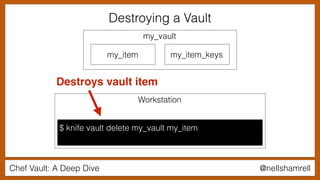
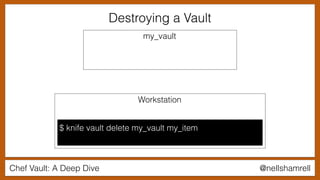
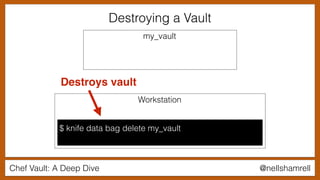
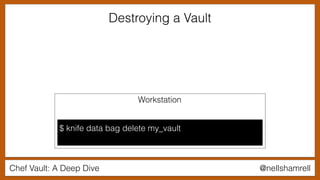
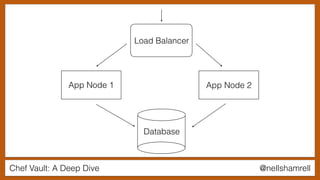
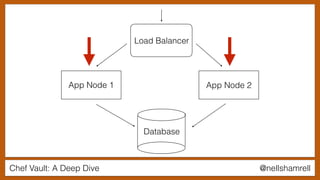
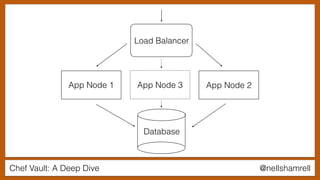
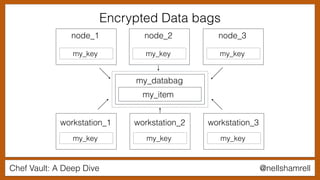
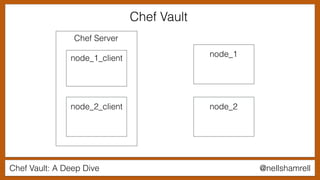
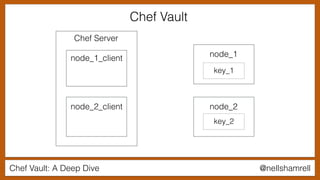
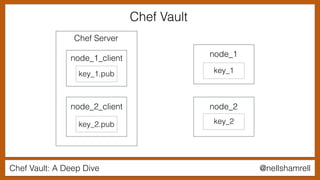
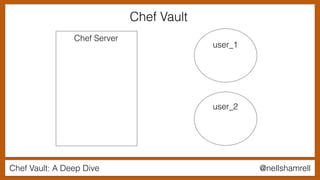
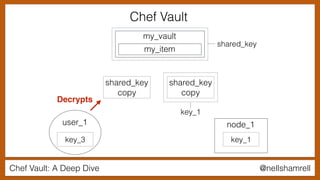
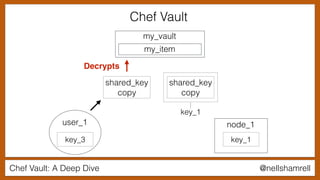
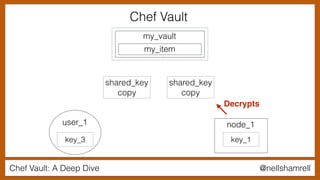
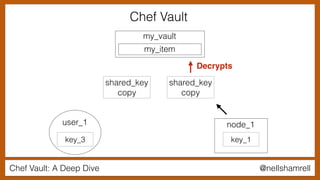
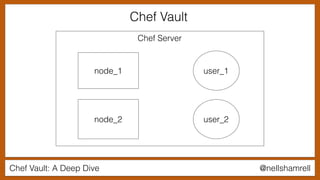
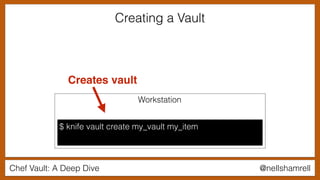
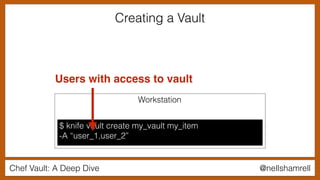
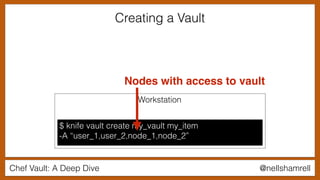
The document discusses Chef Vault, a tool for managing encrypted information across nodes, emphasizing the balance between security and usability. It covers its functionality, including creating, editing, and destroying vaults, as well as key management challenges like key rotation and user access. Alternatives to Chef Vault, like Hashicorp Vault and Citadel, are also mentioned, highlighting different use case considerations in selecting a secrets management tool.



























![Chef Vault: A Deep Dive @nellshamrell
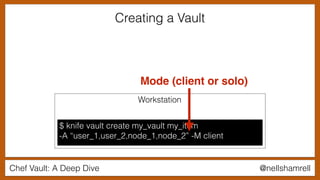
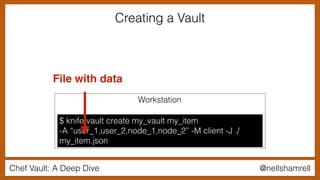
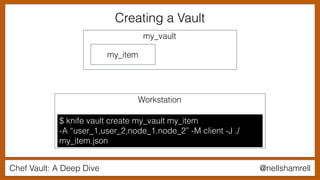
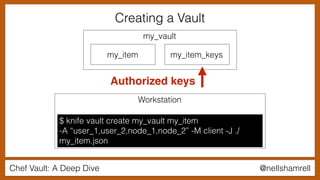
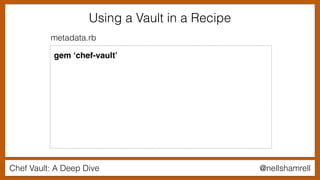
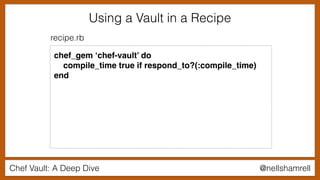
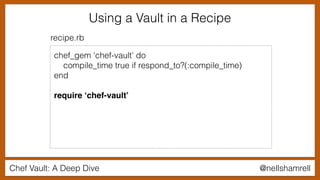
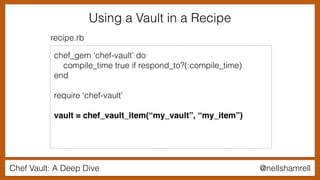
Using a Vault in a Recipe
chef_gem ‘chef-vault’ do
compile_time true if respond_to?(:compile_time)
end
require ‘chef-vault’
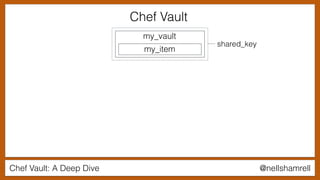
vault = chef_vault_item(“my_vault”, “my_item”)
node.set[‘database’][‘password’] = vault[‘password’]
recipe.rb](https://image.slidesharecdn.com/chefvaultfinal-170524205010/85/Chef-Vault-A-Deep-Dive-81-320.jpg)