Three key topics were discussed:
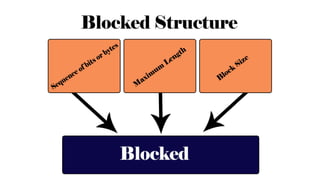
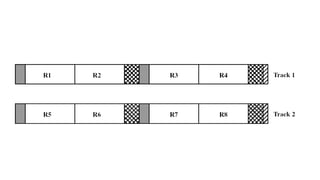
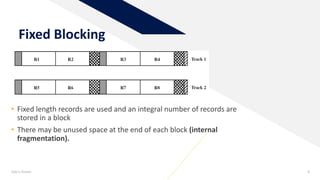
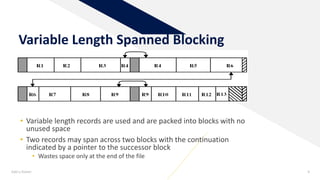
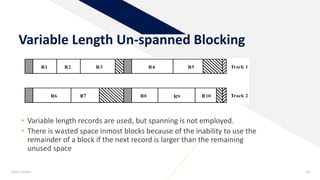
1) Record blocking - the process of grouping related data records into blocks for storage. Fixed, variable-length spanned, and unspanned blocking methods were described.
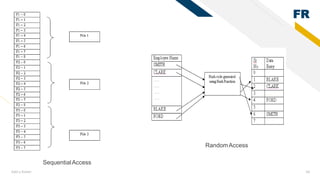
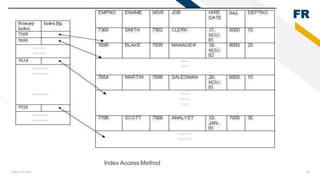
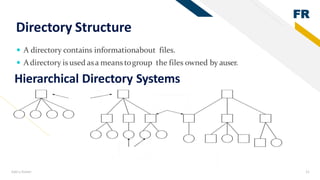
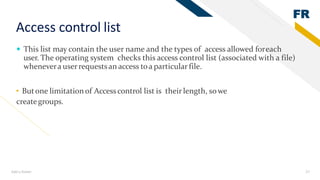
2) File management in secondary memory - files have attributes like name, size, permissions. Common file operations are create, open, read, write. Directory structures and access paths organize files.
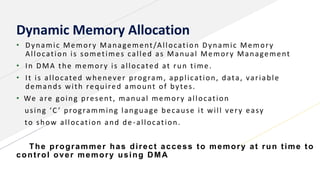
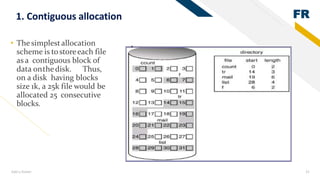
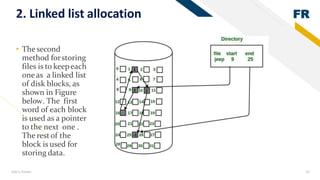
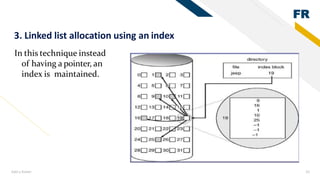
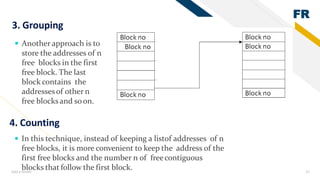
3) Memory allocation - static allocation assigns memory at compile time while dynamic allocation occurs at runtime using functions like malloc(), free(), calloc(), realloc(). Contiguous, linked lists and indexing are approaches to storing files and managing free space.




























![Example:
int[] arr =new int[6];](https://image.slidesharecdn.com/reportblockingmanagementoffilesinsecondrymemorystaticvsdynamicallocation-190918104837/85/Report-blocking-management-of-files-in-secondry-memory-static-vs-dynamic-allocation-42-320.jpg)