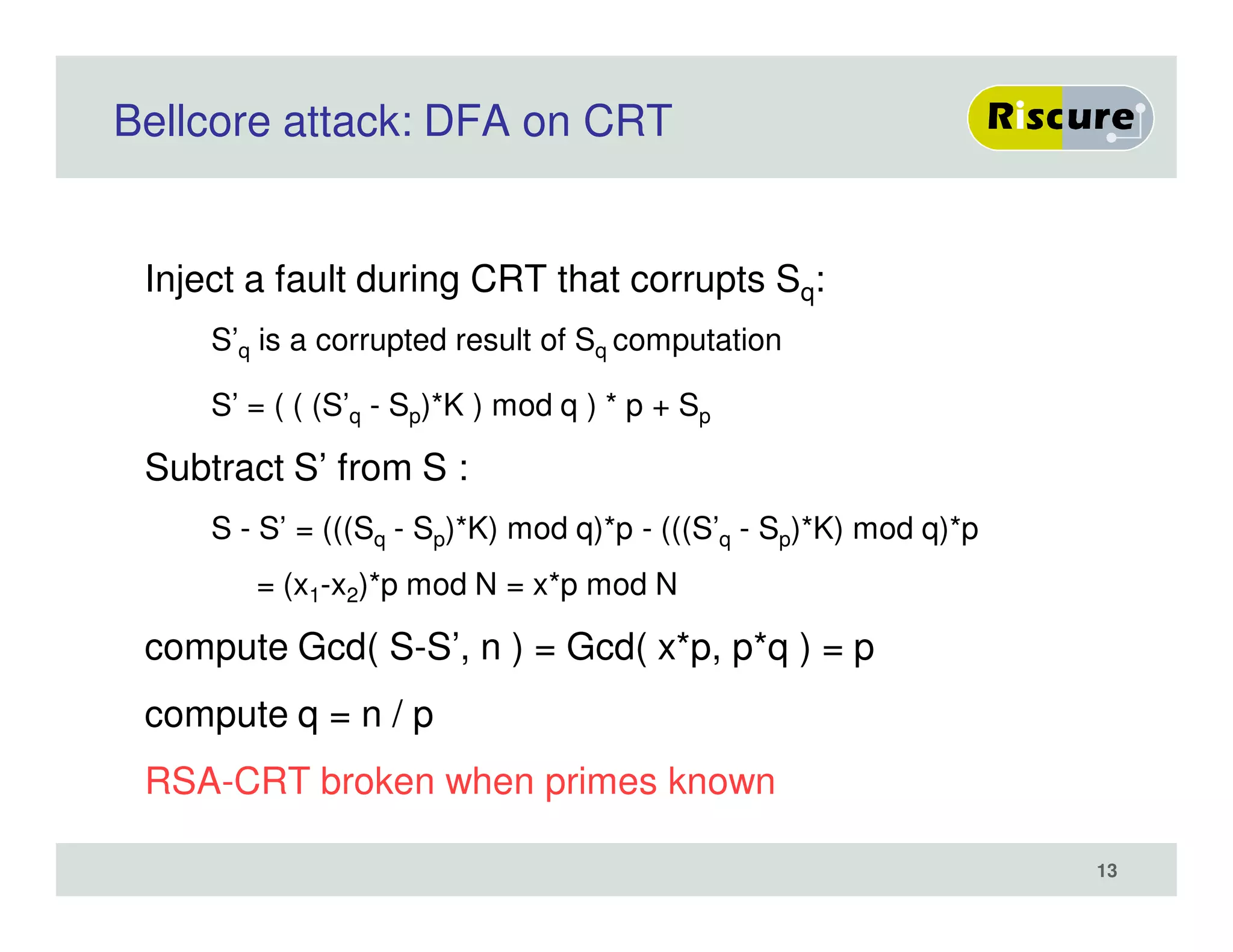
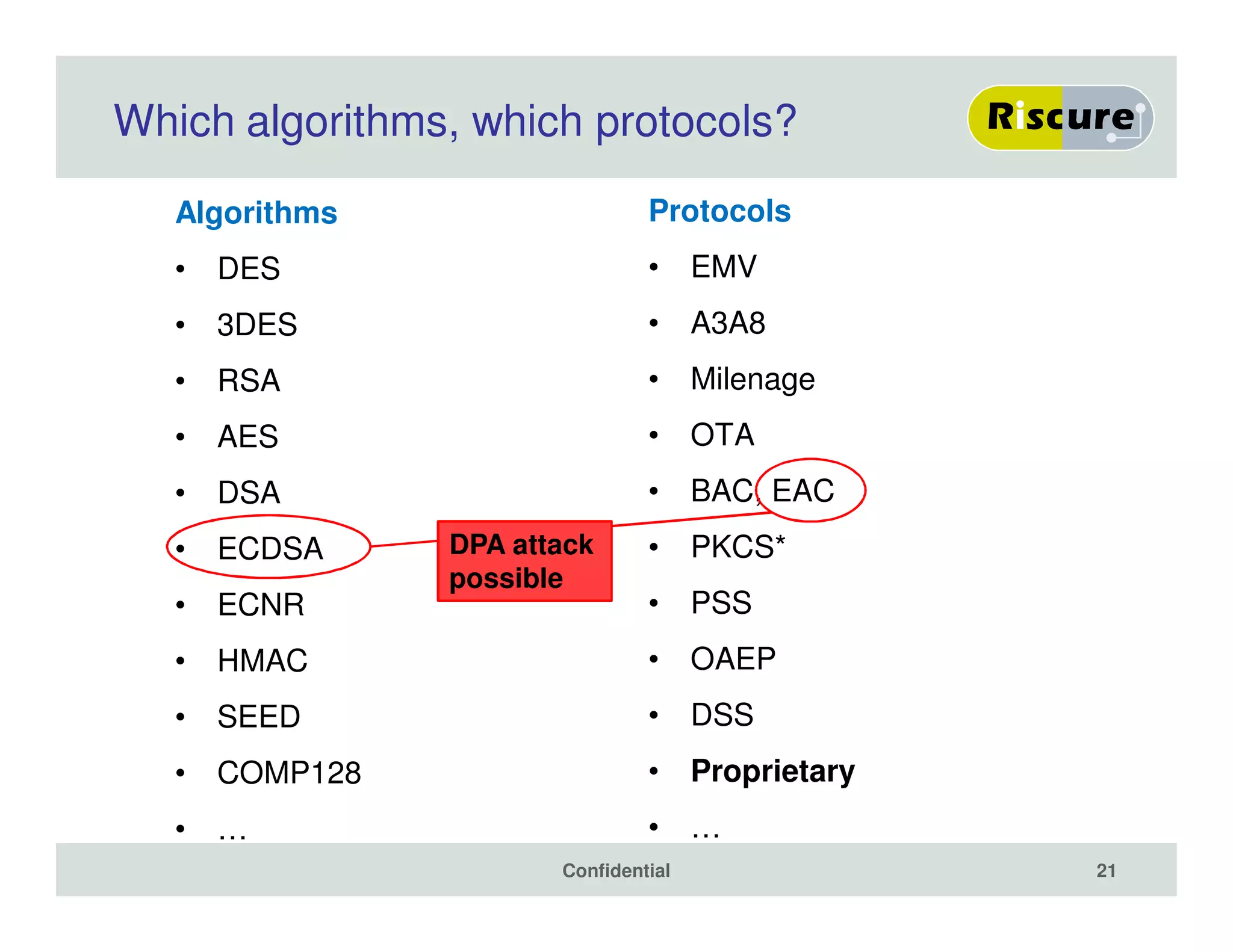
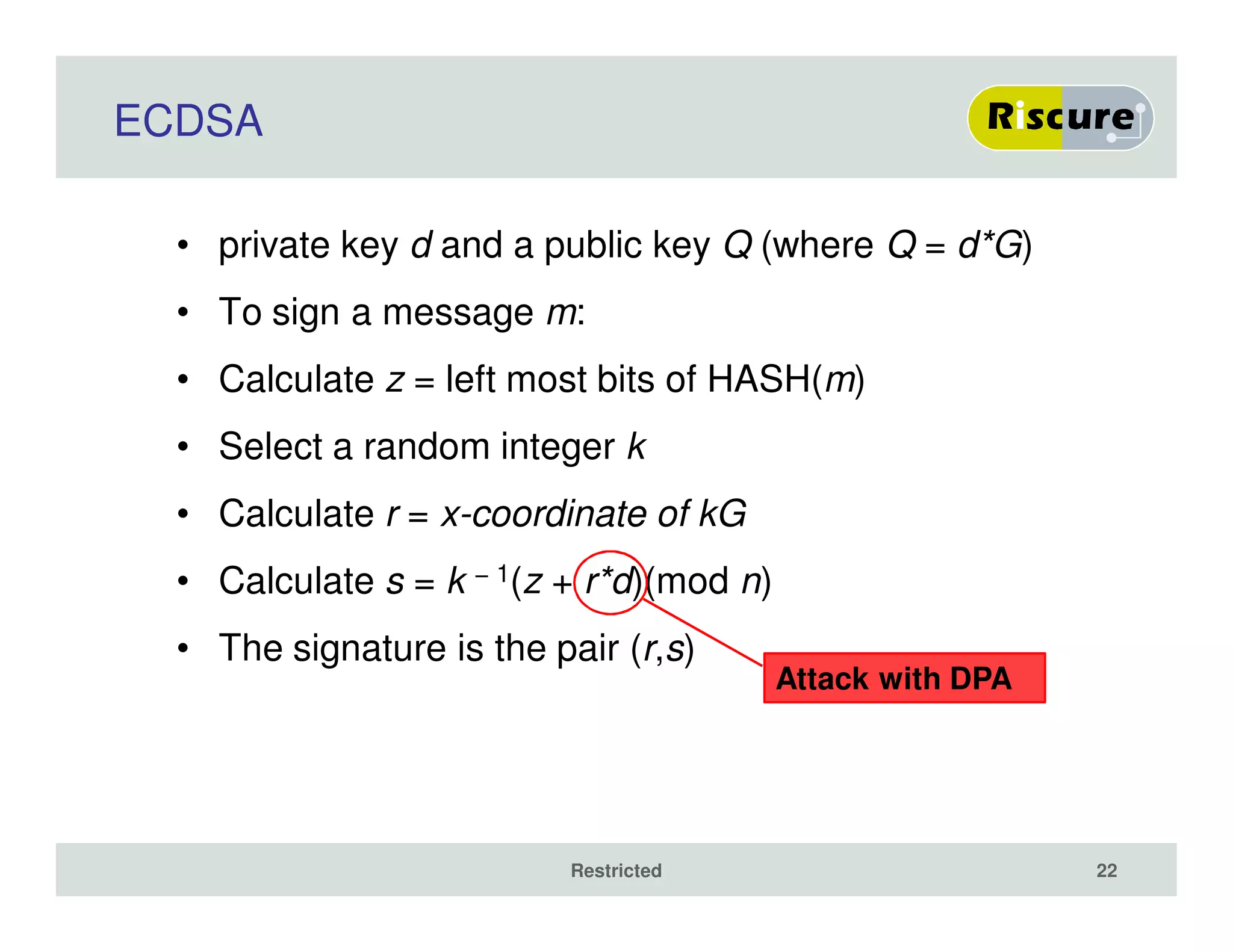
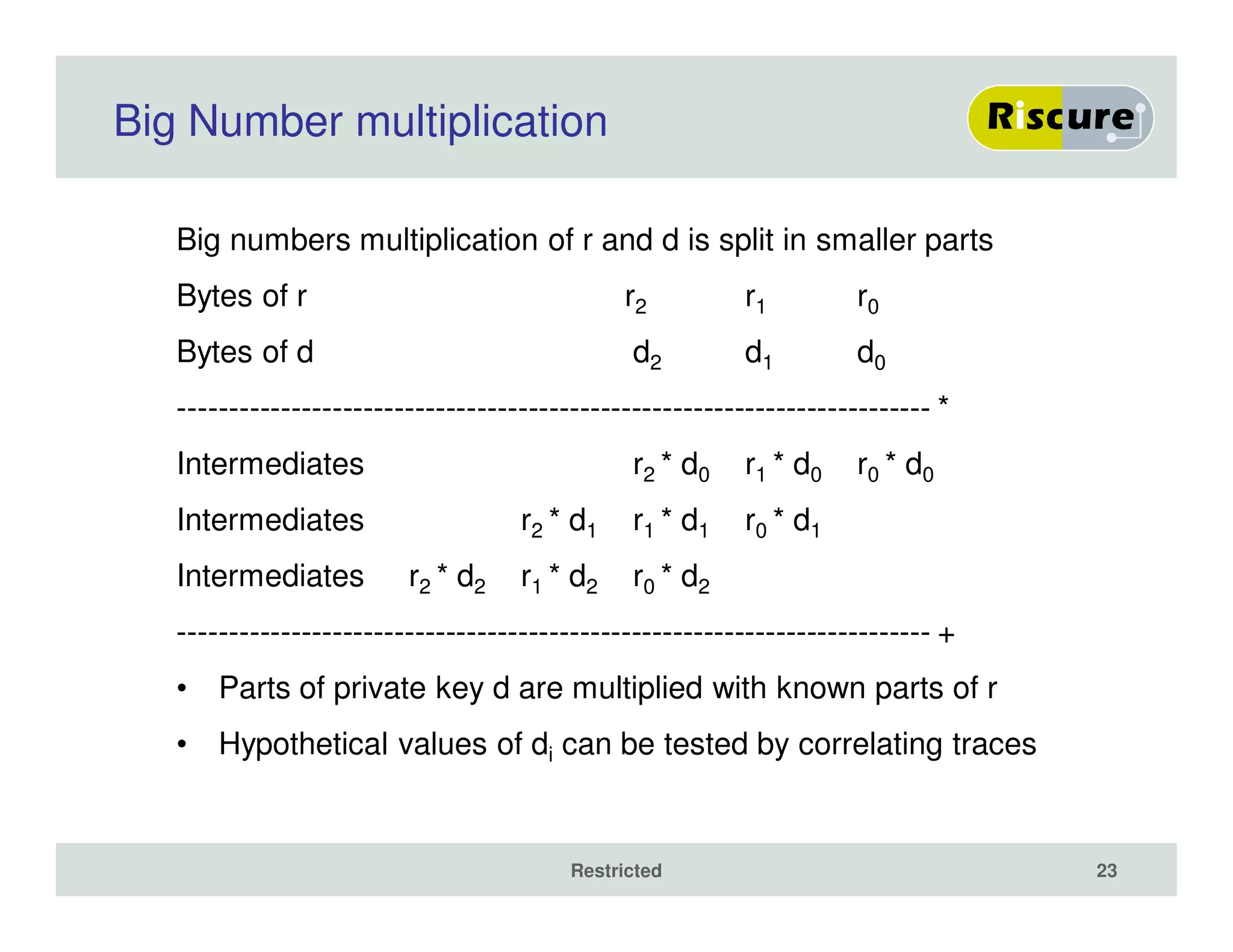
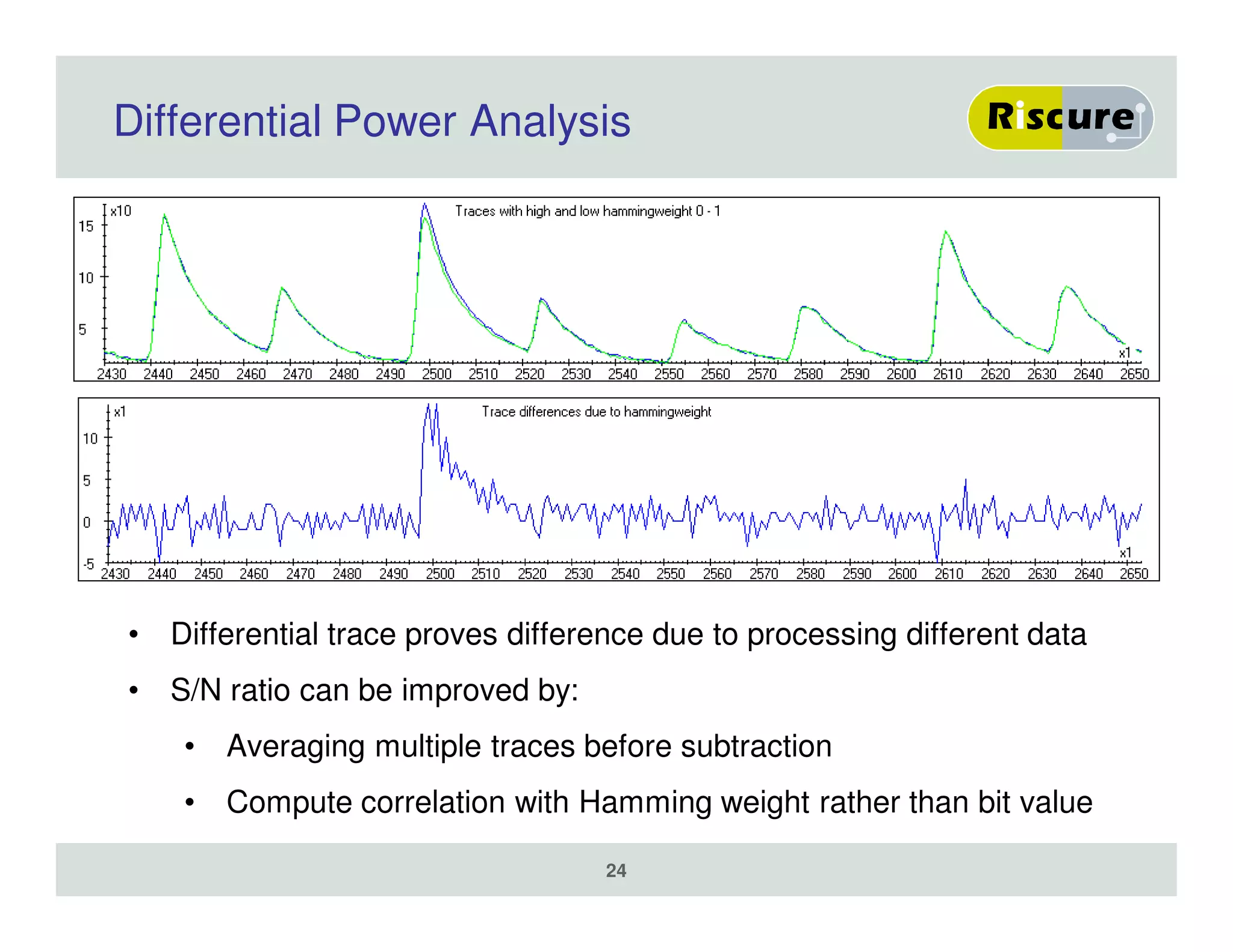
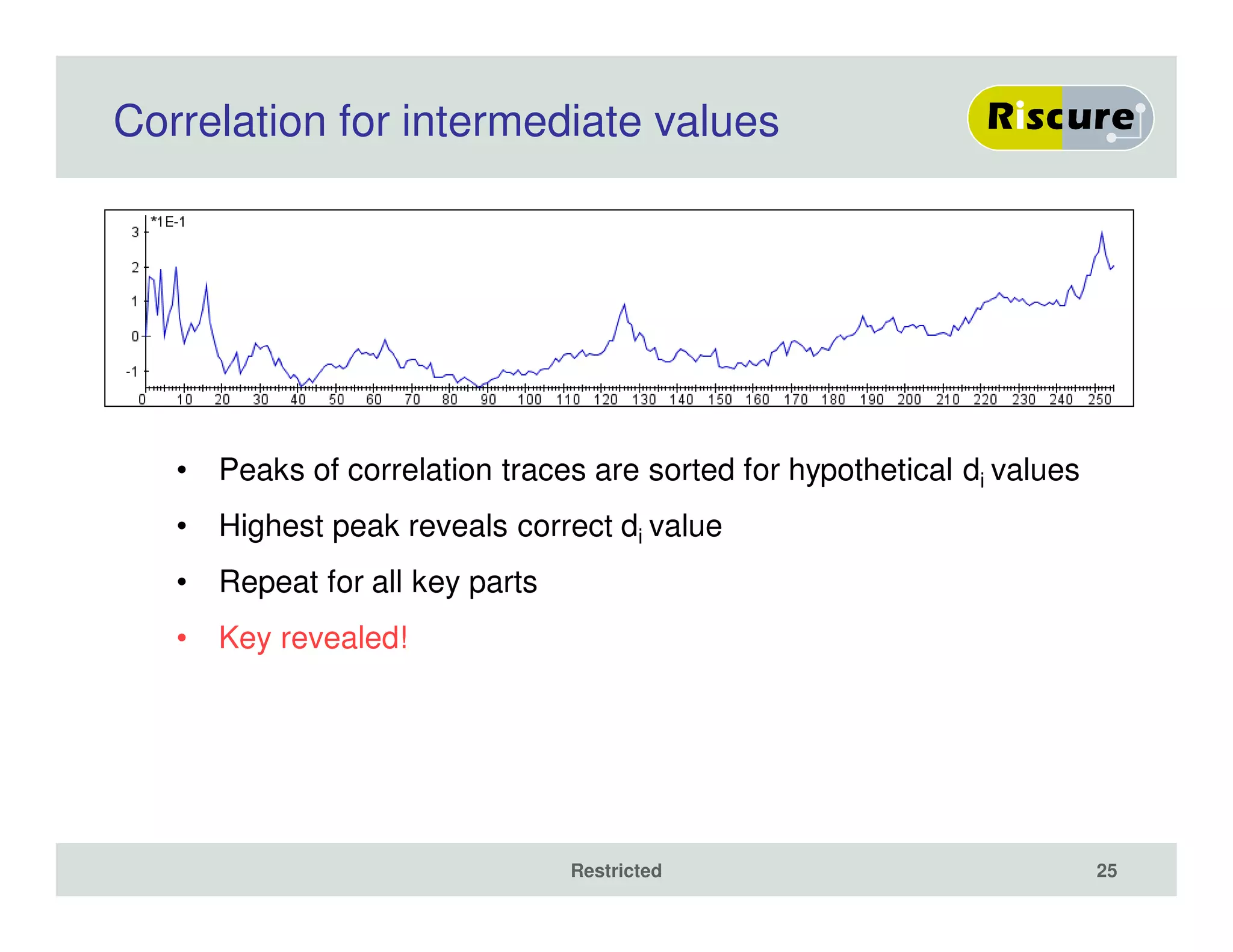
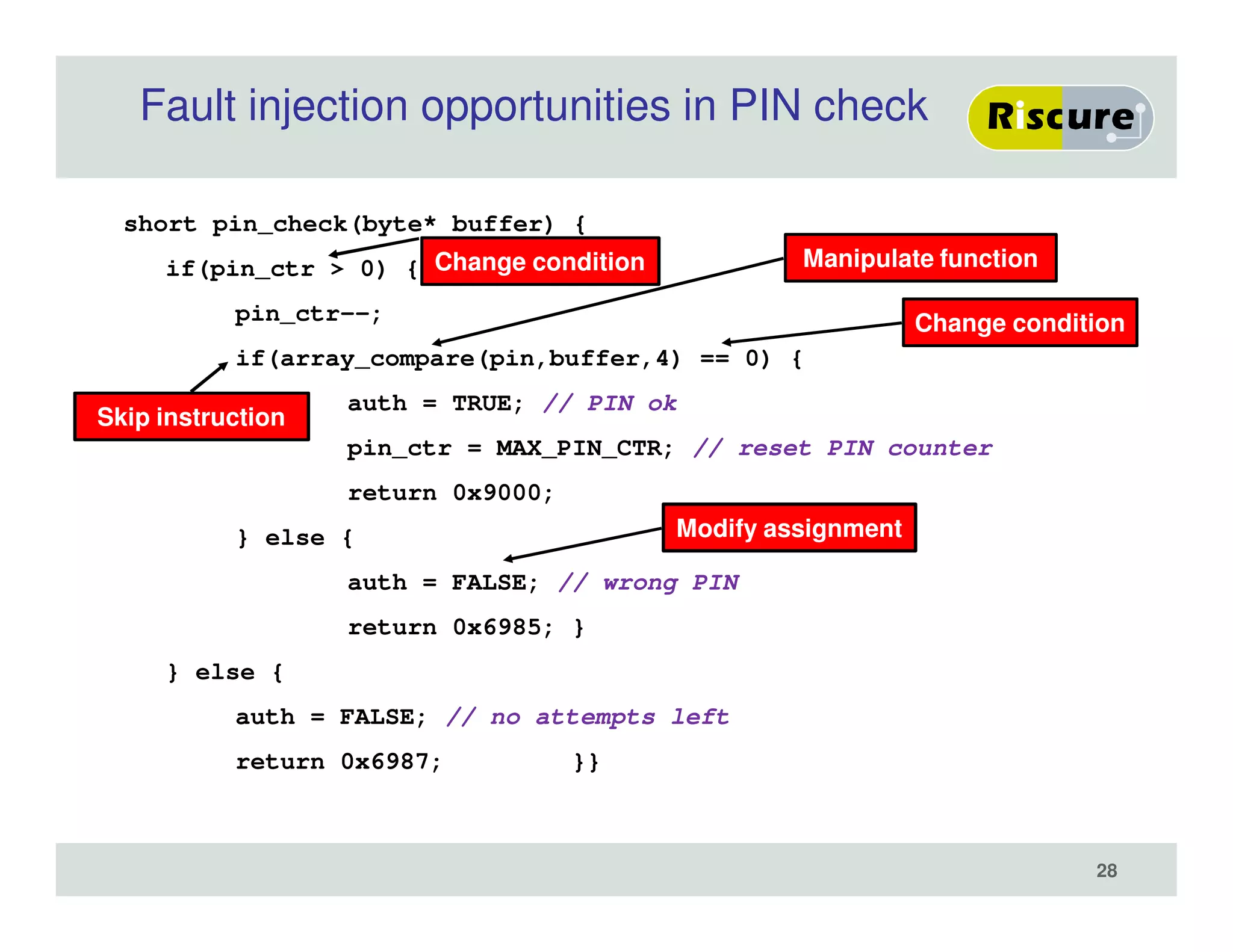
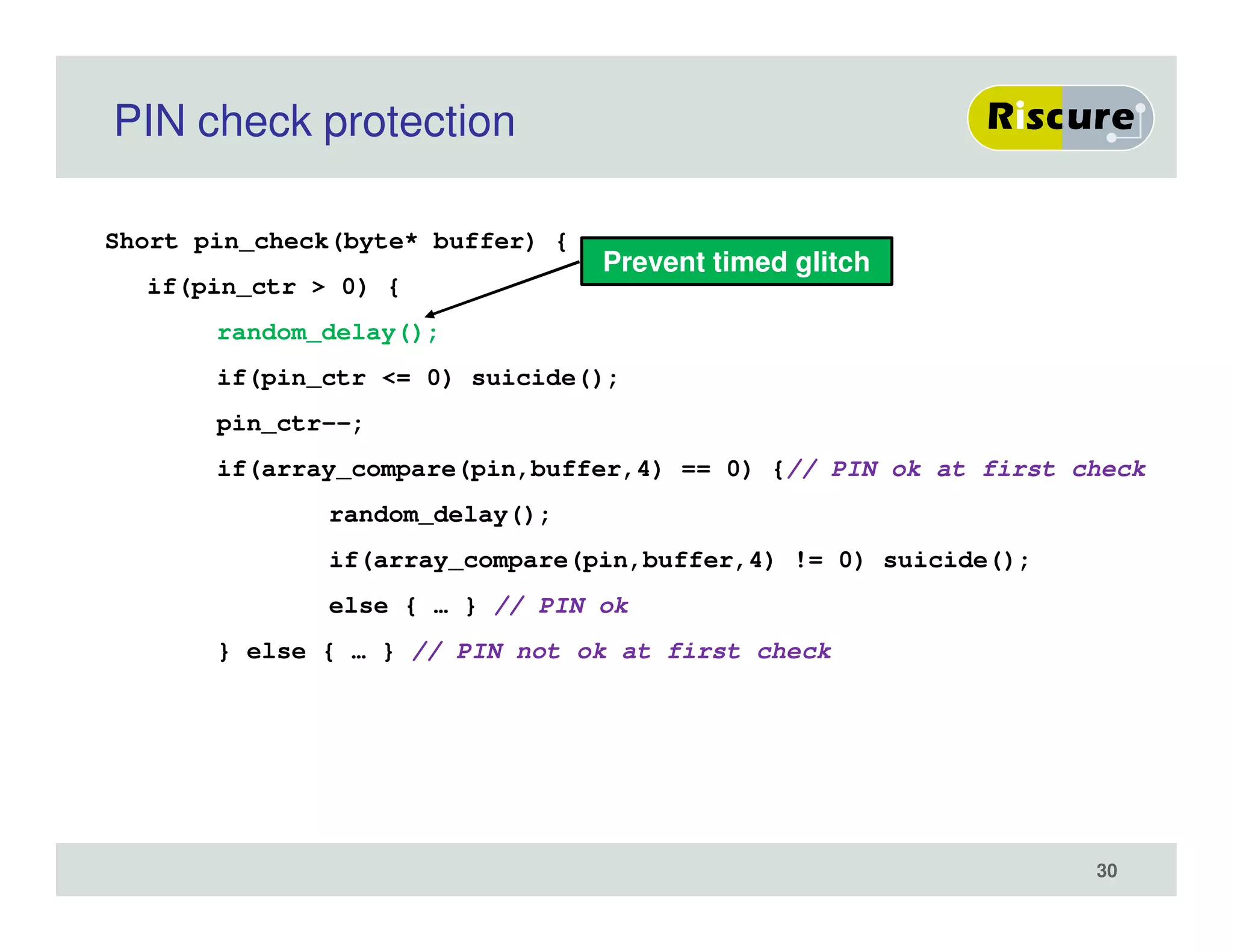
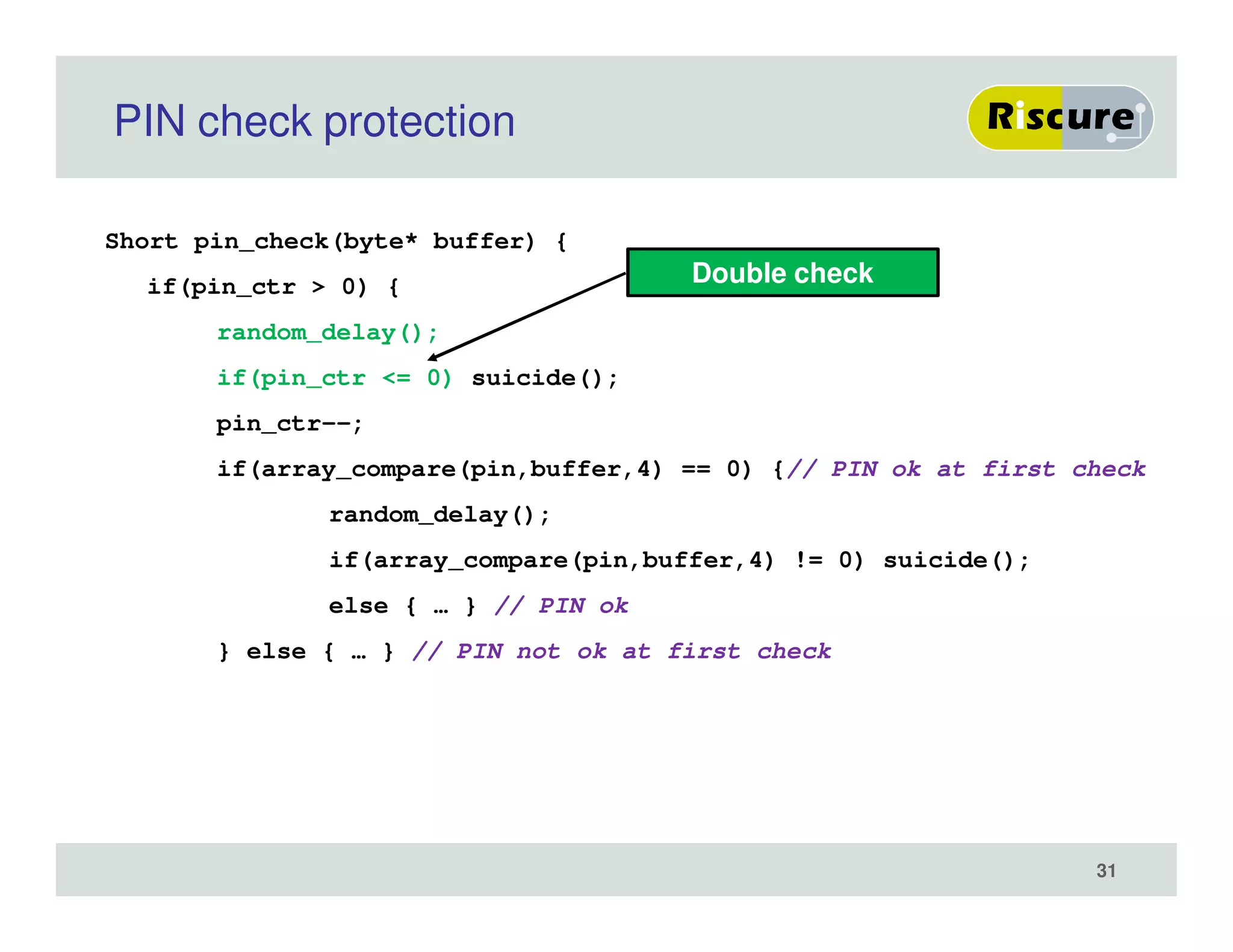
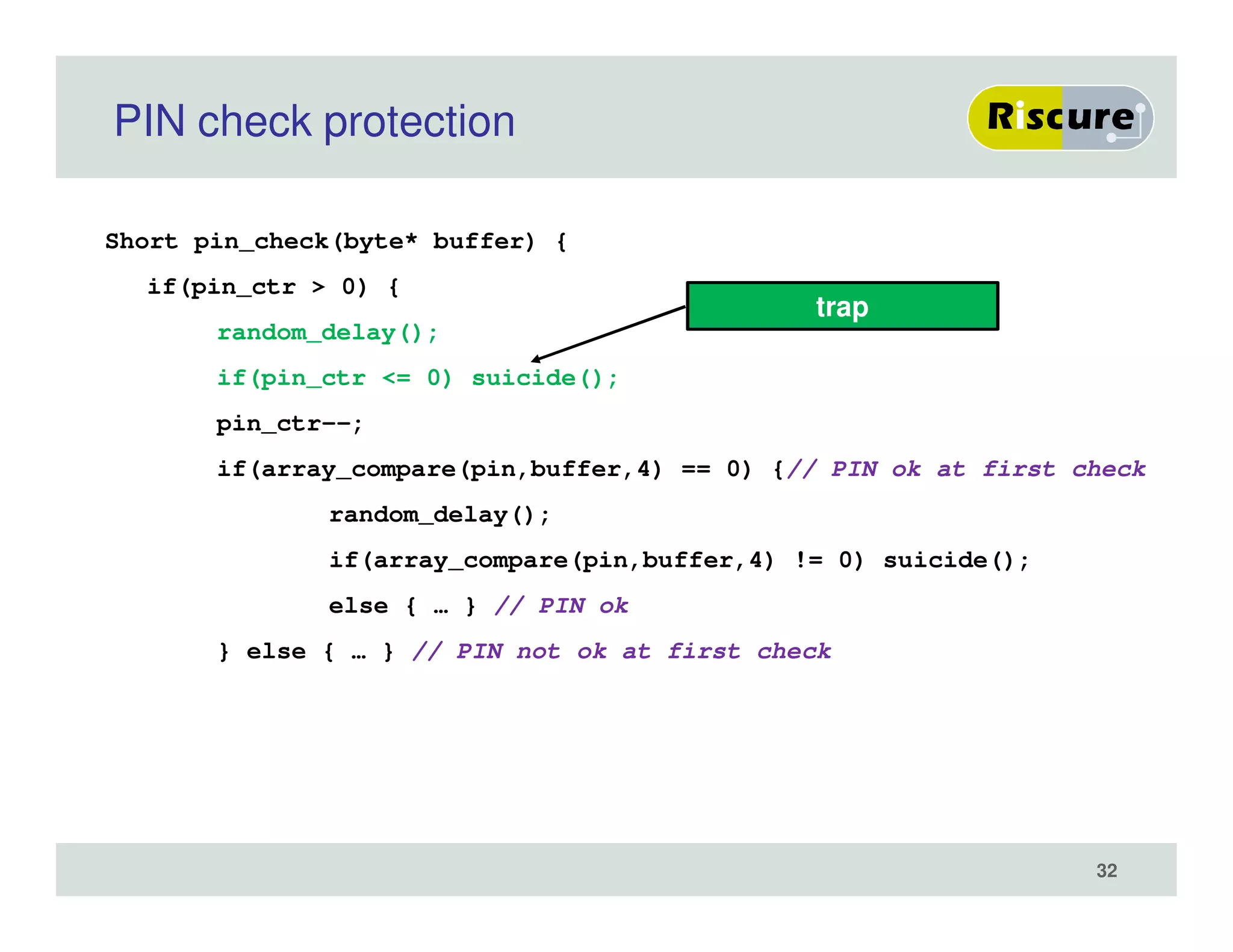
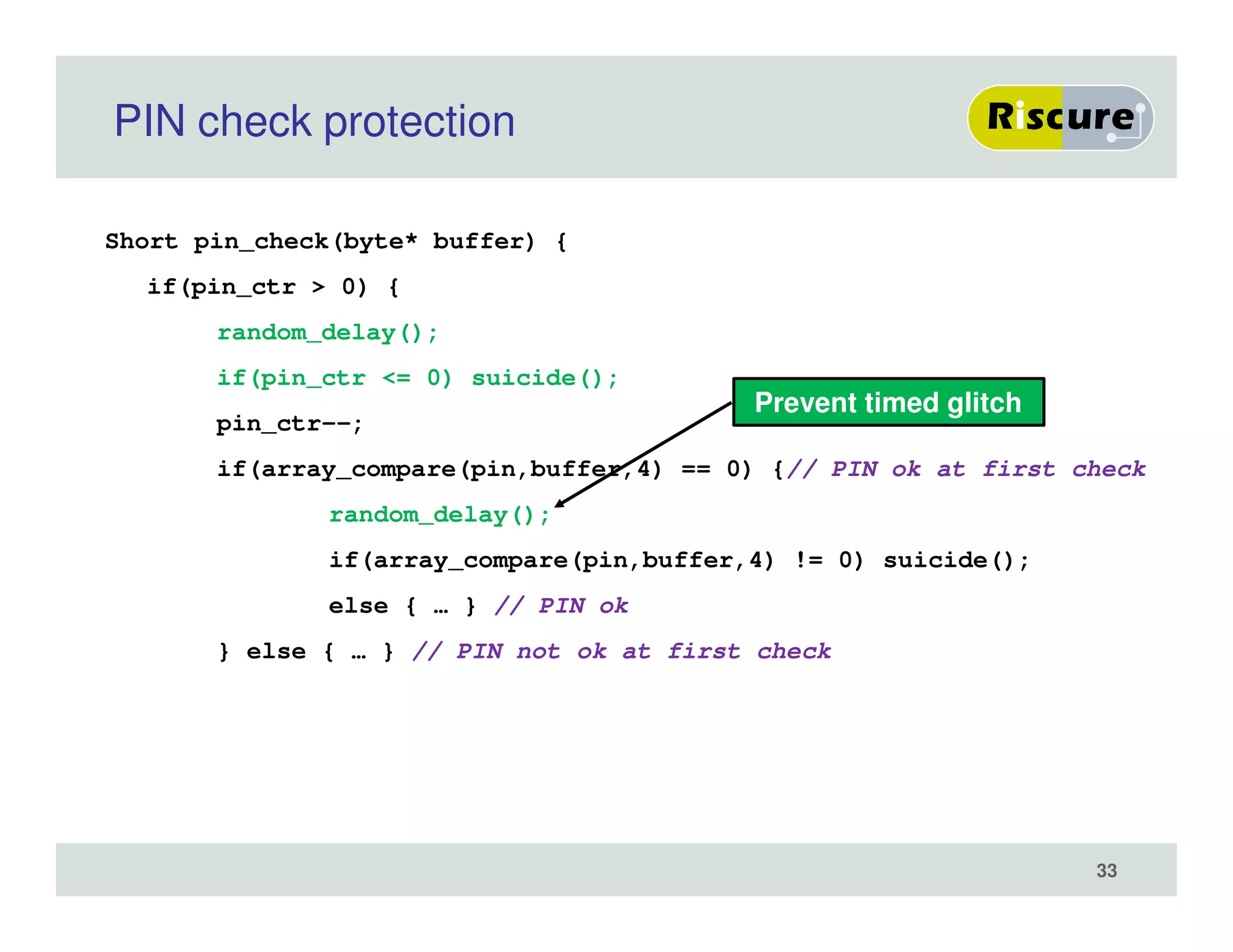
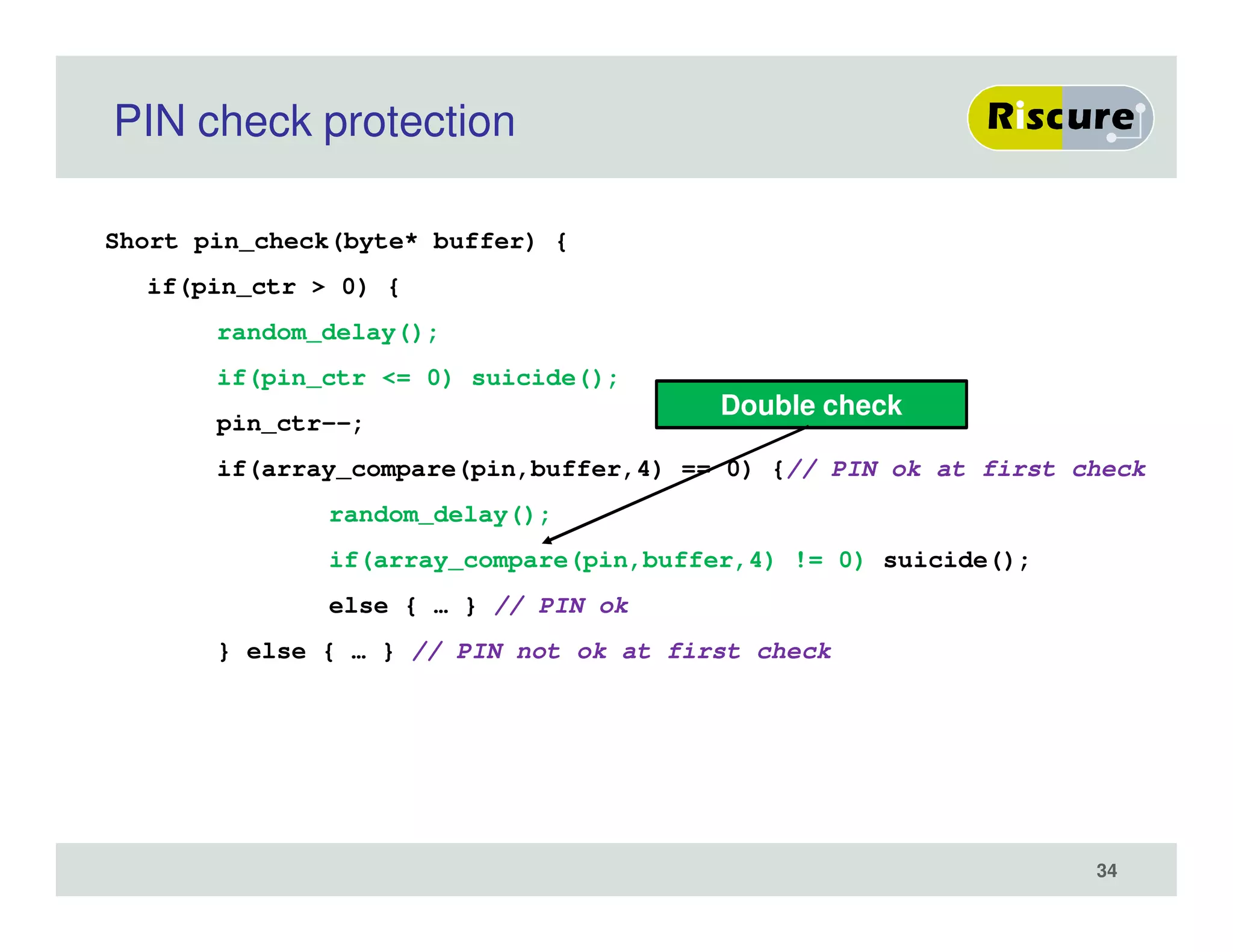
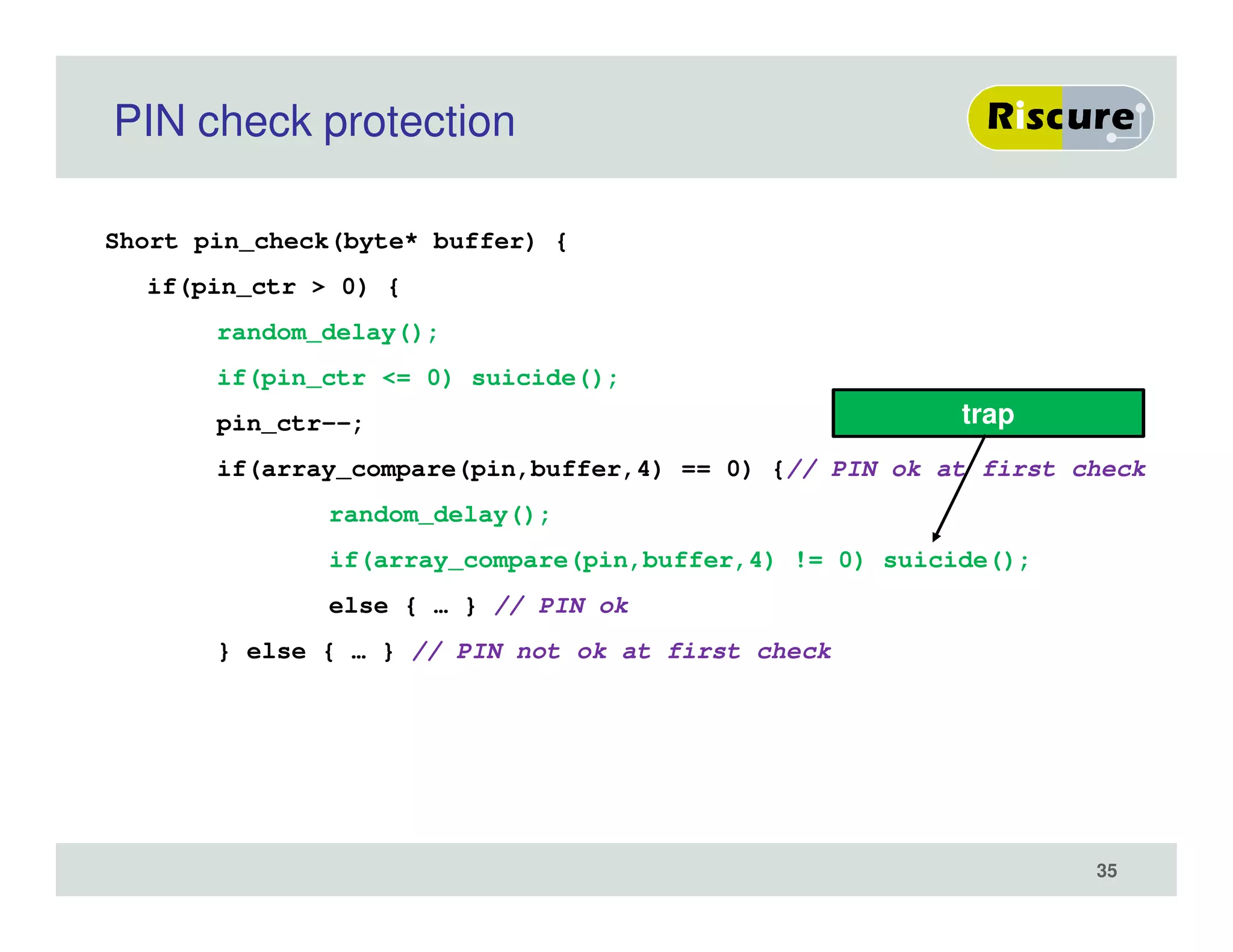
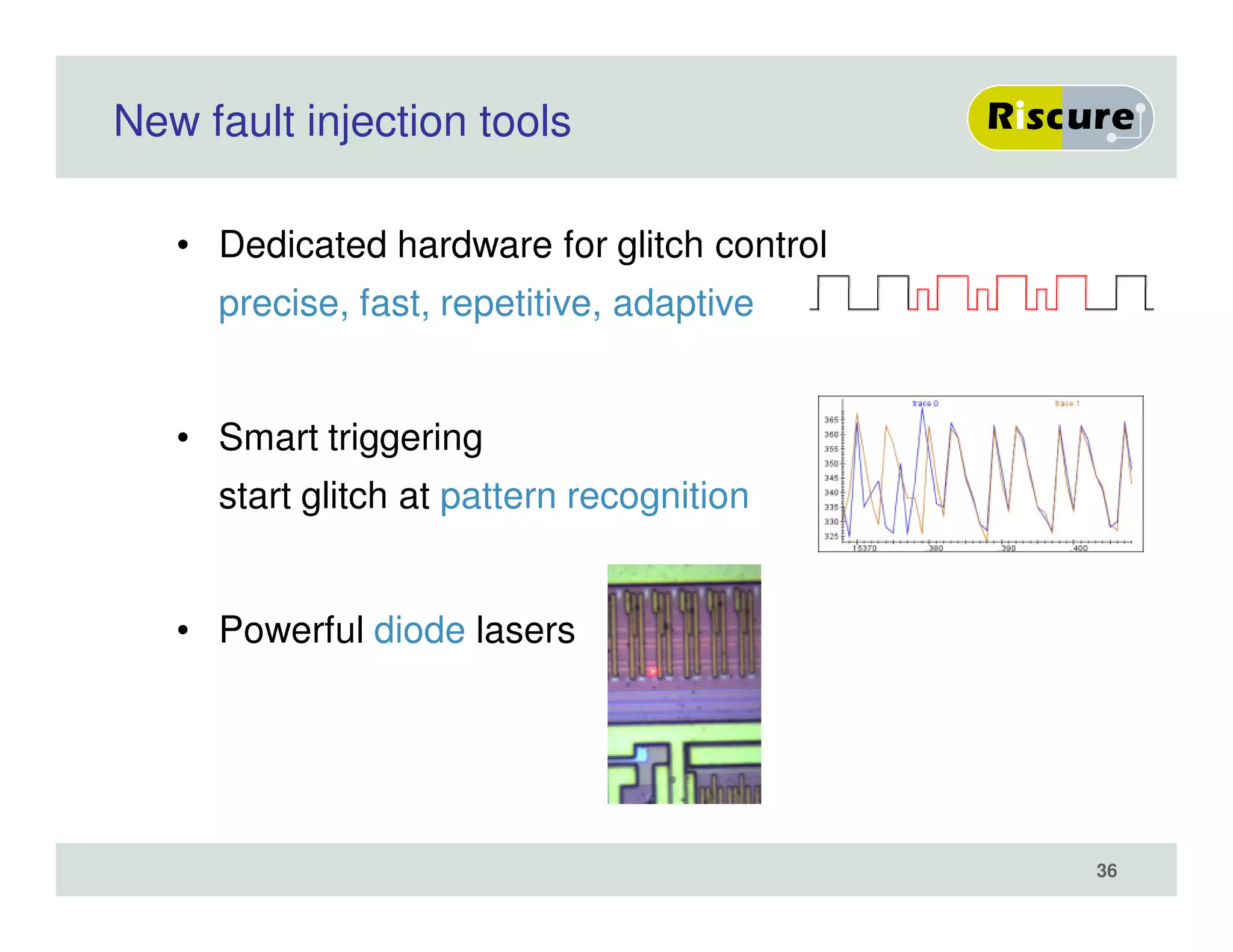
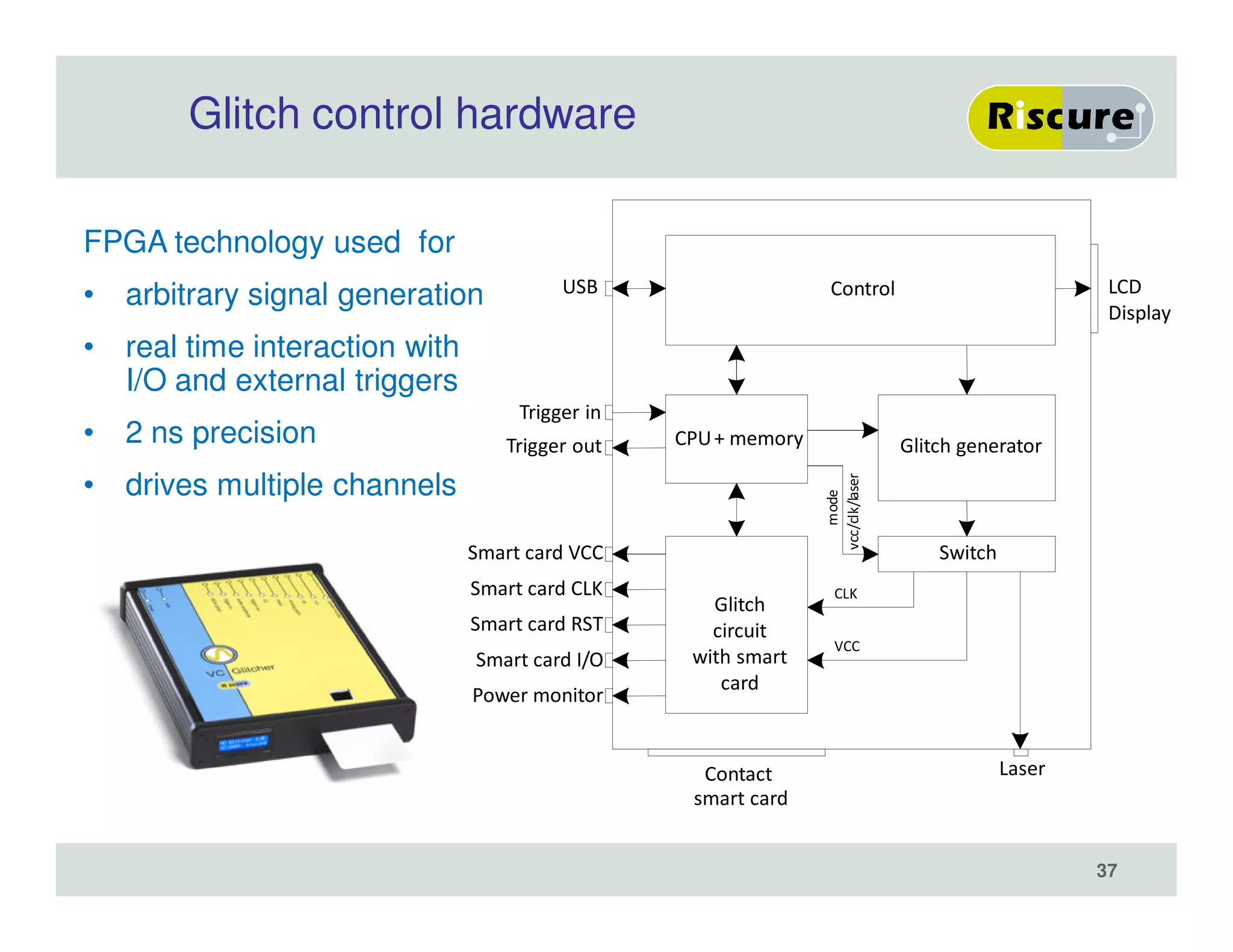
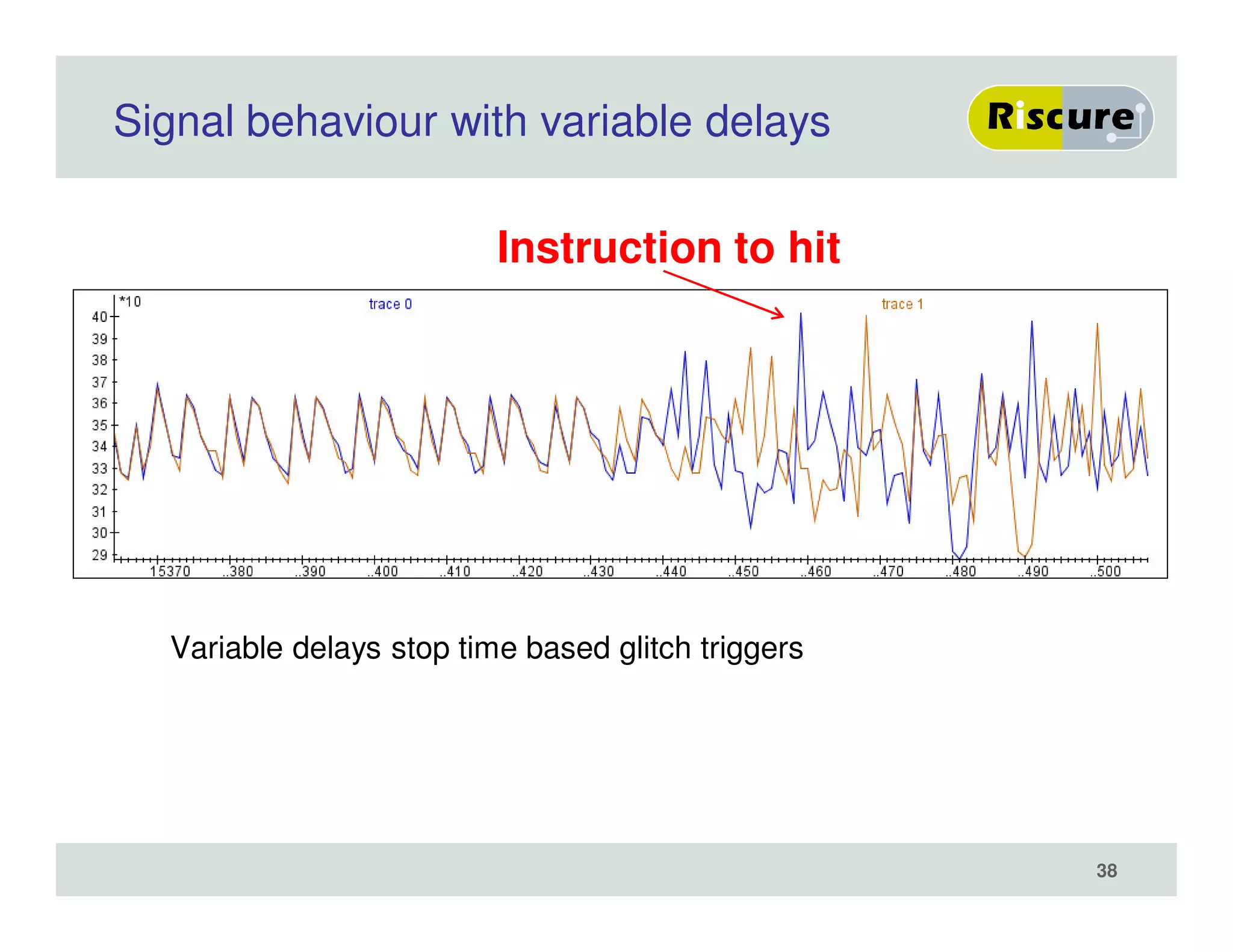
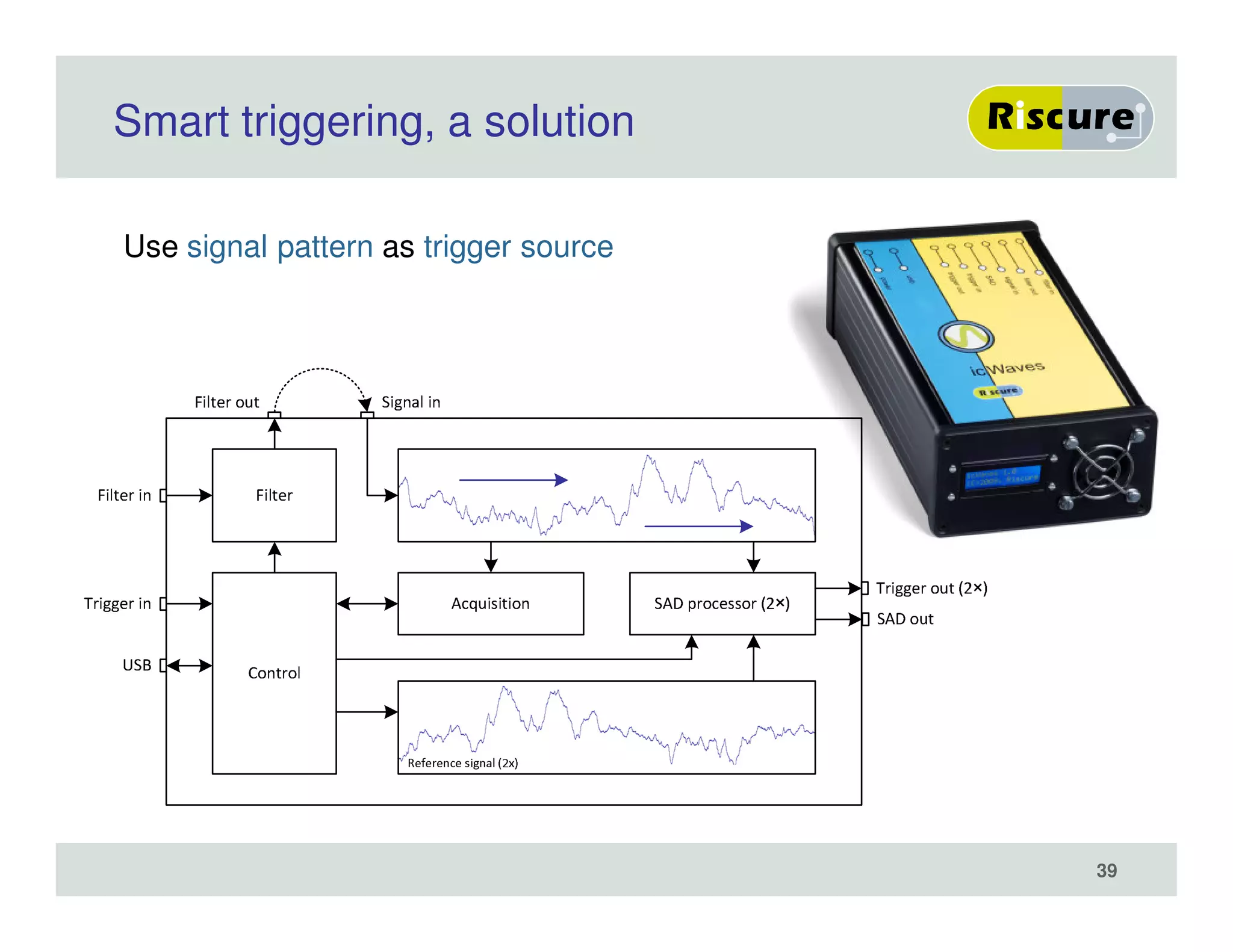
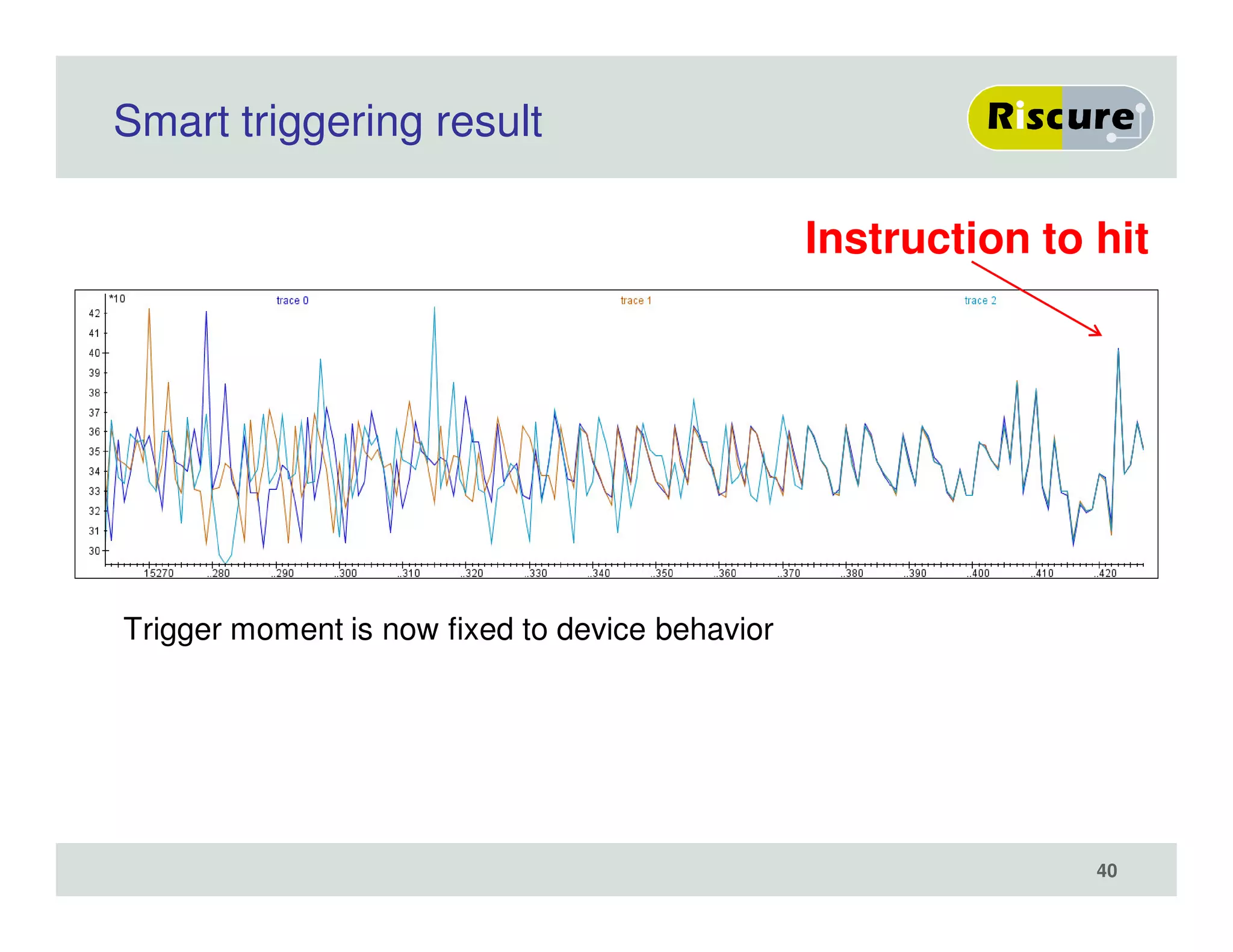
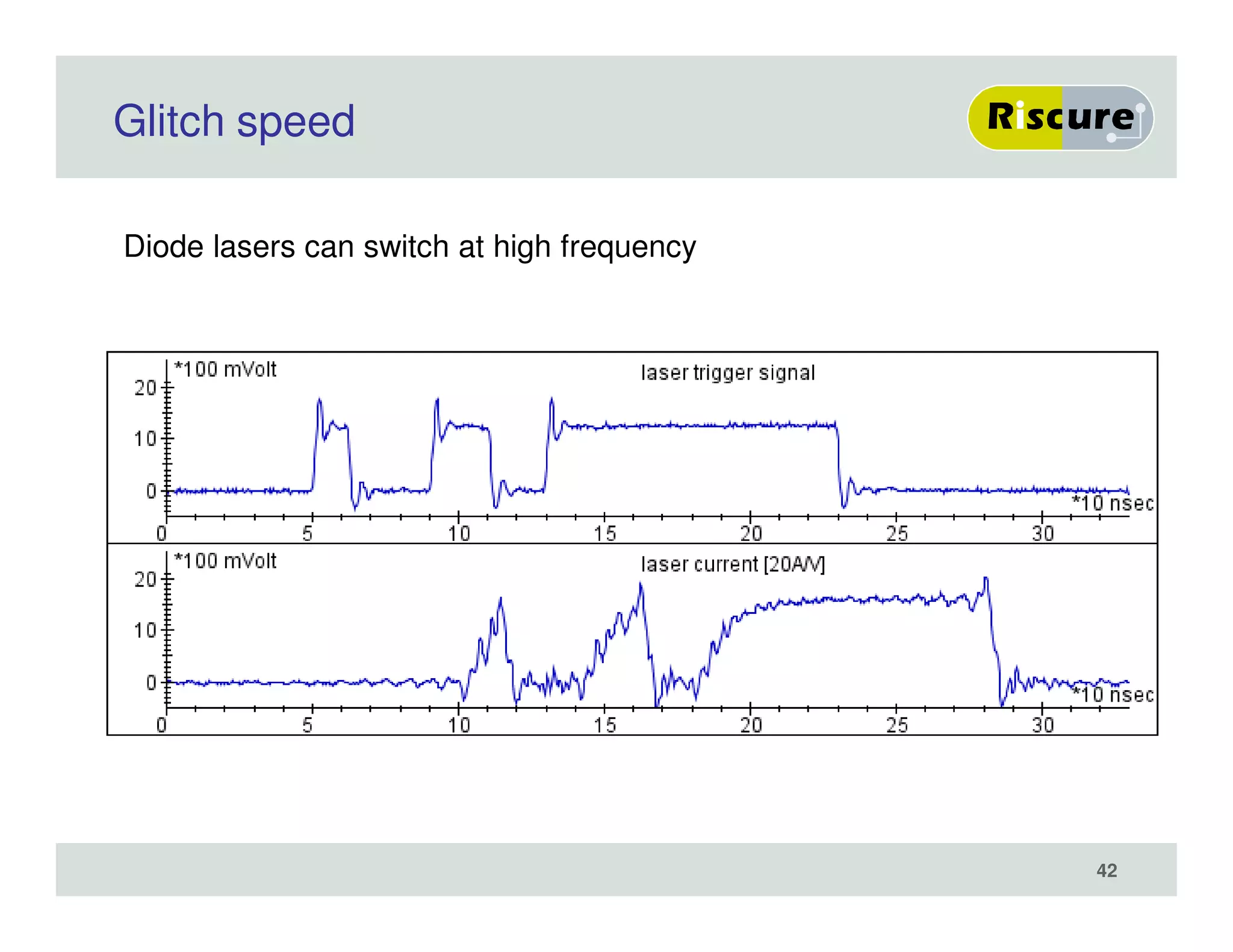
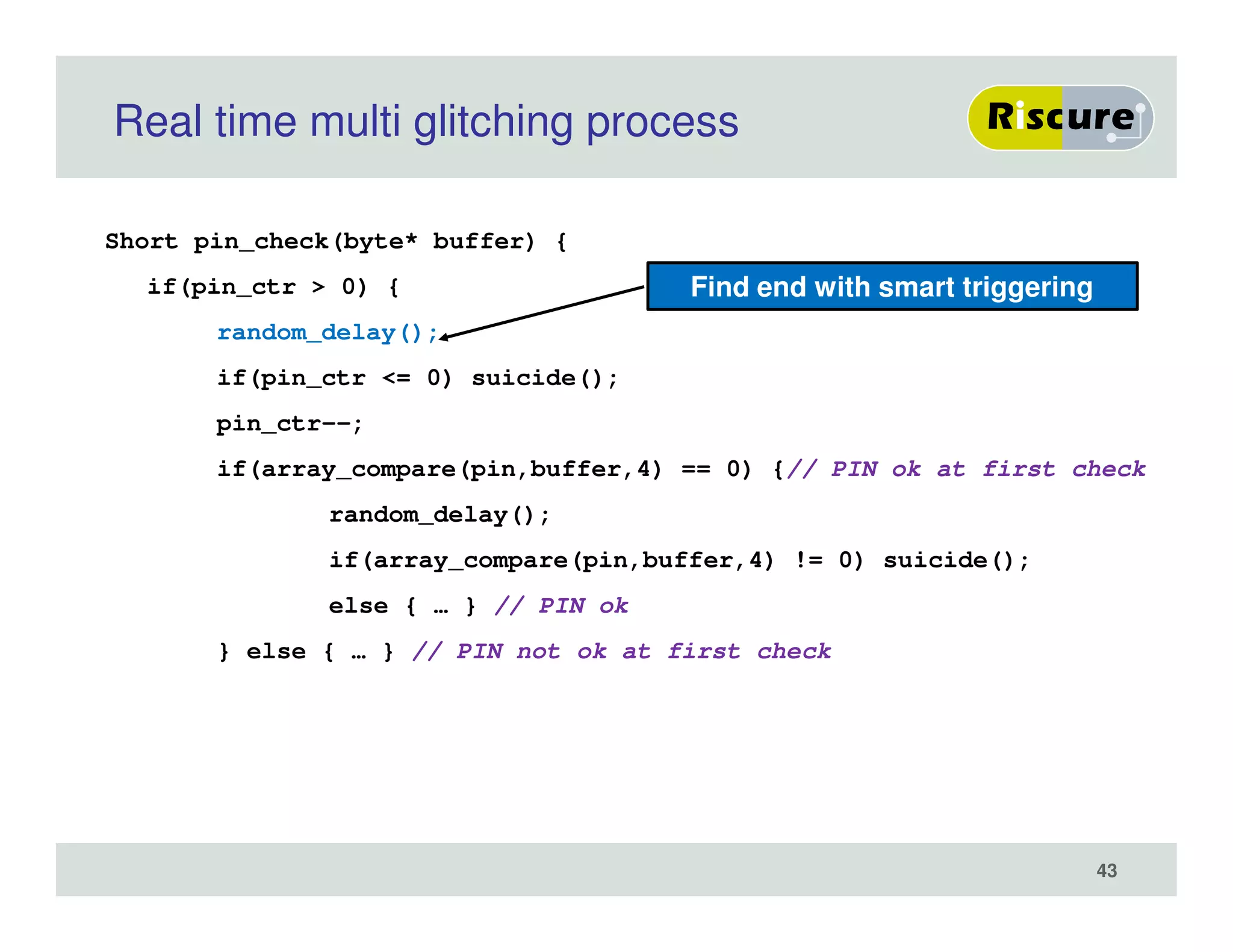
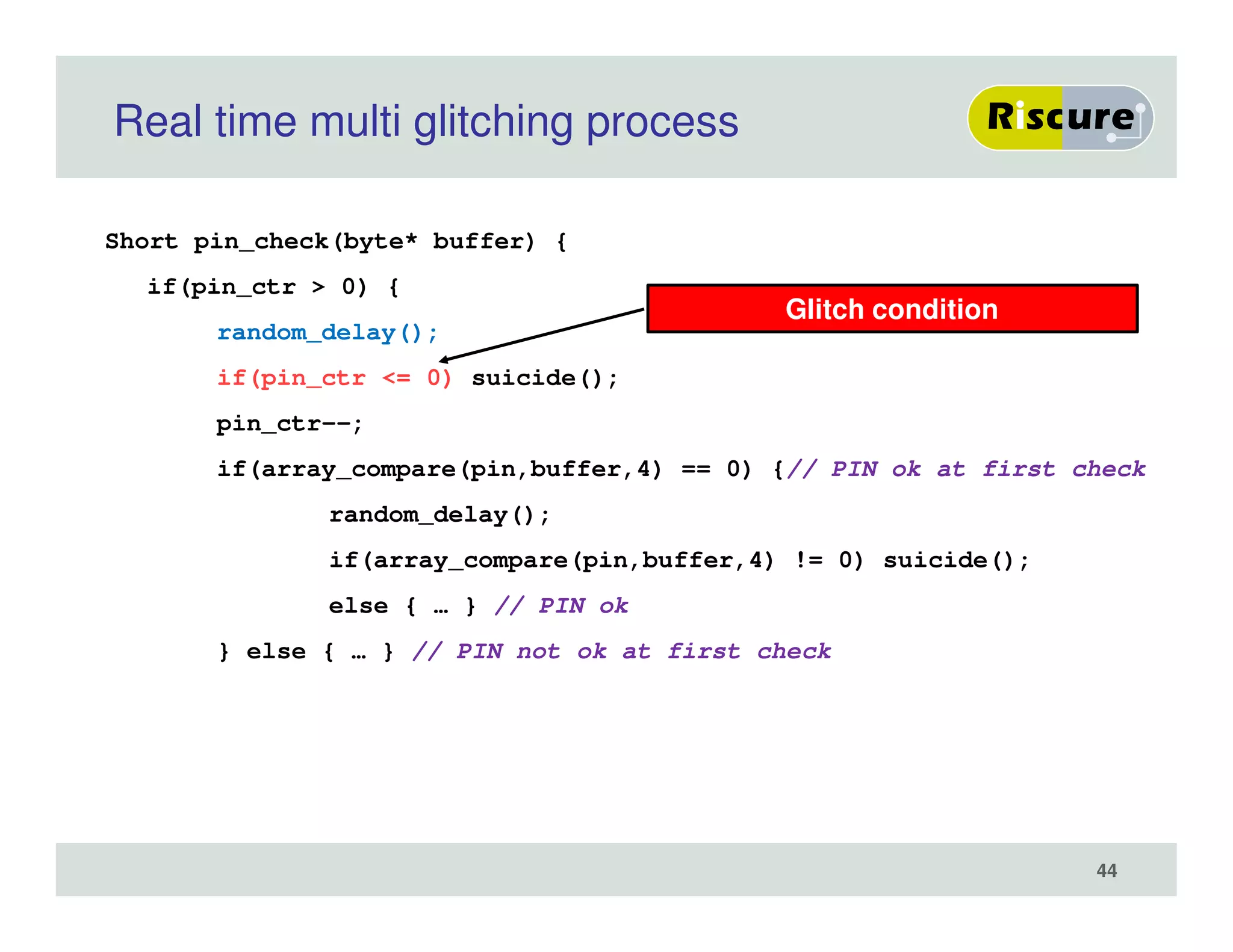
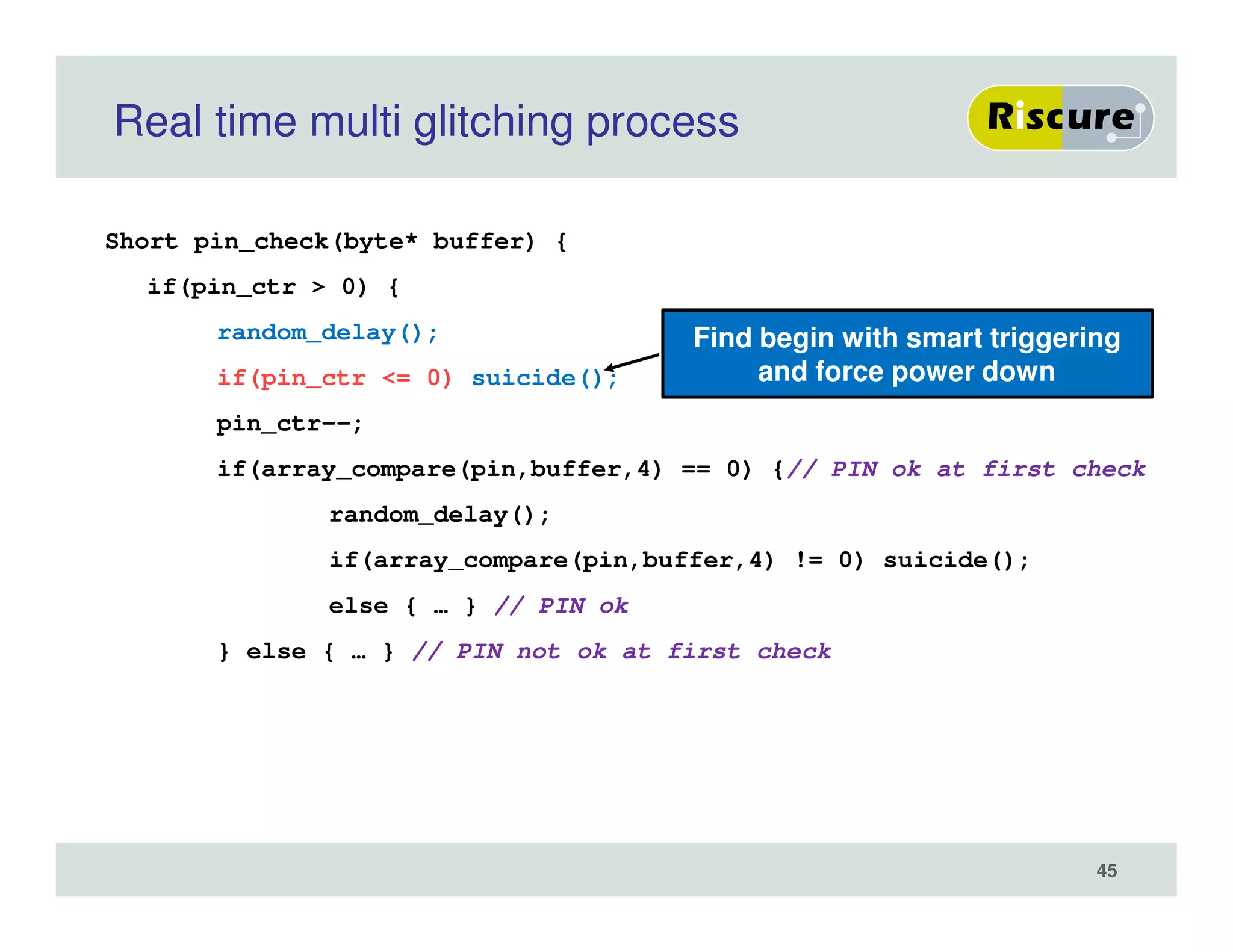
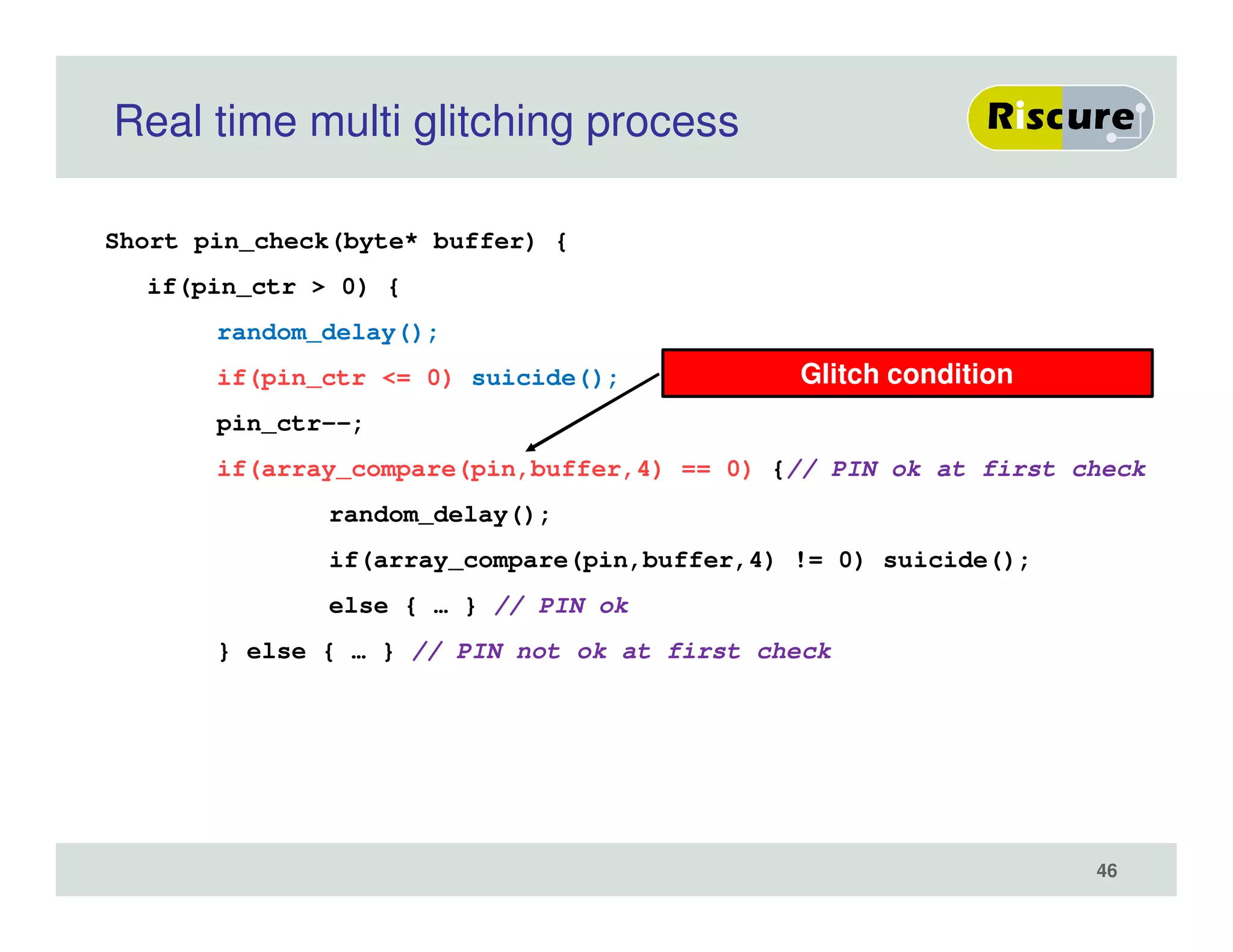
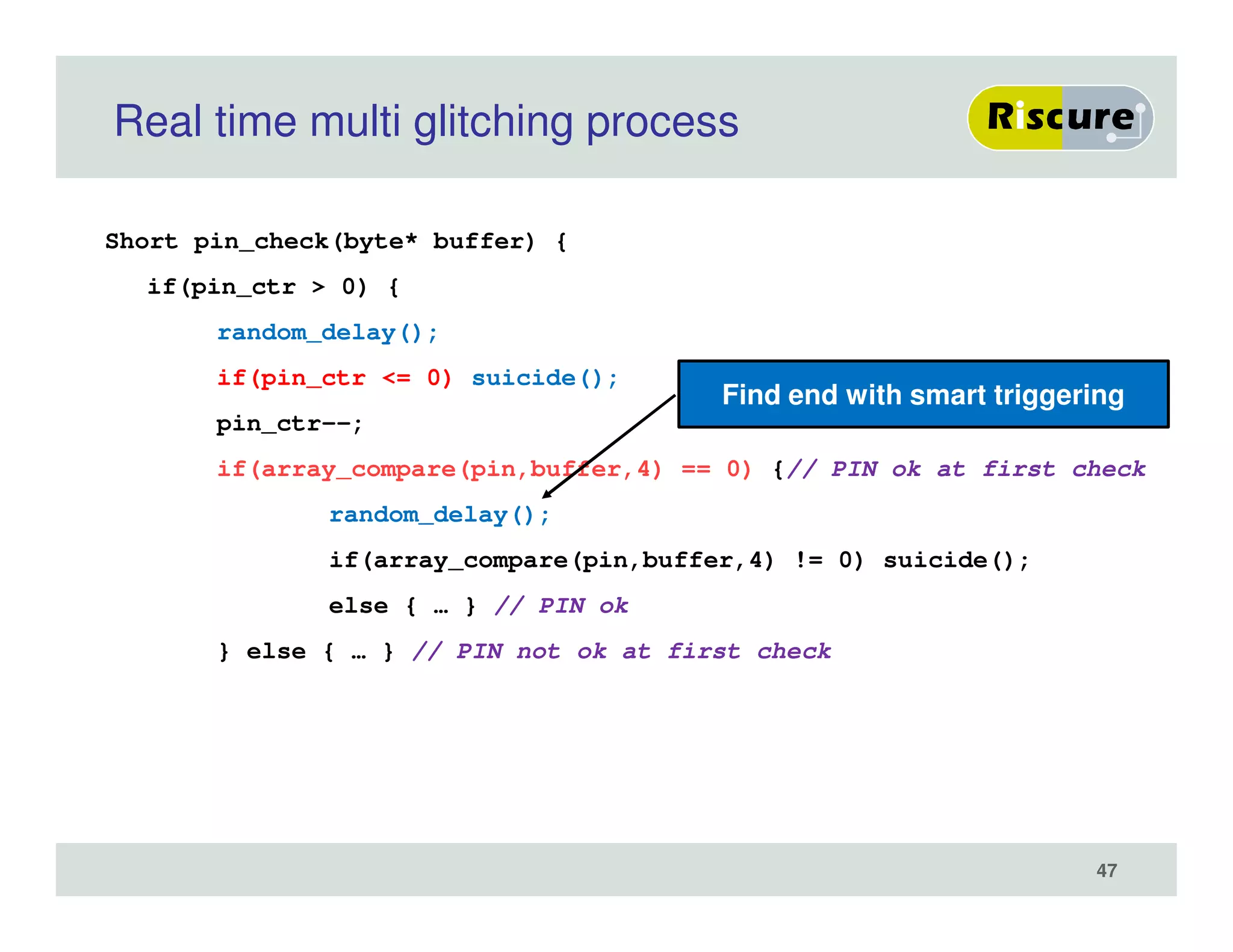
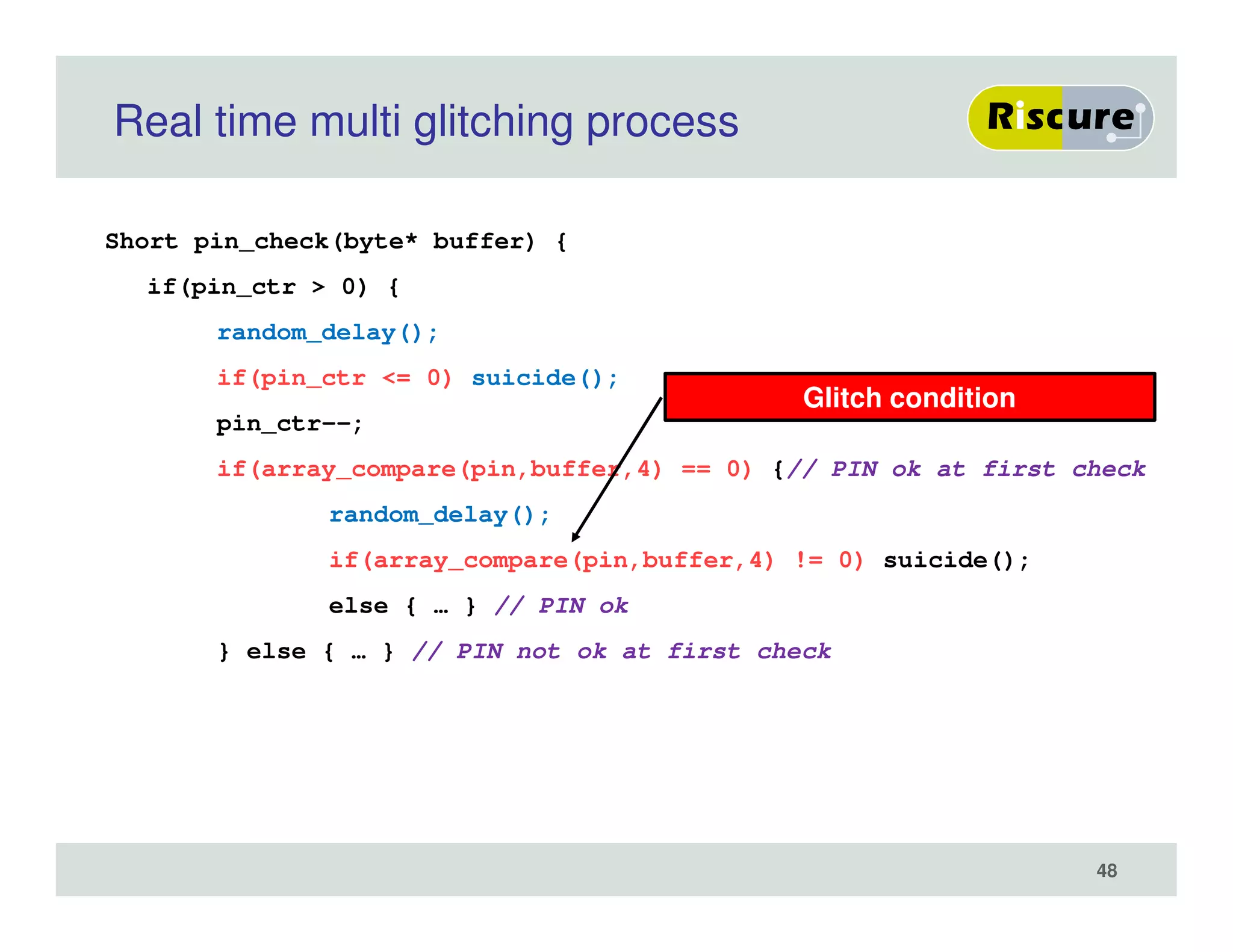
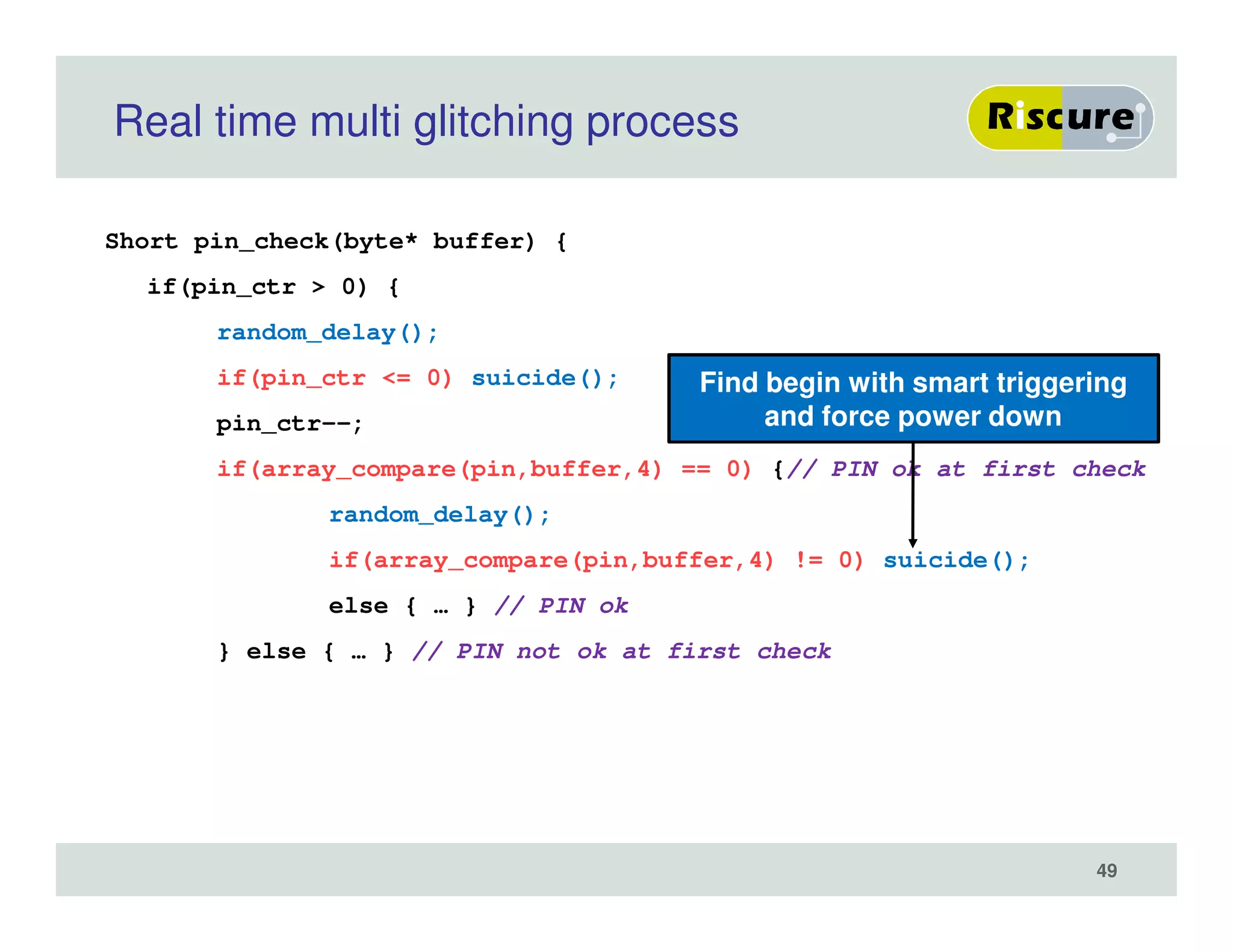
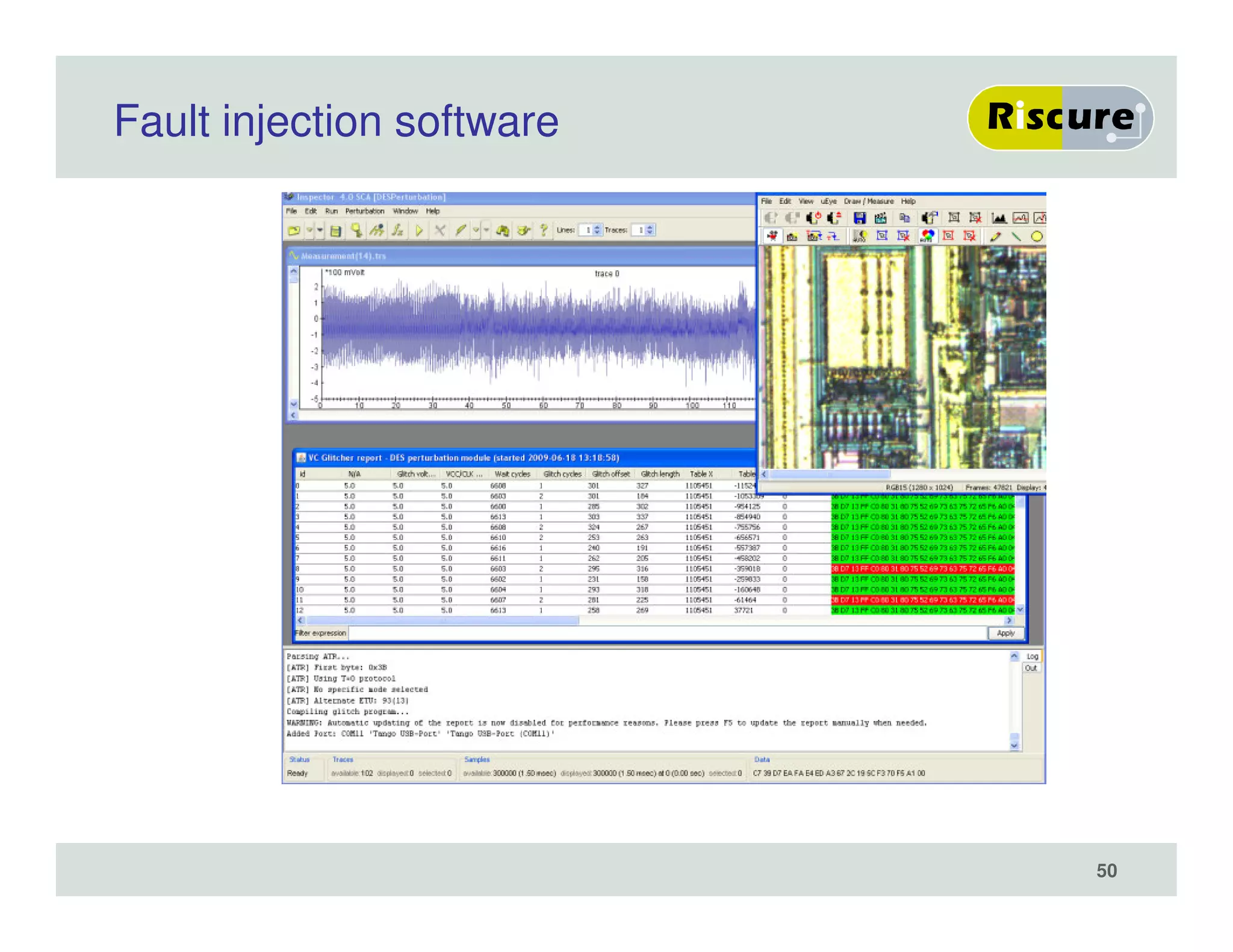
The document discusses the ongoing vulnerabilities to side channel attacks, particularly focusing on RSA cryptography and the methods attackers use to exploit these vulnerabilities through differential fault analysis and power analysis. It highlights various countermeasures that have been developed to combat these attacks, while also acknowledging that advancements in attack techniques continue to evolve. The document underscores the persistent threat posed by side channel attacks, despite efforts to enhance cryptographic security.