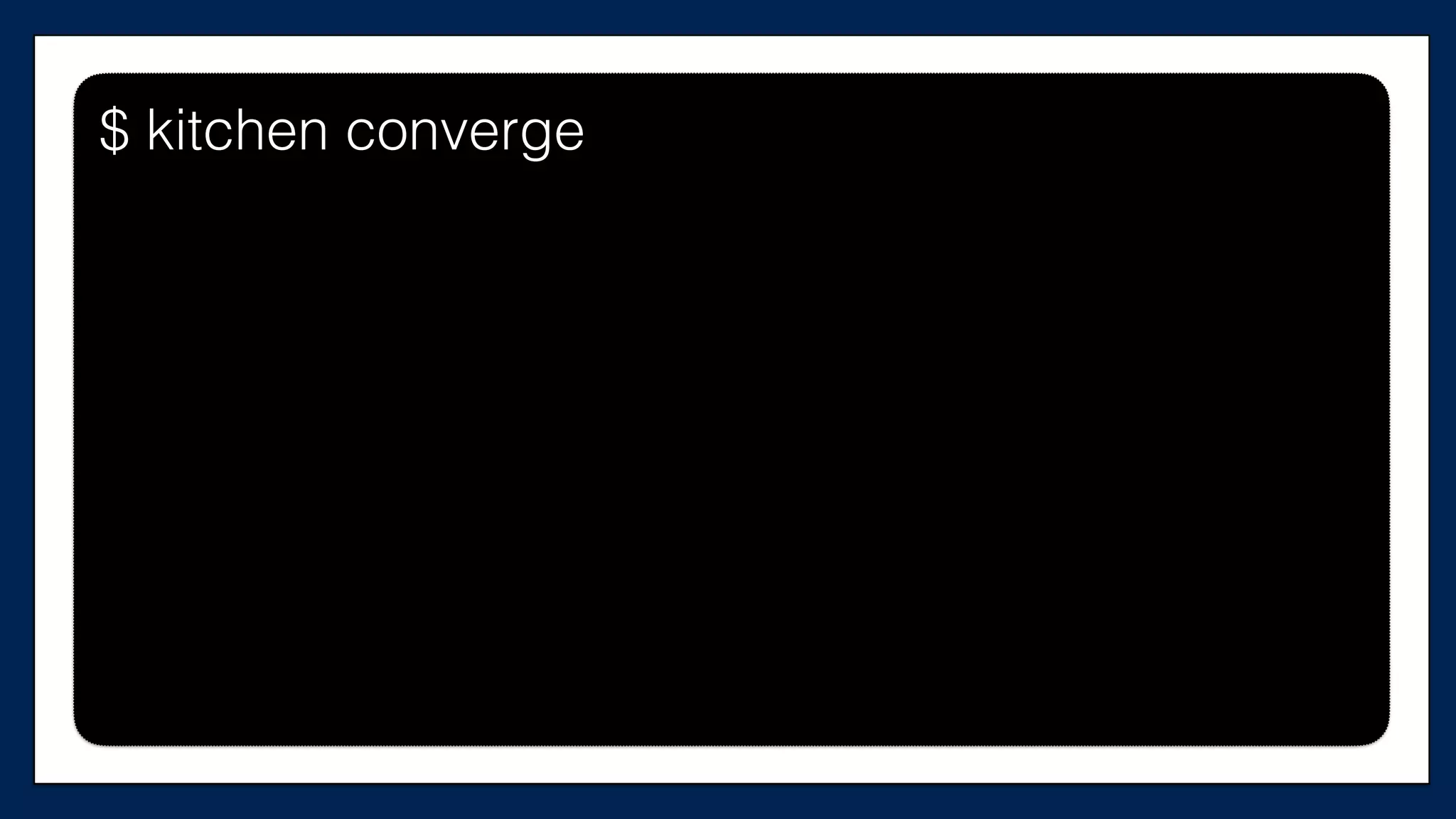
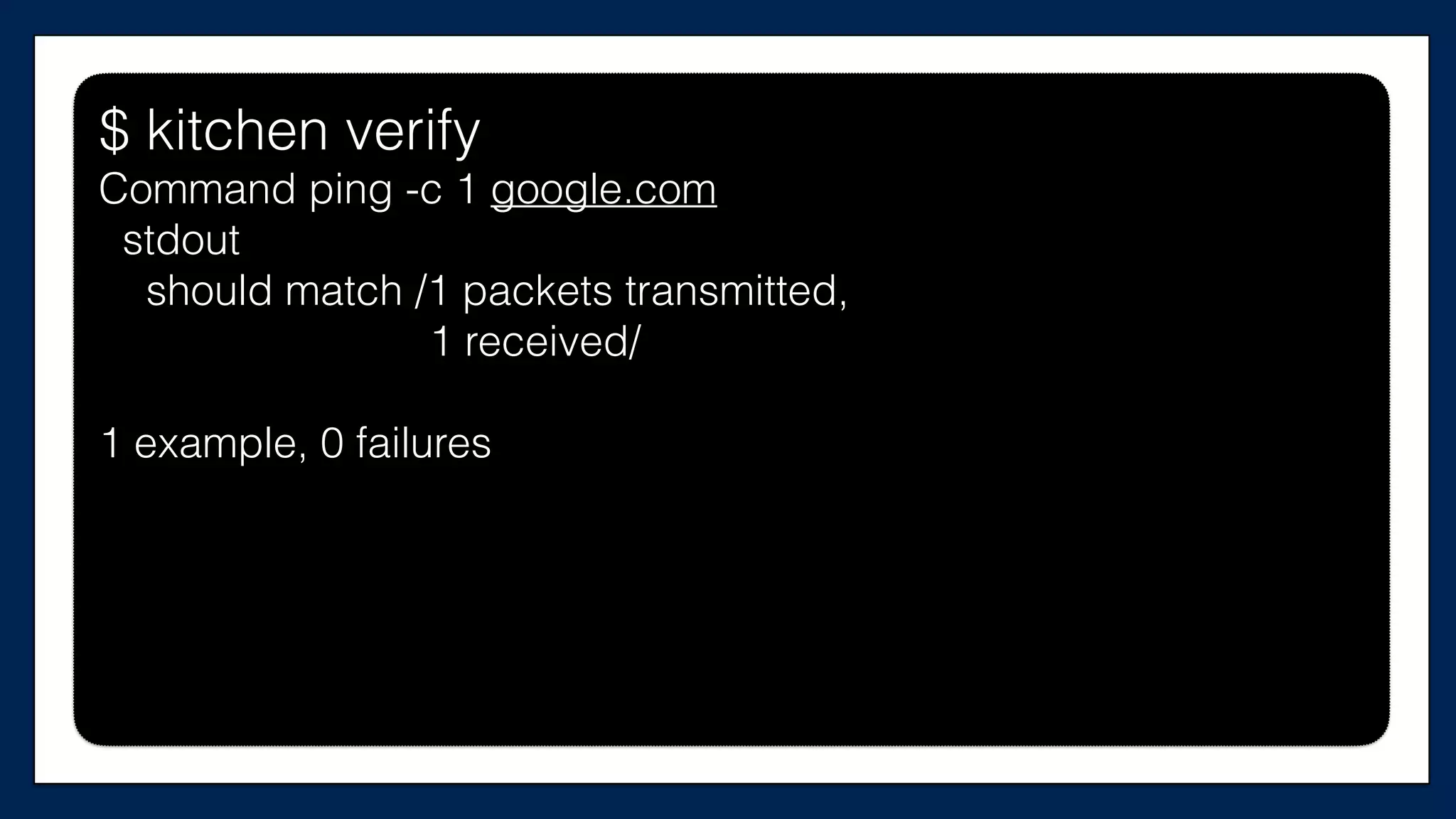
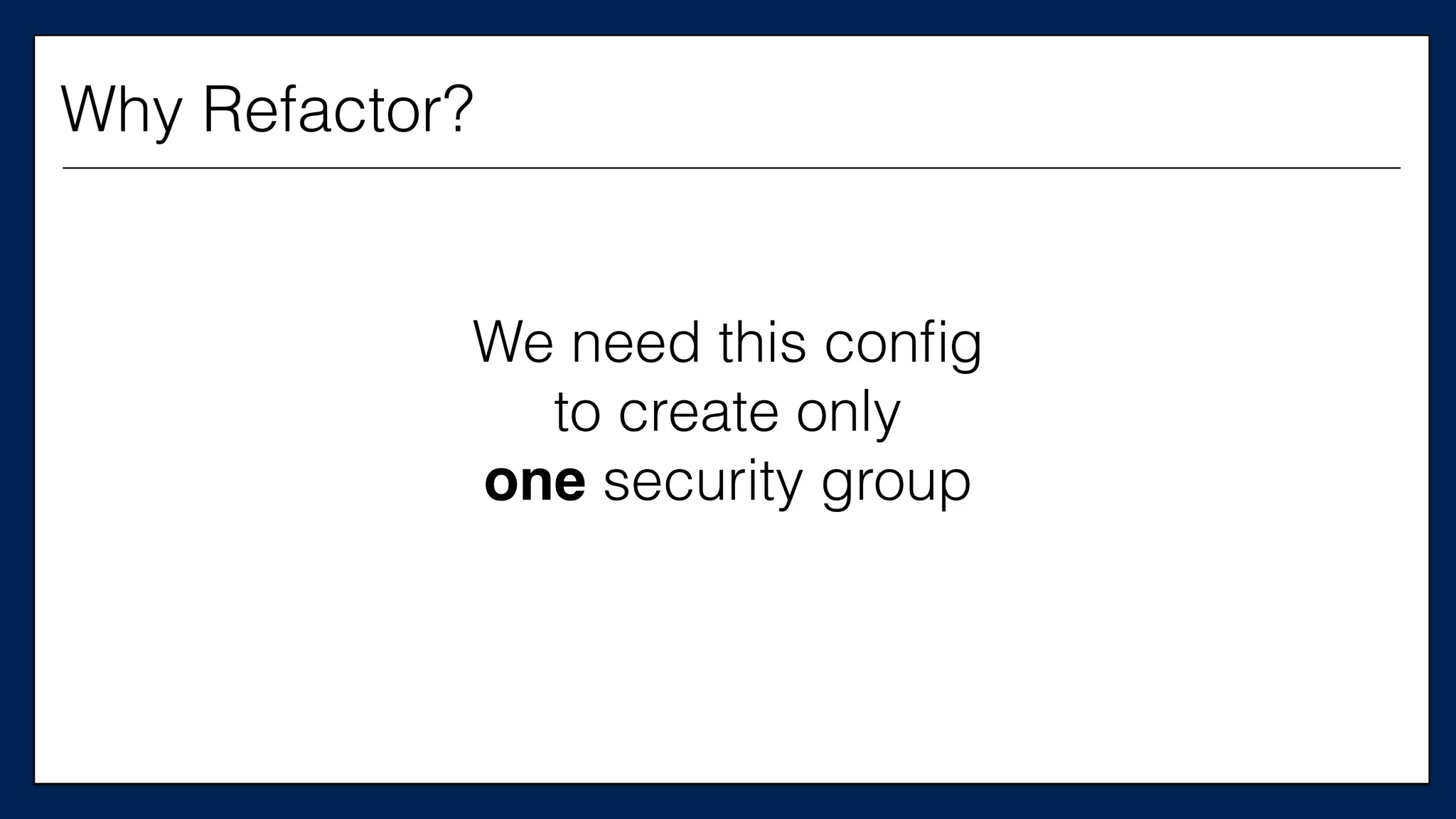
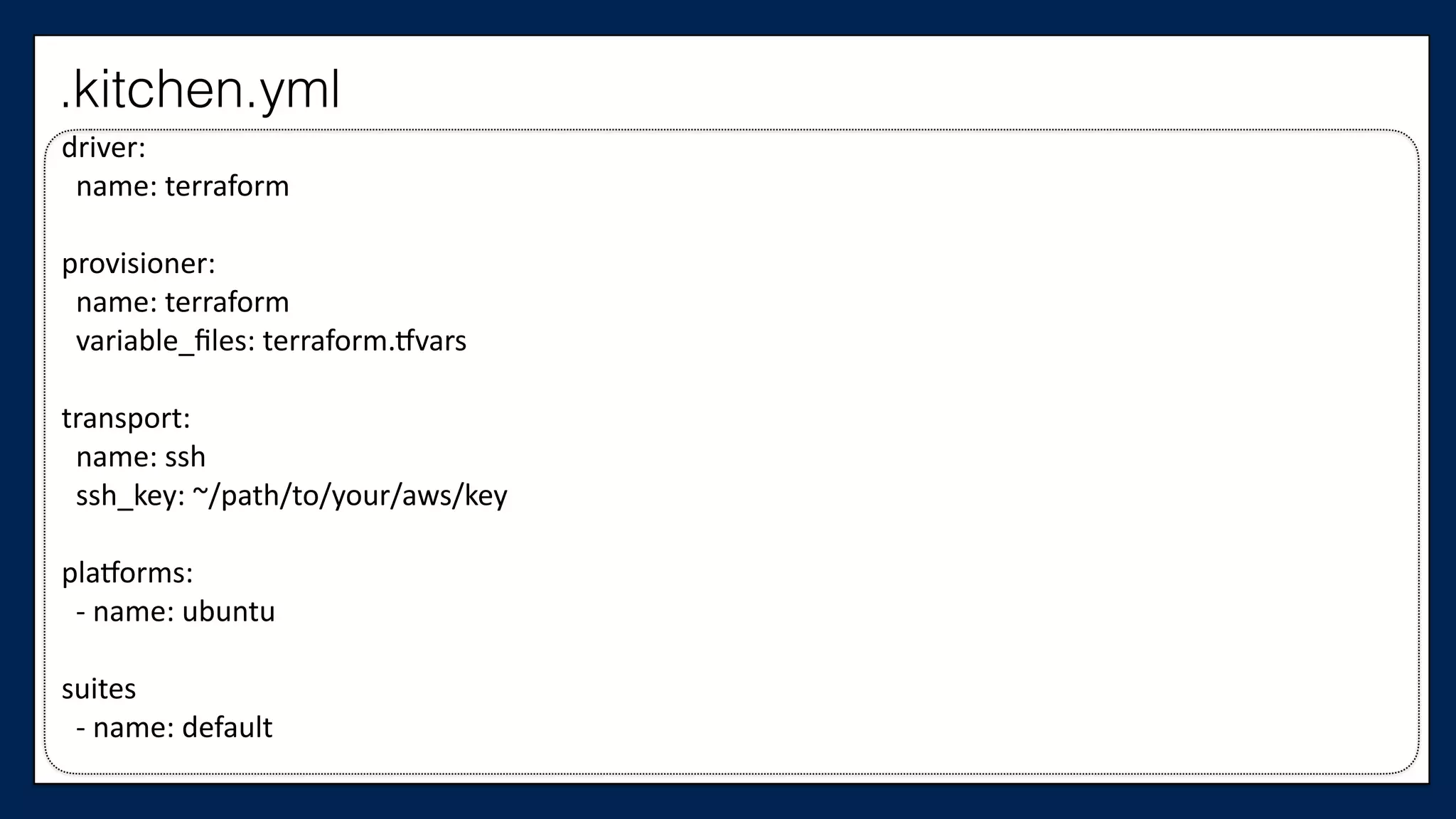
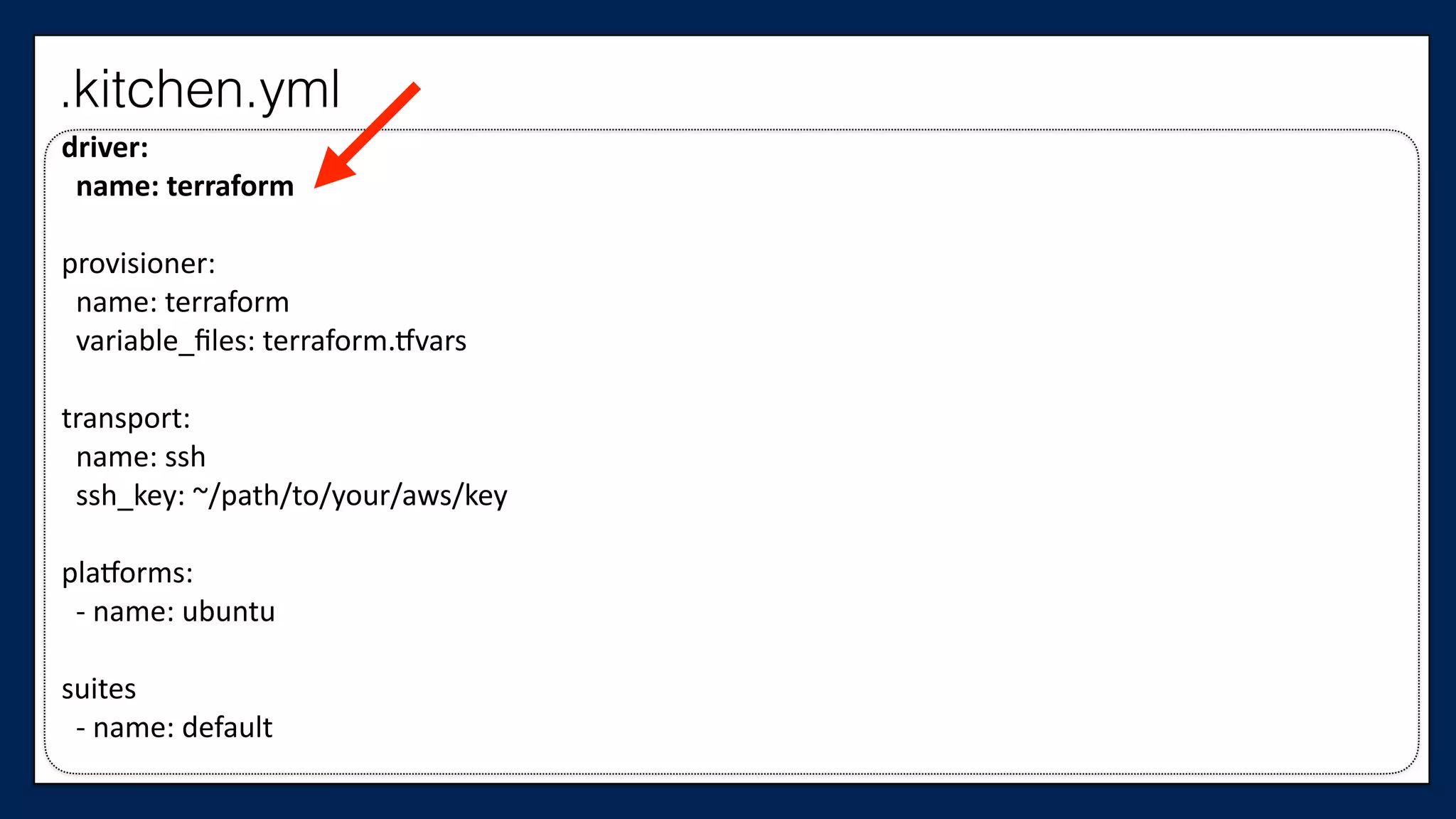
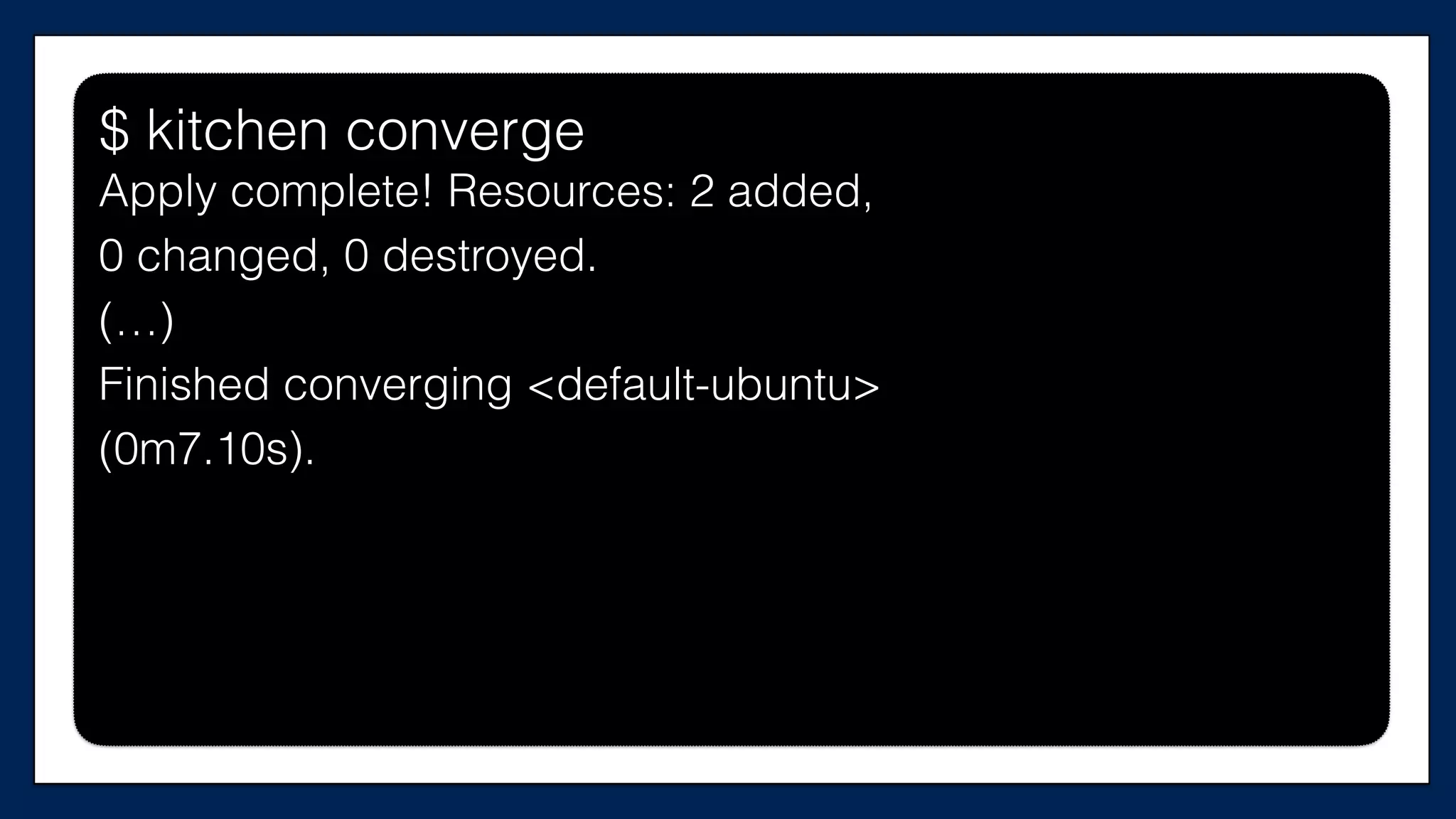
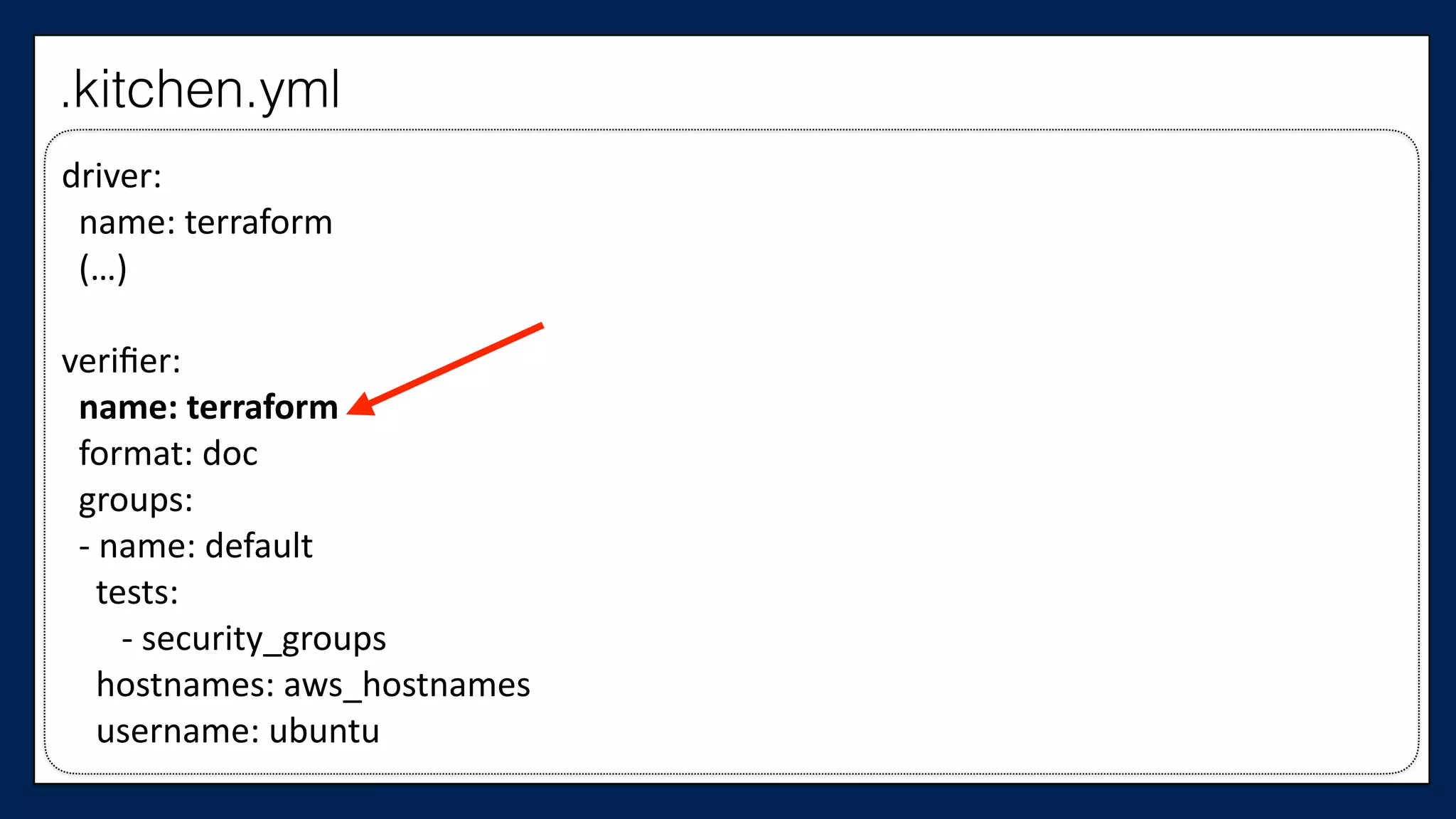
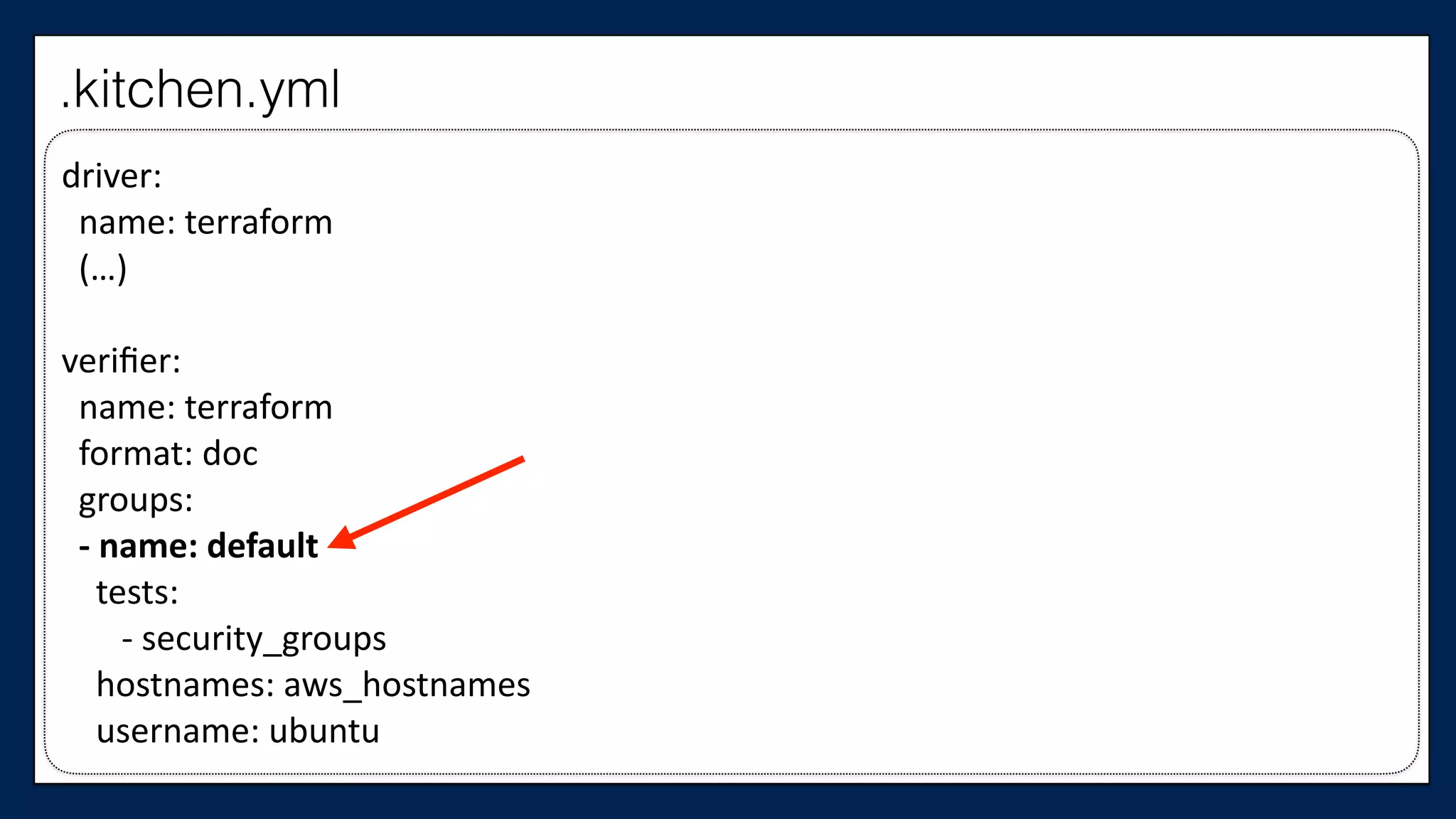
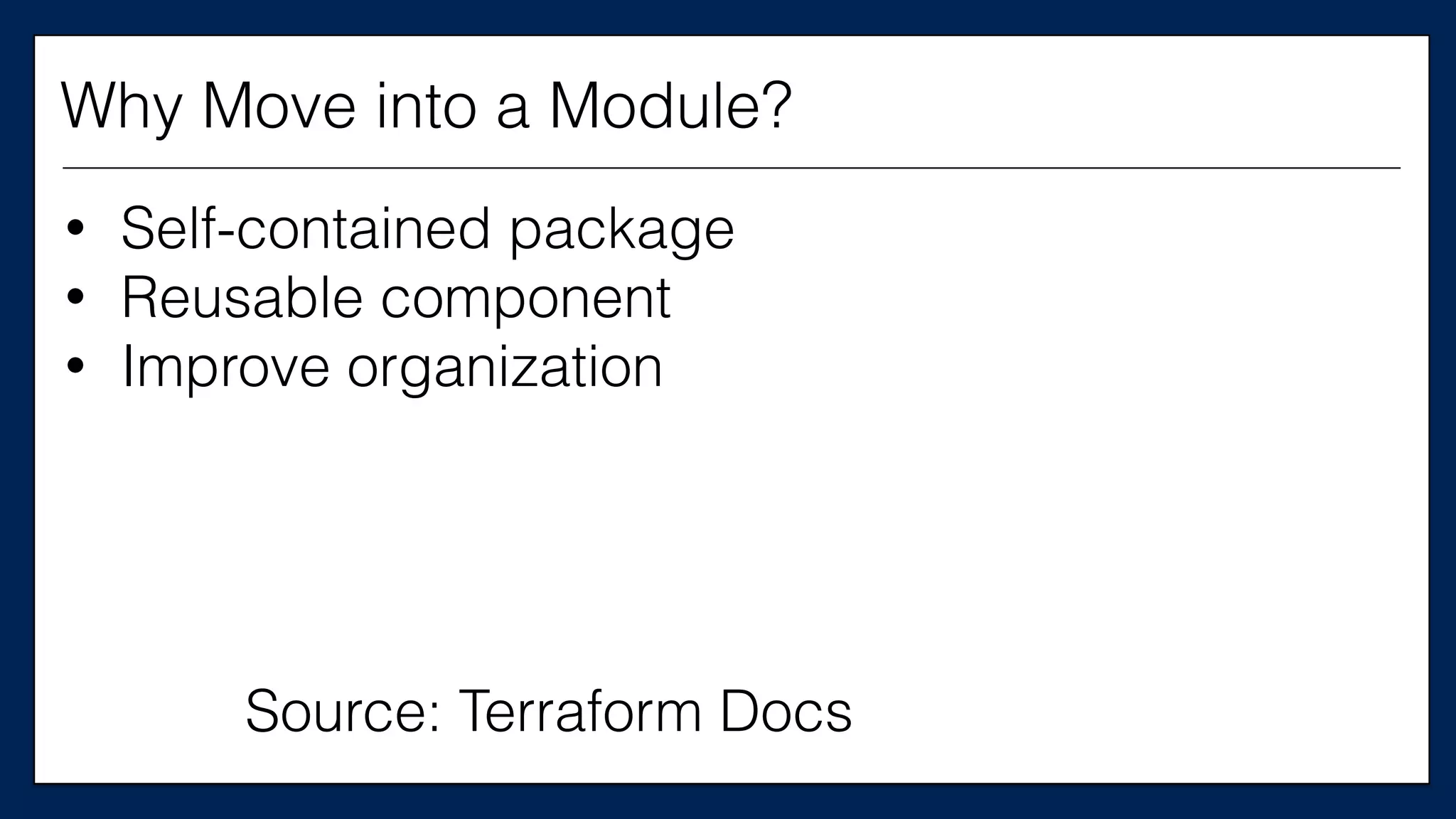
The document discusses the importance of refactoring infrastructure code, specifically focusing on Terraform configurations. It outlines various motivations for refactoring, demonstrates an example with AWS providers and security groups, and emphasizes the necessity of testing to ensure improvements. Additionally, it presents tools like Test Kitchen and Kitchen-Terraform for testing Terraform code effectively.






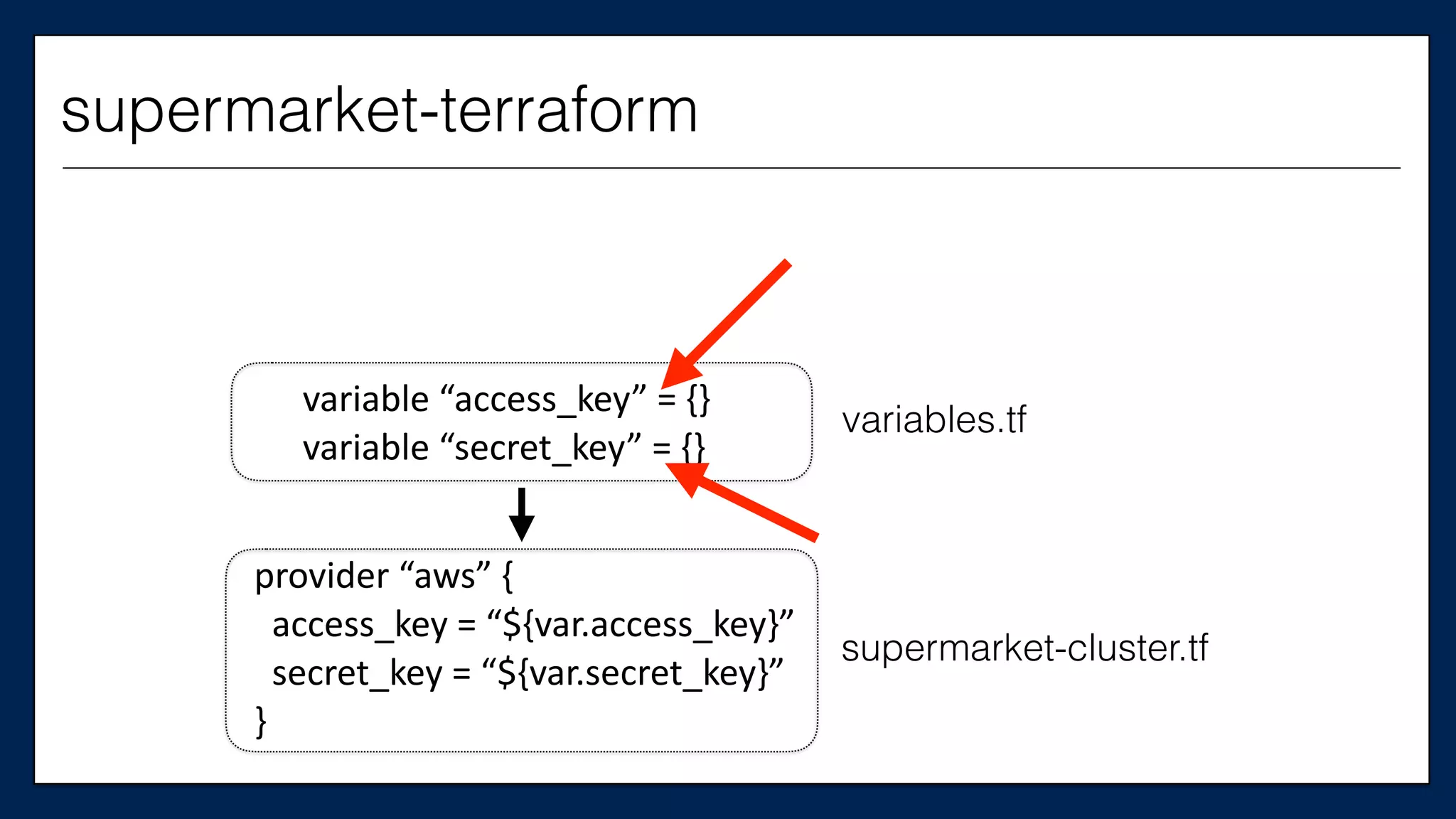
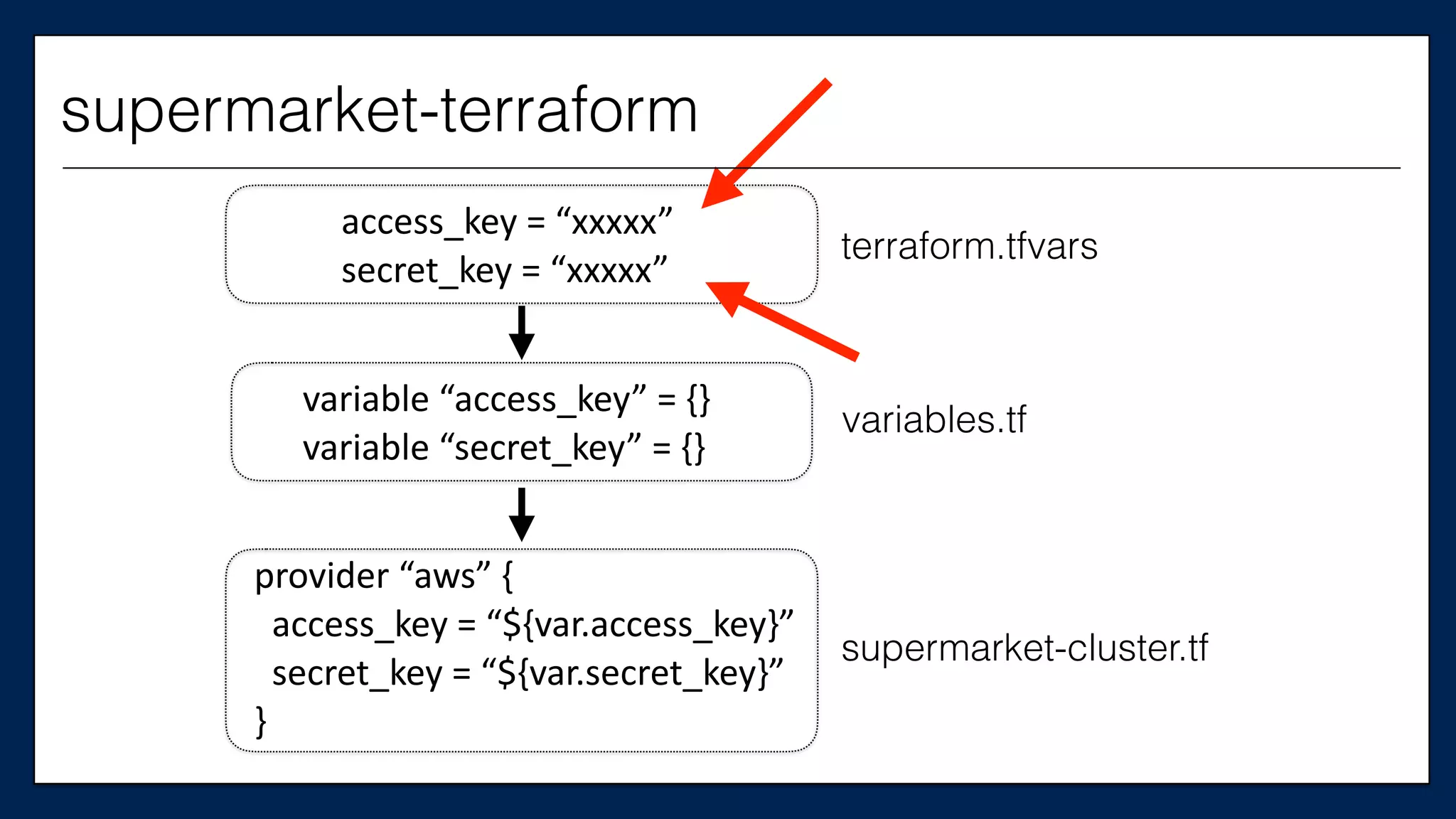



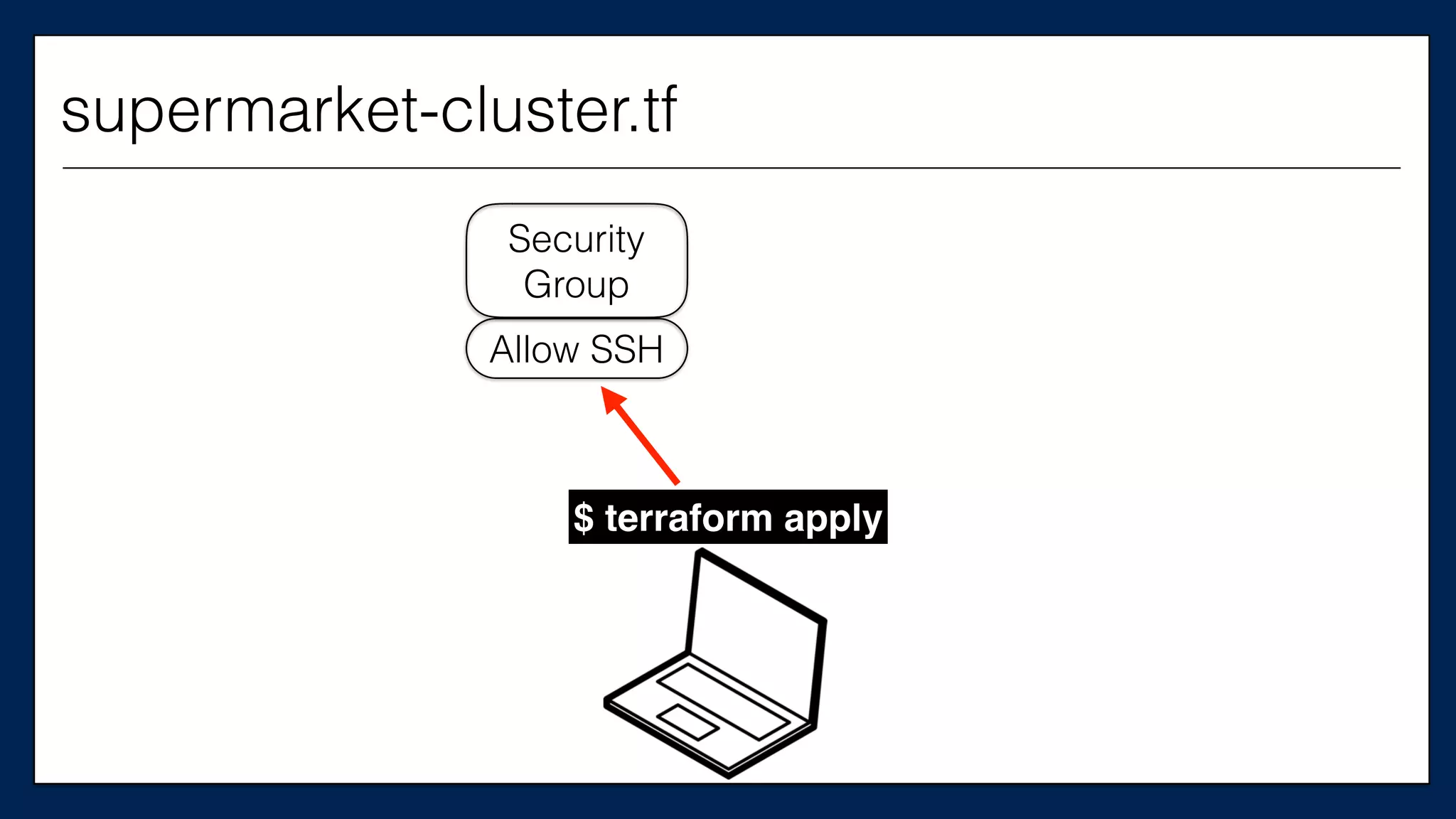
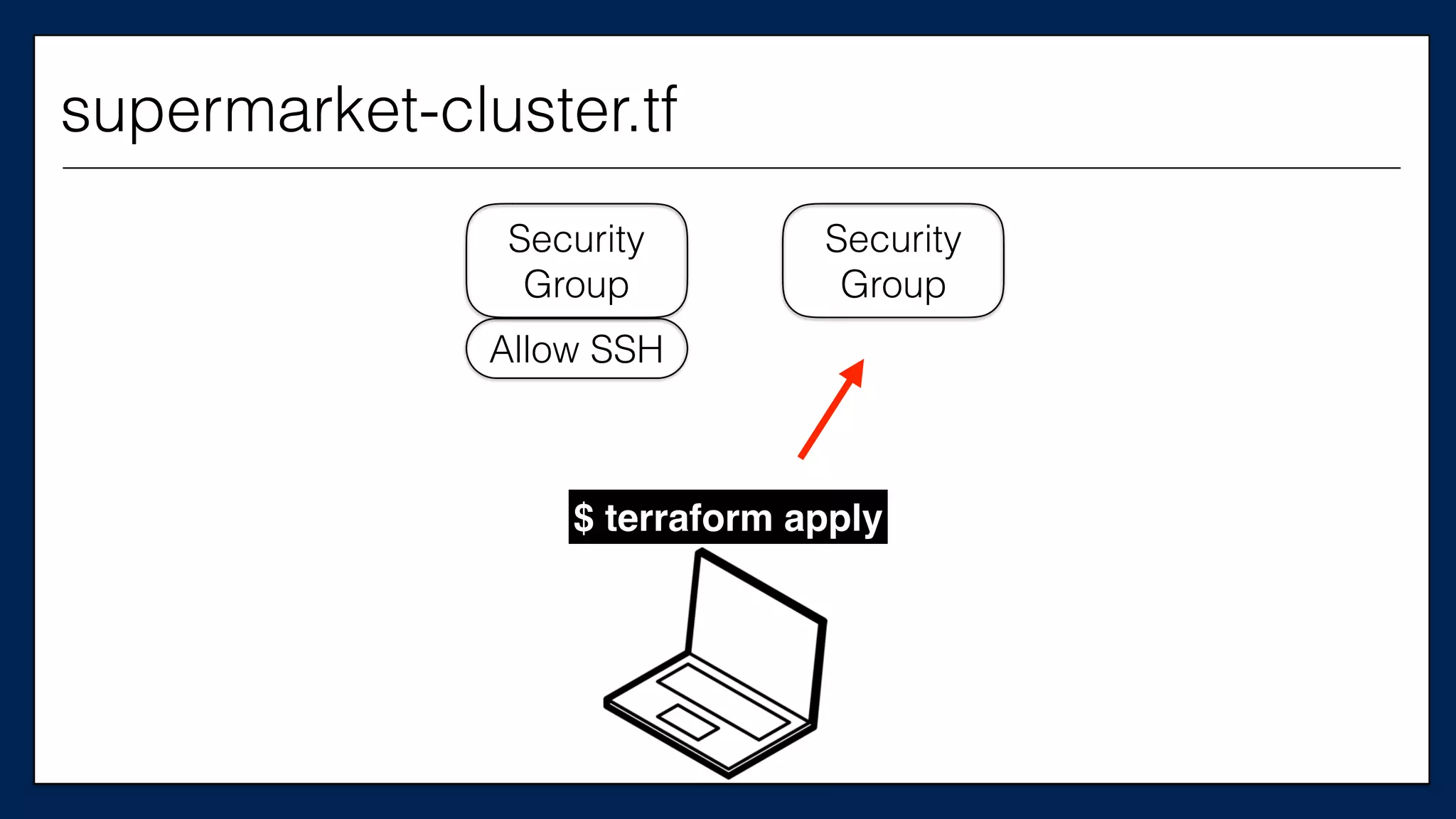
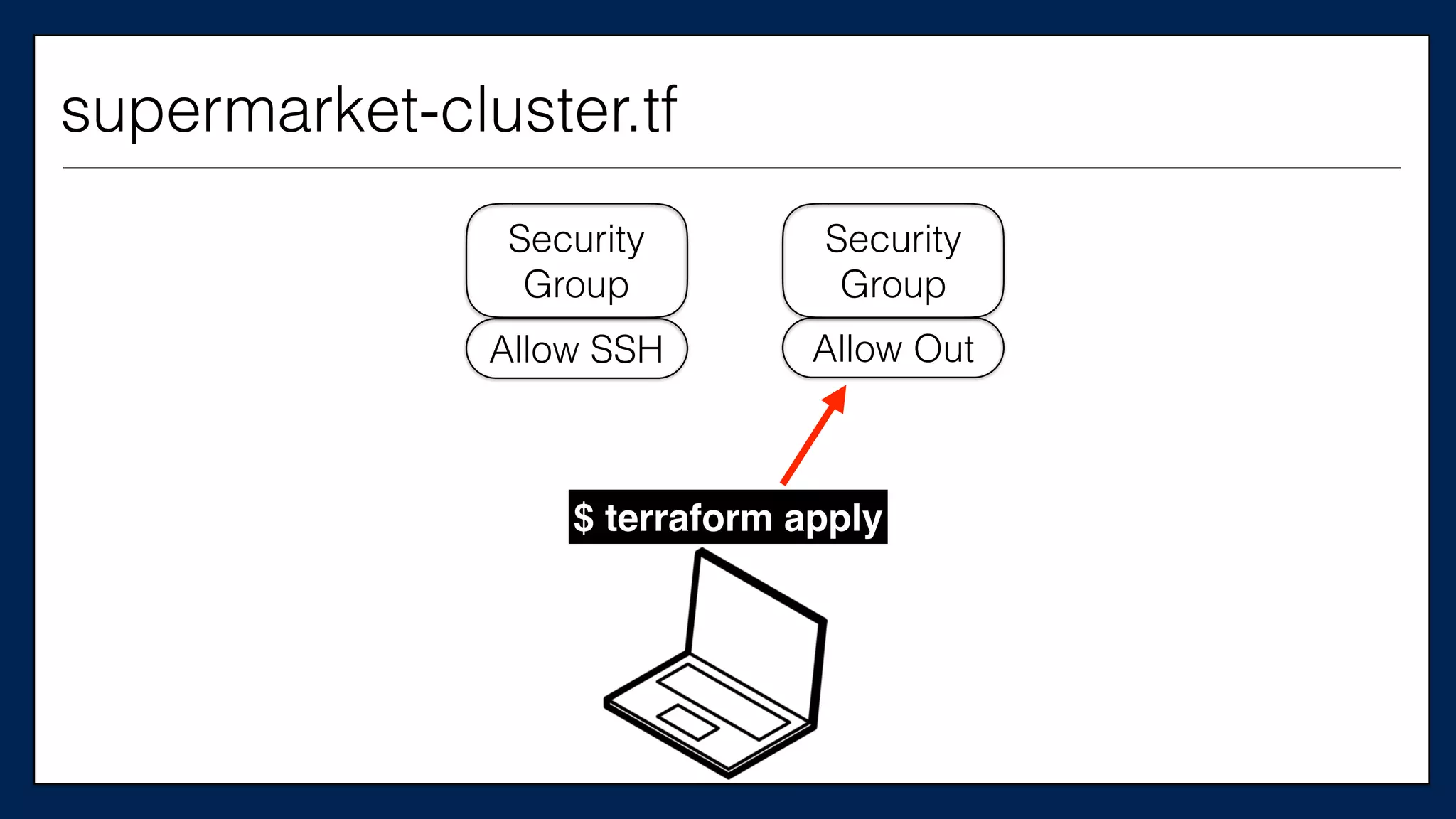
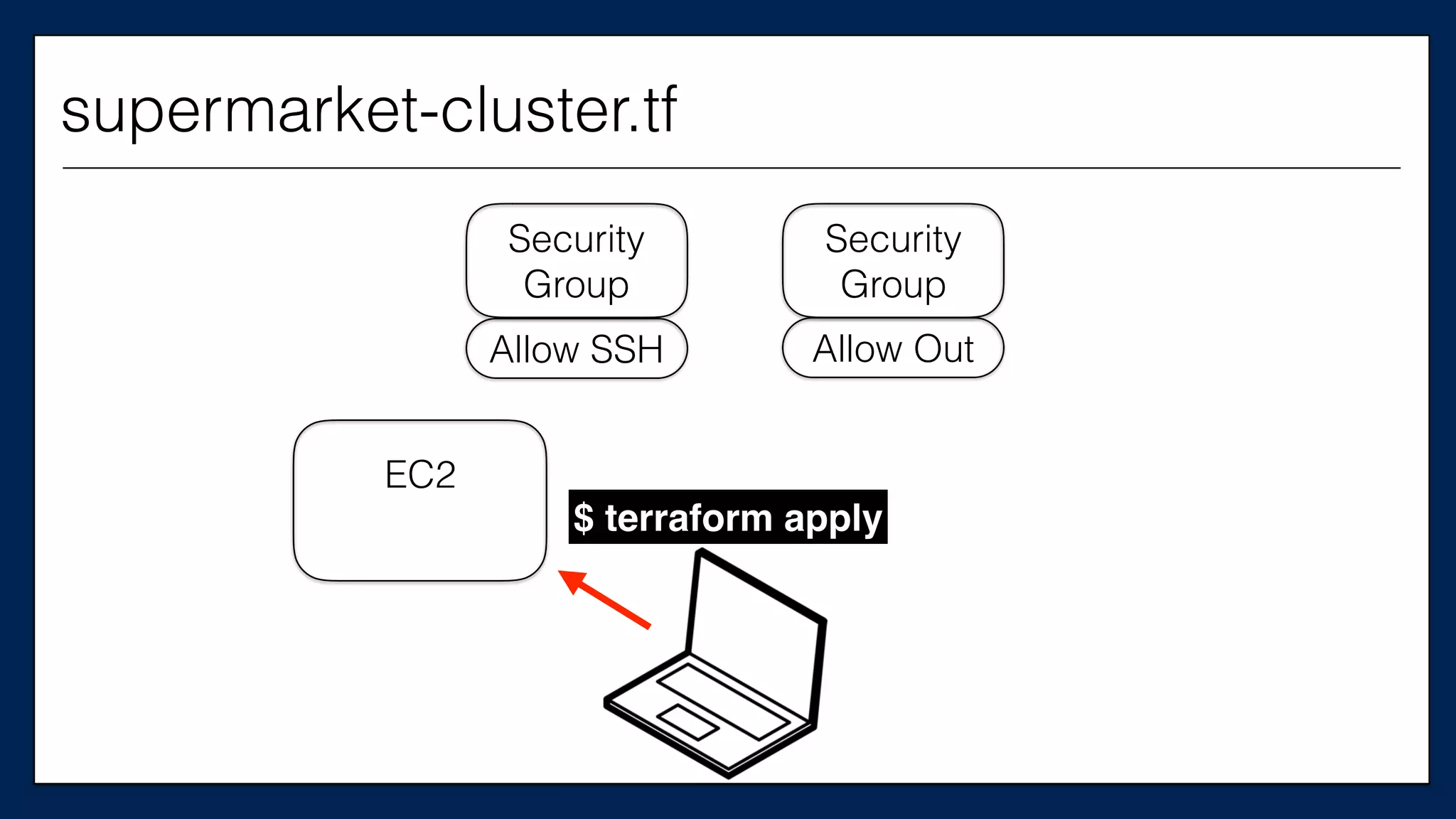











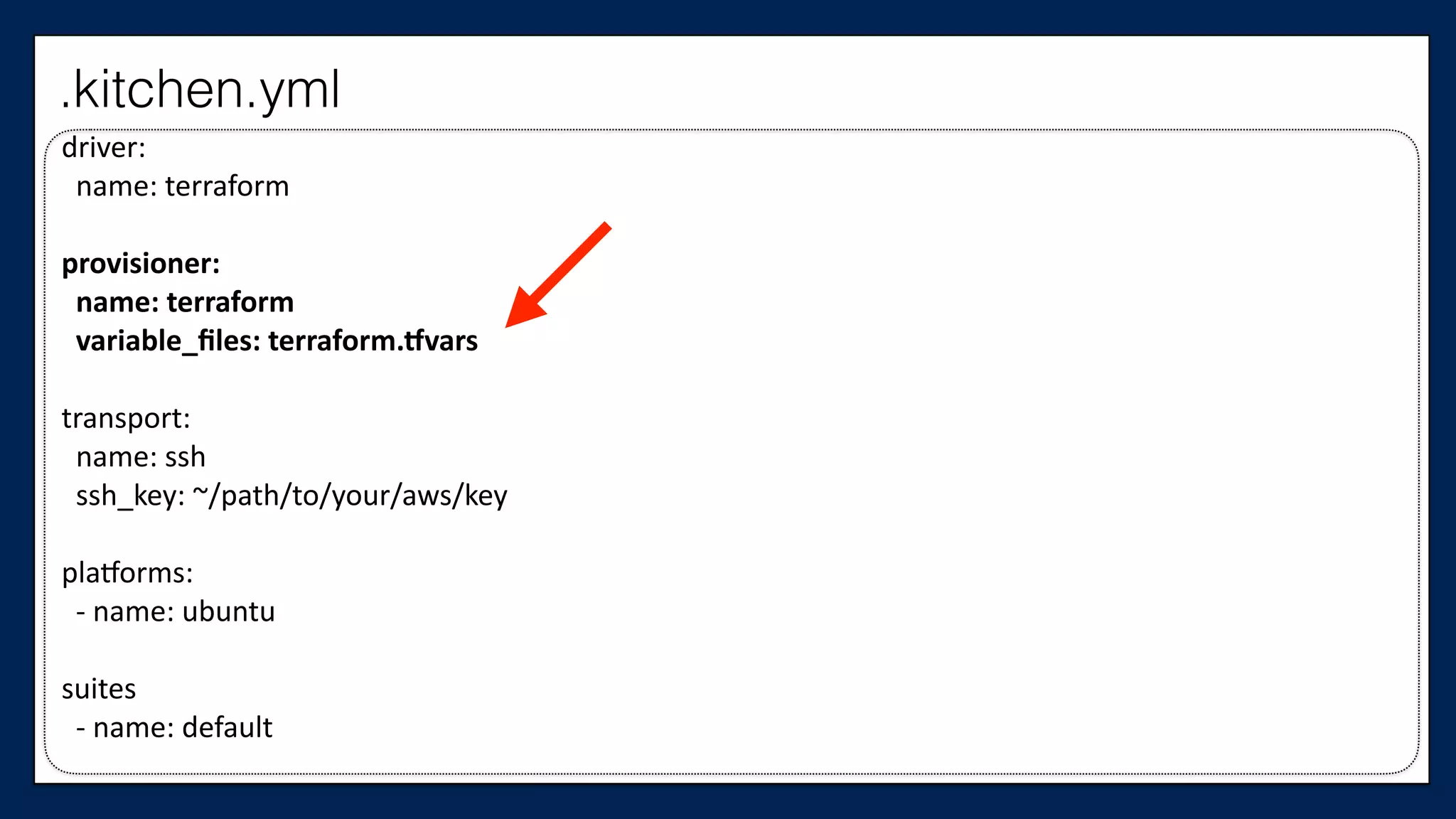
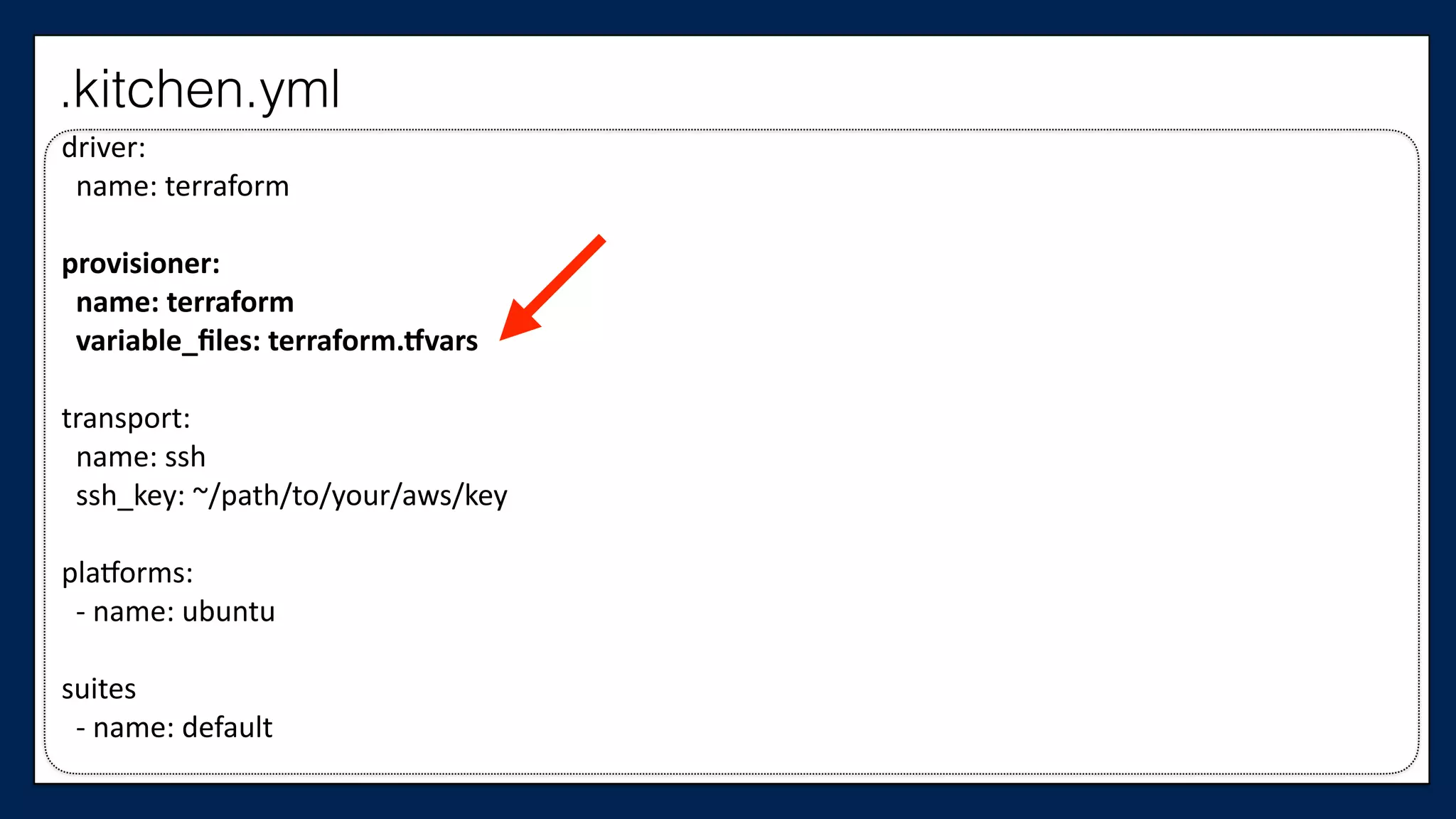
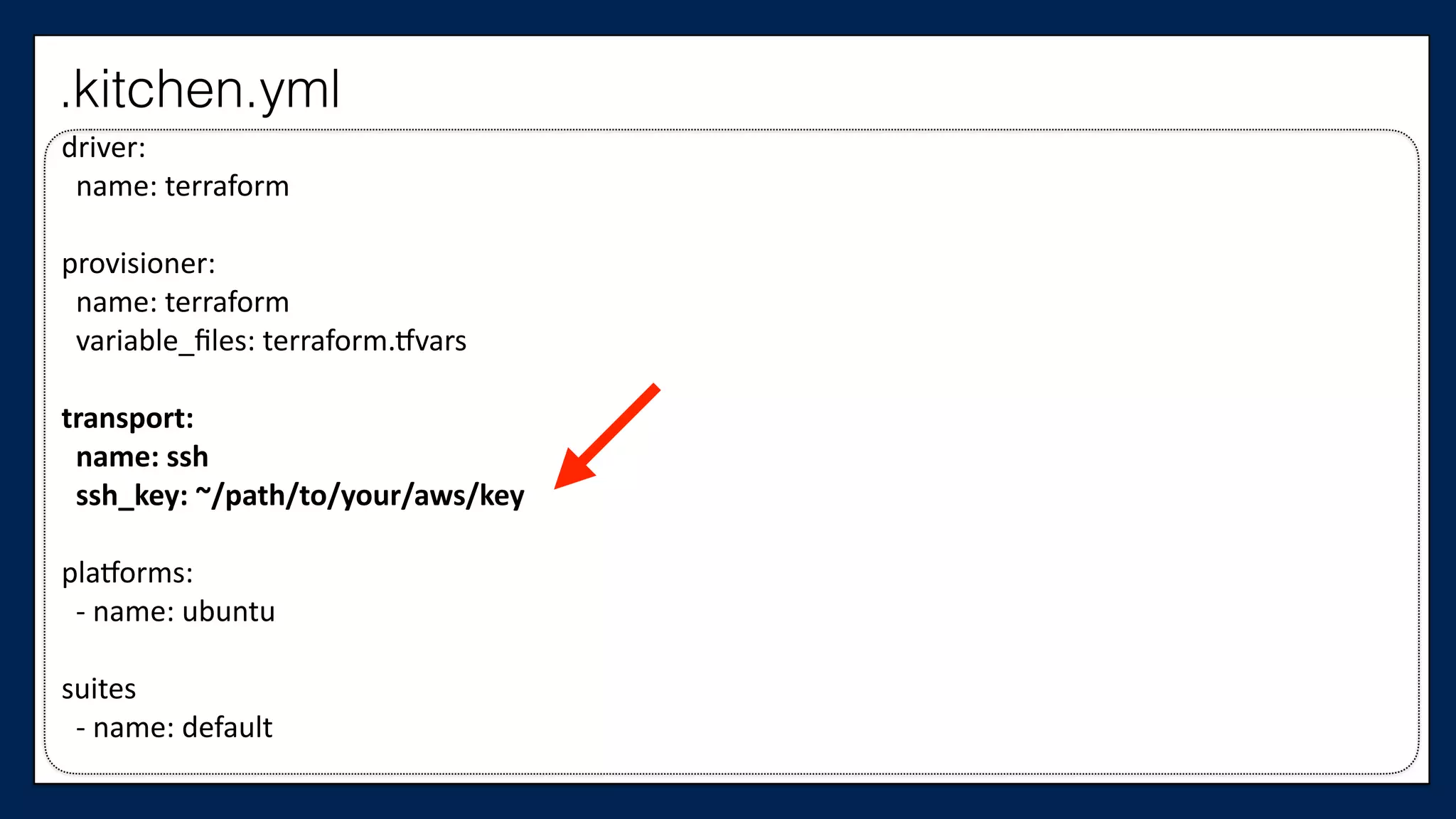
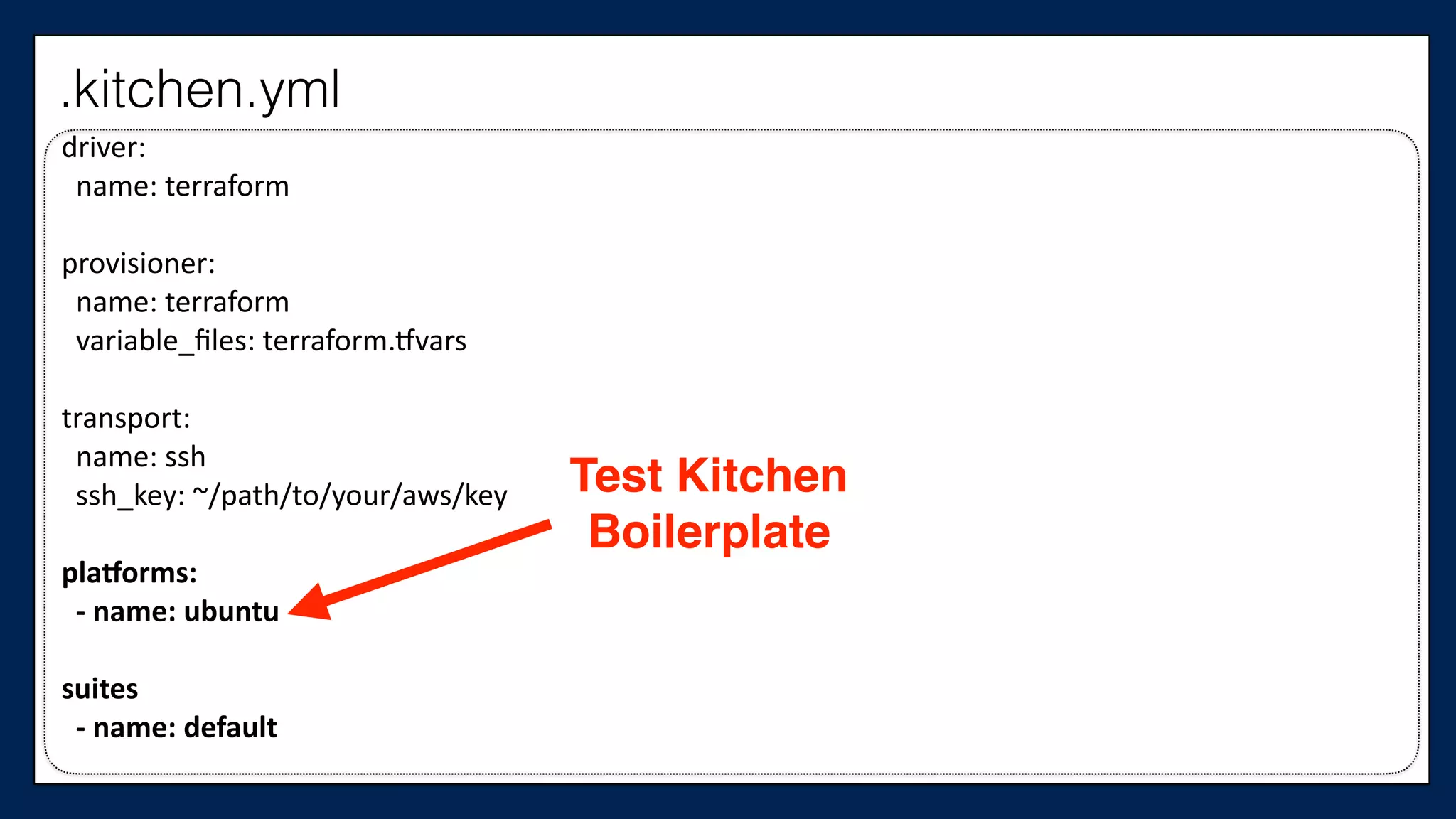



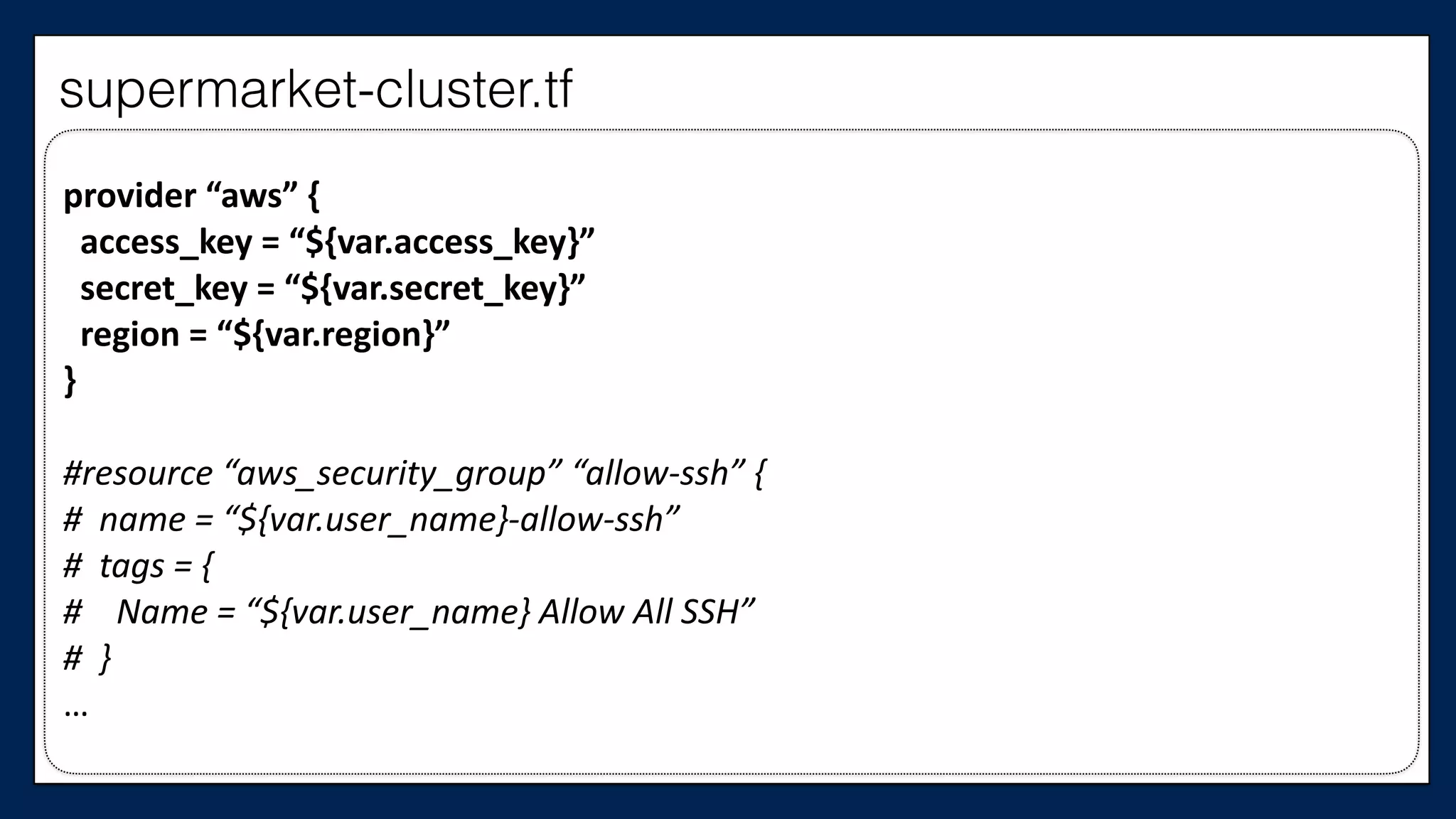


![…
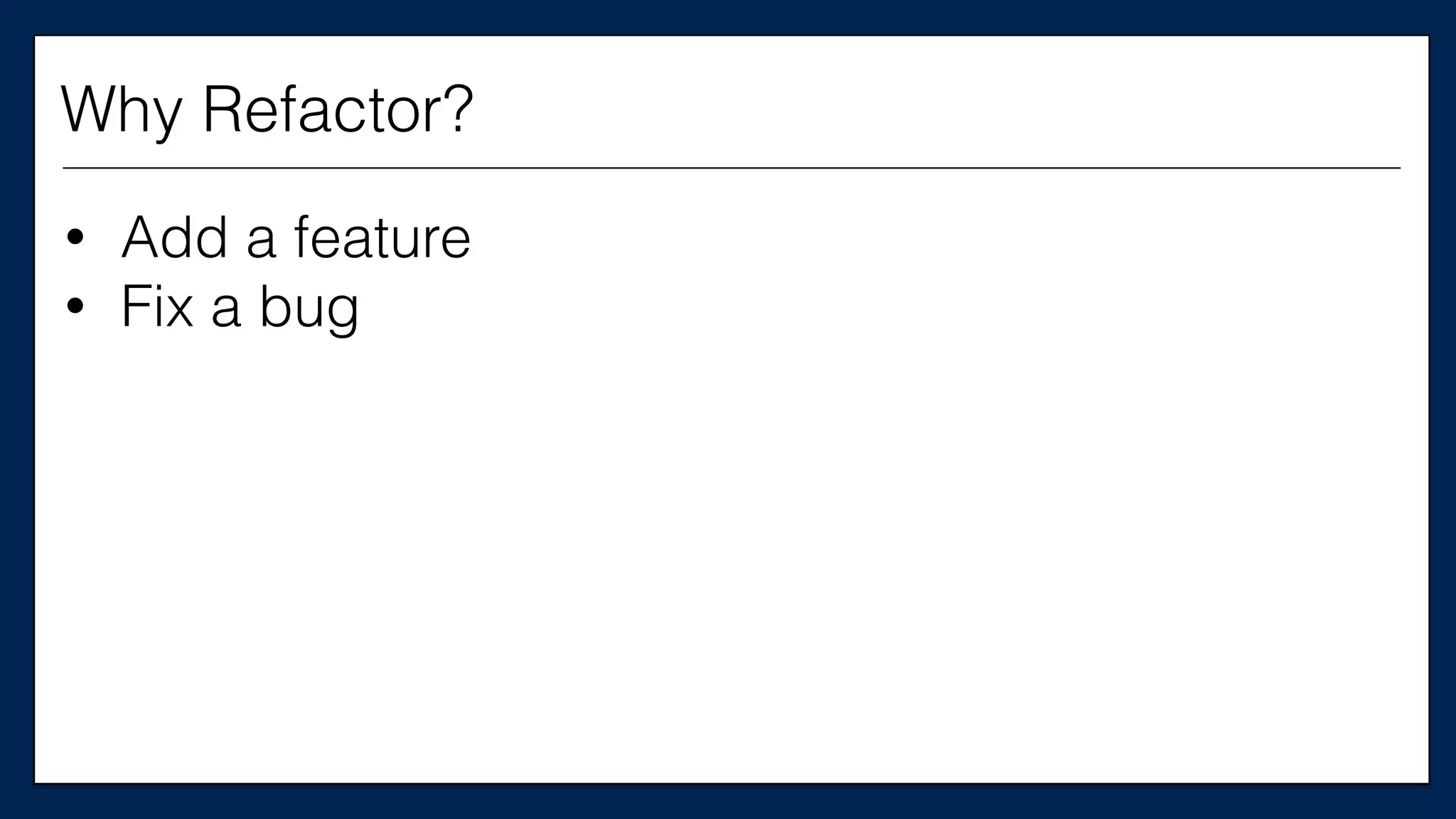
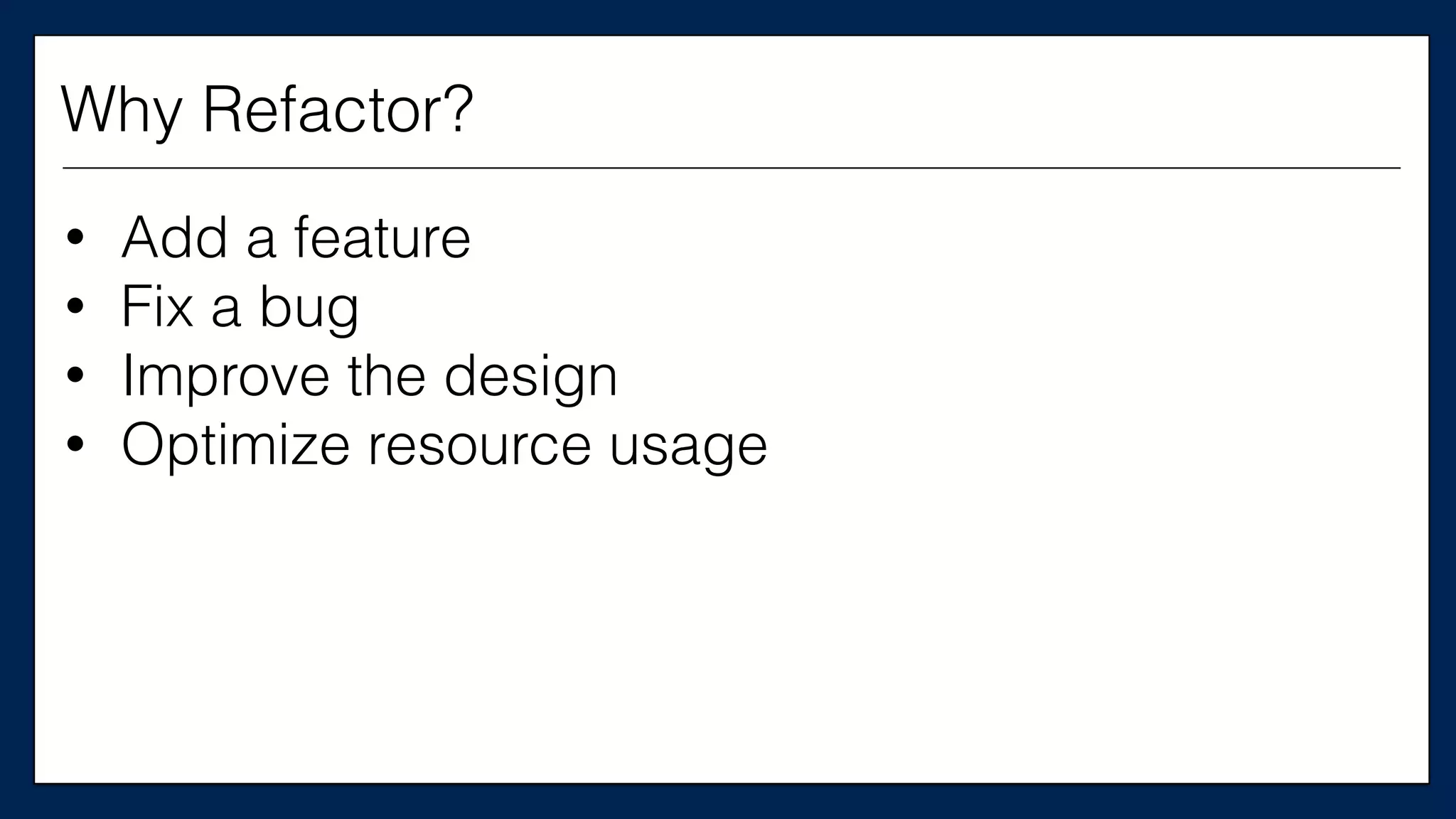
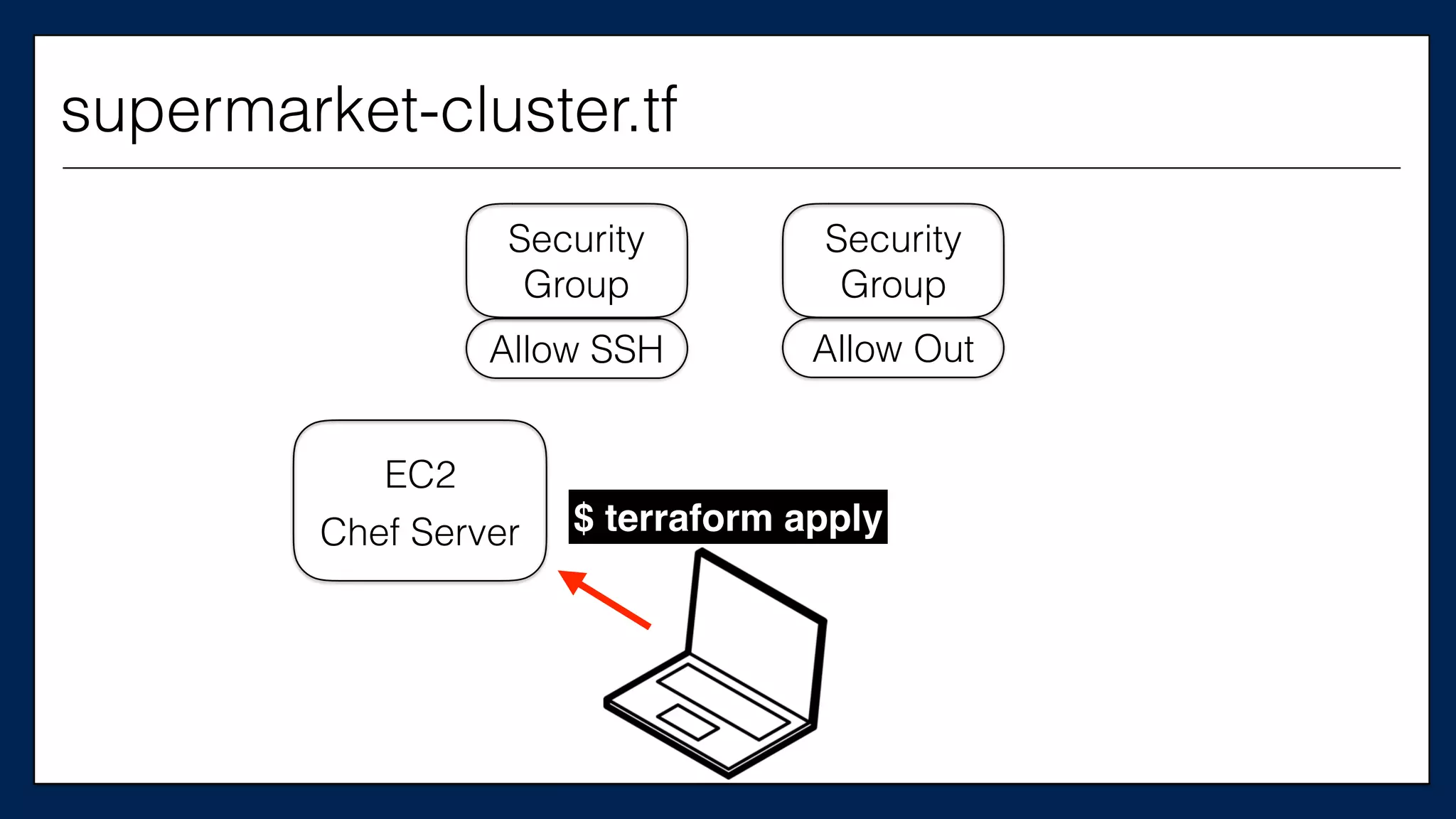
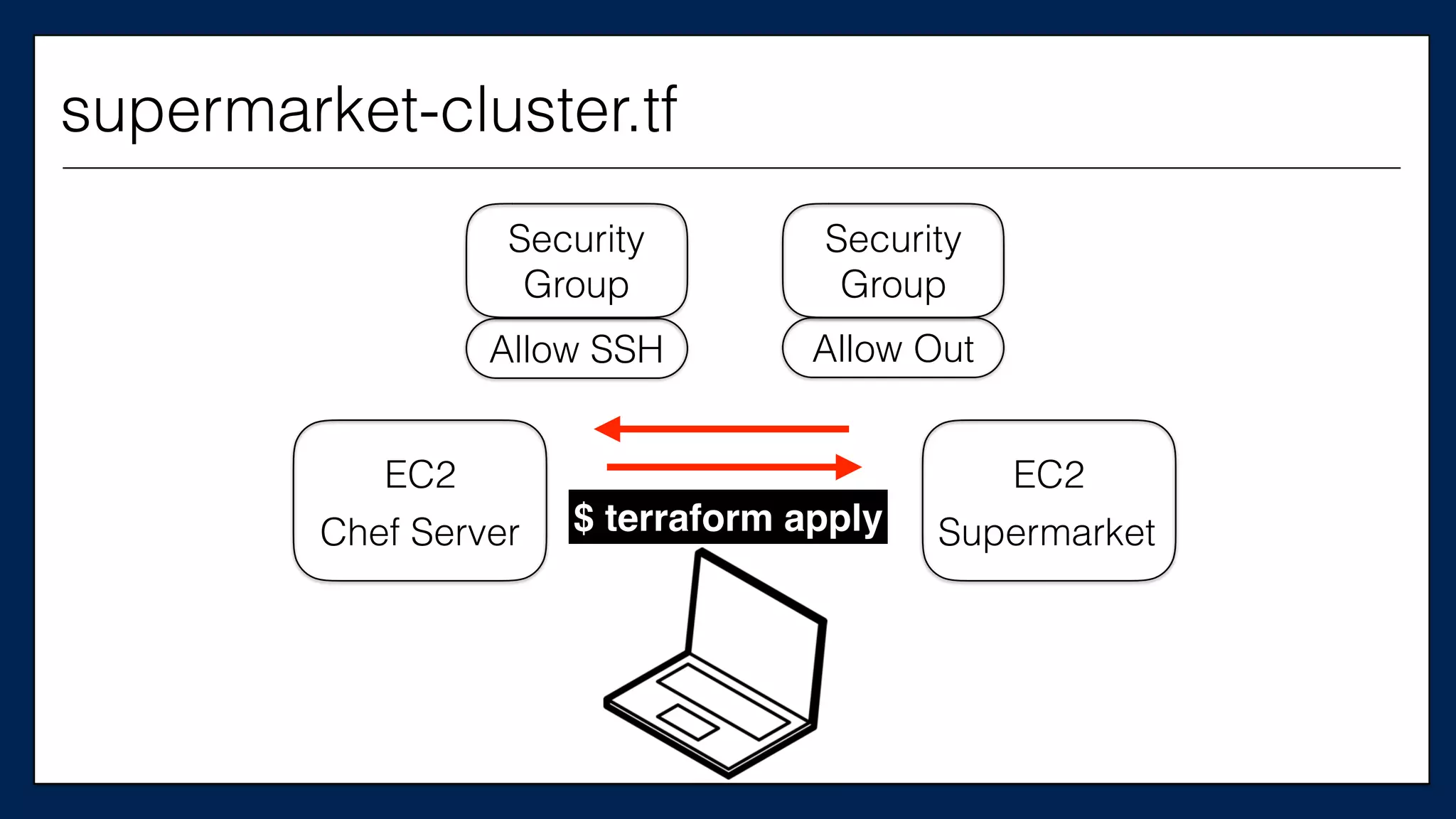
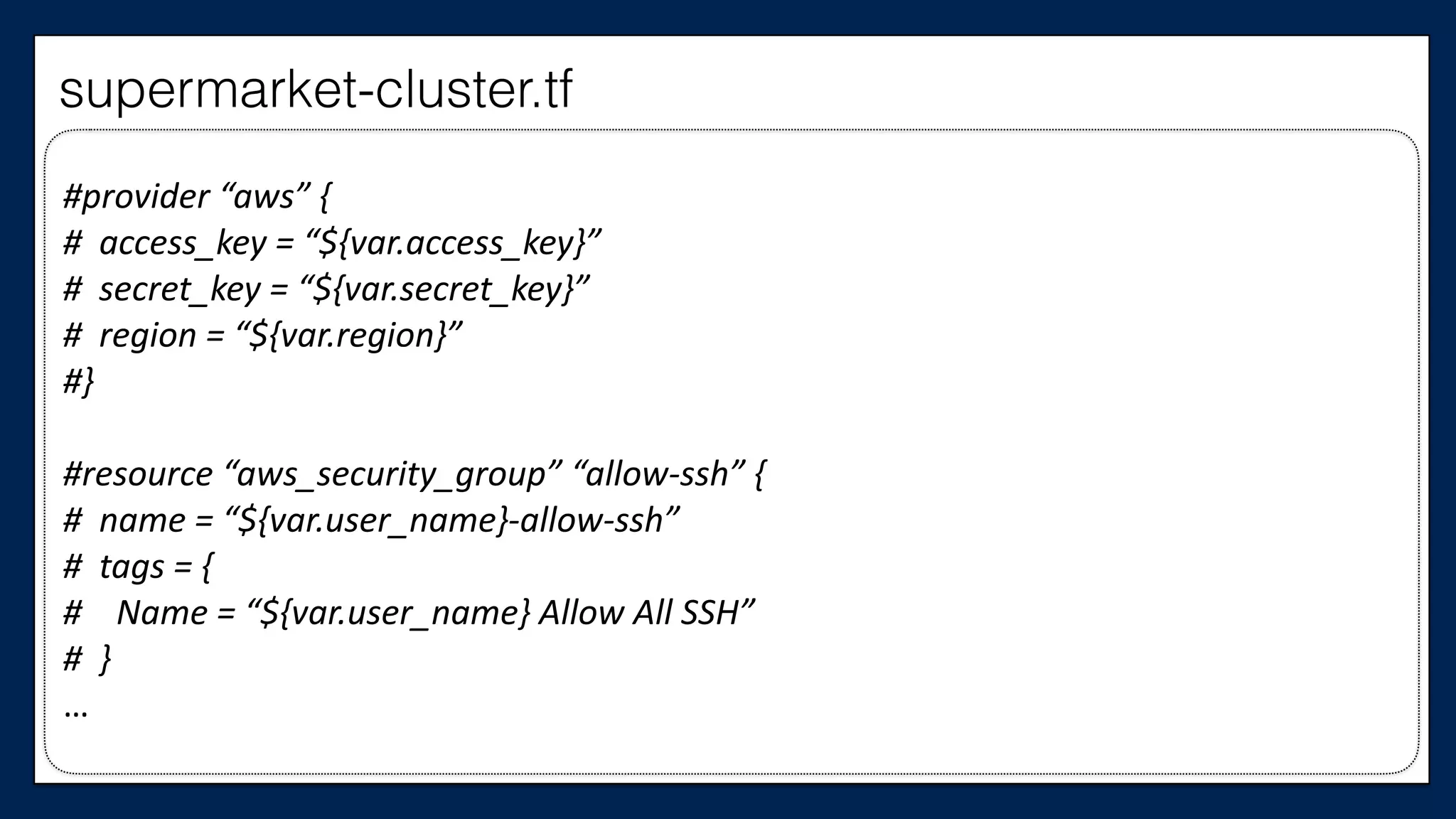
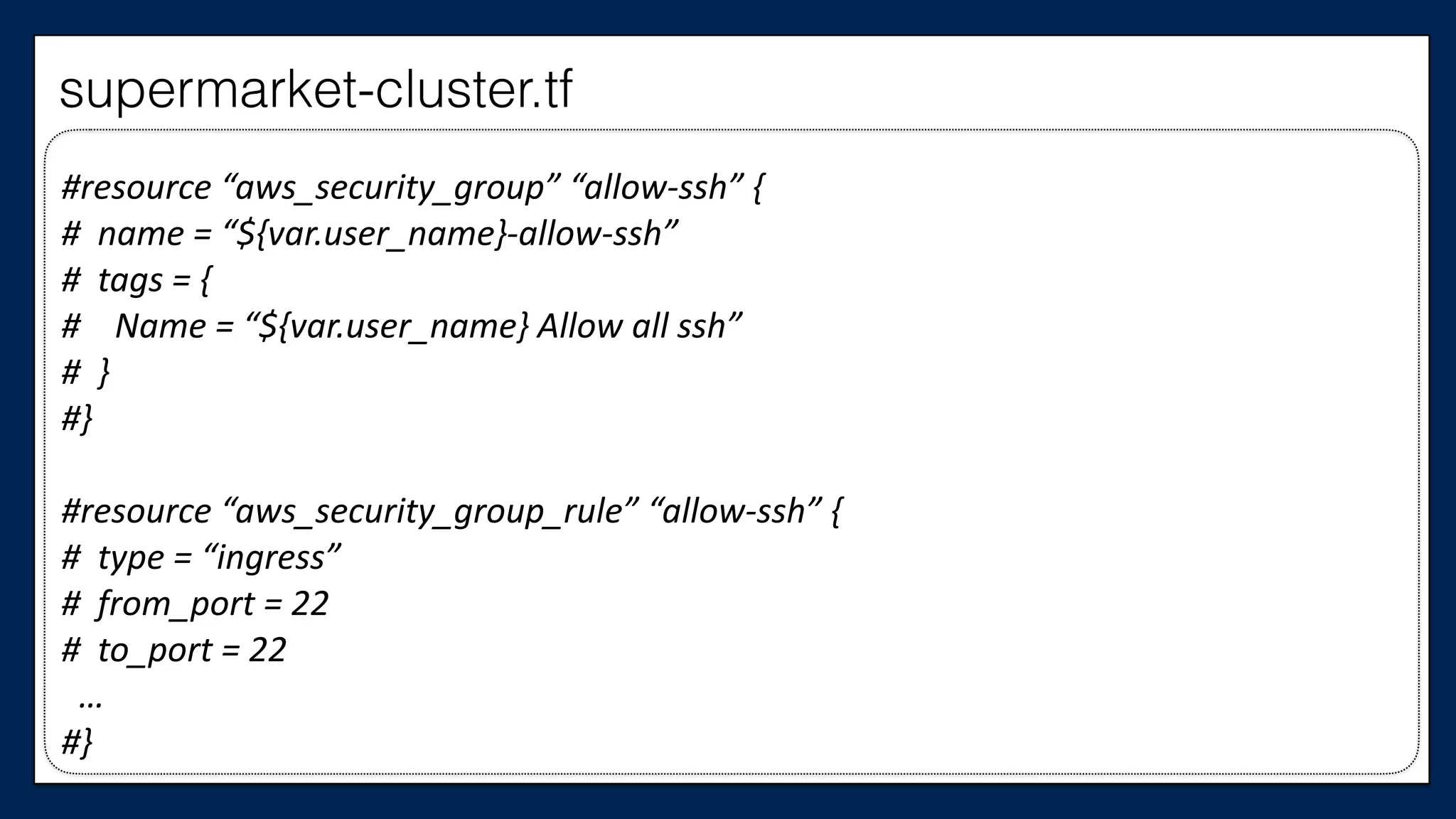
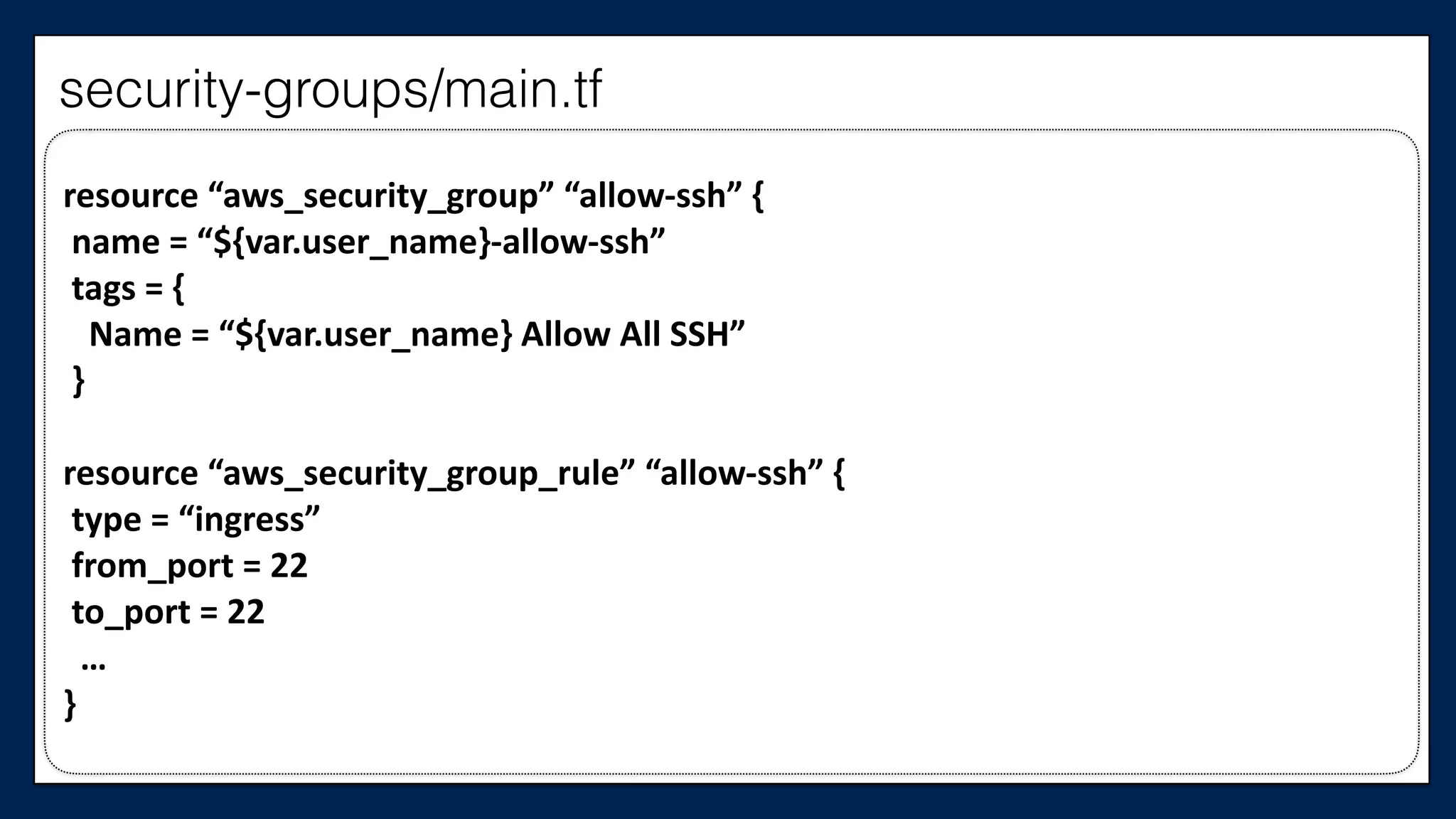
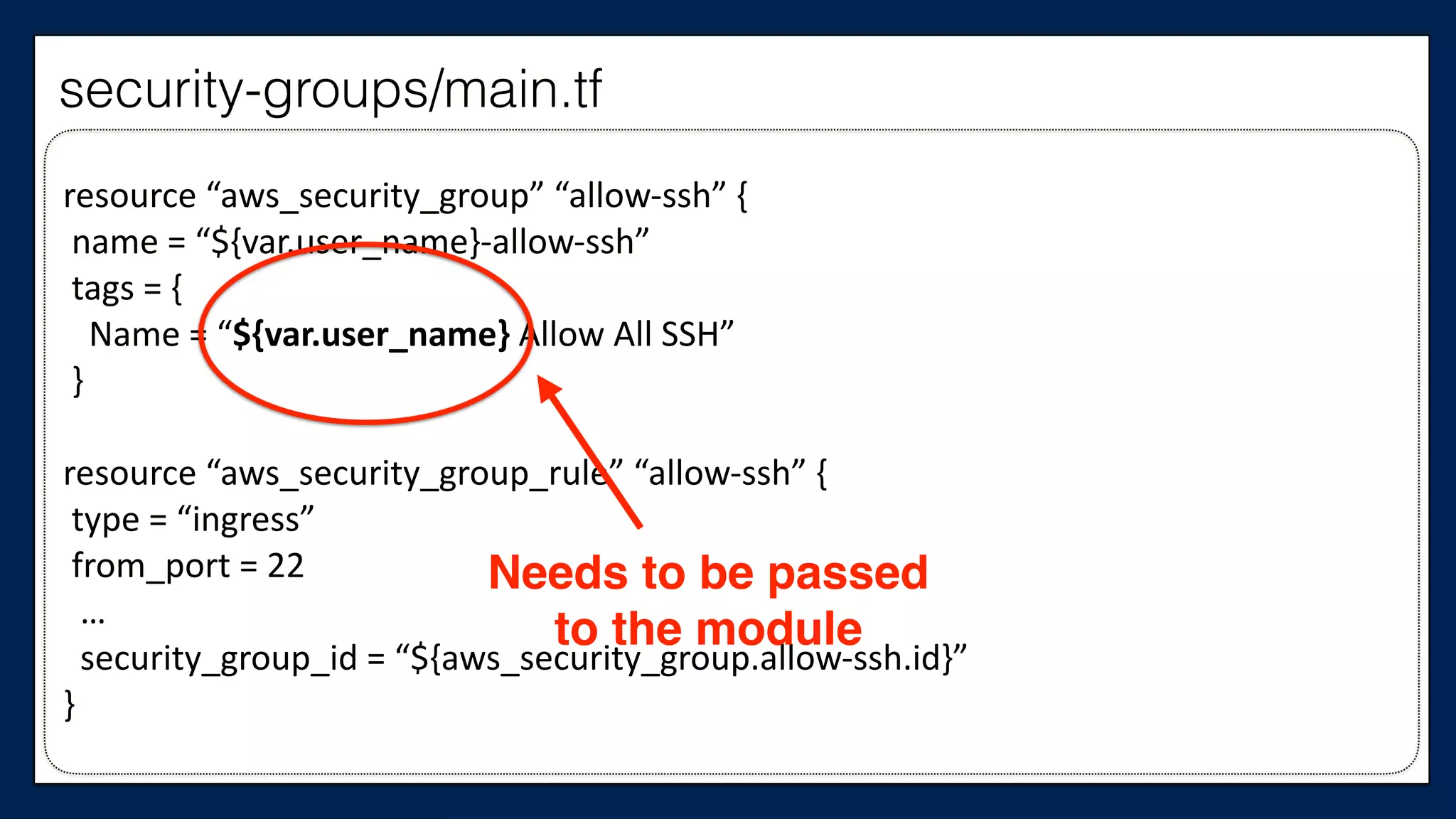
#resource
“aws_instance”
“chef_server”
{
#
ami
=
“${var.ami}”
#
instance_type
=
“${var.instance_type}”
#
key_name
=
“${var.key_name}”
#
tags
{
#
Name
=
“dev-‐chef-‐server”
#
}
#
security_groups
=
[“${aws_security_group.allow-‐ssh.name}”,
#
“${aws_security_group.allow-‐out.name}”]
#
(…)
#}
…
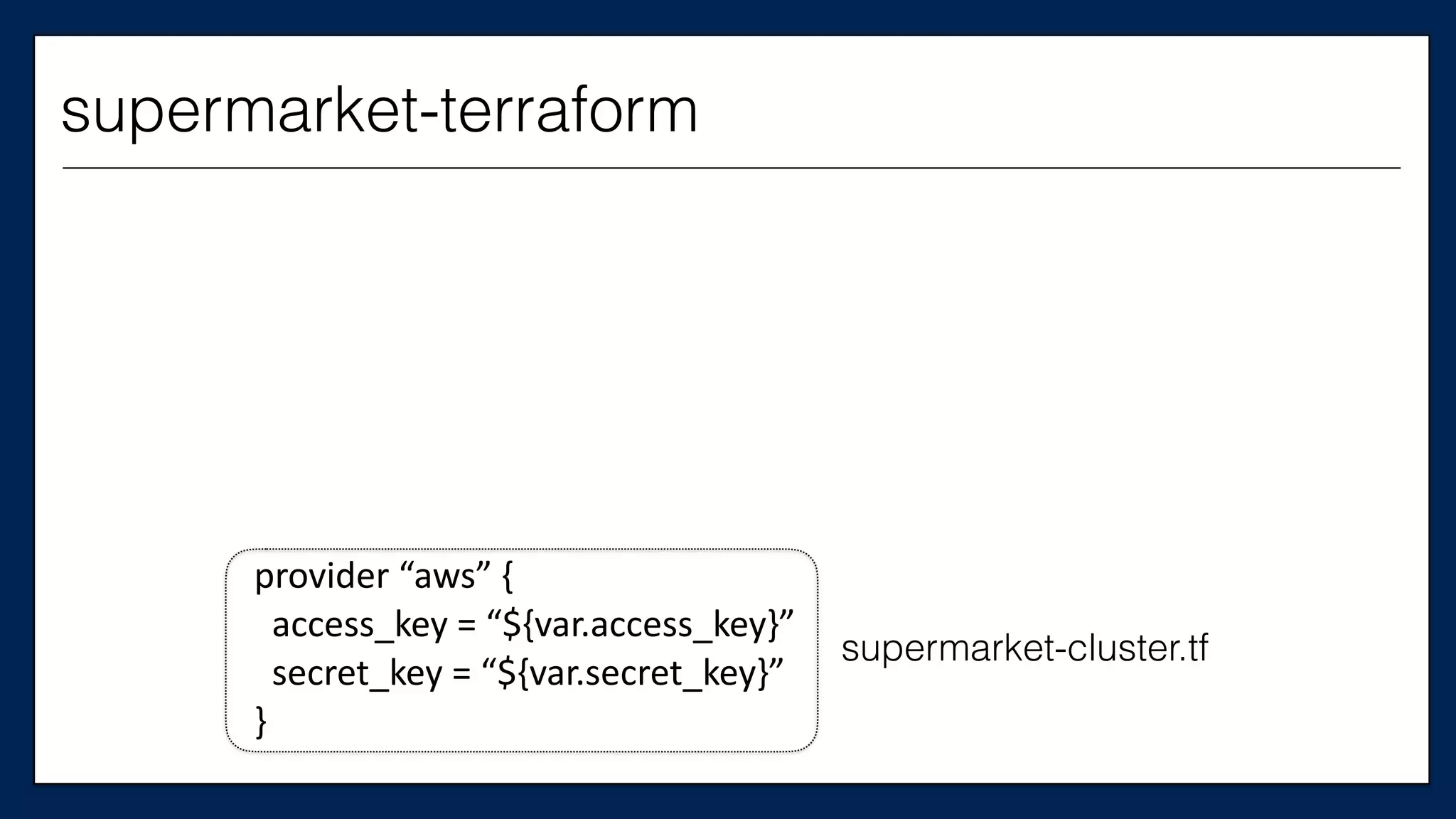
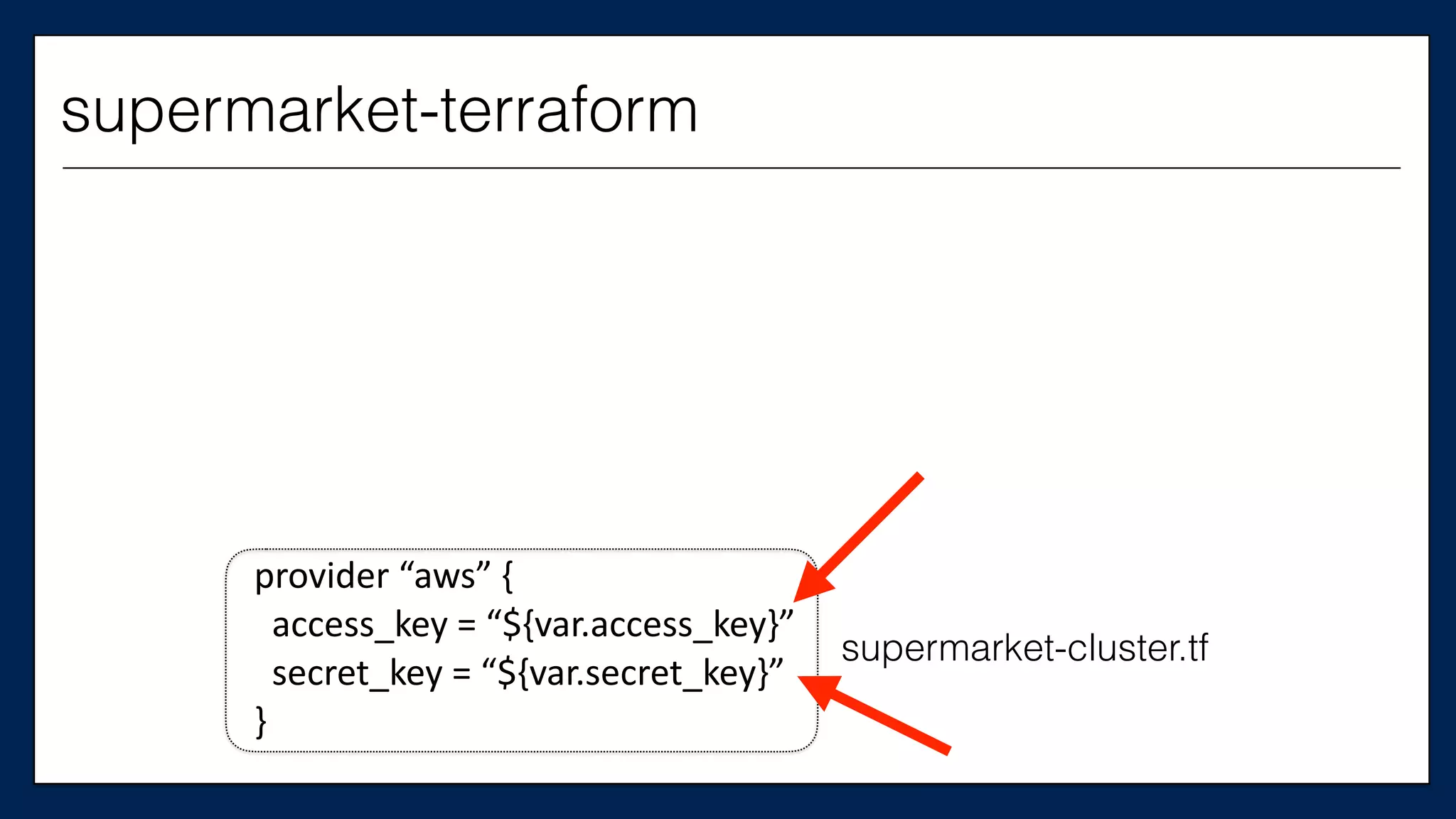
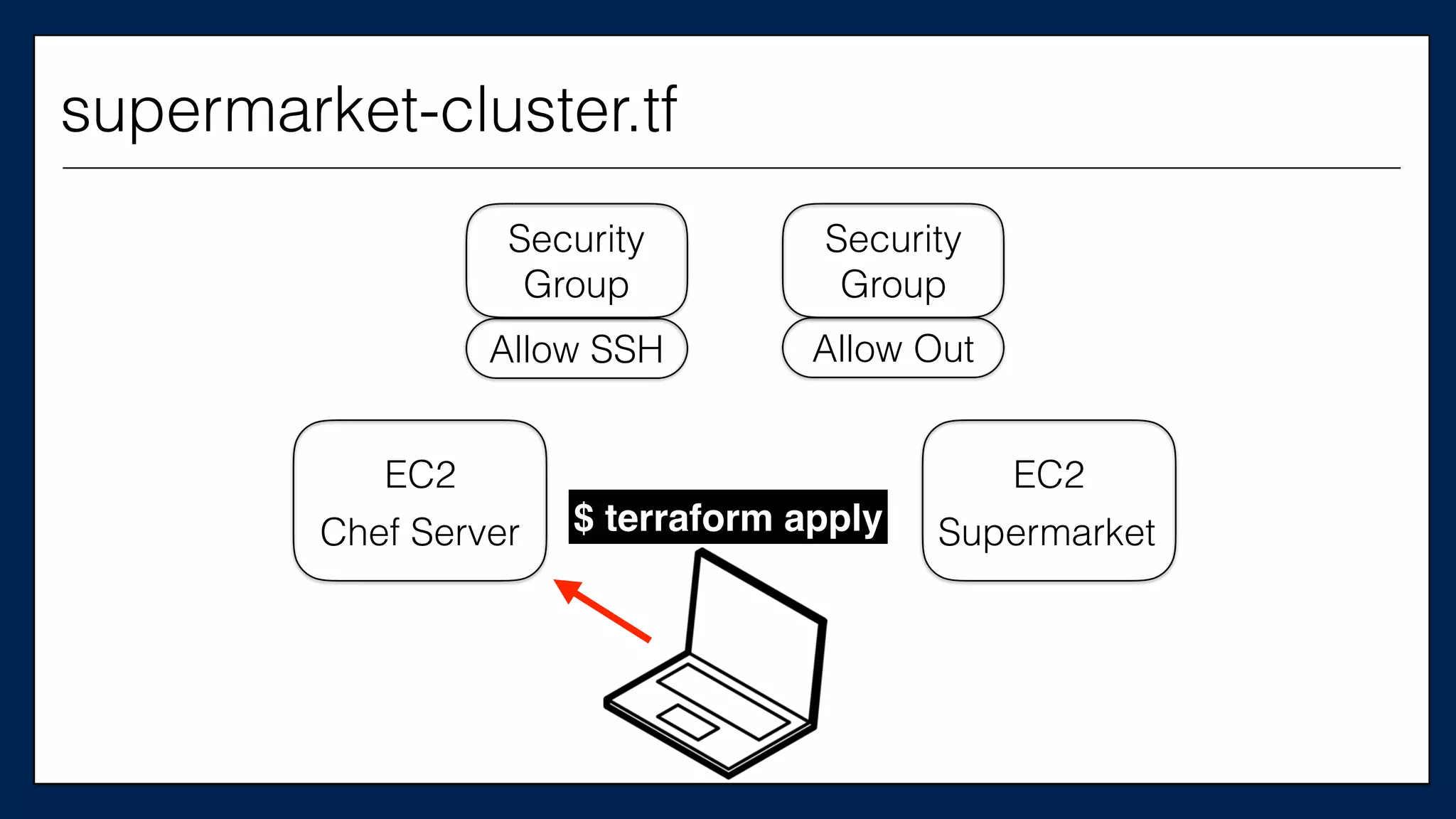
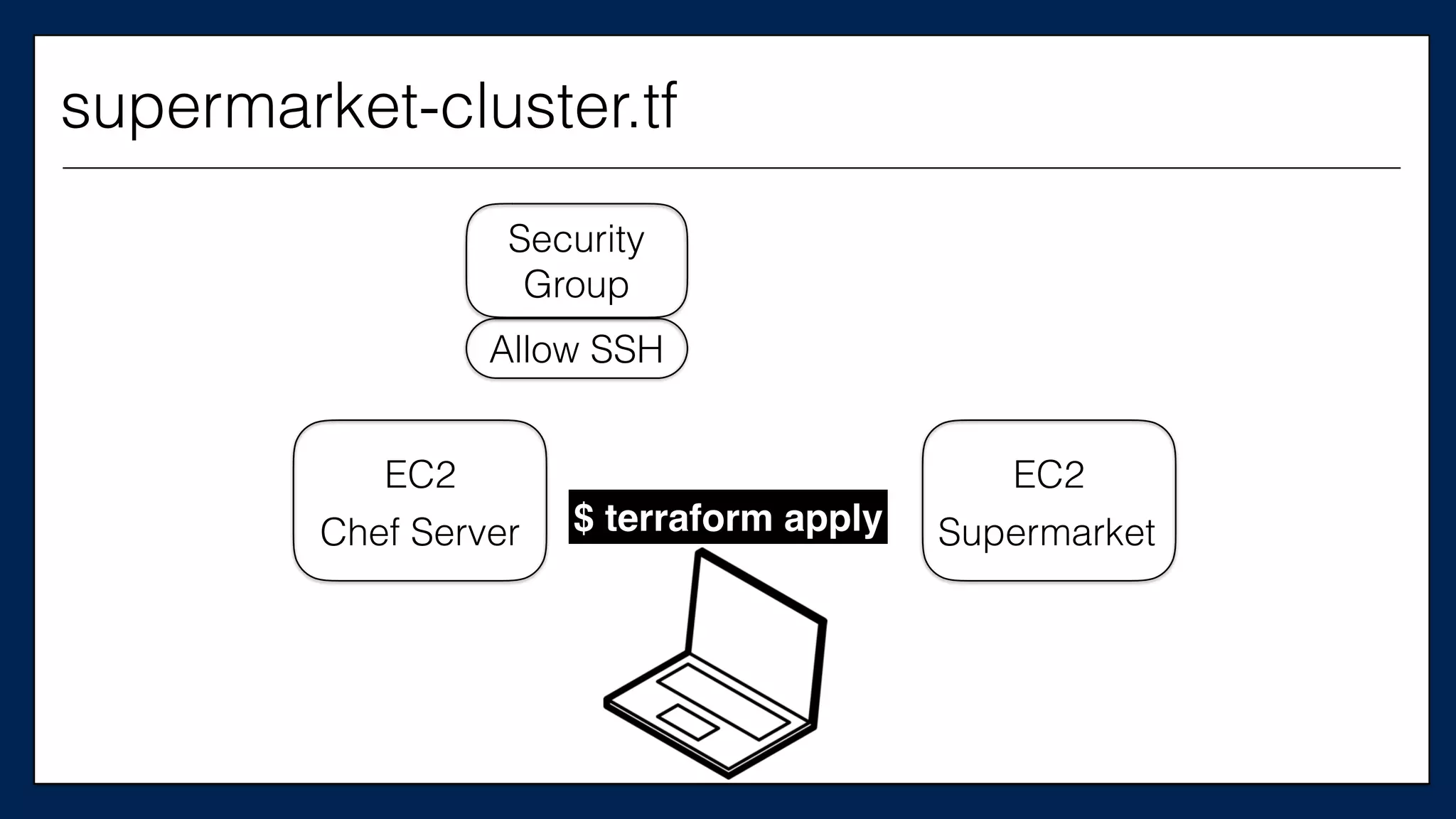
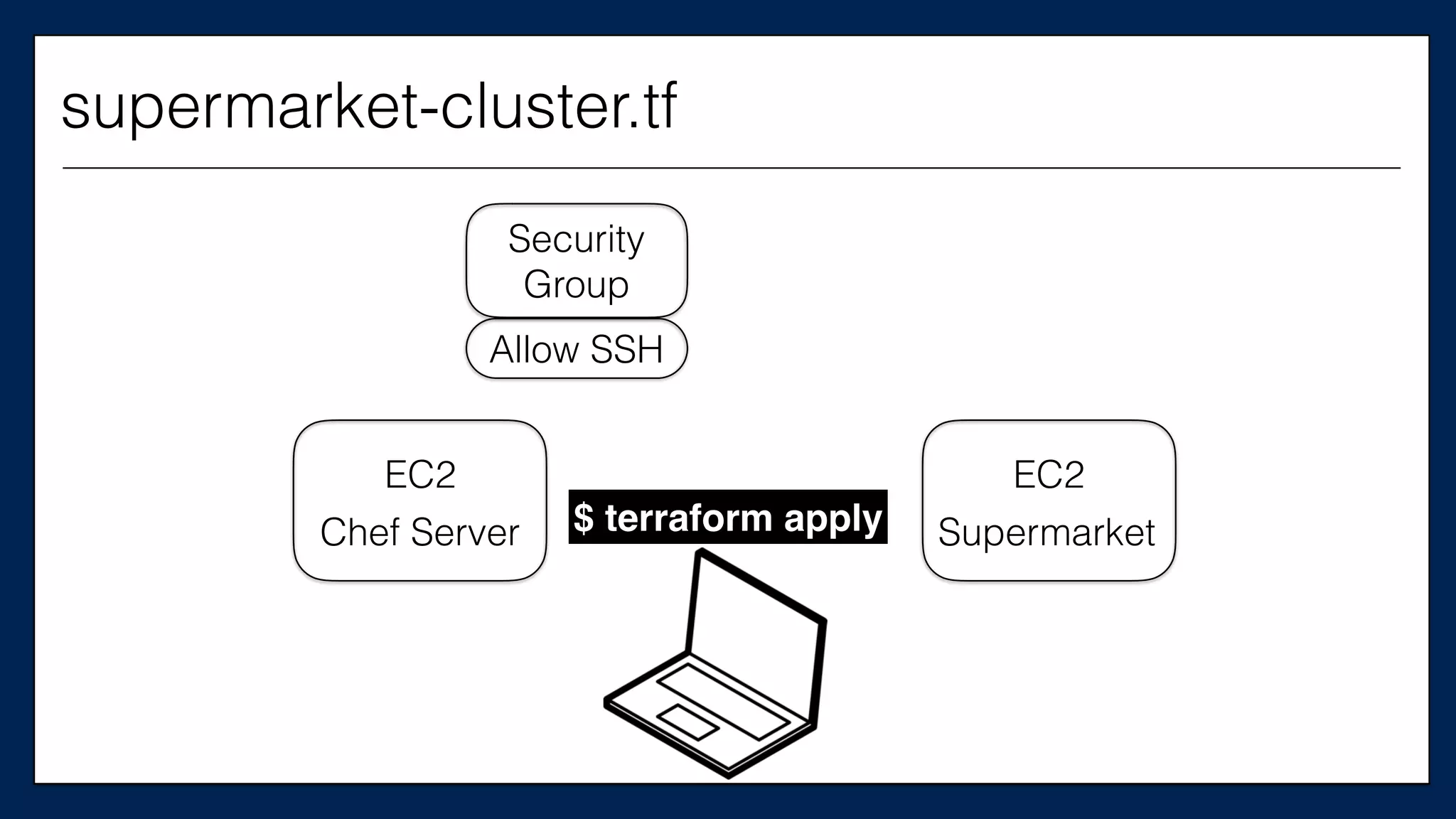
This is the
Chef Server
supermarket-cluster.tf](https://image.slidesharecdn.com/refactoringinfradevopsdayschidraft3-160831163013/75/Refactoring-Infrastructure-Code-61-2048.jpg)
![…
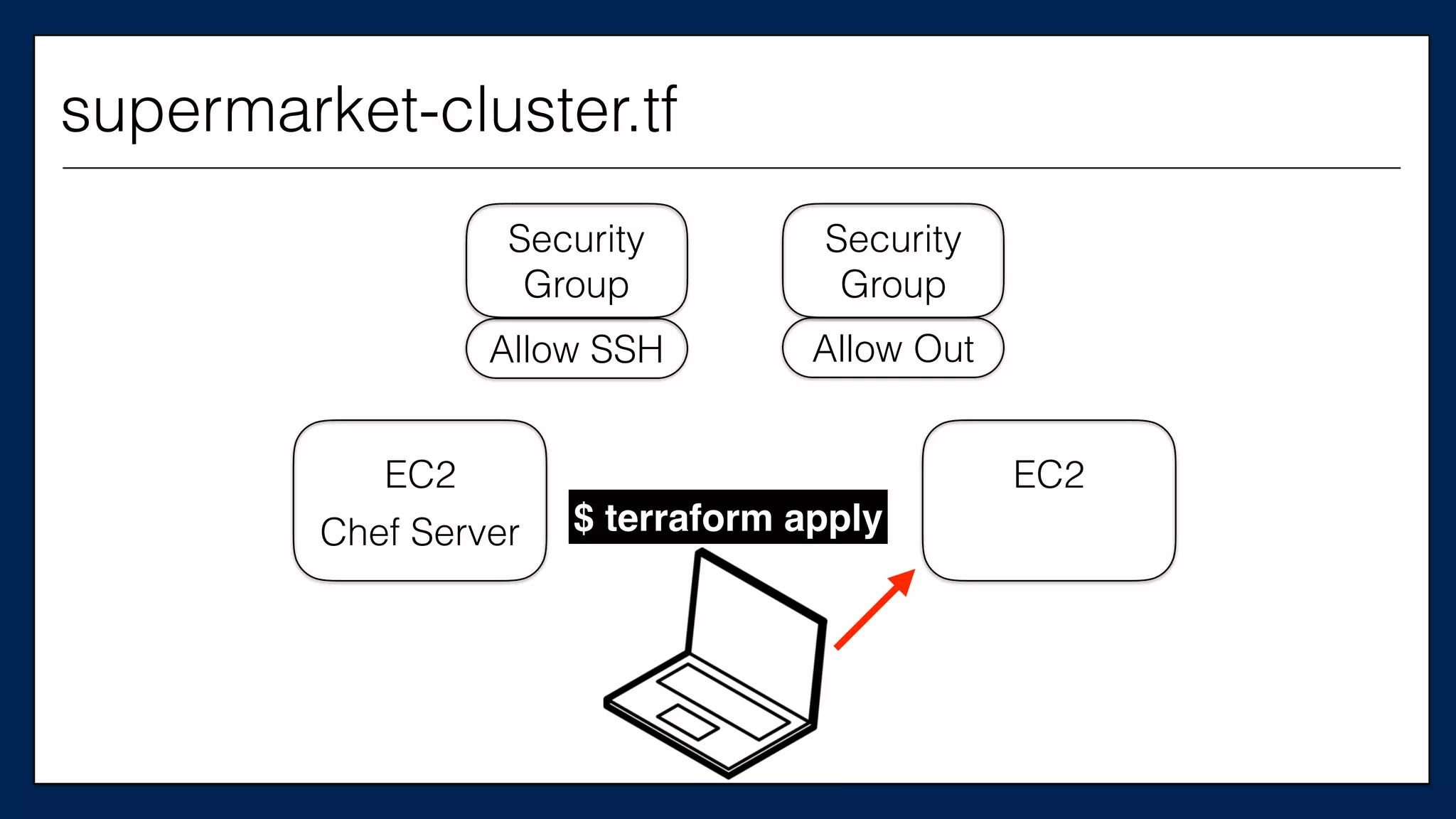
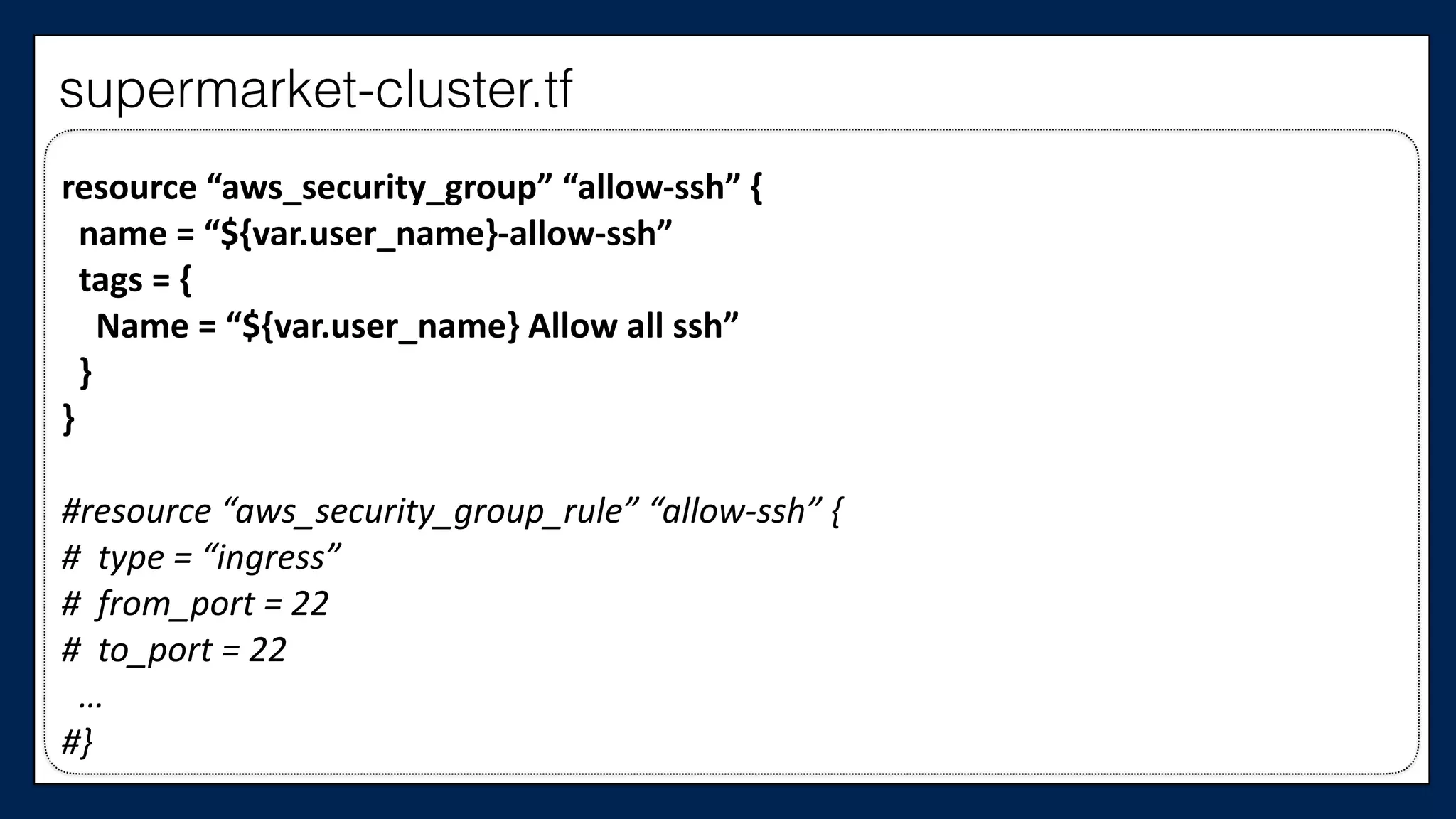
resource
“aws_instance”
“chef_server”
{
ami
=
“${var.ami}”
instance_type
=
“${var.instance_type}”
key_name
=
“${var.key_name}”
tags
{
Name
=
“dev-‐chef-‐server”
}
security_groups
=
[“${aws_security_group.allow-‐ssh.name}”,
“${aws_security_group.allow-‐out.name}”]
(…)
}
…
This is the
Chef Server
supermarket-cluster.tf](https://image.slidesharecdn.com/refactoringinfradevopsdayschidraft3-160831163013/75/Refactoring-Infrastructure-Code-62-2048.jpg)

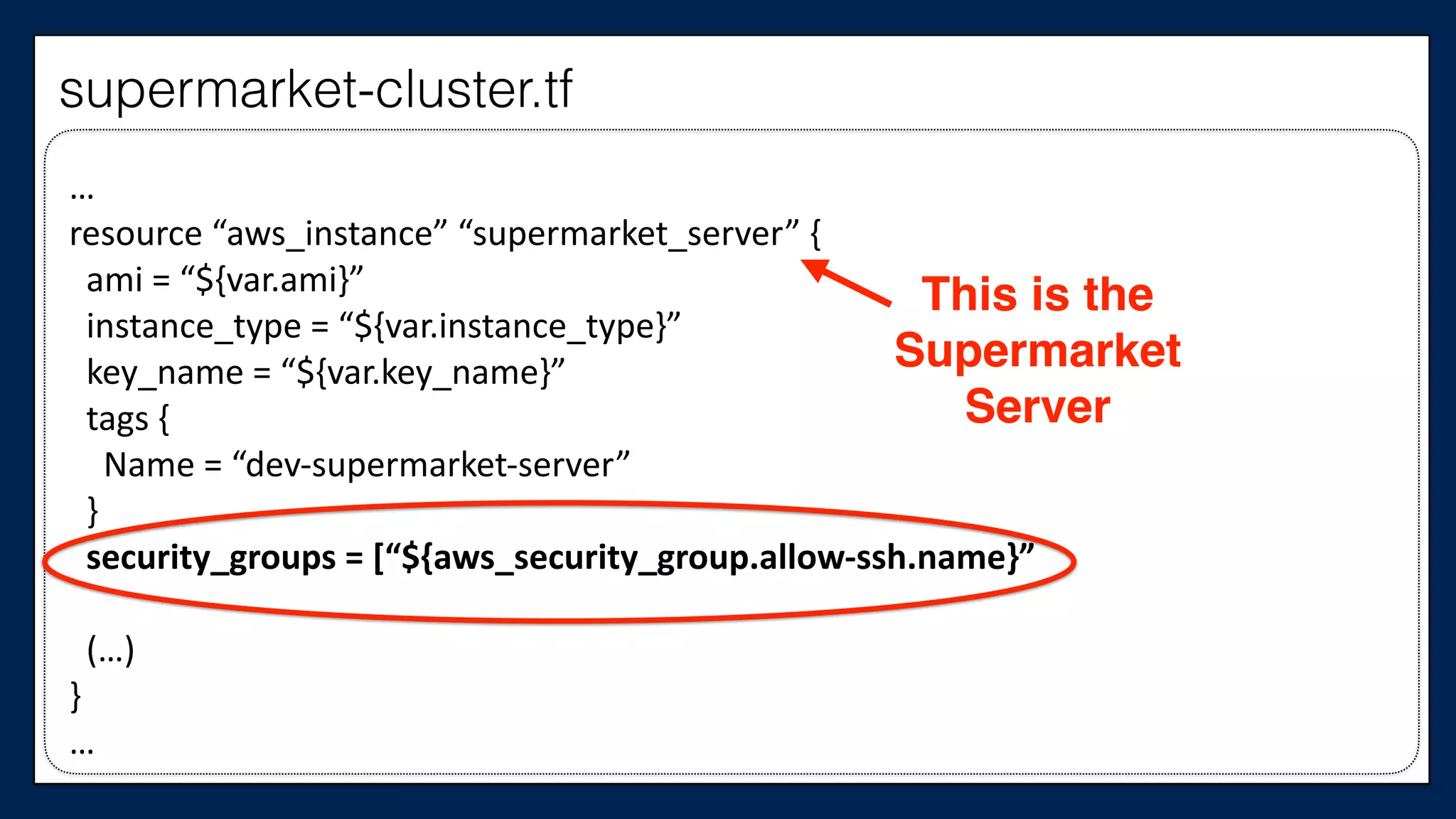
![…
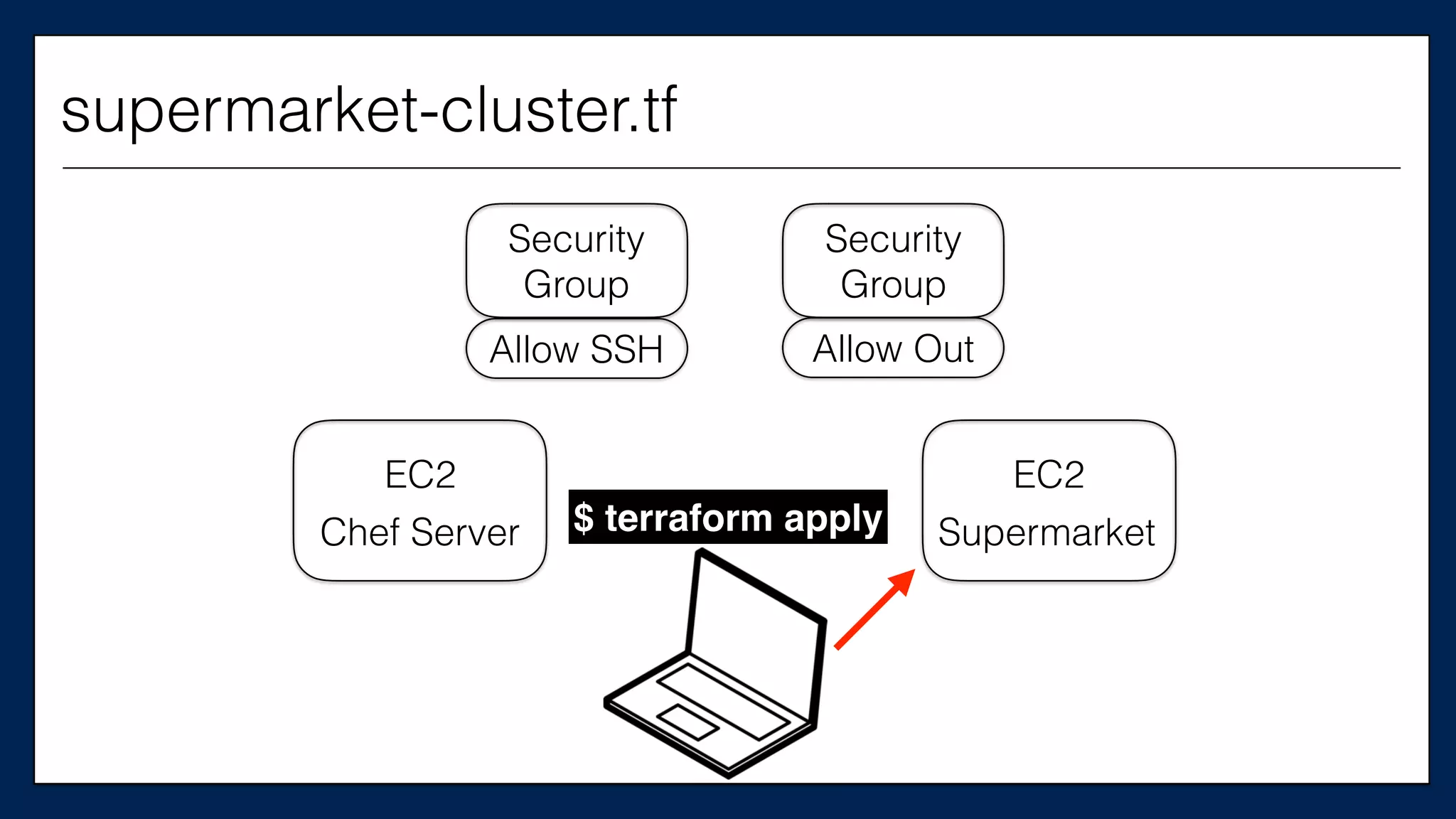
#resource
“aws_instance”
“supermarket_server”
{
#
ami
=
“${var.ami}”
#
instance_type
=
“${var.instance_type}”
#
key_name
=
“${var.key_name}”
#
tags
{
#
Name
=
“dev-‐supermarket-‐server”
#
}
#
security_groups
=
[“${aws_security_group.allow-‐ssh.name}”,
#
“${aws_security_group.allow-‐out.name}”]
#
(…)
#}
…
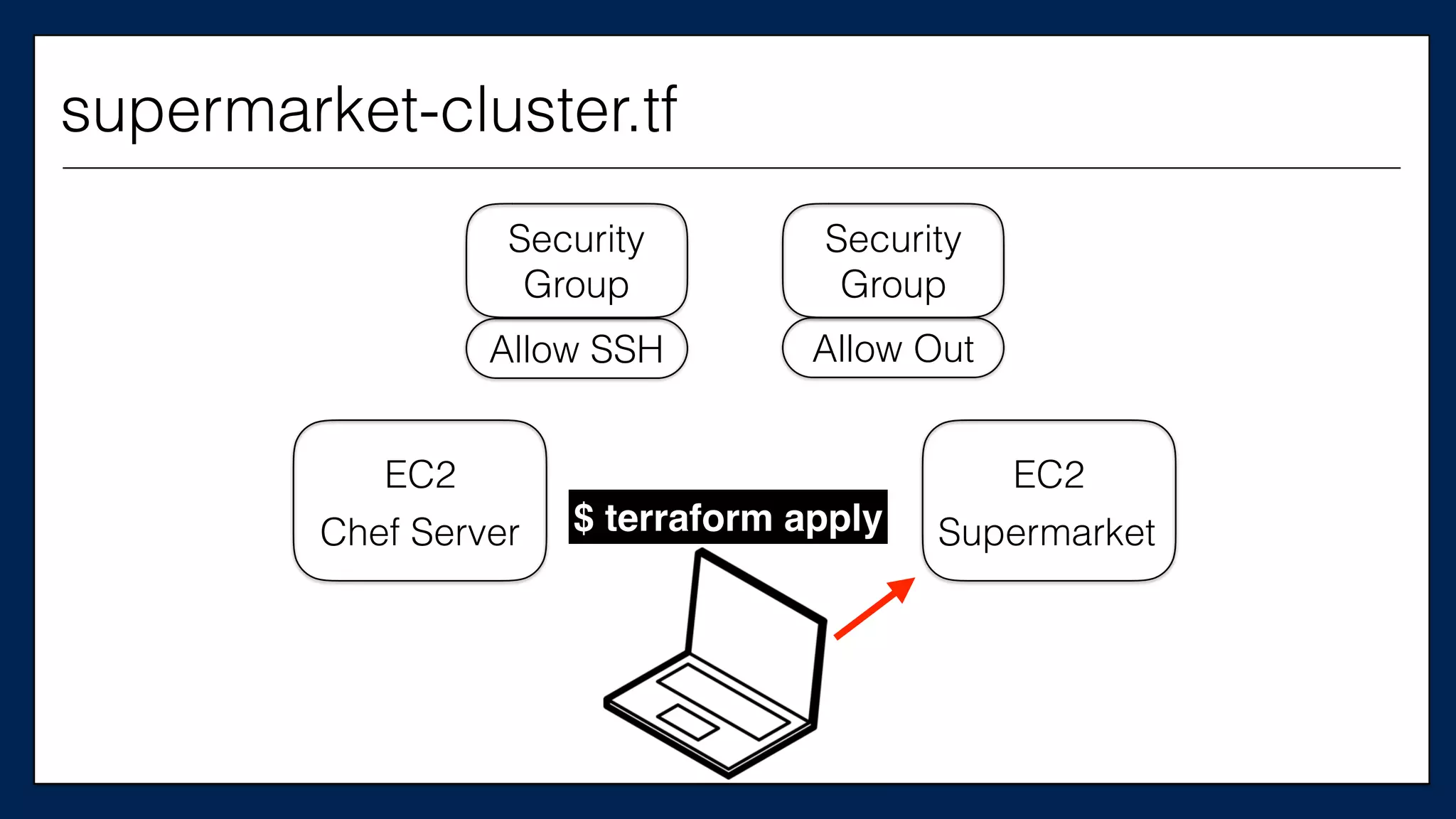
This is the
Supermarket
Server
supermarket-cluster.tf](https://image.slidesharecdn.com/refactoringinfradevopsdayschidraft3-160831163013/75/Refactoring-Infrastructure-Code-66-2048.jpg)
![…
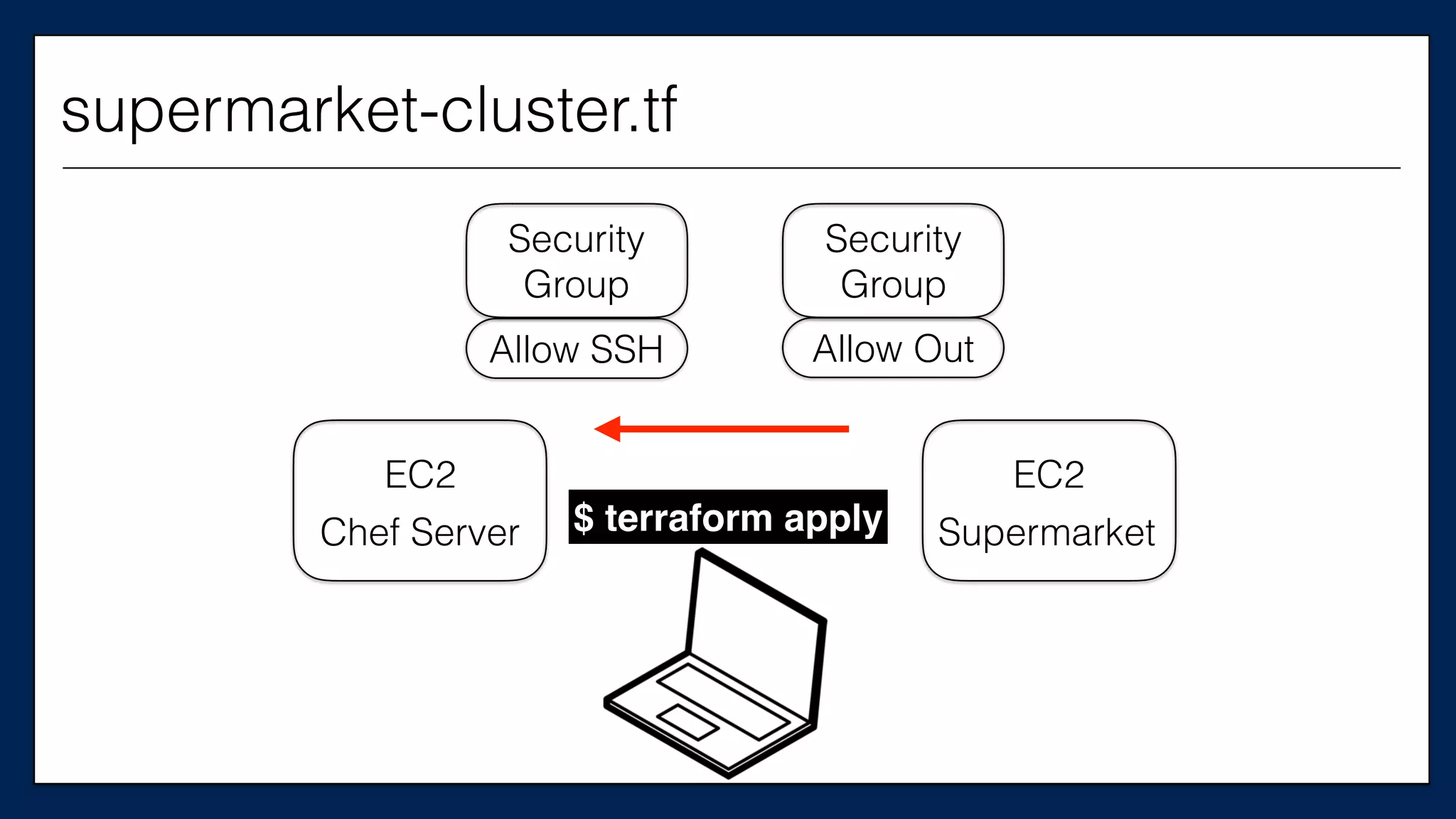
resource
“aws_instance”
“supermarket_server”
{
ami
=
“${var.ami}”
instance_type
=
“${var.instance_type}”
key_name
=
“${var.key_name}”
tags
{
Name
=
“dev-‐supermarket-‐server”
}
security_groups
=
[“${aws_security_group.allow-‐ssh.name}”,
“${aws_security_group.allow-‐out.name}”]
(…)
}
…
This is the
Supermarket
Server
supermarket-cluster.tf](https://image.slidesharecdn.com/refactoringinfradevopsdayschidraft3-160831163013/75/Refactoring-Infrastructure-Code-67-2048.jpg)




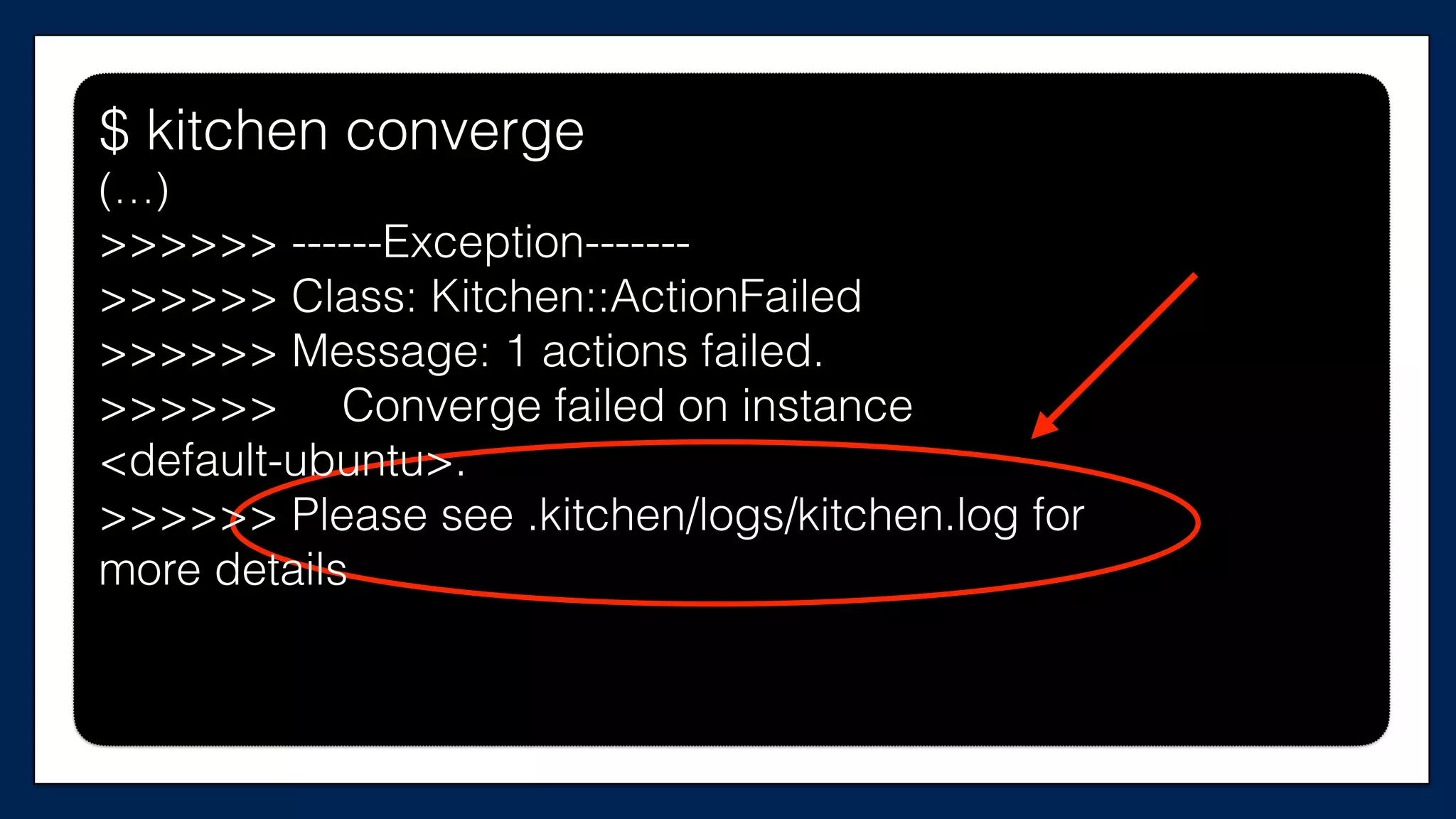


![…
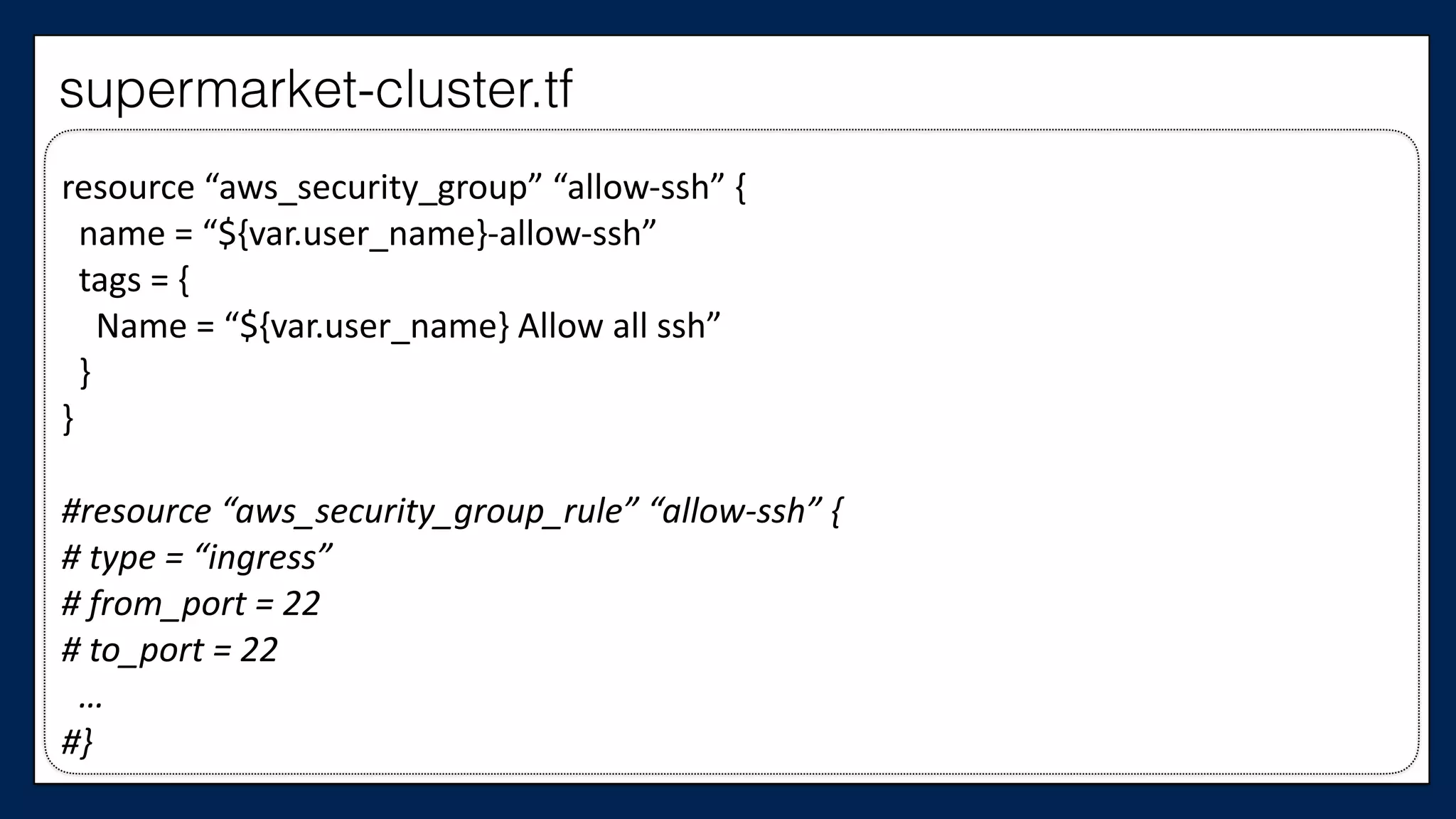
resource
“aws_instance”
“chef_server”
{
ami
=
“${var.ami}”
instance_type
=
“${var.instance_type}”
key_name
=
“${var.key_name}”
tags
{
Name
=
“dev-‐chef-‐server”
}
security_groups
=
[“${aws_security_group.allow-‐ssh.name}”,
“${aws_security_group.allow-‐out.name}”]
(…)
}
…
This is the
Chef Server
supermarket-cluster.tf](https://image.slidesharecdn.com/refactoringinfradevopsdayschidraft3-160831163013/75/Refactoring-Infrastructure-Code-85-2048.jpg)
![…
resource
“aws_instance”
“chef_server”
{
ami
=
“${var.ami}”
instance_type
=
“${var.instance_type}”
key_name
=
“${var.key_name}”
tags
{
Name
=
“dev-‐chef-‐server”
}
security_groups
=
[“${aws_security_group.allow-‐ssh.name}”]
(…)
}
…
This is the
Chef Server
supermarket-cluster.tf](https://image.slidesharecdn.com/refactoringinfradevopsdayschidraft3-160831163013/75/Refactoring-Infrastructure-Code-86-2048.jpg)

![…
resource
“aws_instance”
“supermarket_server”
{
ami
=
“${var.ami}”
instance_type
=
“${var.instance_type}”
key_name
=
“${var.key_name}”
tags
{
Name
=
“dev-‐supermarket-‐server”
}
security_groups
=
[“${aws_security_group.allow-‐ssh.name}”,
“${aws_security_group.allow-‐out.name}”]
(…)
}
…
This is the
Supermarket
Server
supermarket-cluster.tf](https://image.slidesharecdn.com/refactoringinfradevopsdayschidraft3-160831163013/75/Refactoring-Infrastructure-Code-88-2048.jpg)


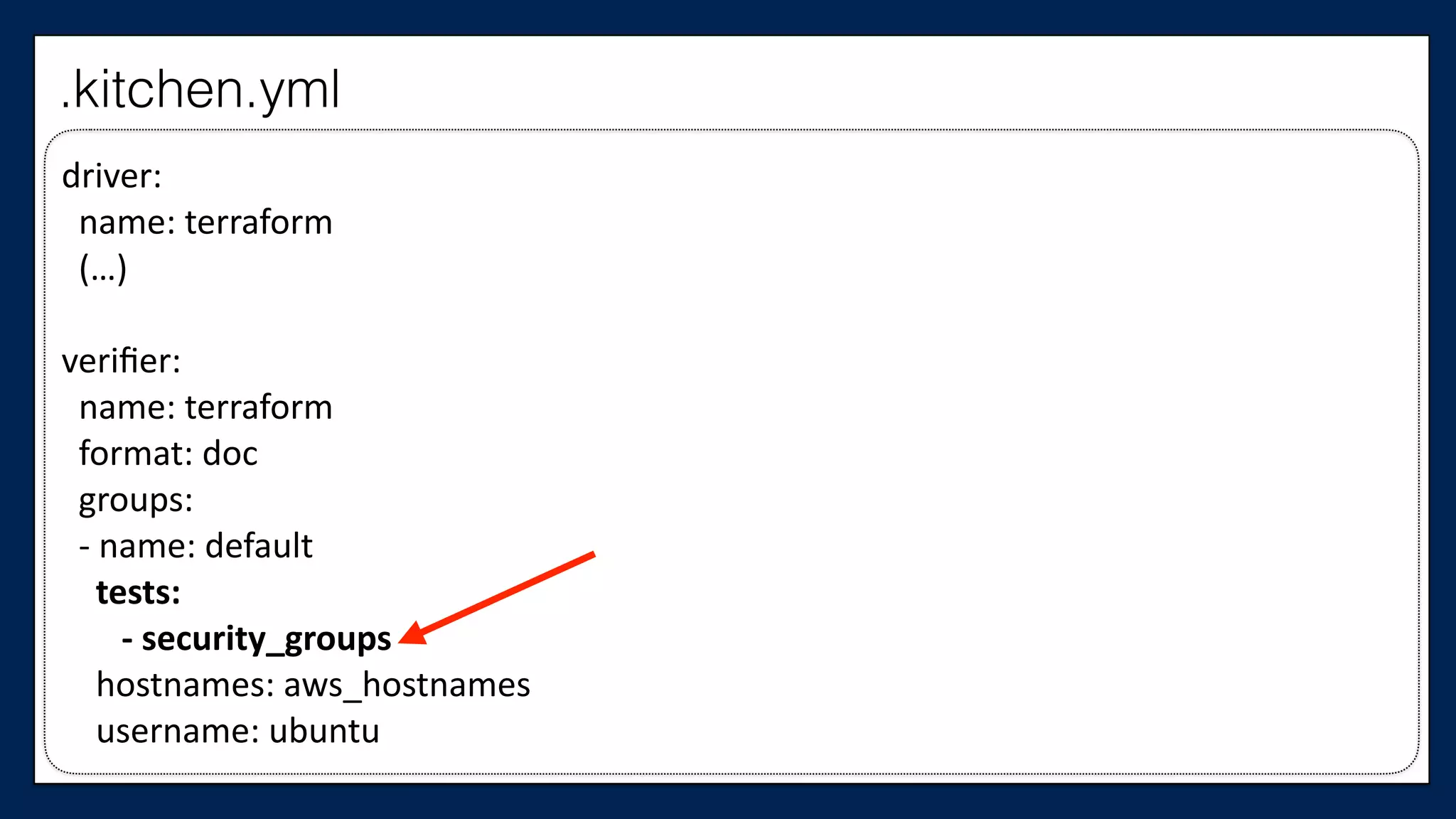
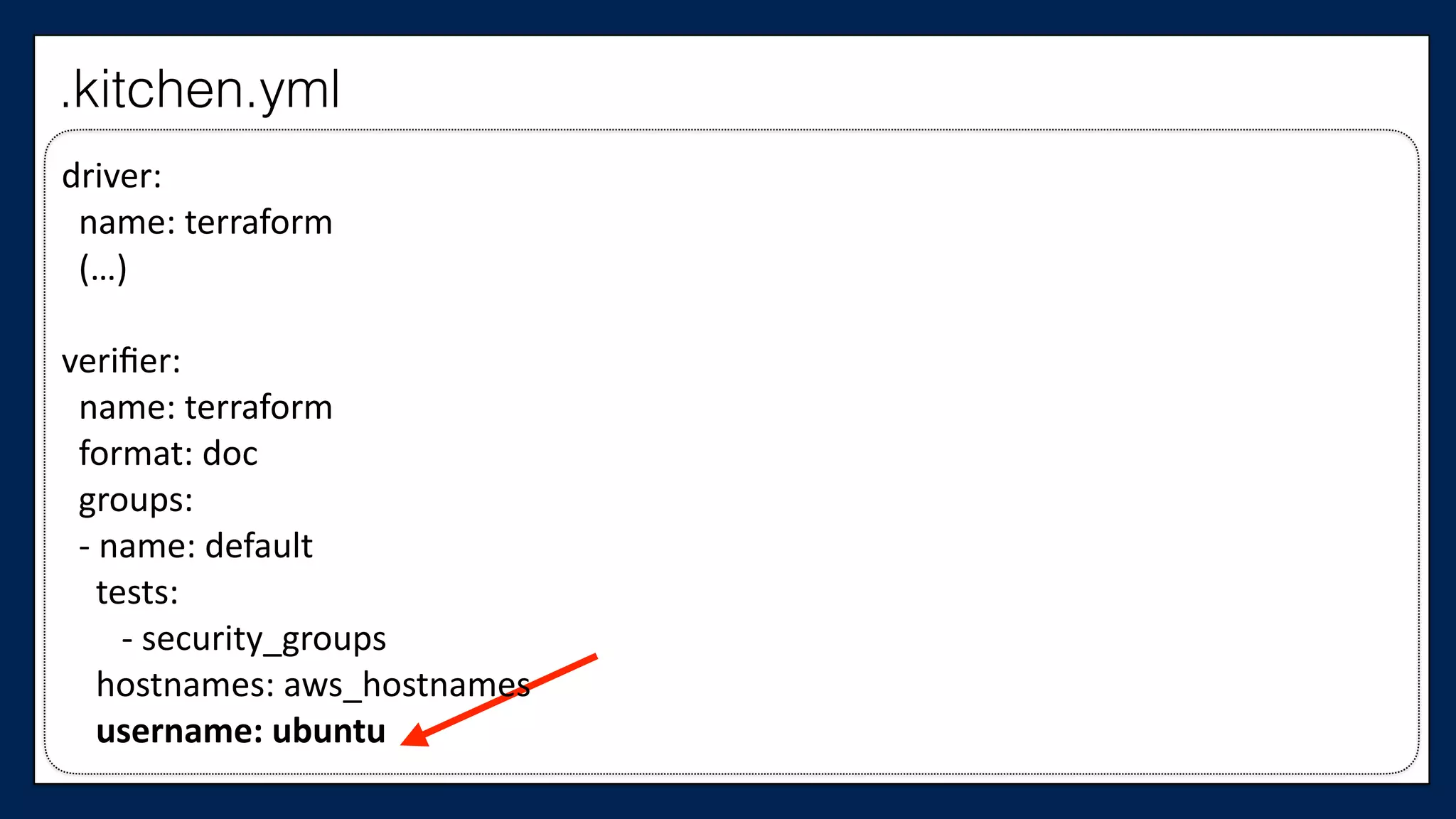
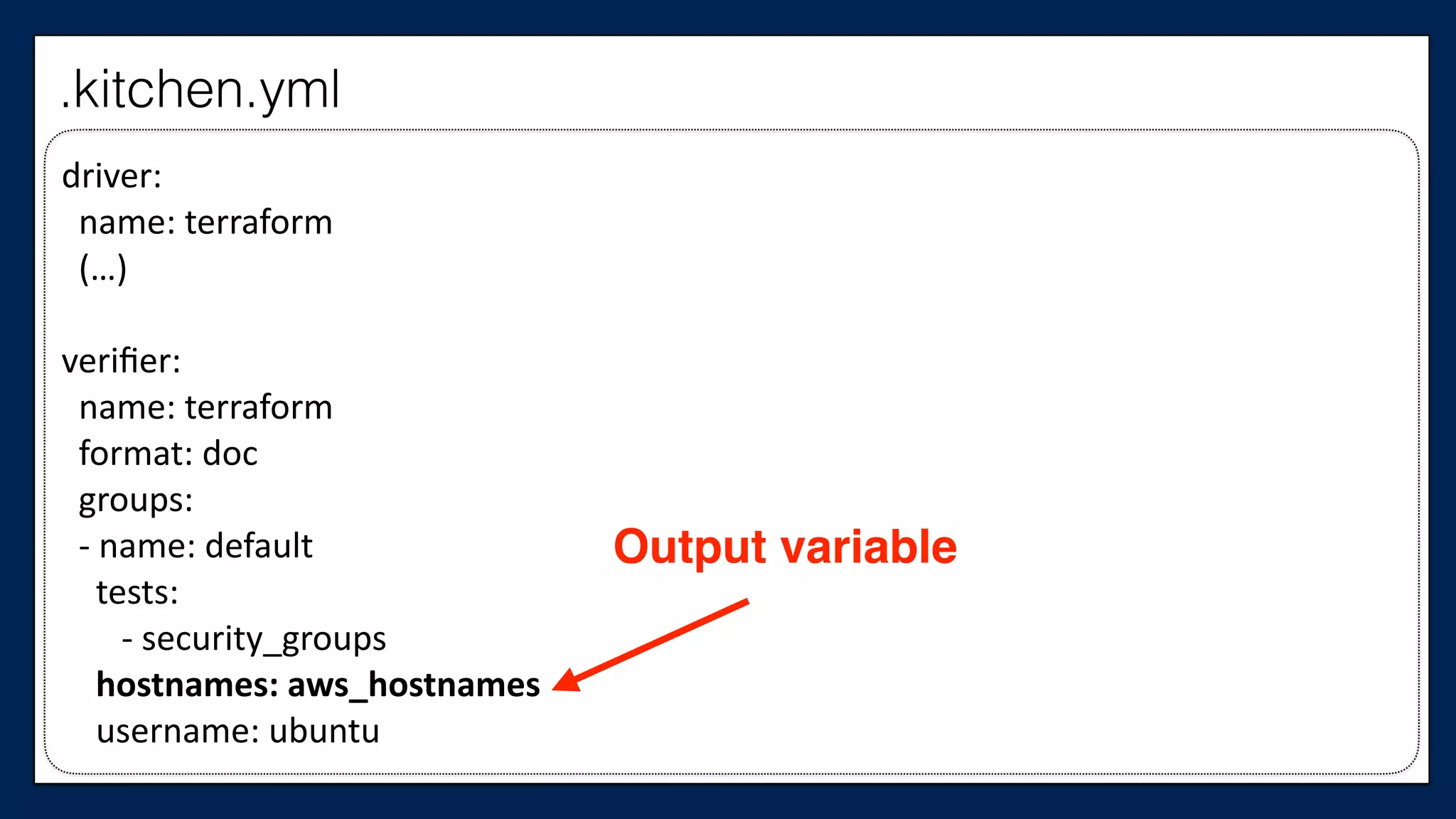

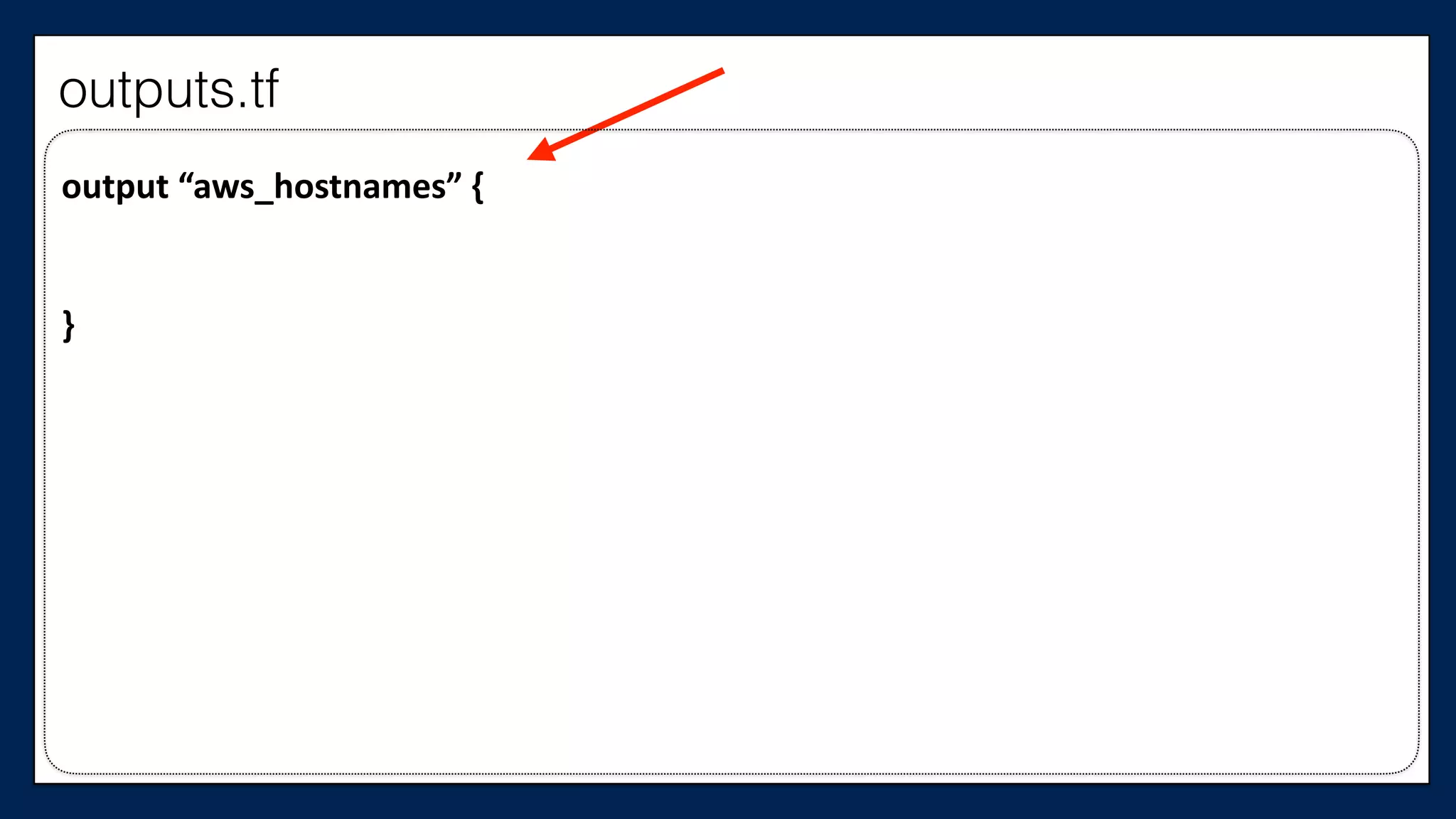
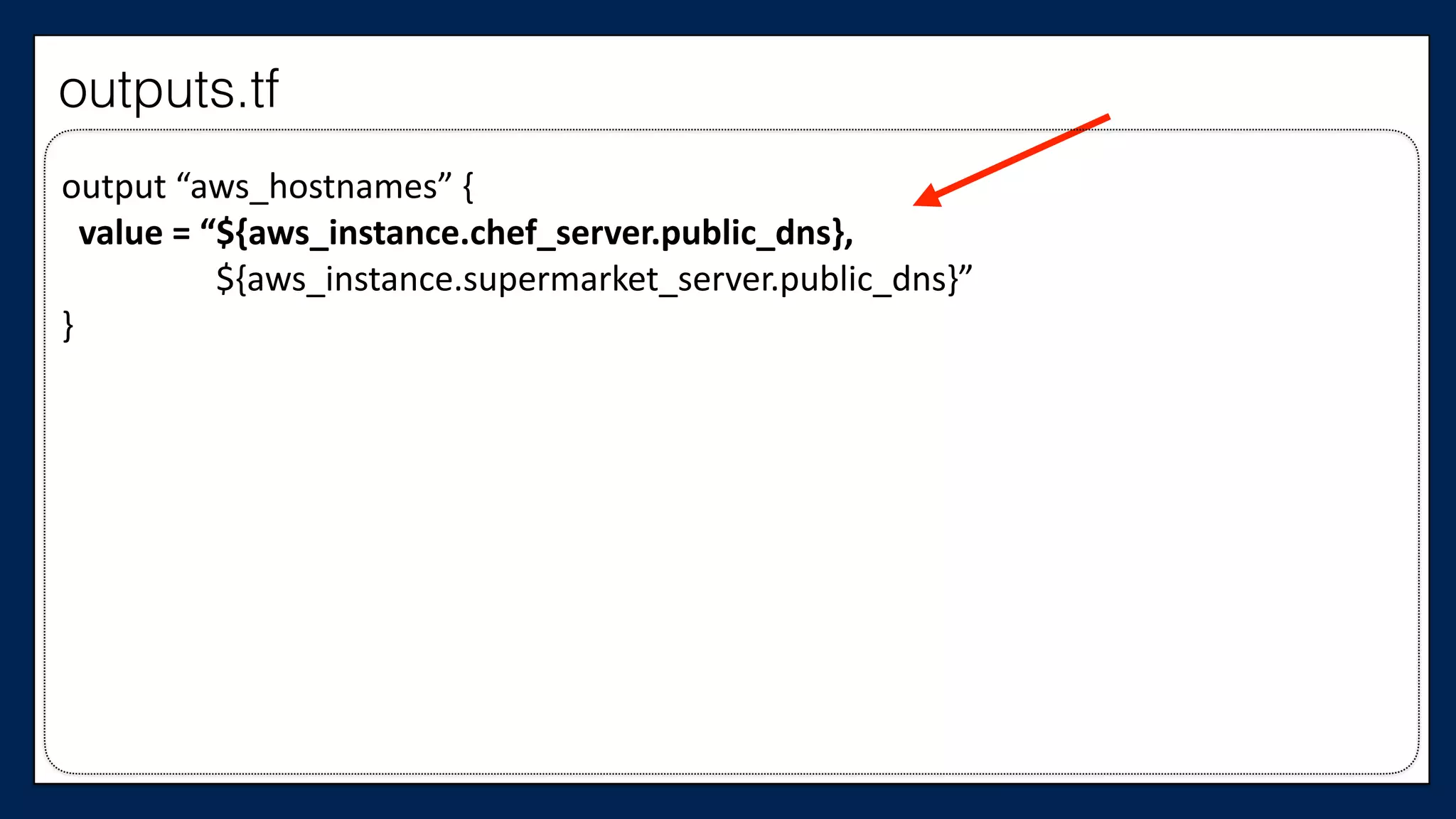
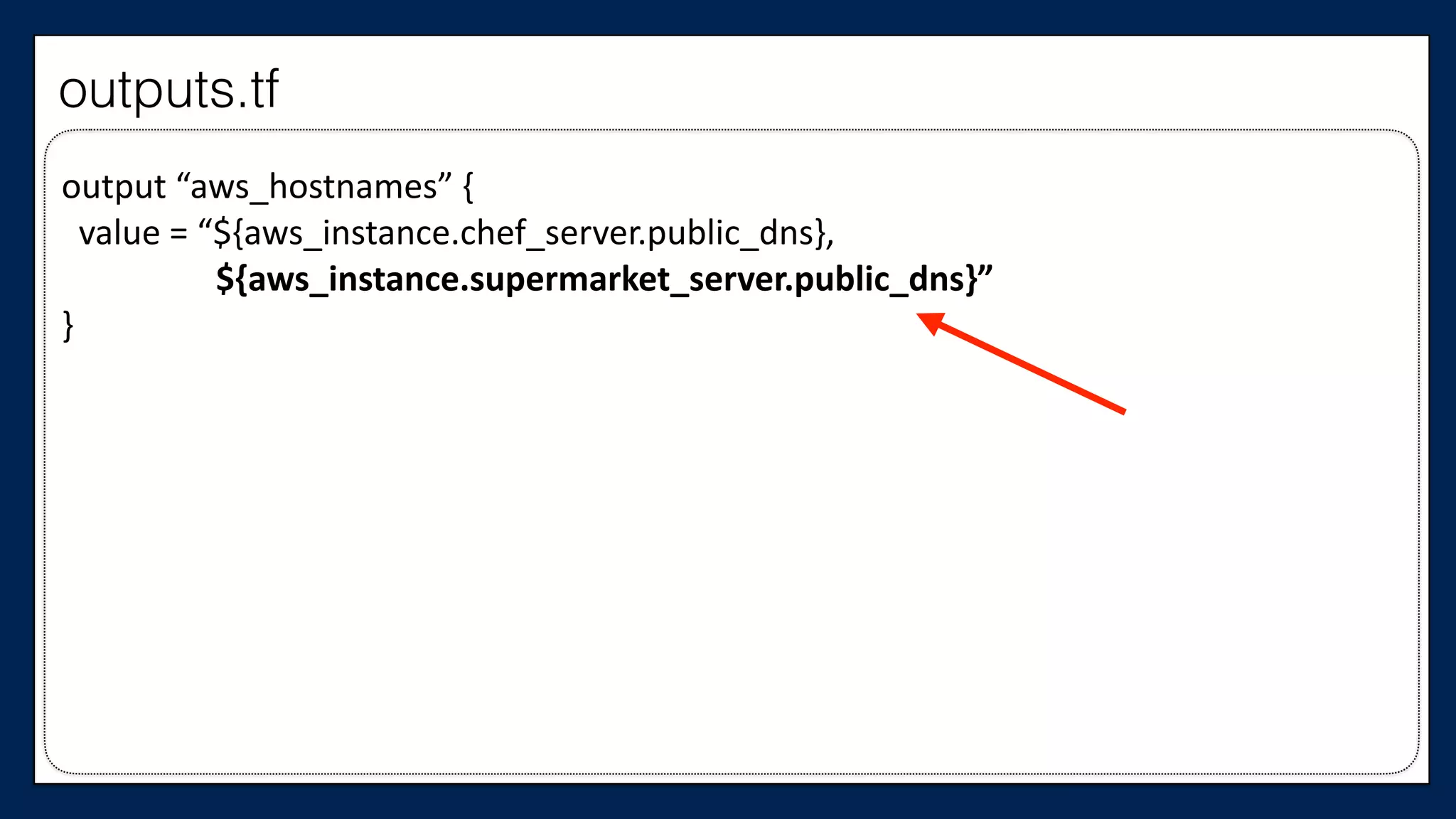
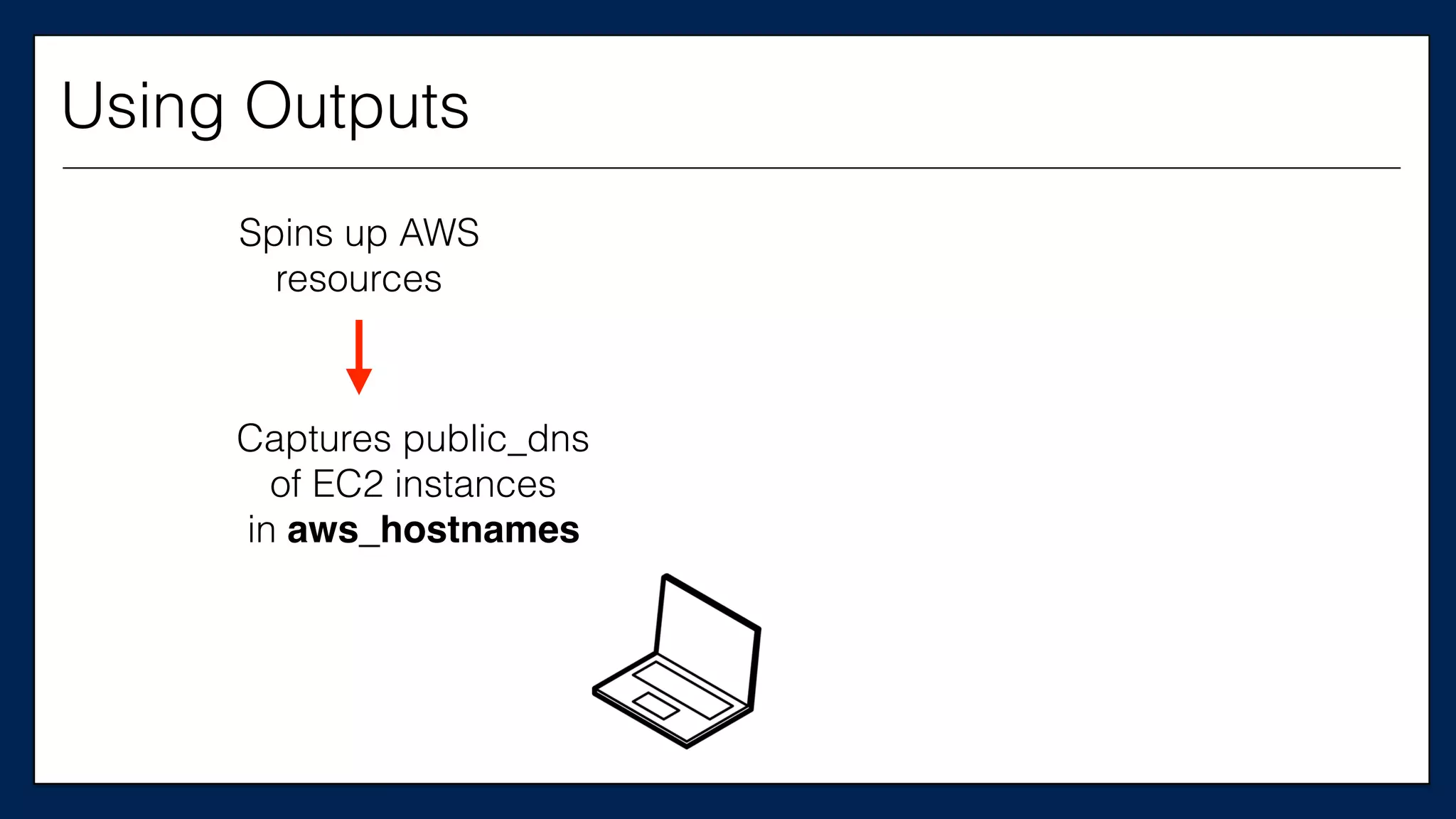
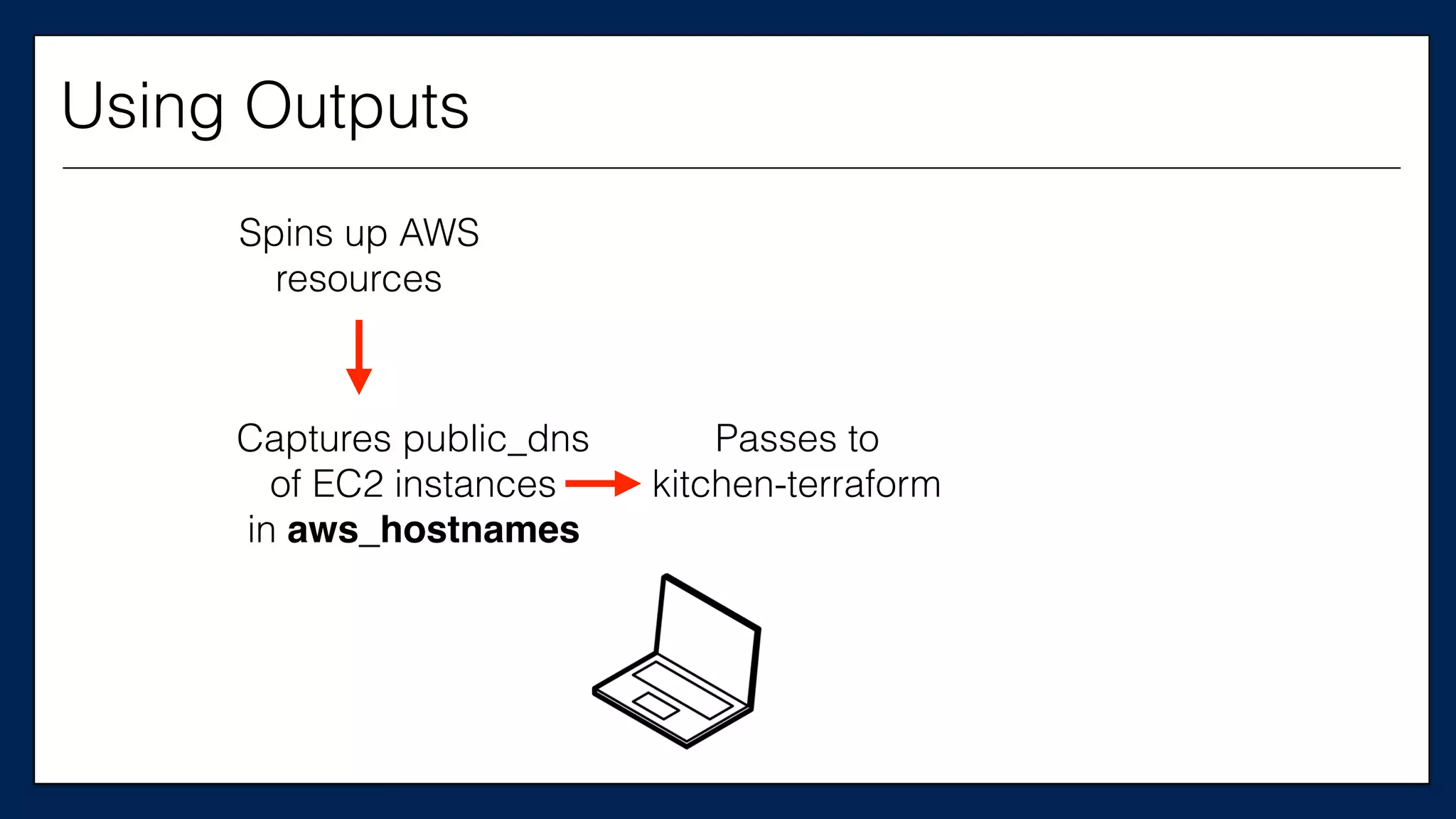
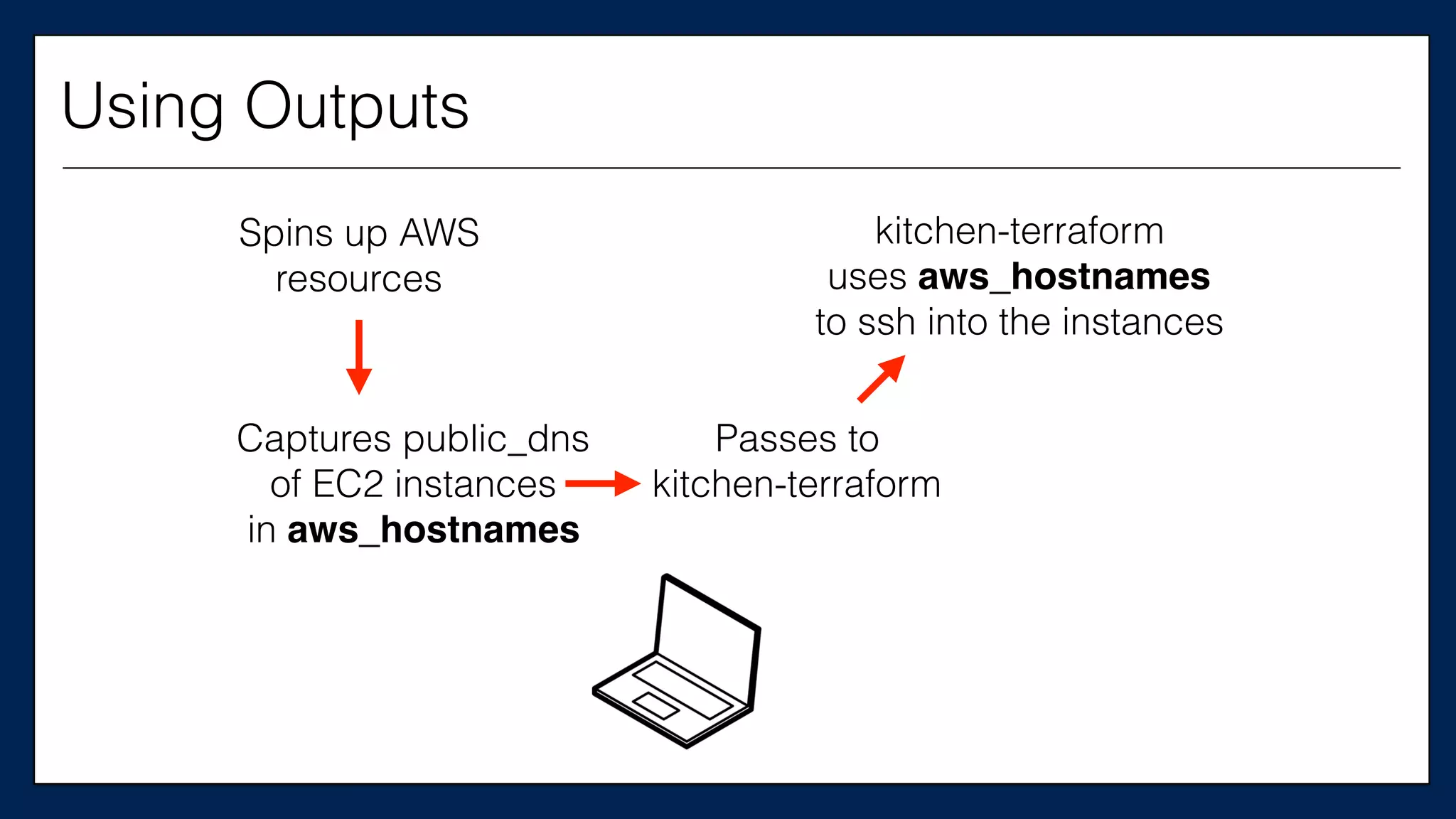
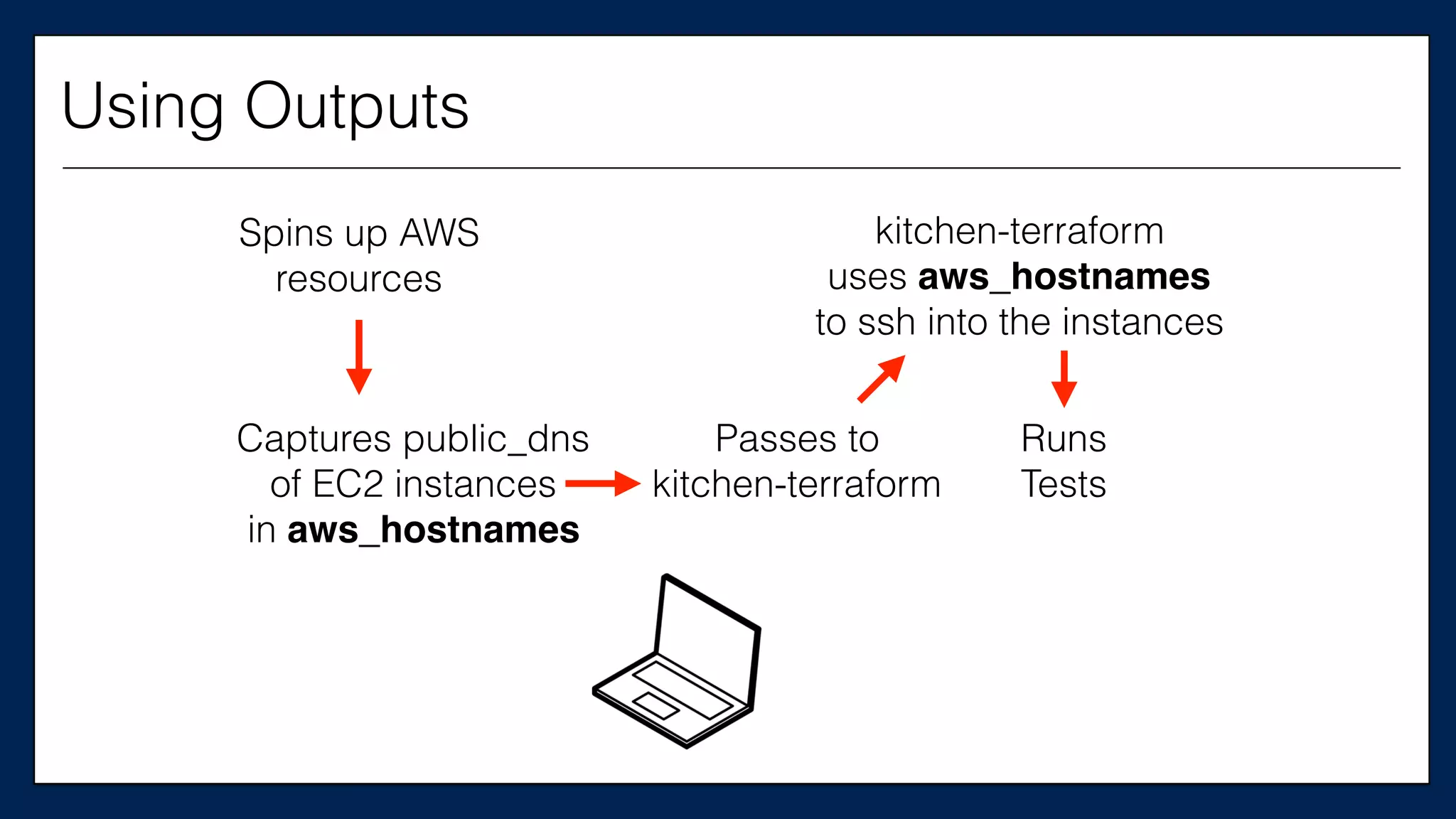

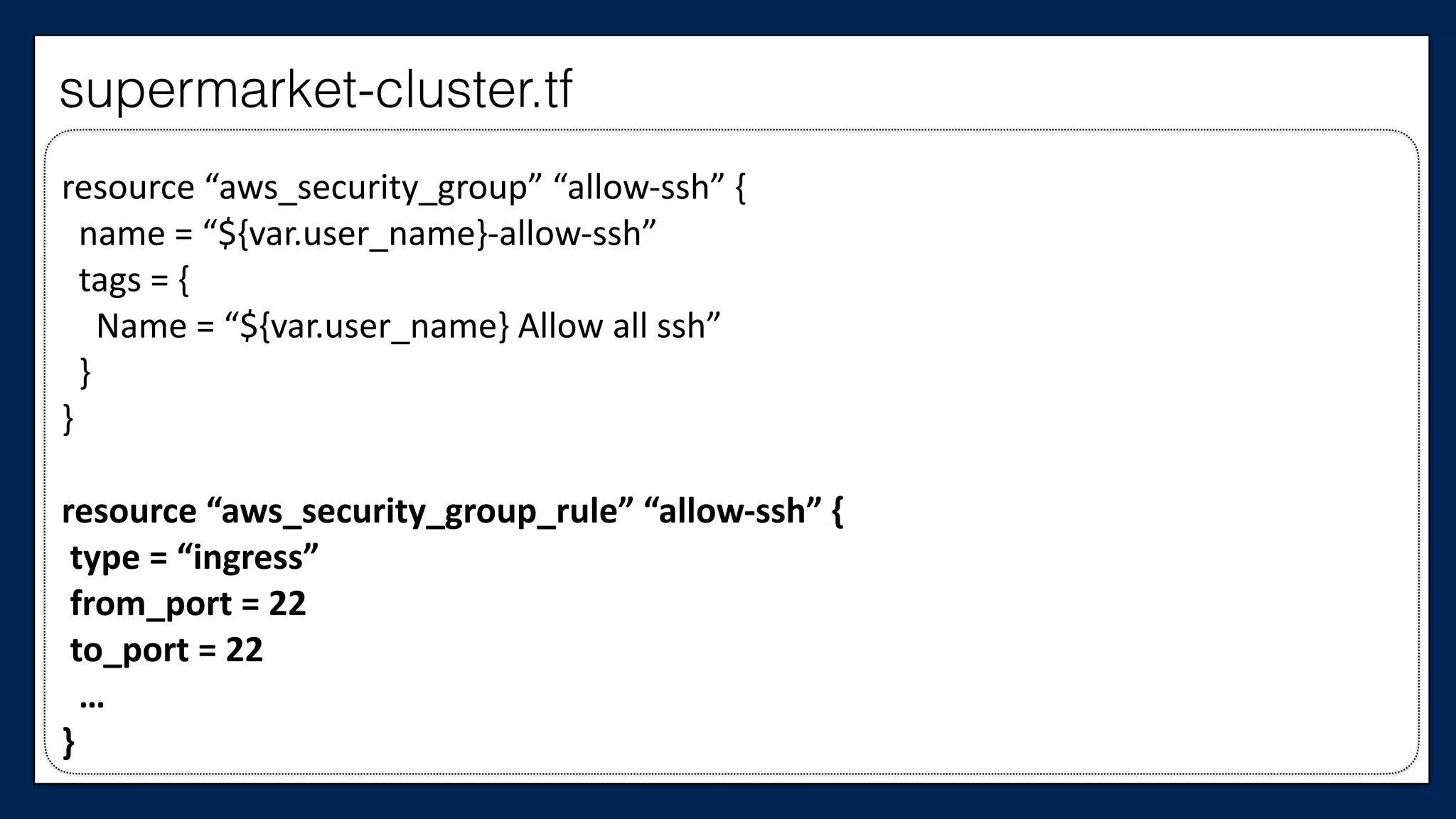
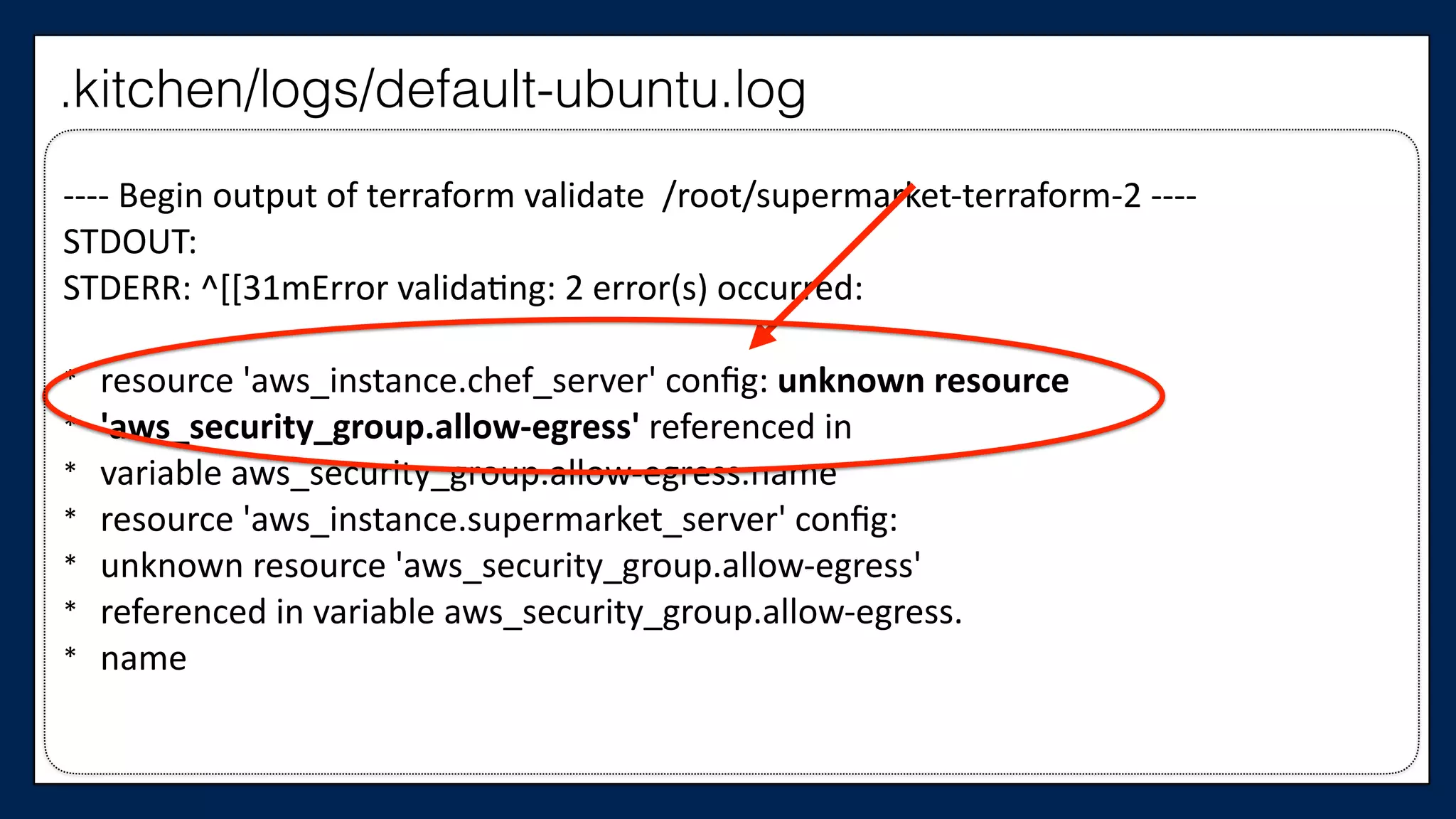
![#resource
“aws_security_group”
“allow-‐egress”
{
#
name
=
“${var.user_name}-‐allow-‐egress”
#
tags
=
{
#
Name
=
“${var.user_name}
Allow
connecLons
out”
#
}
#}
#resource
“aws_security_group_rule”
“allow-‐out”
{
#
type
=
“egress”
#
from_port
=
0
#
to_port
=
65535
#
cidr_blocks
=
["0.0.0.0/0"]
…
supermarket-cluster.tf](https://image.slidesharecdn.com/refactoringinfradevopsdayschidraft3-160831163013/75/Refactoring-Infrastructure-Code-111-2048.jpg)

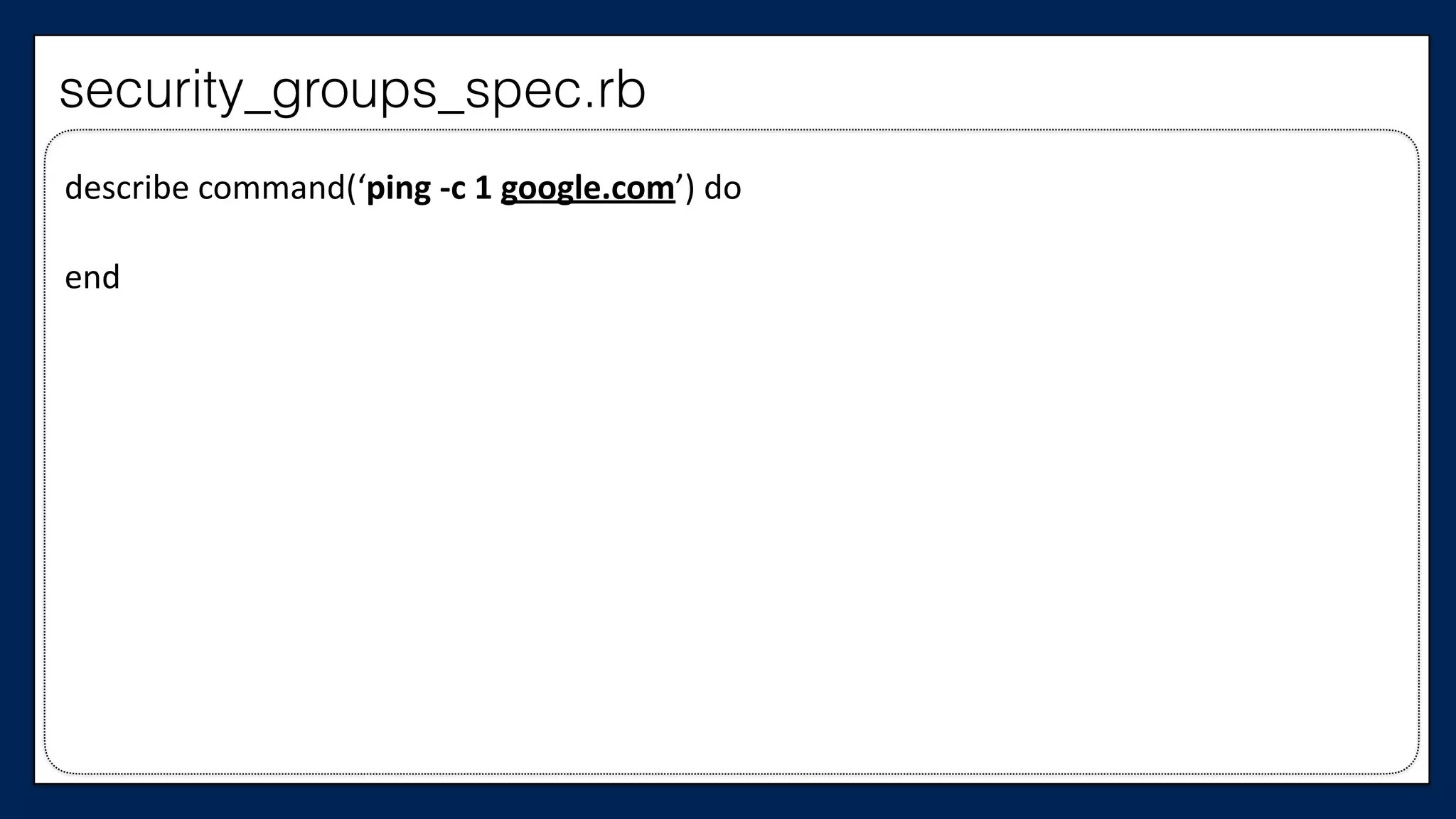
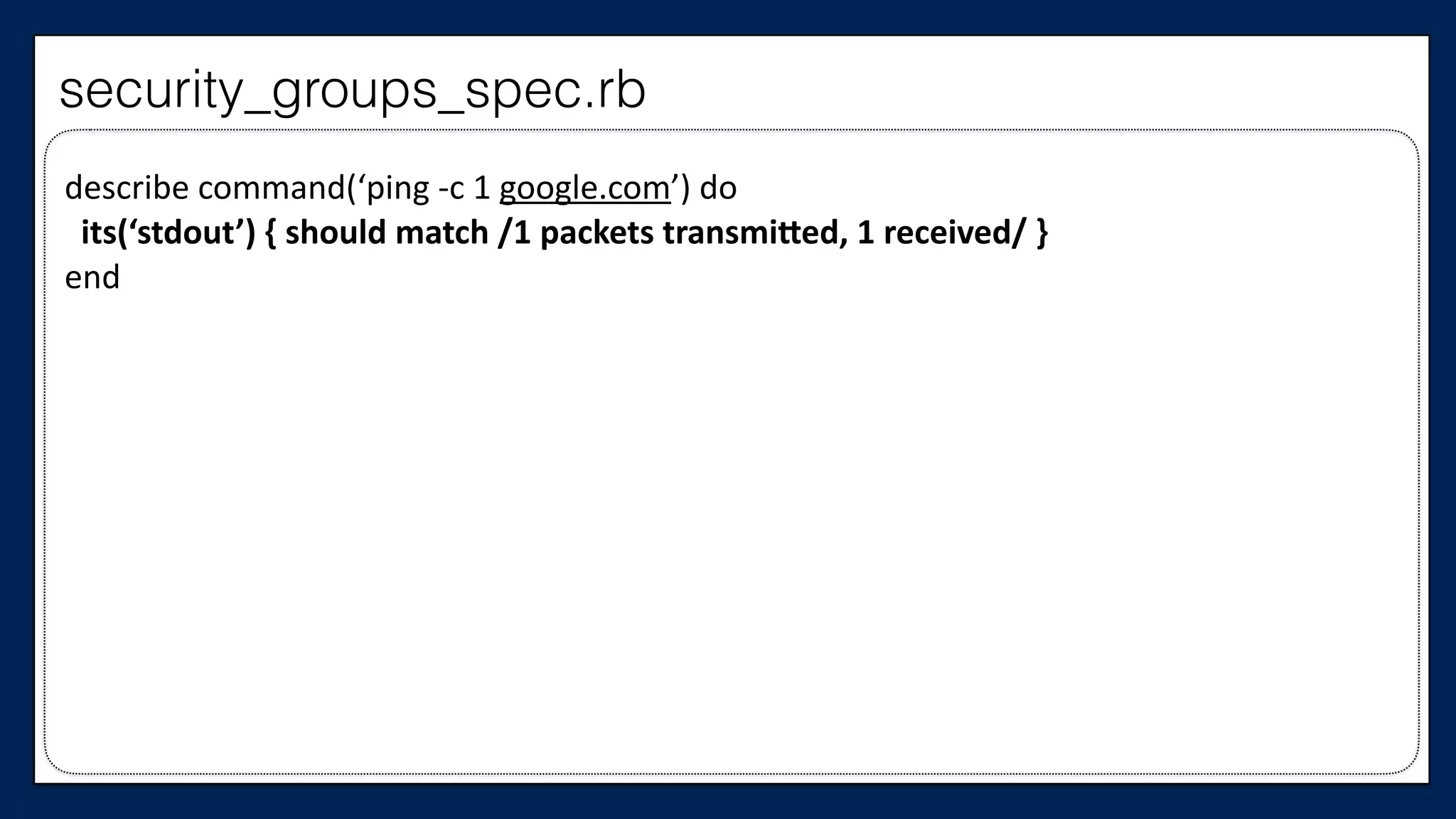
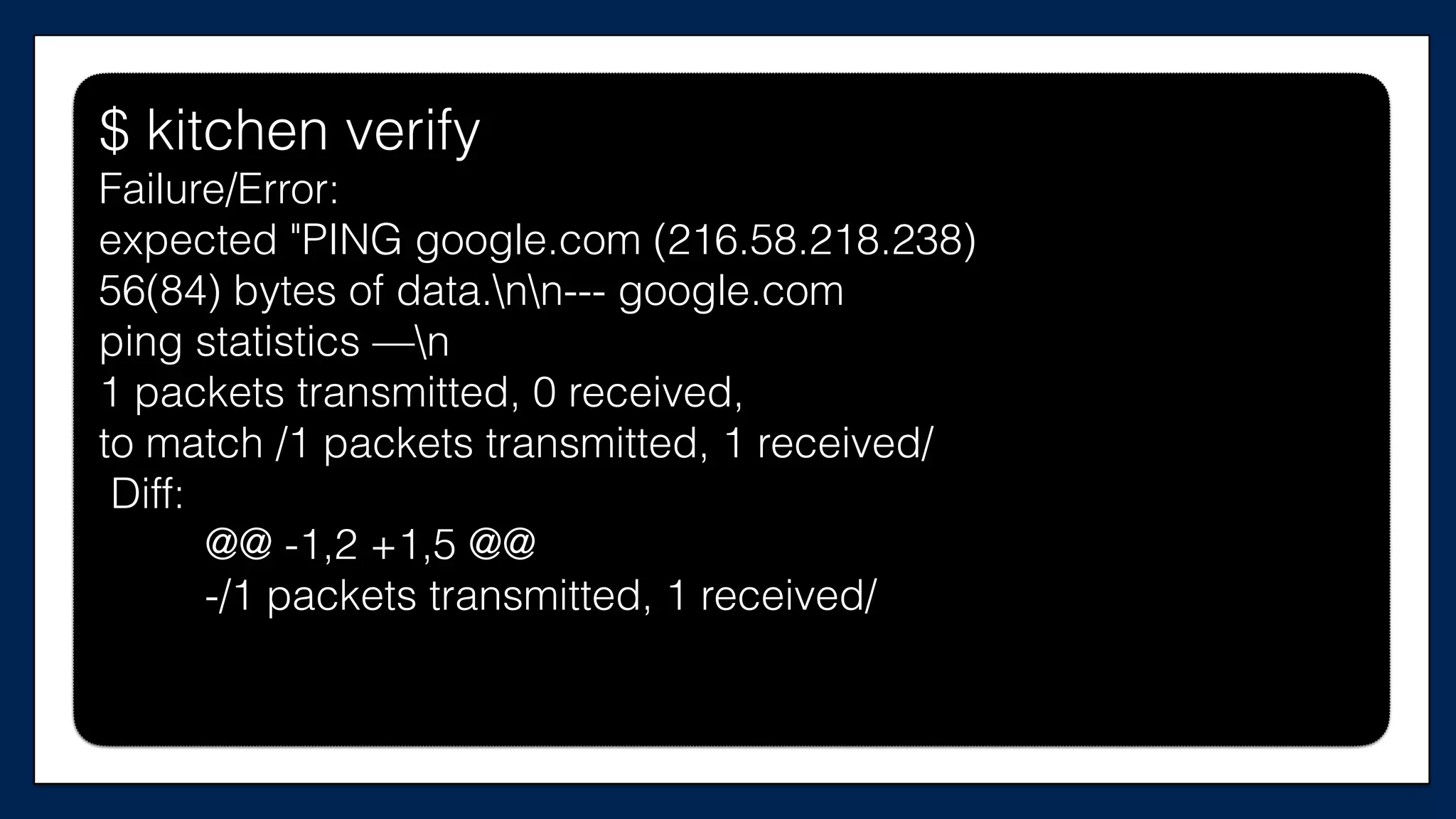


![#resource
“aws_security_group”
“allow-‐egress”
{
#
name
=
“${var.user_name}-‐allow-‐egress”
#
tags
=
{
#
Name
=
“${var.user_name}
Allow
connecLons
out”
#
}
#}
#resource
“aws_security_group_rule”
“allow-‐out”
{
#
type
=
“egress”
#
from_port
=
0
#
to_port
=
65535
#
cidr_blocks
=
["0.0.0.0/0"]
…
supermarket-cluster.tf](https://image.slidesharecdn.com/refactoringinfradevopsdayschidraft3-160831163013/75/Refactoring-Infrastructure-Code-119-2048.jpg)
![resource
“aws_security_group”
“allow-‐egress”
{
name
=
“${var.user_name}-‐allow-‐egress”
tags
=
{
Name
=
“${var.user_name}
Allow
connecTons
out”
}
}
resource
“aws_security_group_rule”
“allow-‐out”
{
type
=
“egress”
from_port
=
0
to_port
=
65535
cidr_blocks
=
["0.0.0.0/0"]
…
supermarket-cluster.tf](https://image.slidesharecdn.com/refactoringinfradevopsdayschidraft3-160831163013/75/Refactoring-Infrastructure-Code-120-2048.jpg)
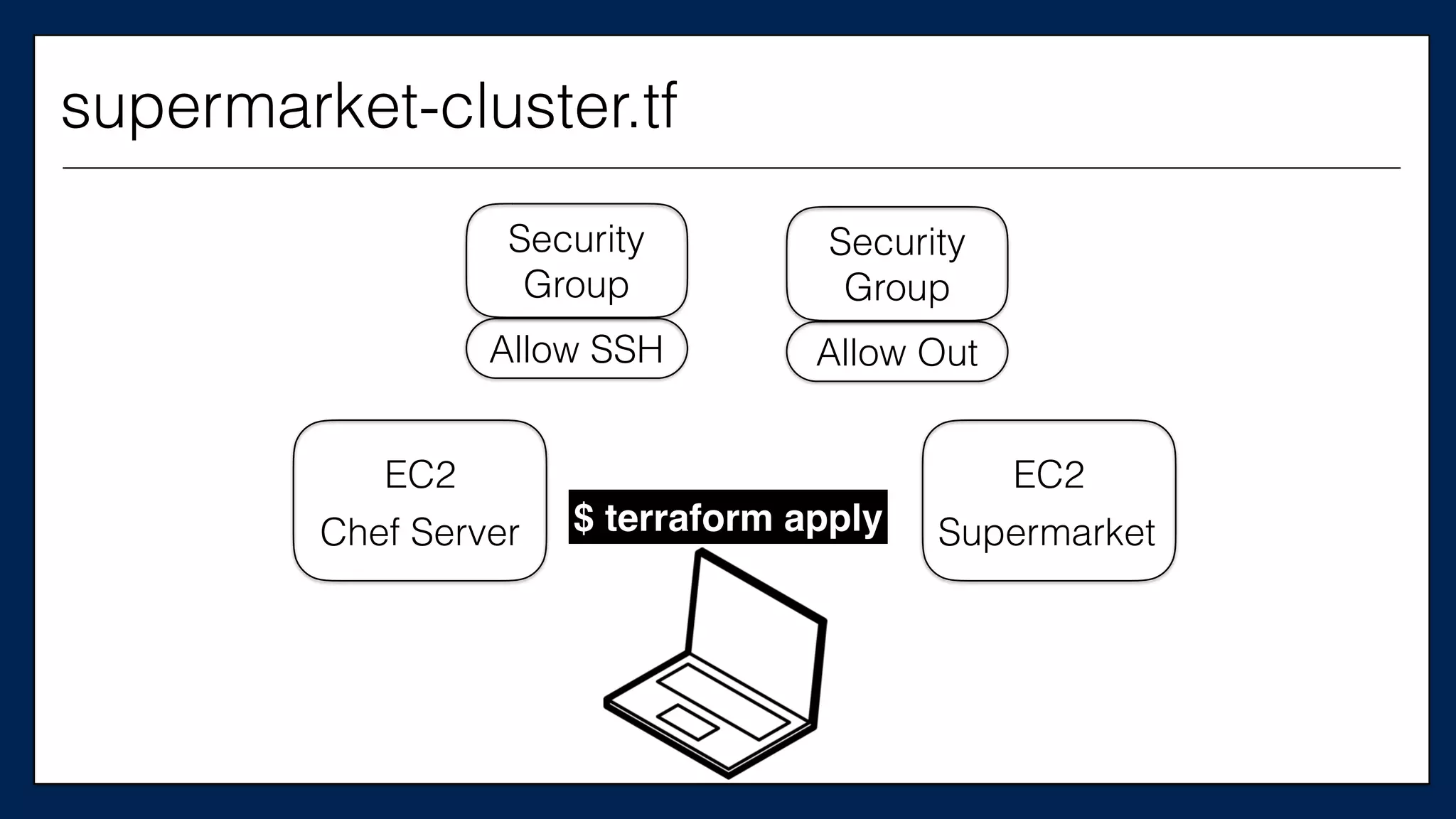

![…
resource
“aws_instance”
“chef_server”
{
ami
=
“${var.ami}”
instance_type
=
“${var.instance_type}”
key_name
=
“${var.key_name}”
tags
{
Name
=
“dev-‐chef-‐server”
}
security_groups
=
[“${aws_security_group.allow-‐ssh.name}”]
(…)
}
…
This is the
Chef Server
supermarket-cluster.tf](https://image.slidesharecdn.com/refactoringinfradevopsdayschidraft3-160831163013/75/Refactoring-Infrastructure-Code-123-2048.jpg)
![…
resource
“aws_instance”
“chef_server”
{
ami
=
“${var.ami}”
instance_type
=
“${var.instance_type}”
key_name
=
“${var.key_name}”
tags
{
Name
=
“dev-‐chef-‐server”
}
security_groups
=
[“${aws_security_group.allow-‐ssh.name}”,
“${aws_security_group.allow-‐out.name}”]
(…)
}
…
This is the
Chef Server
supermarket-cluster.tf](https://image.slidesharecdn.com/refactoringinfradevopsdayschidraft3-160831163013/75/Refactoring-Infrastructure-Code-124-2048.jpg)

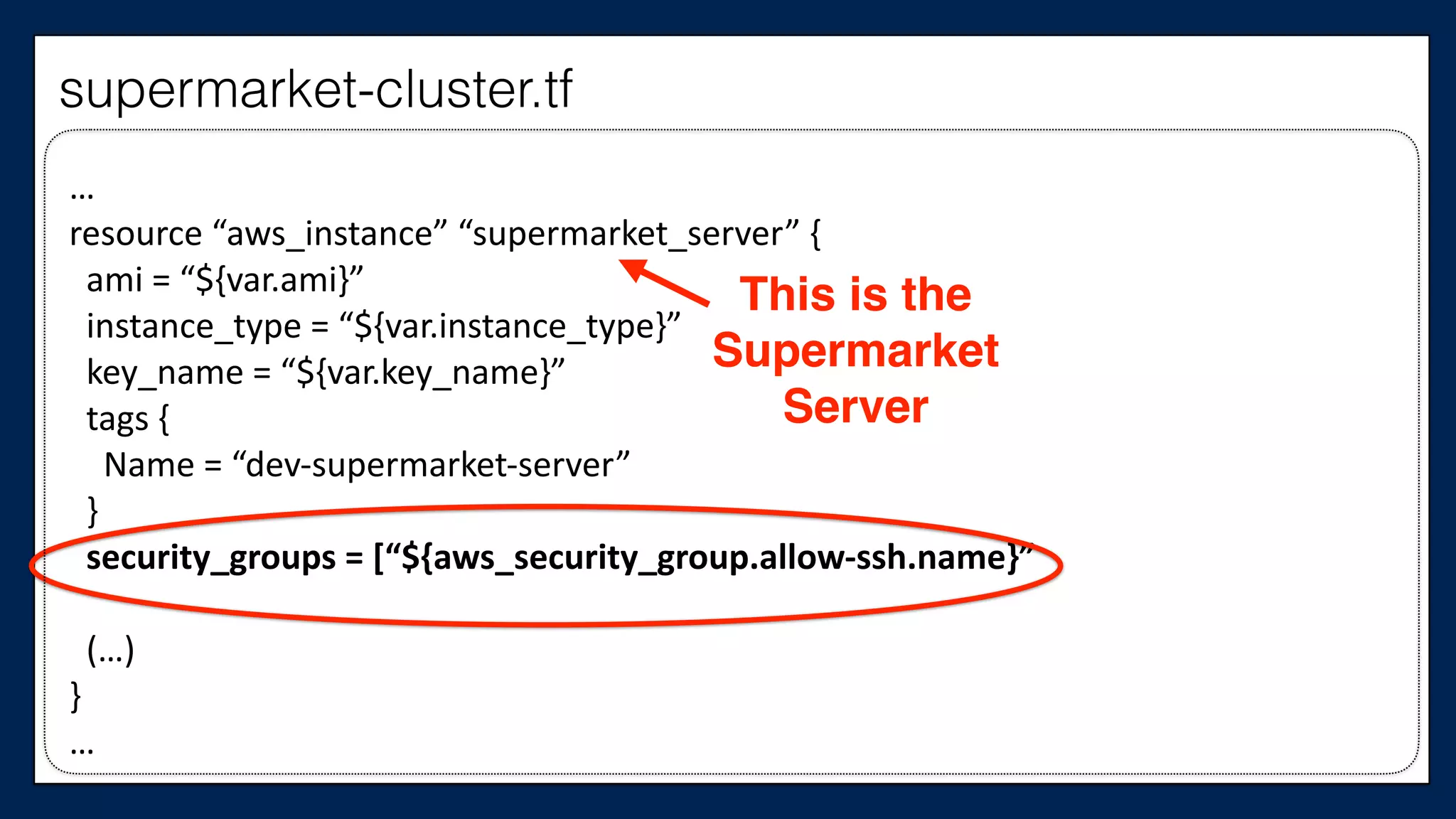
![…
resource
“aws_instance”
“supermarket_server”
{
ami
=
“${var.ami}”
instance_type
=
“${var.instance_type}”
key_name
=
“${var.key_name}”
tags
{
Name
=
“dev-‐supermarket-‐server”
}
security_groups
=
[“${aws_security_group.allow-‐ssh.name}”,
“${aws_security_group.allow-‐out.name}”]
(…)
}
…
This is the
Supermarket
Server
supermarket-cluster.tf](https://image.slidesharecdn.com/refactoringinfradevopsdayschidraft3-160831163013/75/Refactoring-Infrastructure-Code-127-2048.jpg)




![resource
“aws_security_group”
“allow-‐egress”
{
name
=
“${var.user_name}-‐allow-‐egress”
tags
=
{
Name
=
“${var.user_name}
Allow
connecWons
out”
}
}
resource
“aws_security_group_rule”
“allow-‐out”
{
type
=
“egress”
from_port
=
0
to_port
=
65535
cidr_blocks
=
["0.0.0.0/0"]
…
supermarket-cluster.tf](https://image.slidesharecdn.com/refactoringinfradevopsdayschidraft3-160831163013/75/Refactoring-Infrastructure-Code-133-2048.jpg)
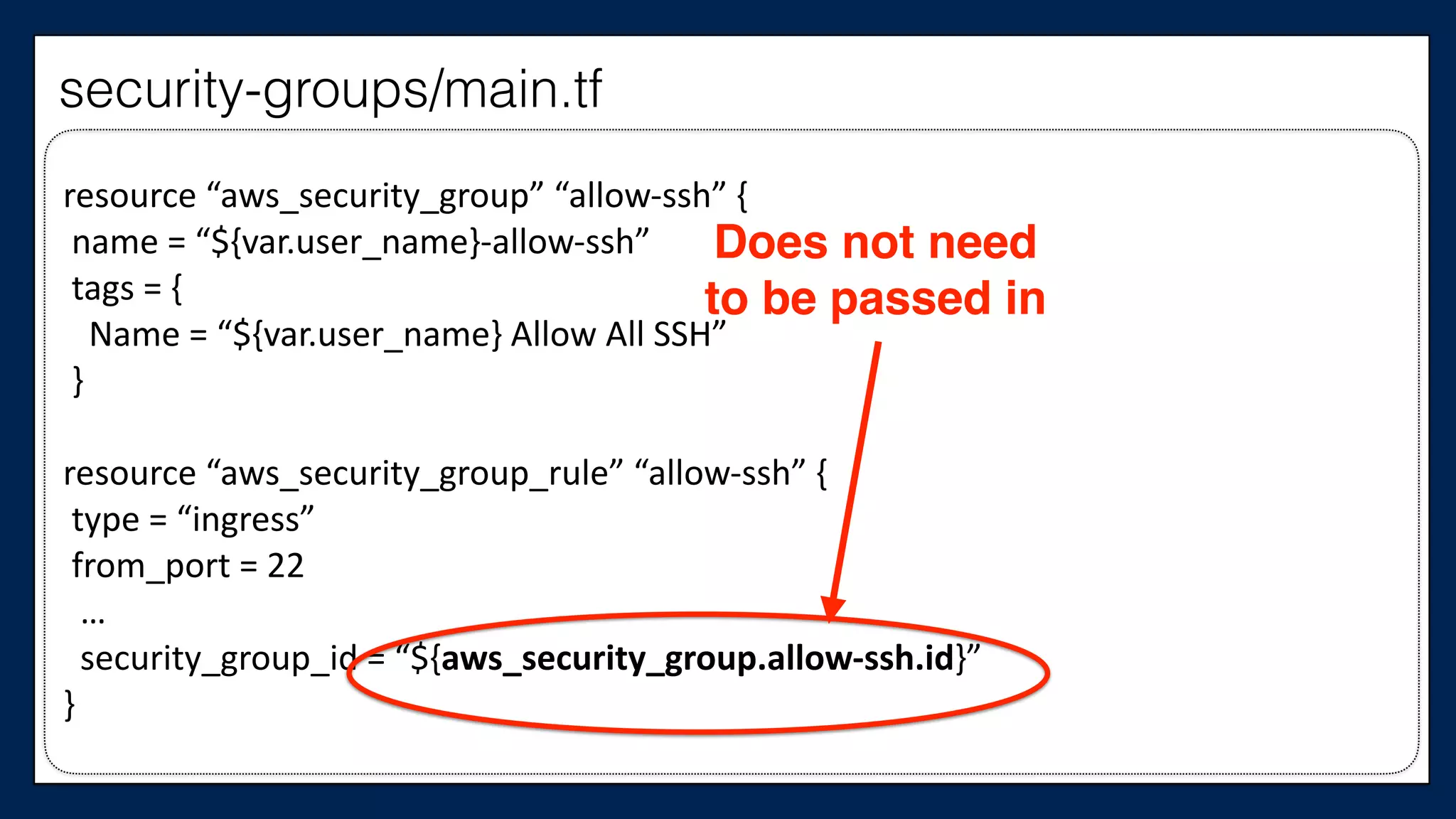
![resource
“aws_security_group_rule”
“allow-‐out”
{
type
=
“egress”
from_port
=
0
to_port
=
65535
cidr_blocks
=
["0.0.0.0/0"]
security_group_id
“${aws_security_group.allow-‐egress.id}”
}
supermarket-cluster.tf](https://image.slidesharecdn.com/refactoringinfradevopsdayschidraft3-160831163013/75/Refactoring-Infrastructure-Code-134-2048.jpg)
![resource
“aws_security_group_rule”
“allow-‐out”
{
type
=
“egress”
from_port
=
0
to_port
=
65535
cidr_blocks
=
["0.0.0.0/0"]
security_group_id
“${aws_security_group.allow-‐ssh.id}”
}
supermarket-cluster.tf](https://image.slidesharecdn.com/refactoringinfradevopsdayschidraft3-160831163013/75/Refactoring-Infrastructure-Code-135-2048.jpg)

![…
resource
“aws_instance”
“chef_server”
{
ami
=
“${var.ami}”
instance_type
=
“${var.instance_type}”
key_name
=
“${var.key_name}”
tags
{
Name
=
“dev-‐chef-‐server”
}
security_groups
=
[“${aws_security_group.allow-‐ssh.name}”,
“${aws_security_group.allow-‐out.name}”]
(…)
}
…
This is the
Chef Server
supermarket-cluster.tf](https://image.slidesharecdn.com/refactoringinfradevopsdayschidraft3-160831163013/75/Refactoring-Infrastructure-Code-137-2048.jpg)
![…
resource
“aws_instance”
“chef_server”
{
ami
=
“${var.ami}”
instance_type
=
“${var.instance_type}”
key_name
=
“${var.key_name}”
tags
{
Name
=
“dev-‐chef-‐server”
}
security_groups
=
[“${aws_security_group.allow-‐ssh.name}”]
(…)
}
…
This is the
Chef Server
supermarket-cluster.tf](https://image.slidesharecdn.com/refactoringinfradevopsdayschidraft3-160831163013/75/Refactoring-Infrastructure-Code-138-2048.jpg)
![…
resource
“aws_instance”
“supermarket_server”
{
ami
=
“${var.ami}”
instance_type
=
“${var.instance_type}”
key_name
=
“${var.key_name}”
tags
{
Name
=
“dev-‐supermarket-‐server”
}
security_groups
=
[“${aws_security_group.allow-‐ssh.name}”,
“${aws_security_group.allow-‐out.name}”]
(…)
}
…
This is the
Supermarket
Server
supermarket-cluster.tf](https://image.slidesharecdn.com/refactoringinfradevopsdayschidraft3-160831163013/75/Refactoring-Infrastructure-Code-139-2048.jpg)
![…
resource
“aws_instance”
“supermarket_server”
{
ami
=
“${var.ami}”
instance_type
=
“${var.instance_type}”
key_name
=
“${var.key_name}”
tags
{
Name
=
“dev-‐supermarket-‐server”
}
security_groups
=
[“${aws_security_group.allow-‐ssh.name}”]
(…)
}
…
This is the
Supermarket
Server
supermarket-cluster.tf](https://image.slidesharecdn.com/refactoringinfradevopsdayschidraft3-160831163013/75/Refactoring-Infrastructure-Code-140-2048.jpg)
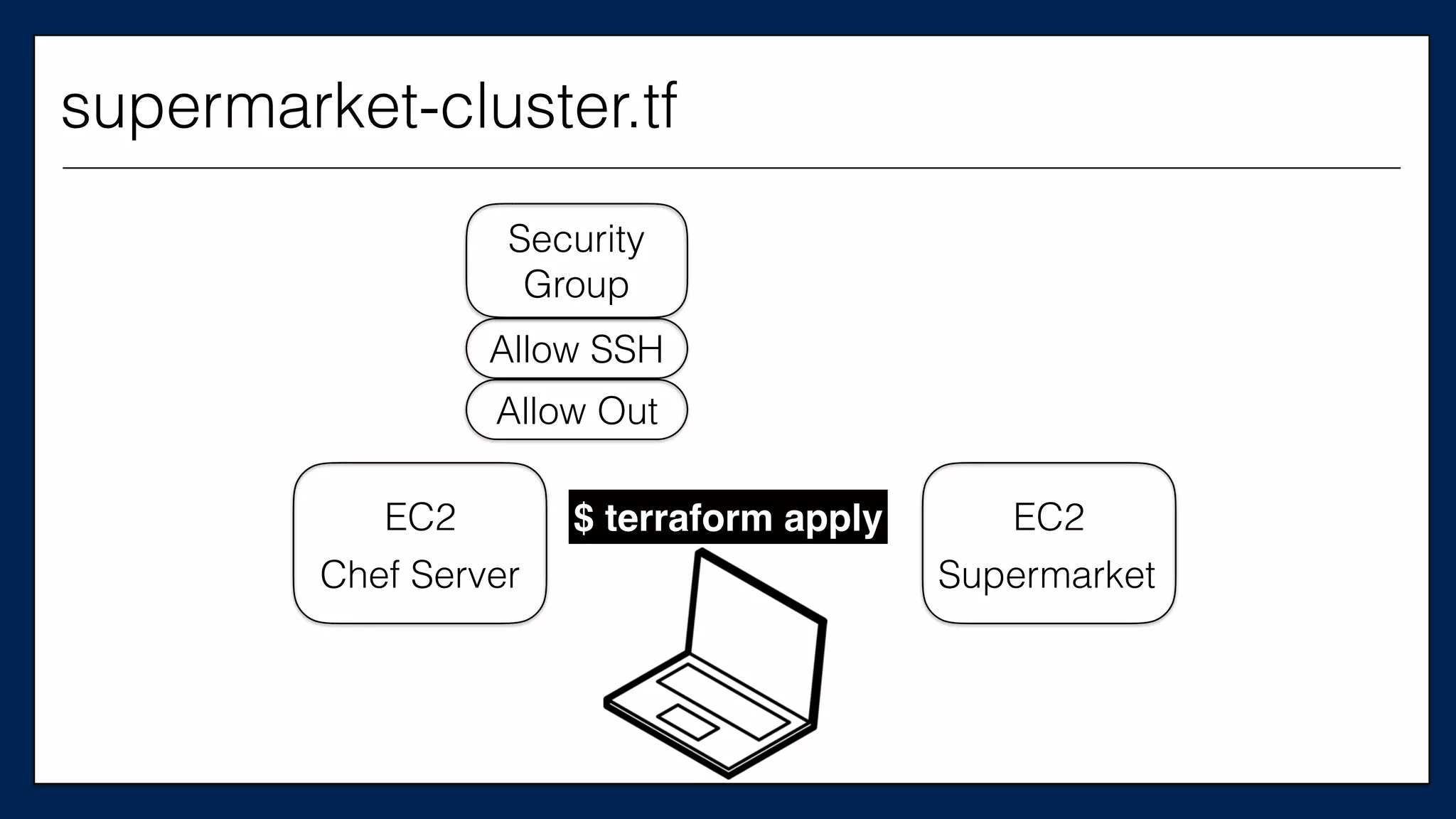


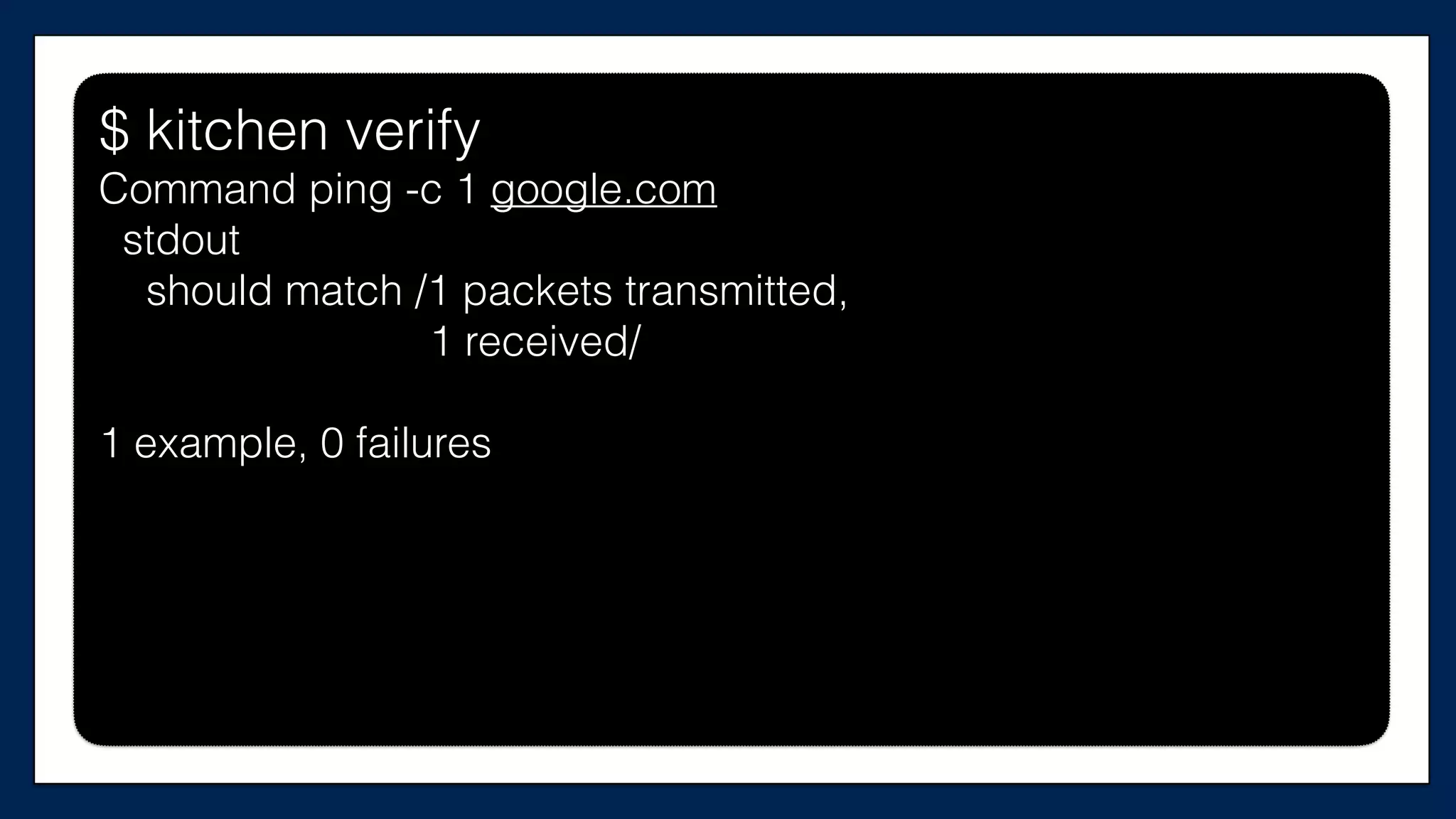


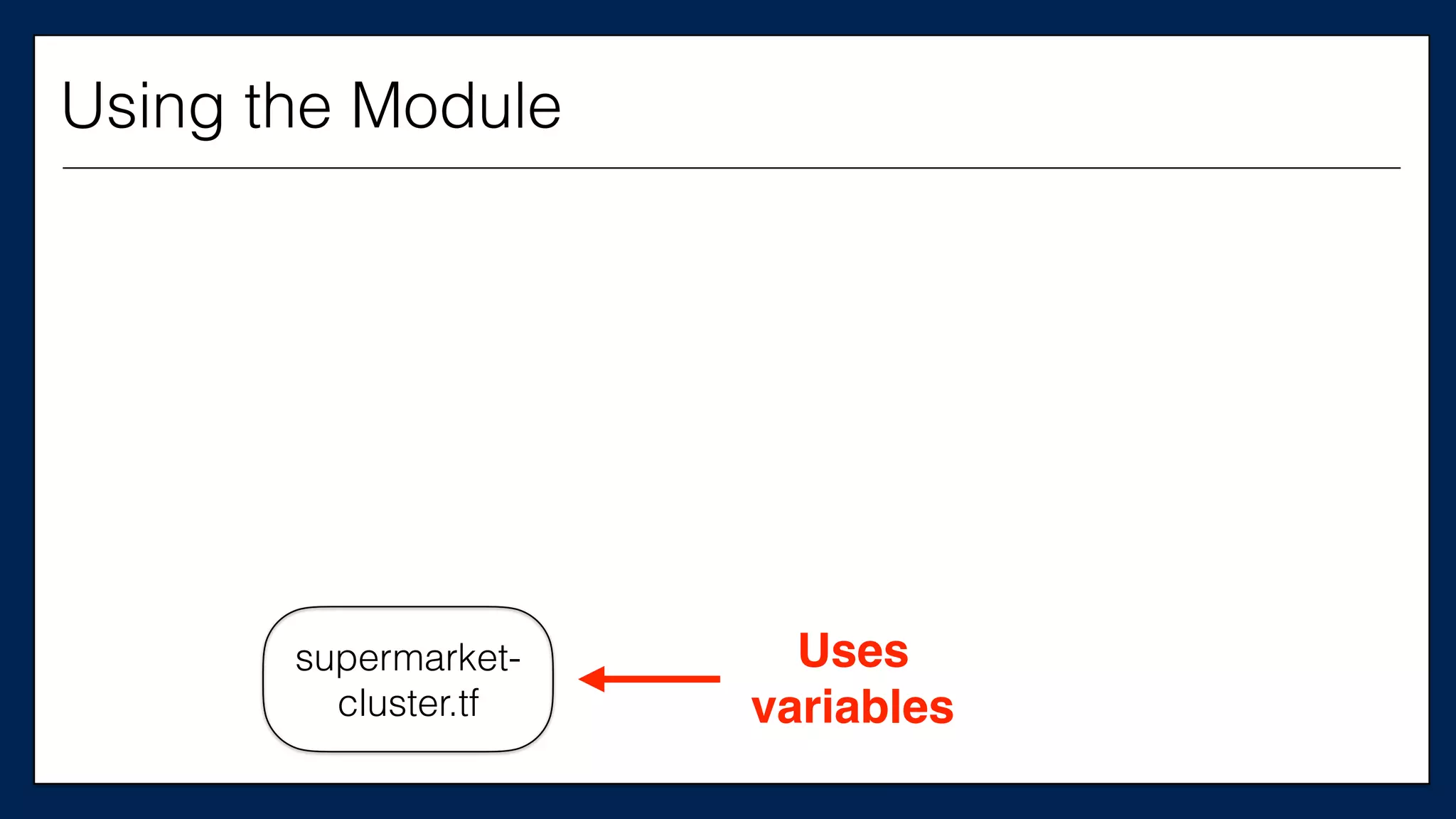
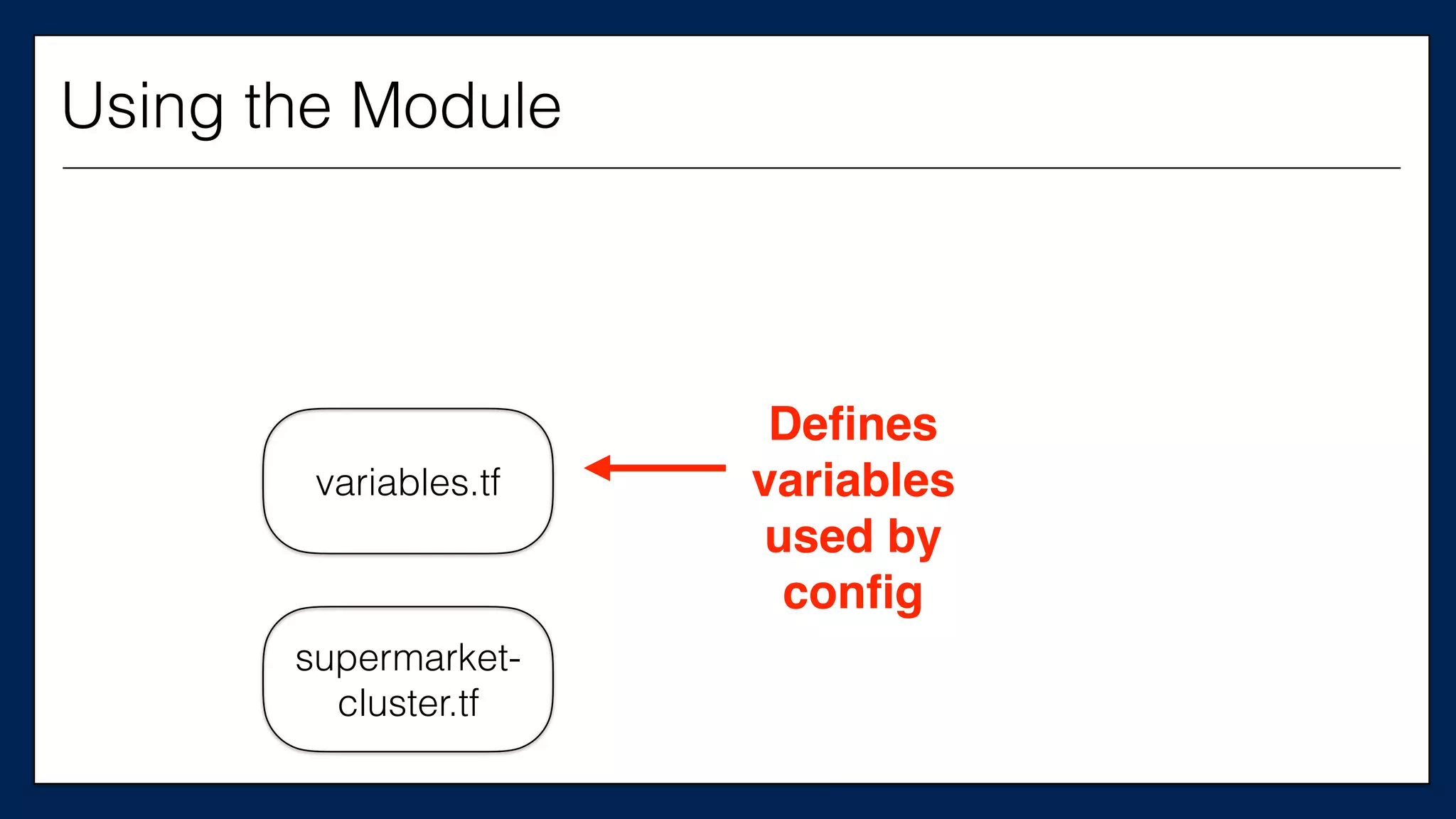
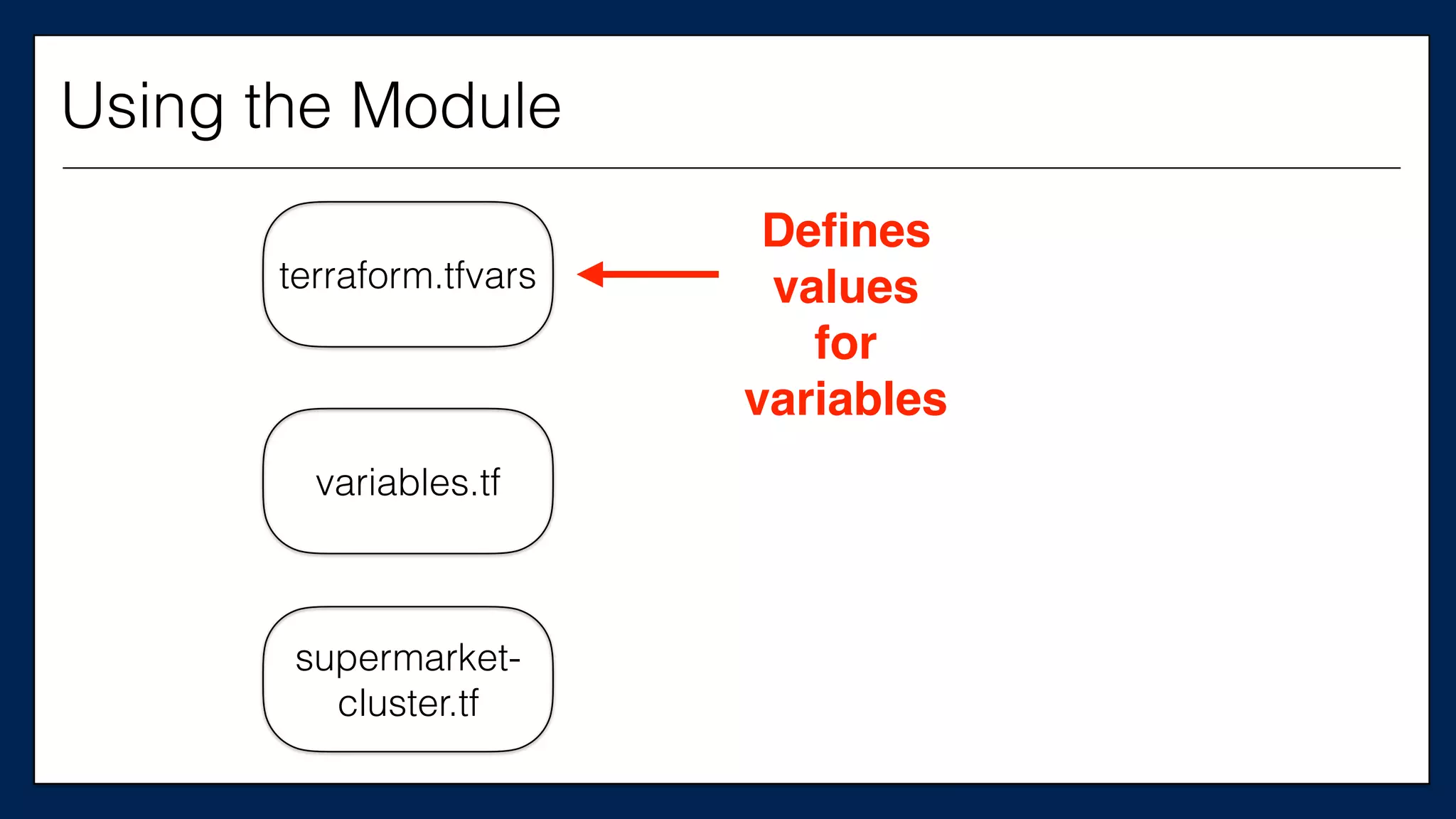
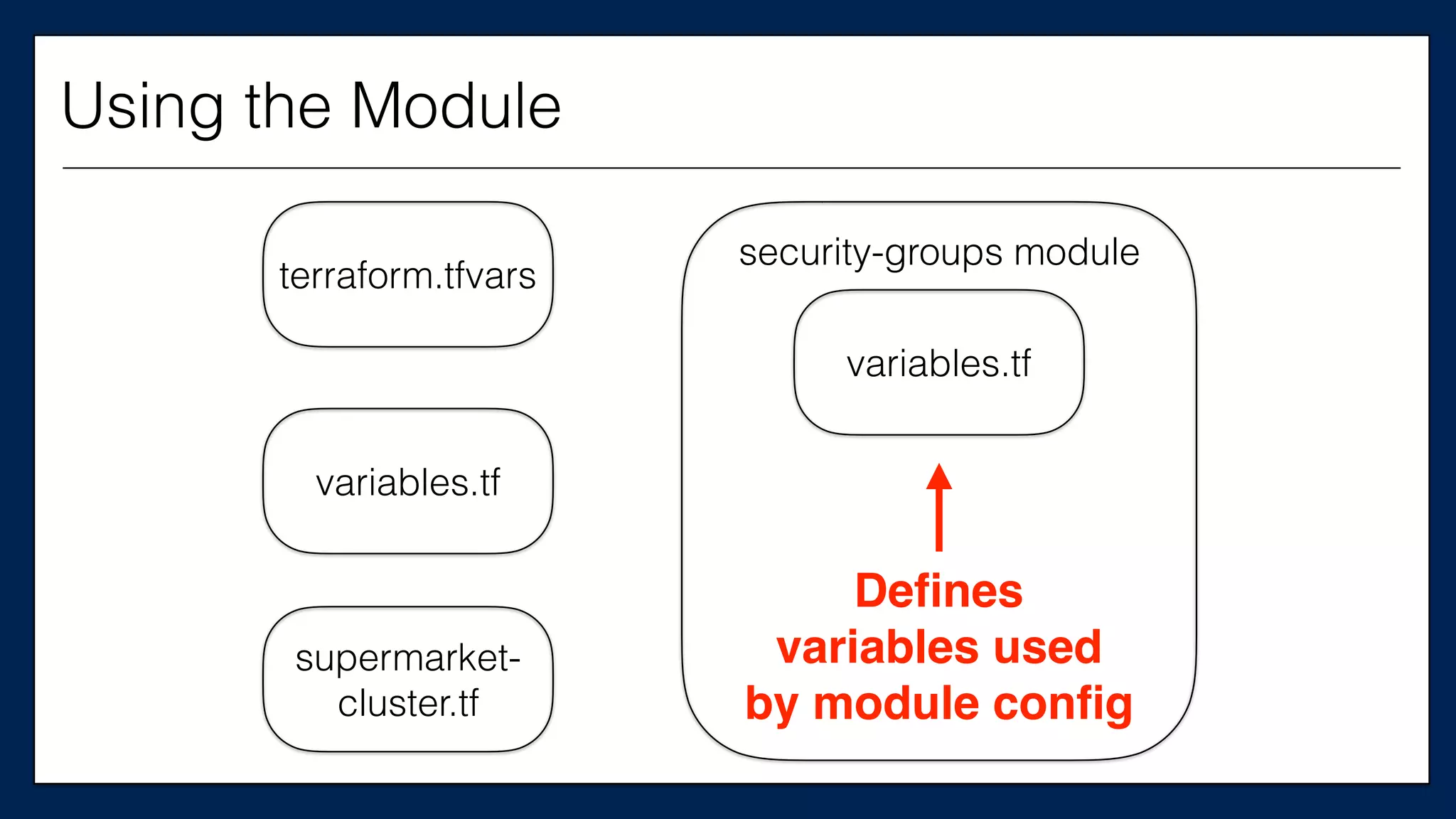
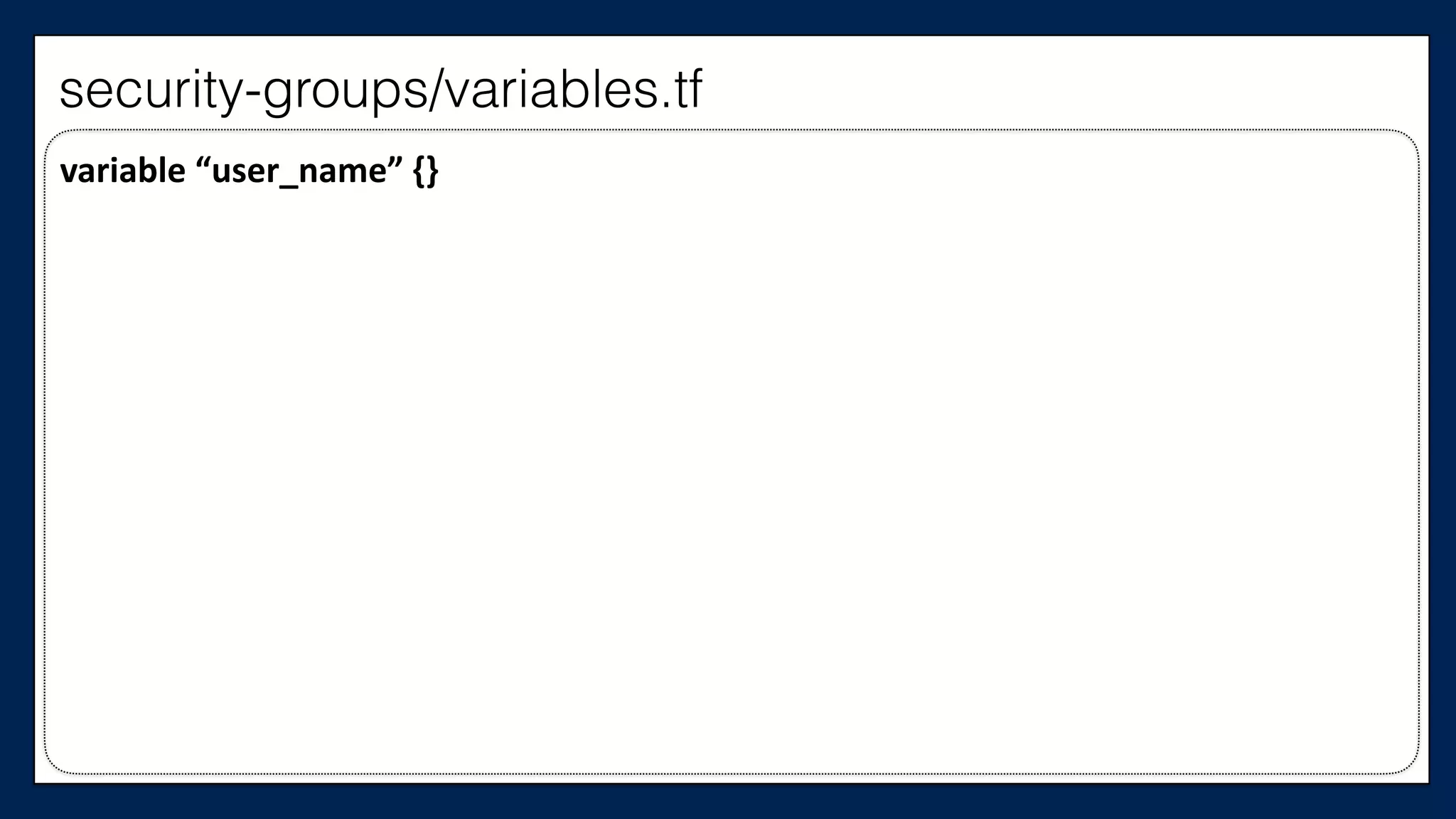
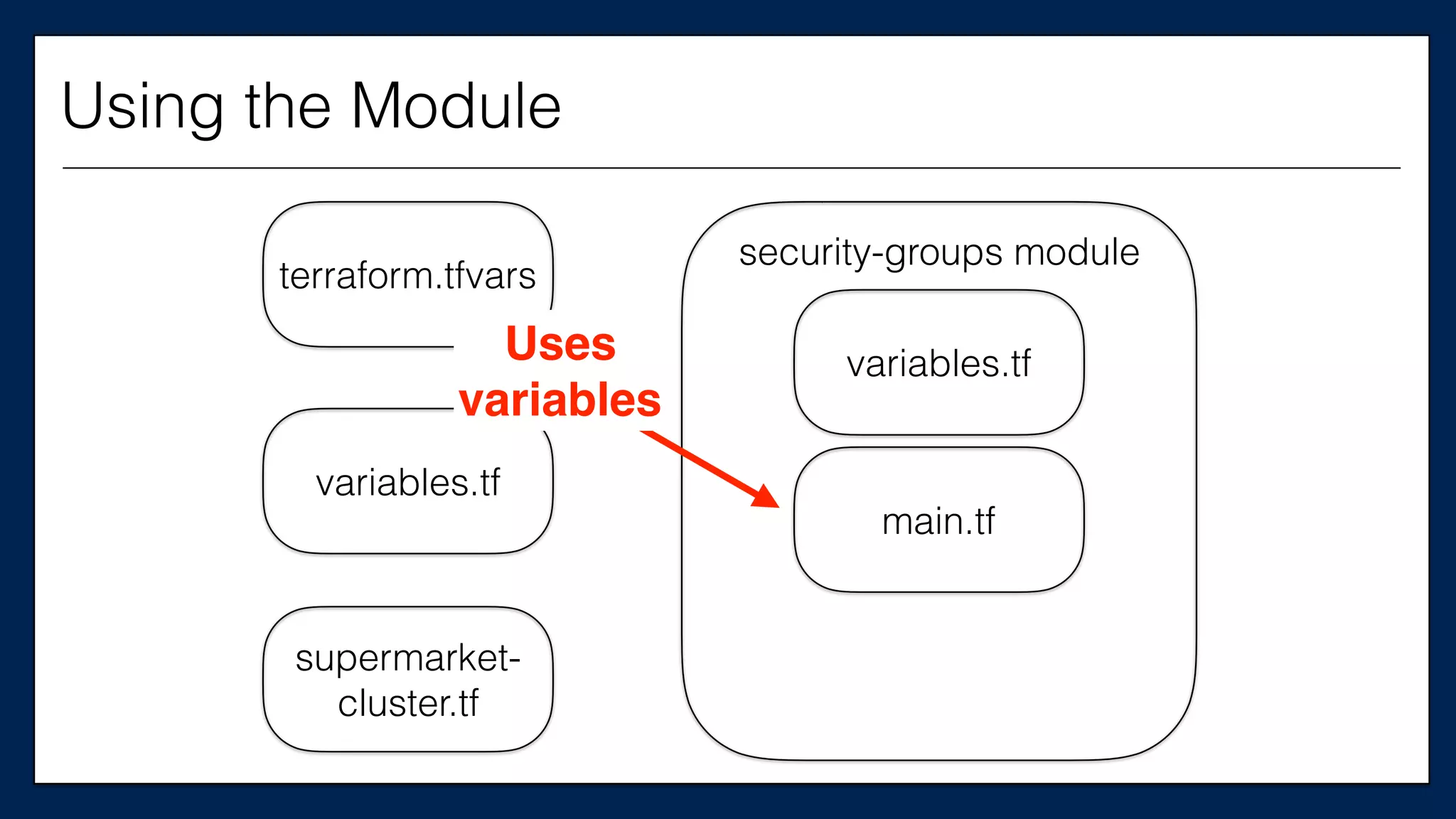
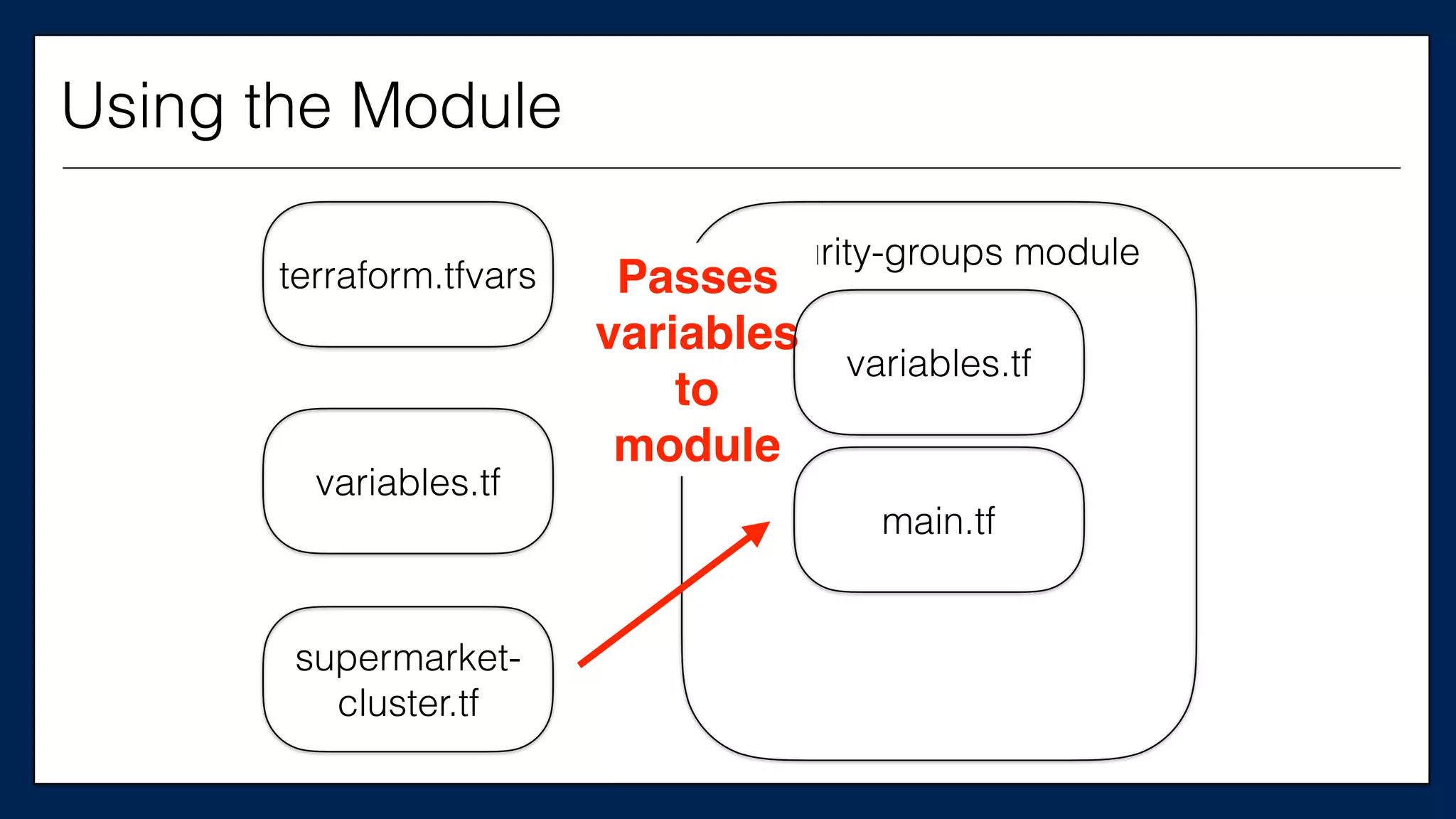
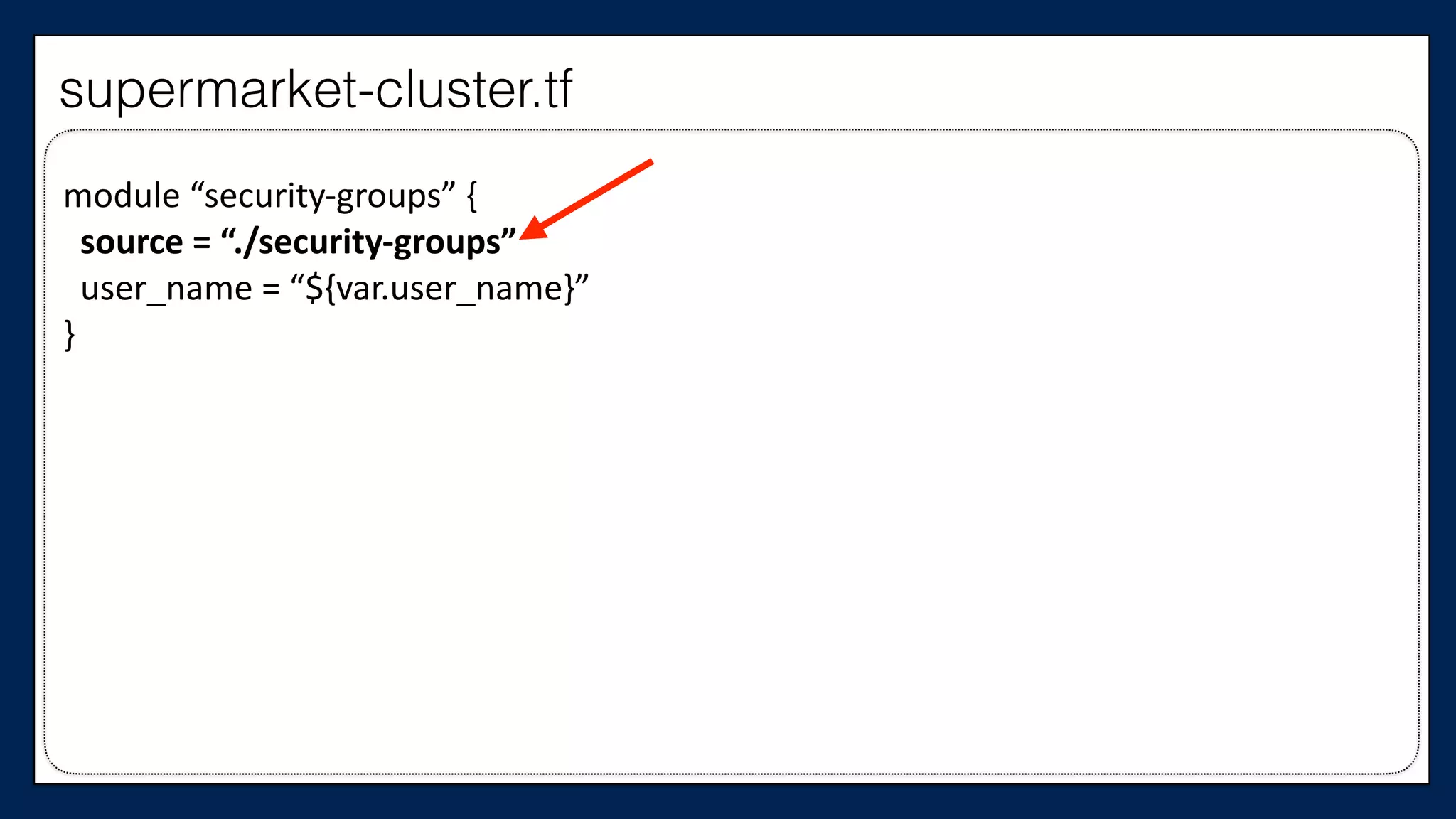
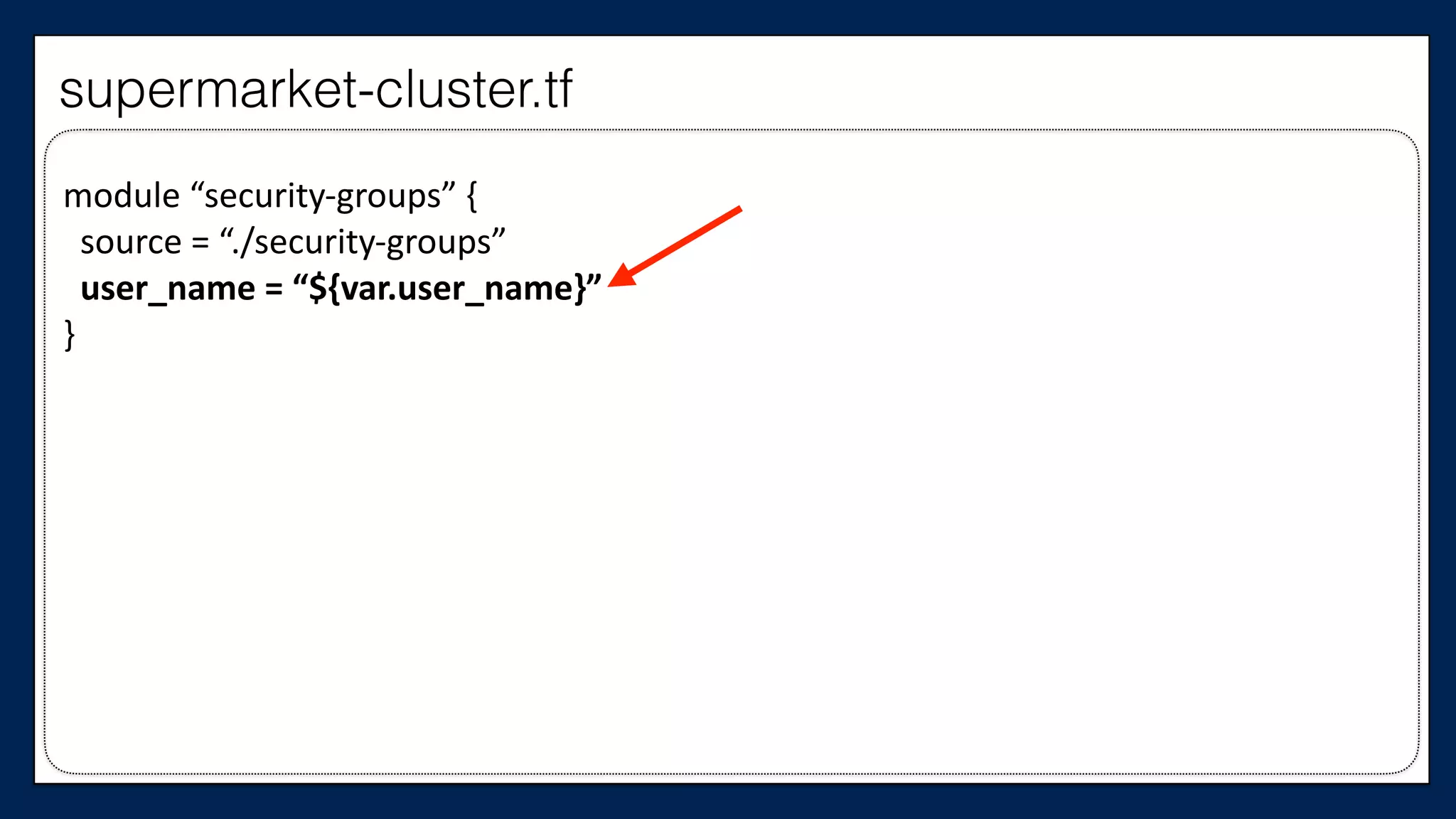
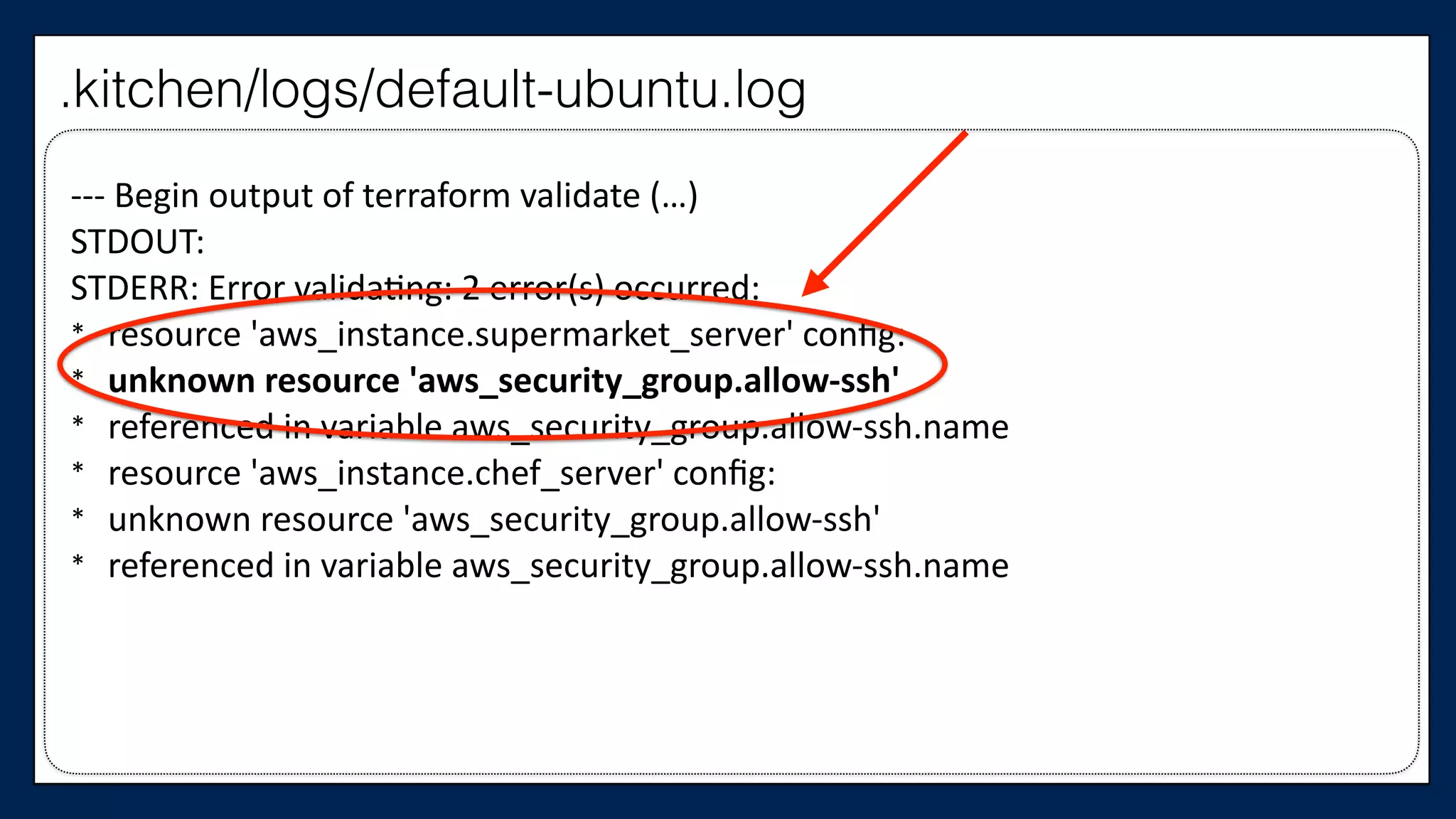
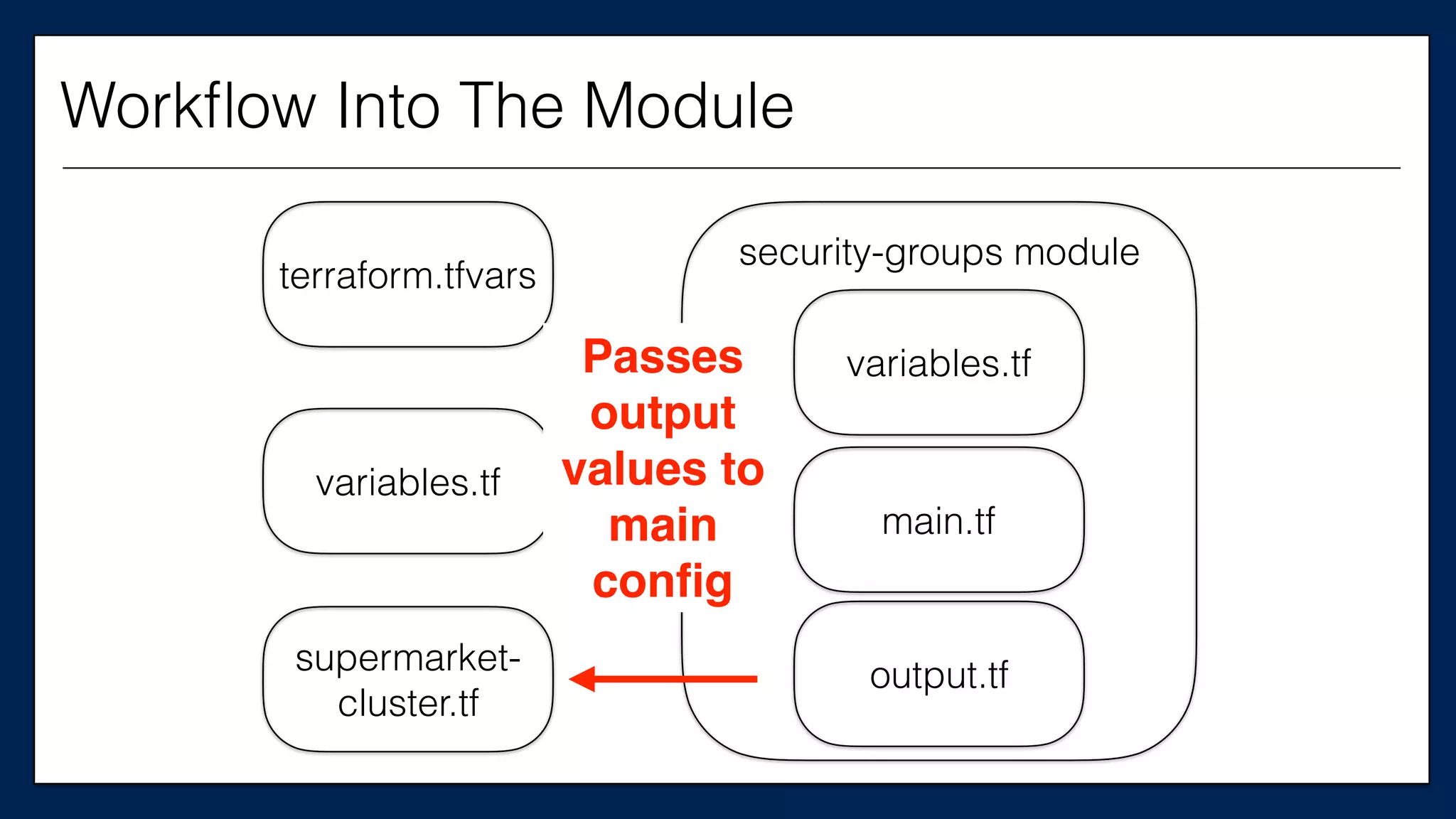
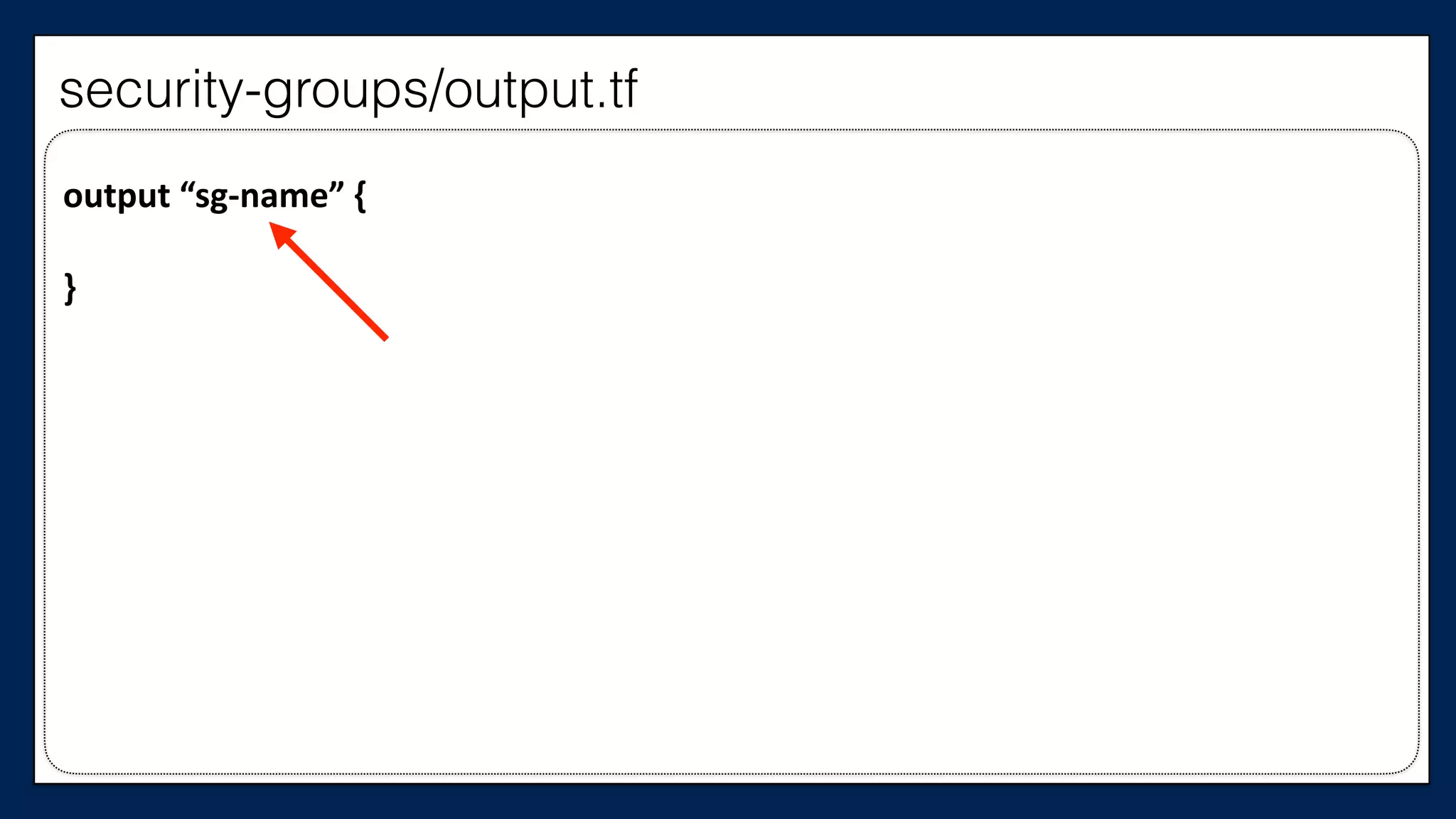
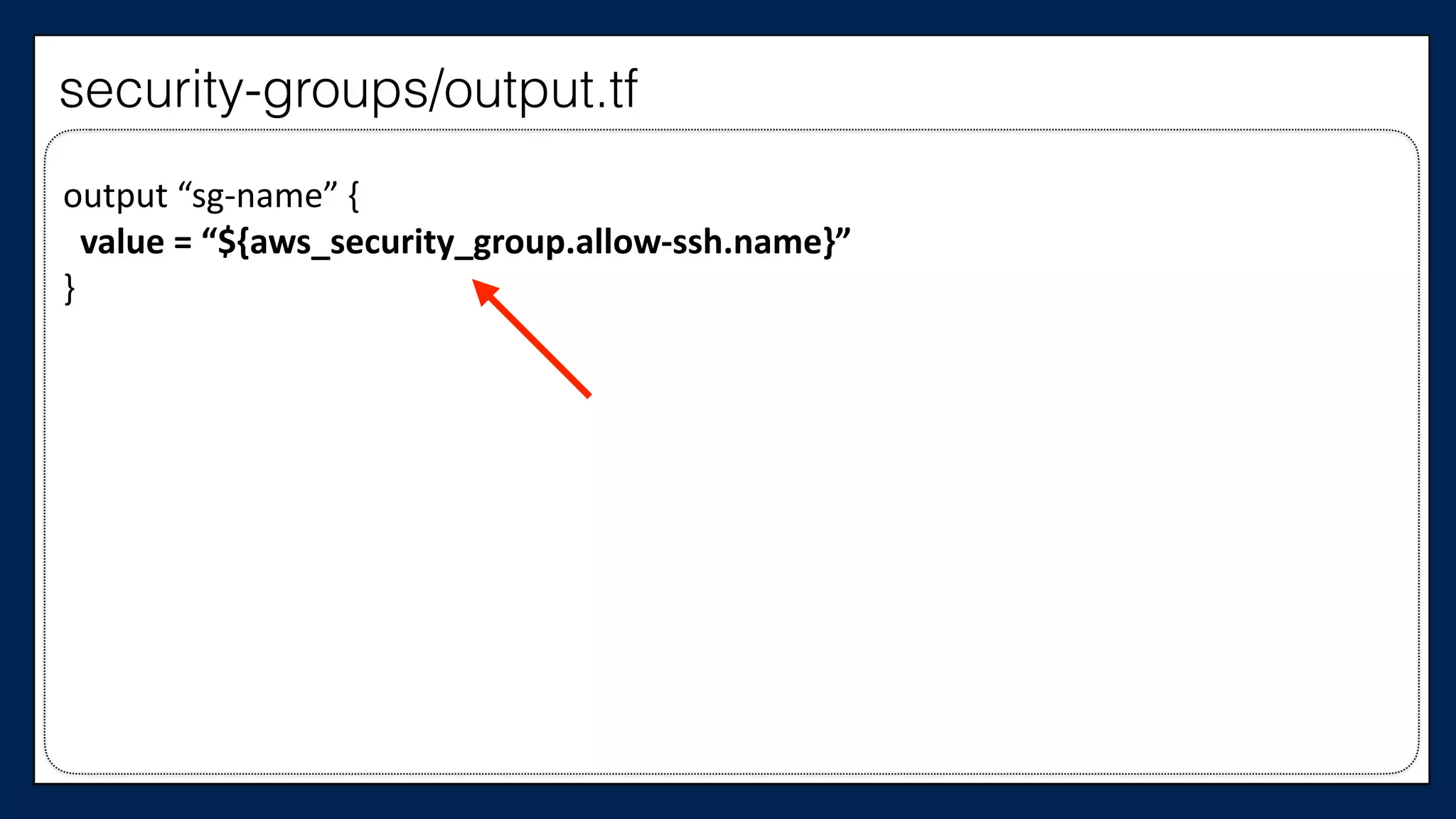

![…
resource
“aws_instance”
“chef_server”
{
ami
=
“${var.ami}”
instance_type
=
“${var.instance_type}”
key_name
=
“${var.key_name}”
tags
{
Name
=
“dev-‐chef-‐server”
}
security_groups
=
[“${aws_security_group.allow-‐ssh.name}”]
(…)
}
…
This is the
Chef Server
supermarket-cluster.tf](https://image.slidesharecdn.com/refactoringinfradevopsdayschidraft3-160831163013/75/Refactoring-Infrastructure-Code-175-2048.jpg)
![…
resource
“aws_instance”
“chef_server”
{
ami
=
“${var.ami}”
instance_type
=
“${var.instance_type}”
key_name
=
“${var.key_name}”
tags
{
Name
=
“dev-‐chef-‐server”
}
security_groups
=
[“${module.security-‐groups.sg-‐name}”]
(…)
}
…
This is the
Chef Server
supermarket-cluster.tf](https://image.slidesharecdn.com/refactoringinfradevopsdayschidraft3-160831163013/75/Refactoring-Infrastructure-Code-176-2048.jpg)
![…
resource
“aws_instance”
“supermarket_server”
{
ami
=
“${var.ami}”
instance_type
=
“${var.instance_type}”
key_name
=
“${var.key_name}”
tags
{
Name
=
“dev-‐supermarket-‐server”
}
security_groups
=
[“${aws_security_group.allow-‐ssh-‐name}”]
(…)
}
…
This is the
Supermarket
Server
supermarket-cluster.tf](https://image.slidesharecdn.com/refactoringinfradevopsdayschidraft3-160831163013/75/Refactoring-Infrastructure-Code-177-2048.jpg)
![…
resource
“aws_instance”
“supermarket_server”
{
ami
=
“${var.ami}”
instance_type
=
“${var.instance_type}”
key_name
=
“${var.key_name}”
tags
{
Name
=
“dev-‐supermarket-‐server”
}
security_groups
=
[“${module.security-‐groups.sg-‐name}”]
(…)
}
…
This is the
Supermarket
Server
supermarket-cluster.tf](https://image.slidesharecdn.com/refactoringinfradevopsdayschidraft3-160831163013/75/Refactoring-Infrastructure-Code-178-2048.jpg)