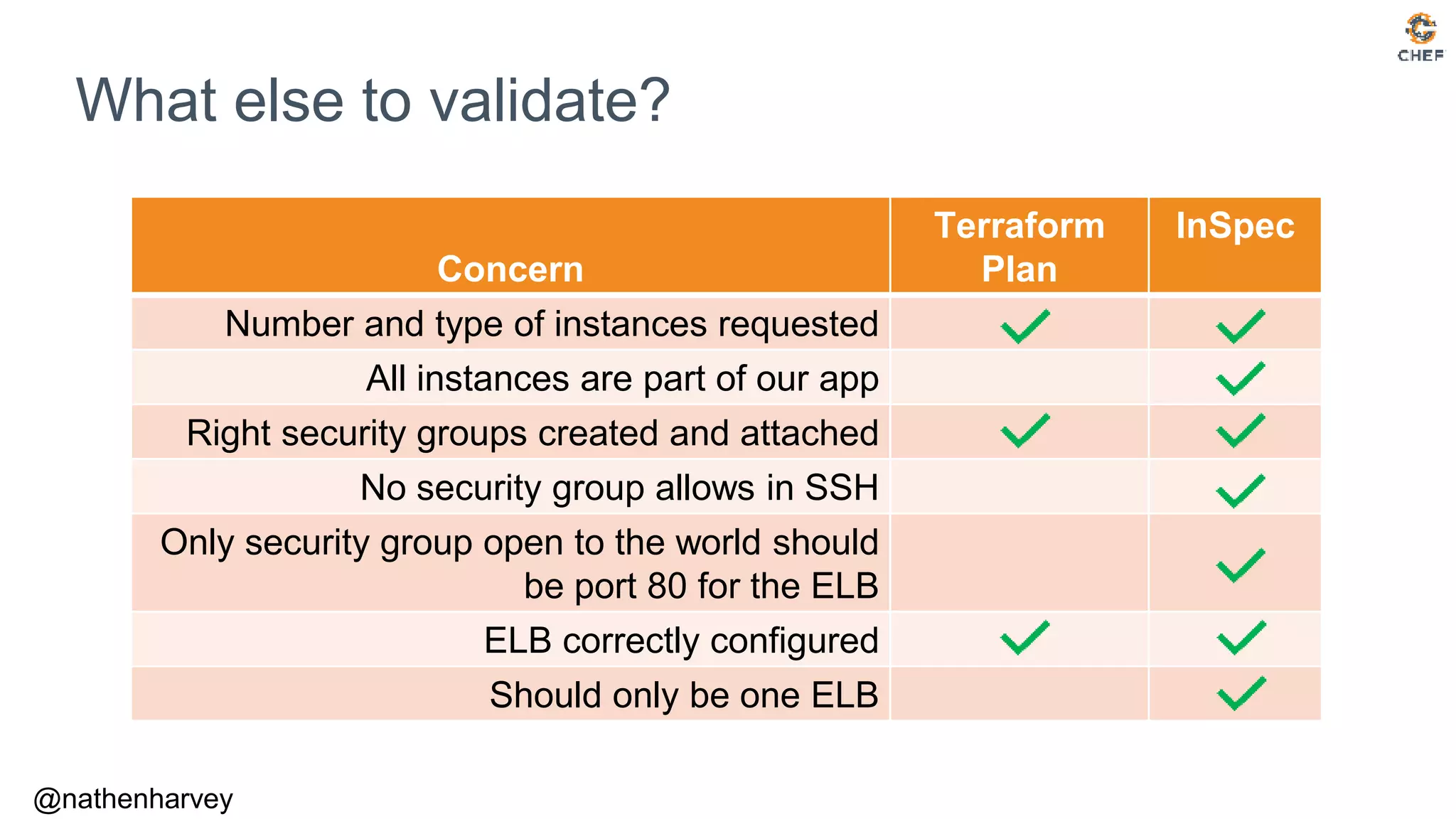
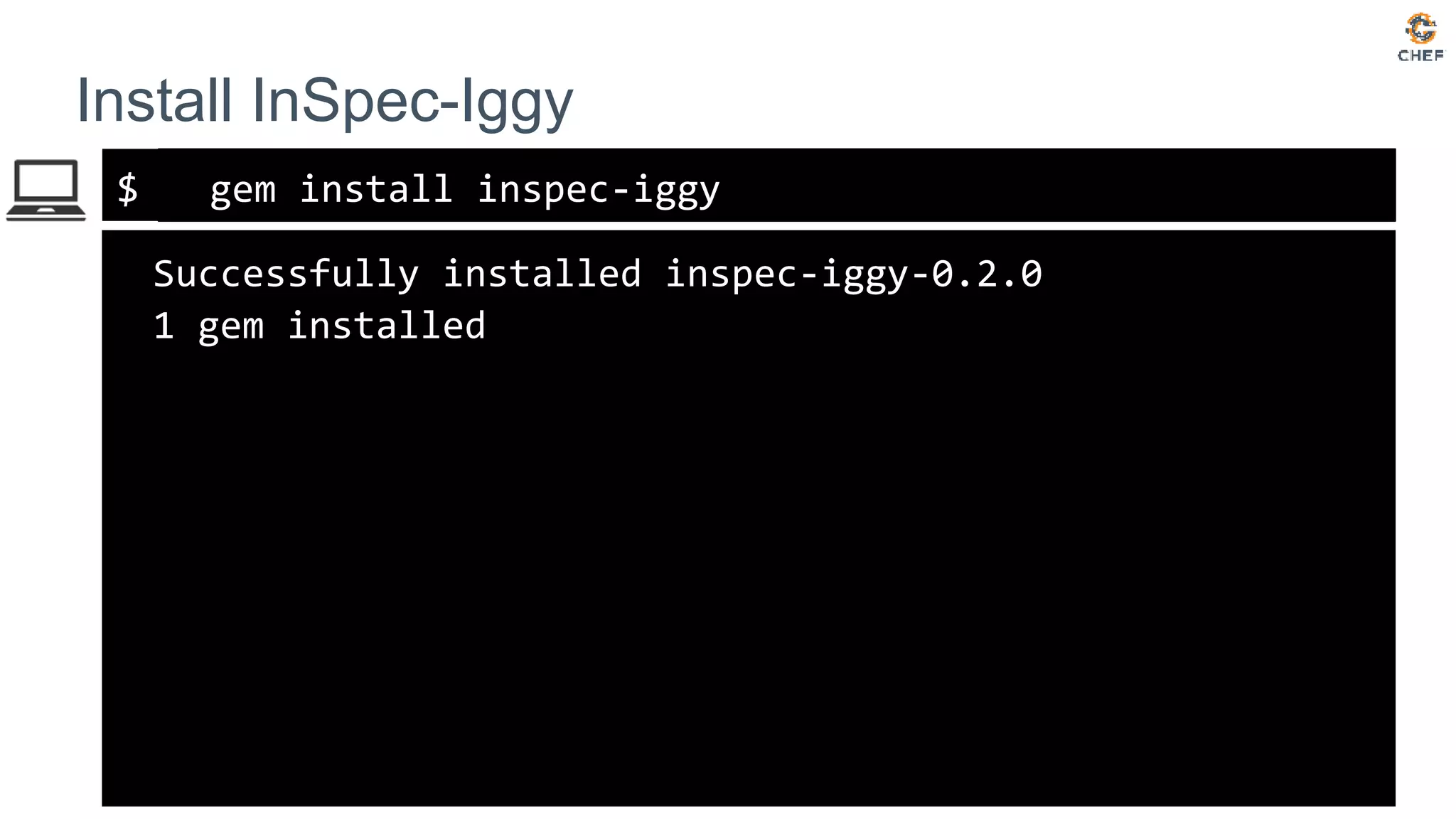
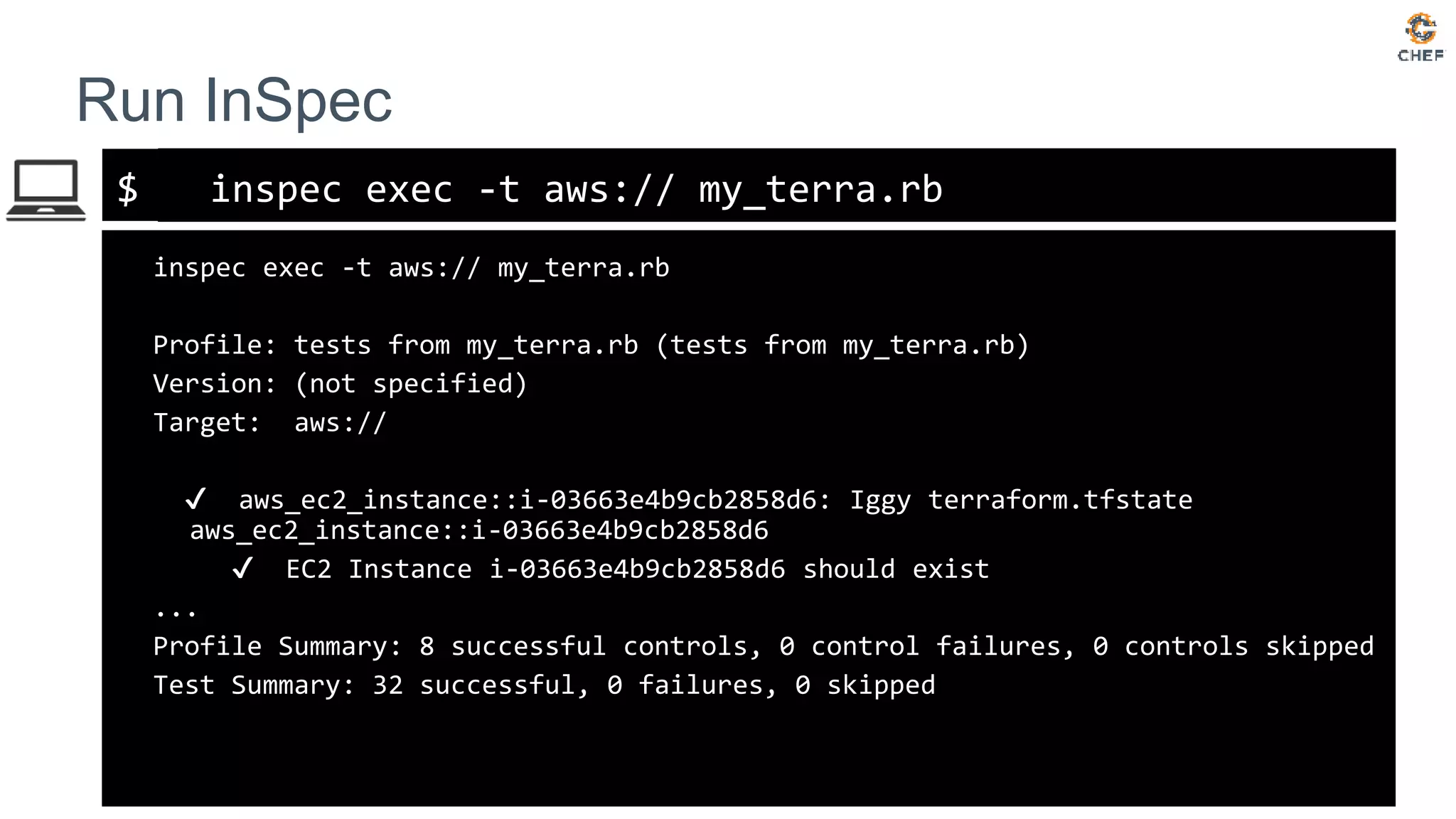
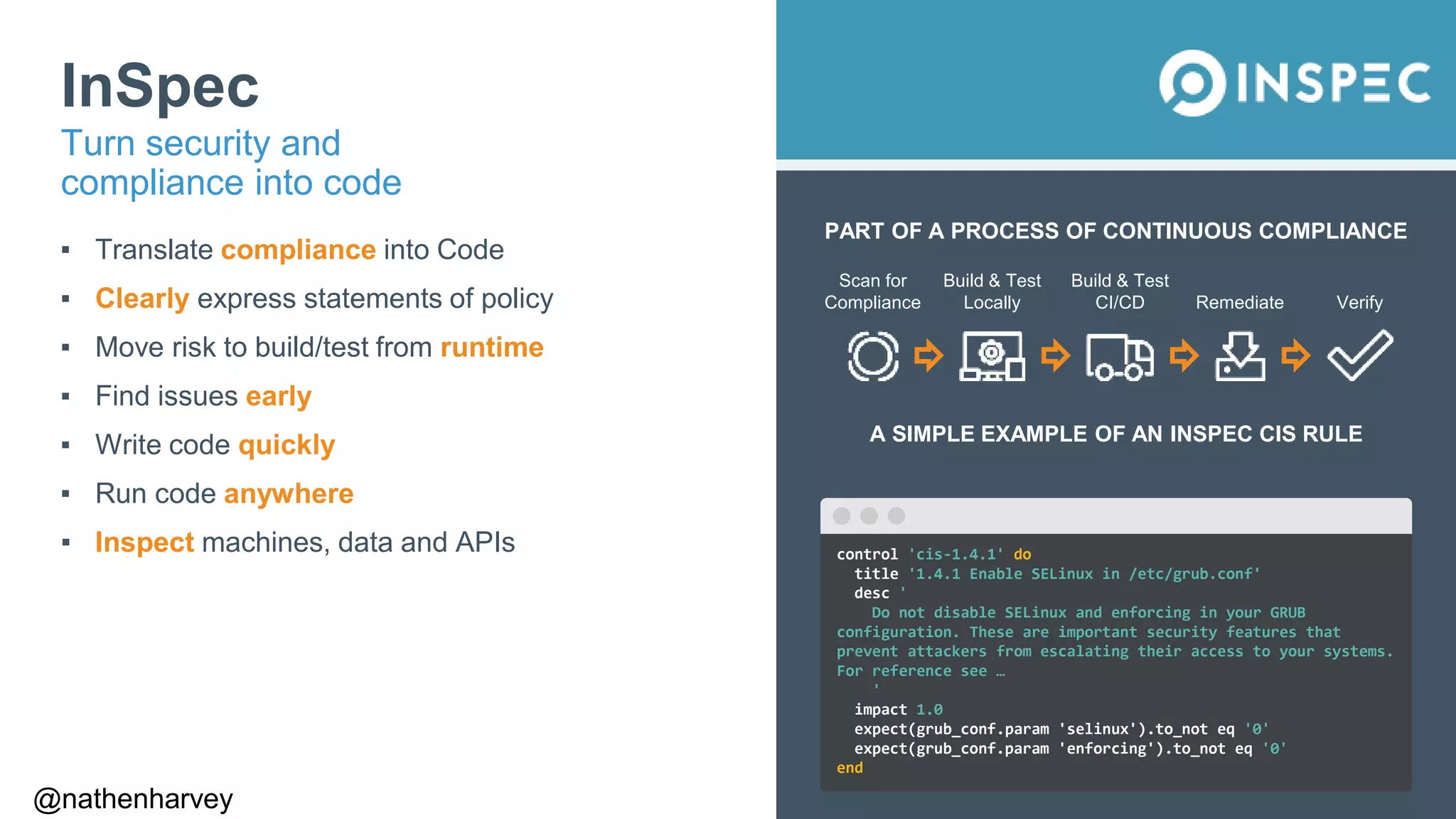
The document discusses how to test Terraform configurations for deploying infrastructure on AWS, advocating for infrastructure as code. It describes specific Terraform resources like EC2 instances and security groups, and emphasizes the importance of continuous compliance through tools like InSpec. Additionally, it outlines the process of using InSpec for auditing security groups and ensuring configurations meet defined policies.

![@nathenharvey
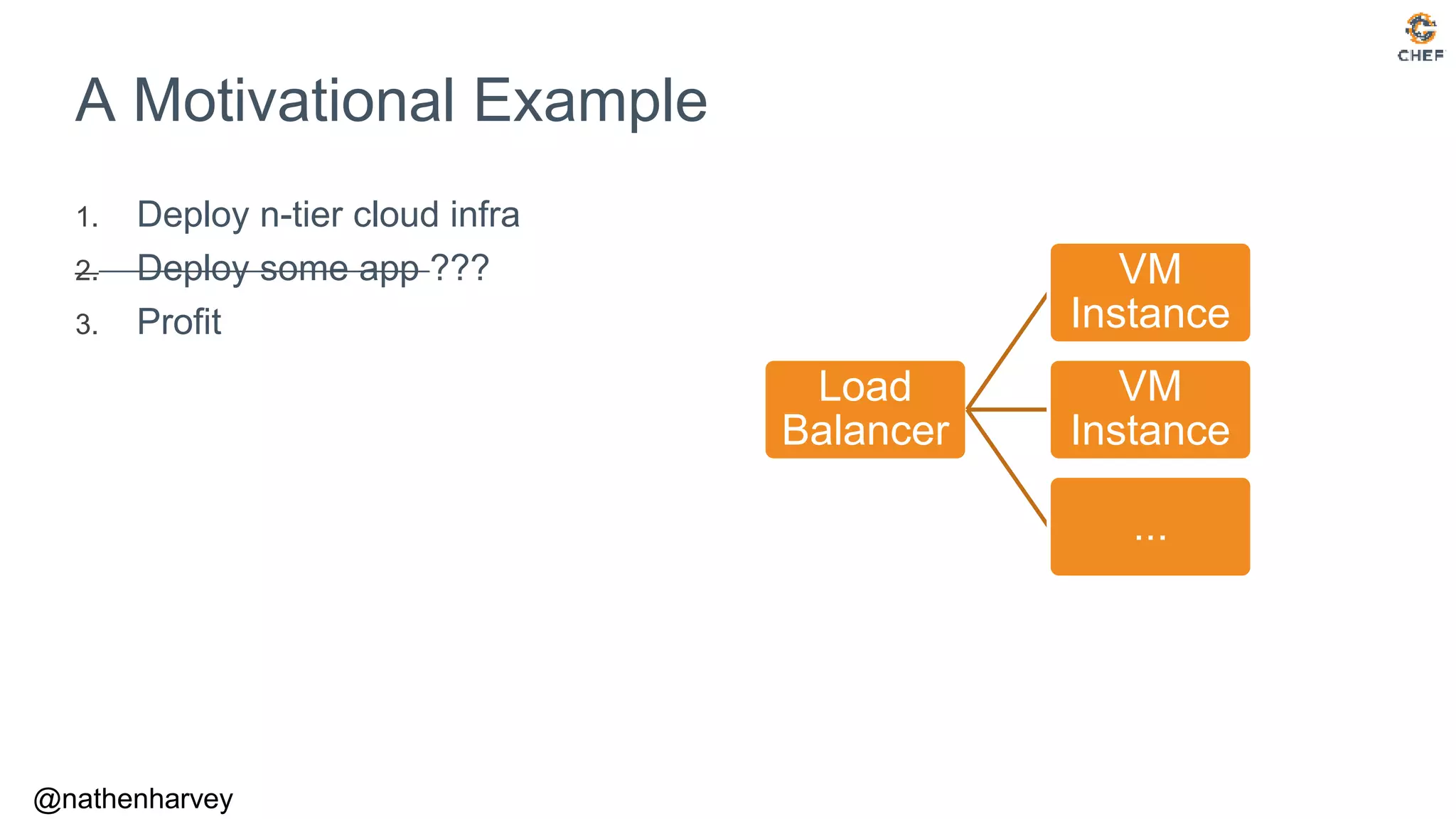
Terraform on AWS: Define an Instance (VM)
resource "aws_instance" "web" {
count = 3
instance_type = "t2.micro"
ami = "${lookup(var.aws_amis, var.aws_region)}"
key_name = "${var.key_name}"
subnet_id = "${aws_subnet.default.id}"
vpc_security_group_ids = [
"${aws_security_group.lb_to_webservers.id}",
"${aws_security_group.ssh_from_office.id}",
]
...
}](https://image.slidesharecdn.com/testing-terraform-180621135054/75/Testing-Terraform-6-2048.jpg)
![@nathenharvey
Terraform on AWS: Define Load Balancer (ELB)
resource "aws_elb" "web" {
name = "testing-terraform-elb"
subnets = ["${aws_subnet.default.id}"]
security_groups = [
"${aws_security_group.world_to_elb.id}",
"${aws_security_group.lb_to_webservers.id}",
]
instances = ["${aws_instance.web.*.id}"]
listener {
instance_port = 80
instance_protocol = "http"
lb_port = 80
lb_protocol = "http"
}
}](https://image.slidesharecdn.com/testing-terraform-180621135054/75/Testing-Terraform-7-2048.jpg)
![@nathenharvey
Terraform on AWS: Define a Firewall Rule
resource "aws_security_group" "ssh_from_office" {
name = "testing-terraform-ssh"
vpc_id = "${aws_vpc.testing_terraform.id}"
# SSH access from special office addresses
ingress {
from_port = 22
to_port = 22
protocol = "tcp"
cidr_blocks = "${var.ssh_cidrs}"
}
# outbound internet access
egress {
from_port = 0
to_port = 0
protocol = "-1"
cidr_blocks = ["0.0.0.0/0"]
}
}](https://image.slidesharecdn.com/testing-terraform-180621135054/75/Testing-Terraform-8-2048.jpg)
![@nathenharvey
Terraform on AWS: Define a Firewall Rule
resource "aws_security_group" "ssh_from_office" {
name = "testing-terraform-ssh"
vpc_id = "${aws_vpc.testing_terraform.id}"
# SSH access from special office addresses
ingress {
from_port = 22
to_port = 22
protocol = "tcp"
cidr_blocks = "${var.ssh_cidrs}"
}
# outbound internet access
egress {
from_port = 0
to_port = 0
protocol = "-1"
cidr_blocks = ["0.0.0.0/0"]
}
}
variable "ssh_cidrs" {
default = [
"173.239.212.22/32",
"12.130.117.75/32"
]
}](https://image.slidesharecdn.com/testing-terraform-180621135054/75/Testing-Terraform-9-2048.jpg)
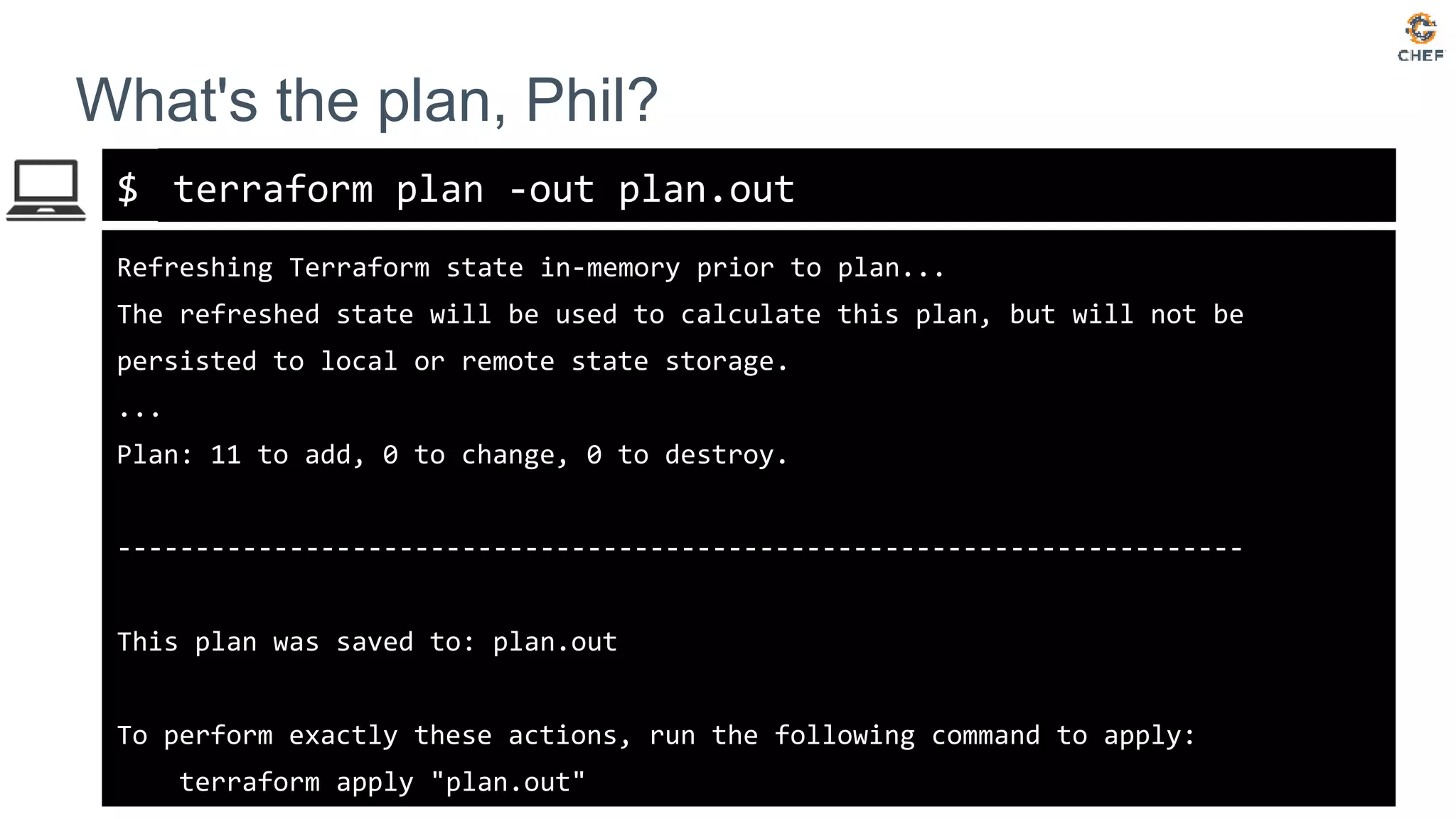
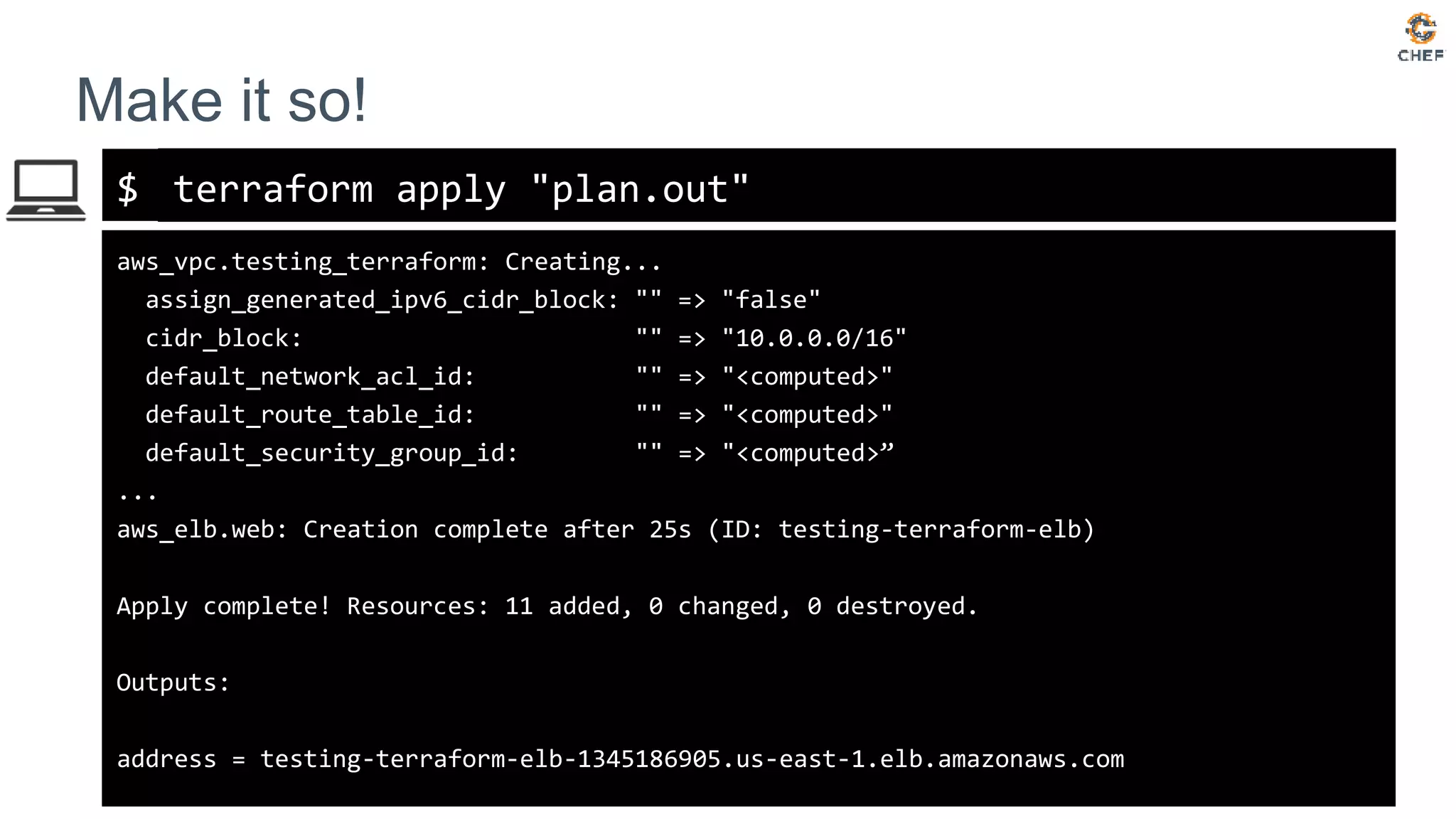
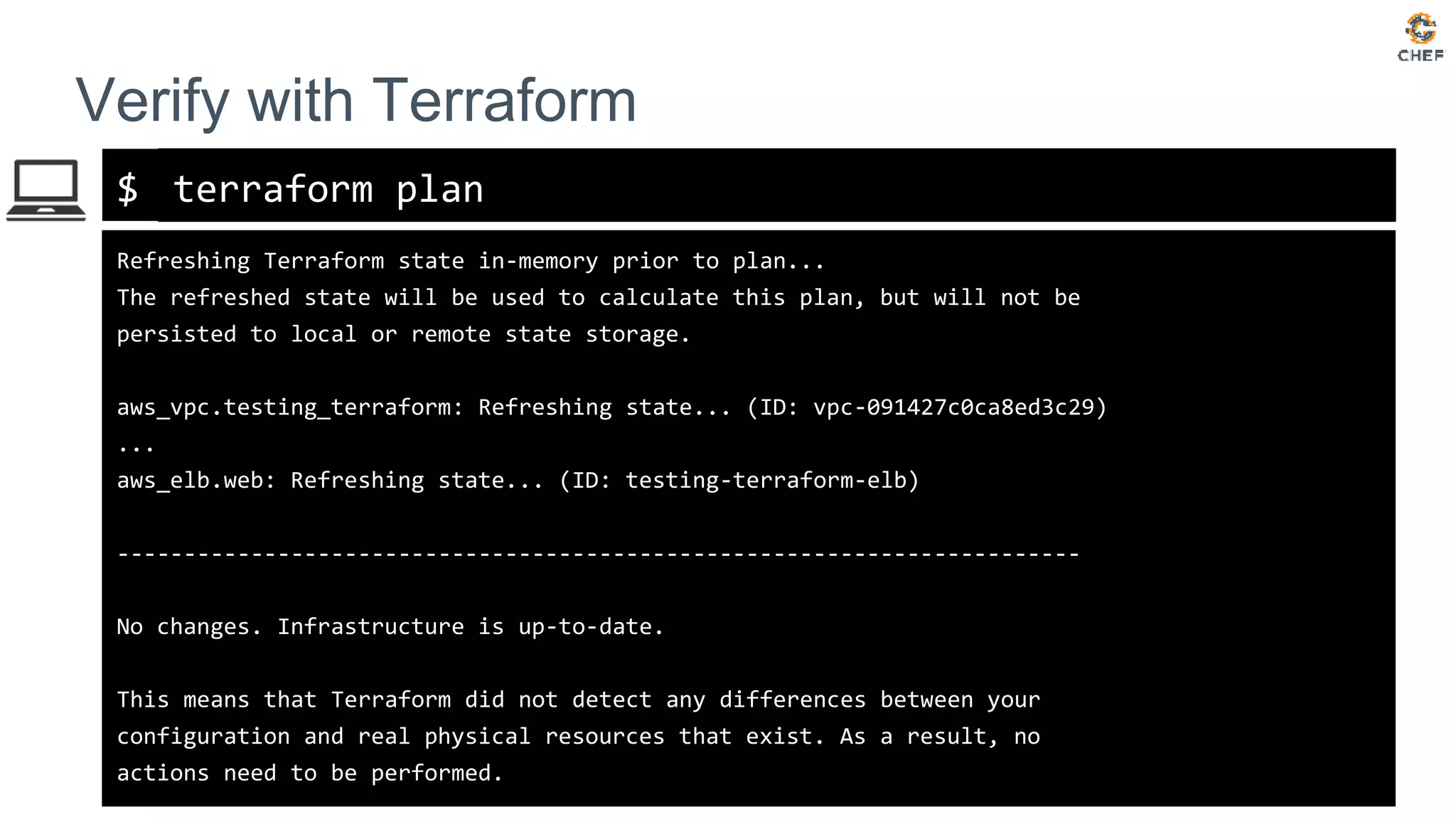

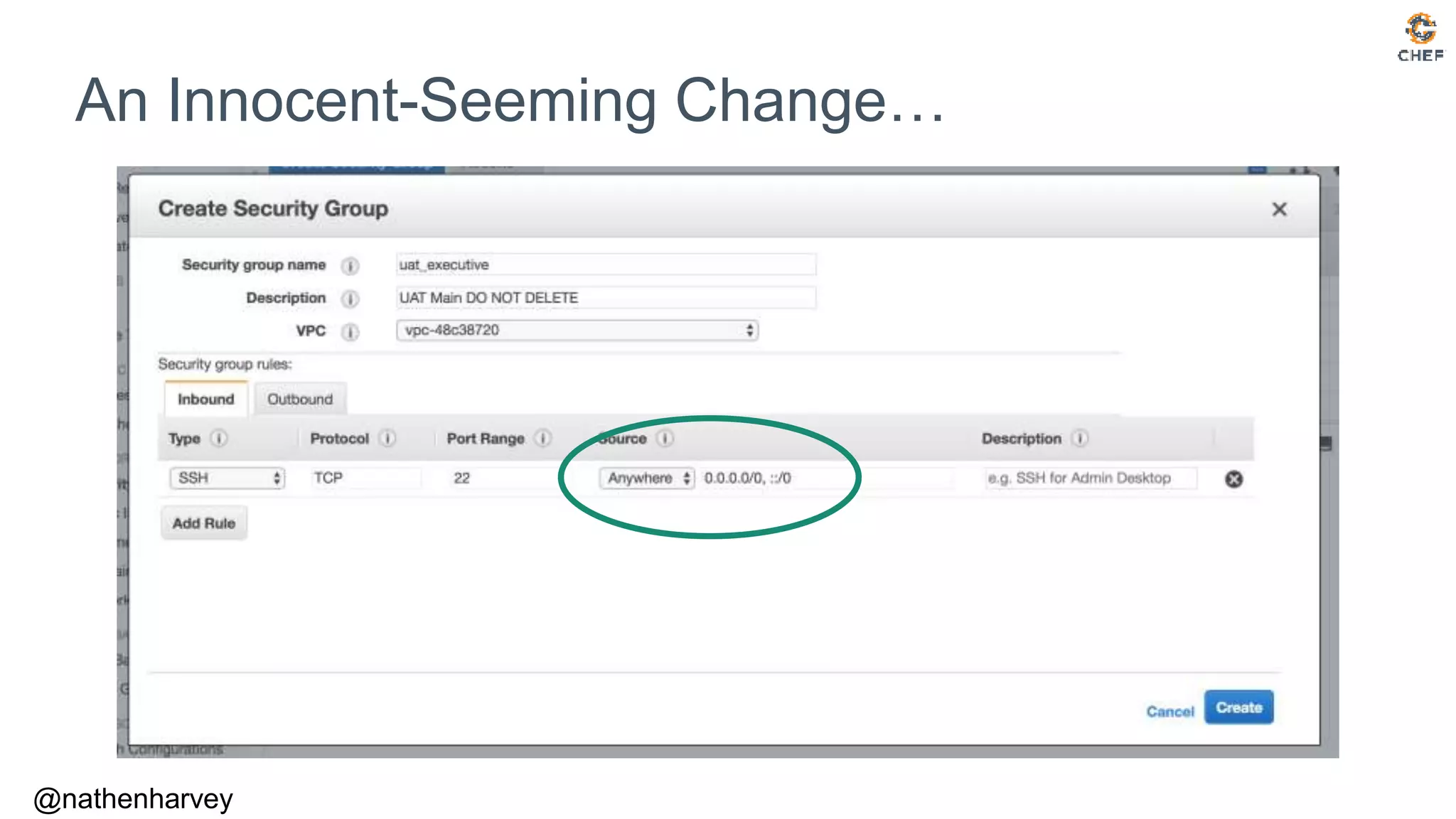
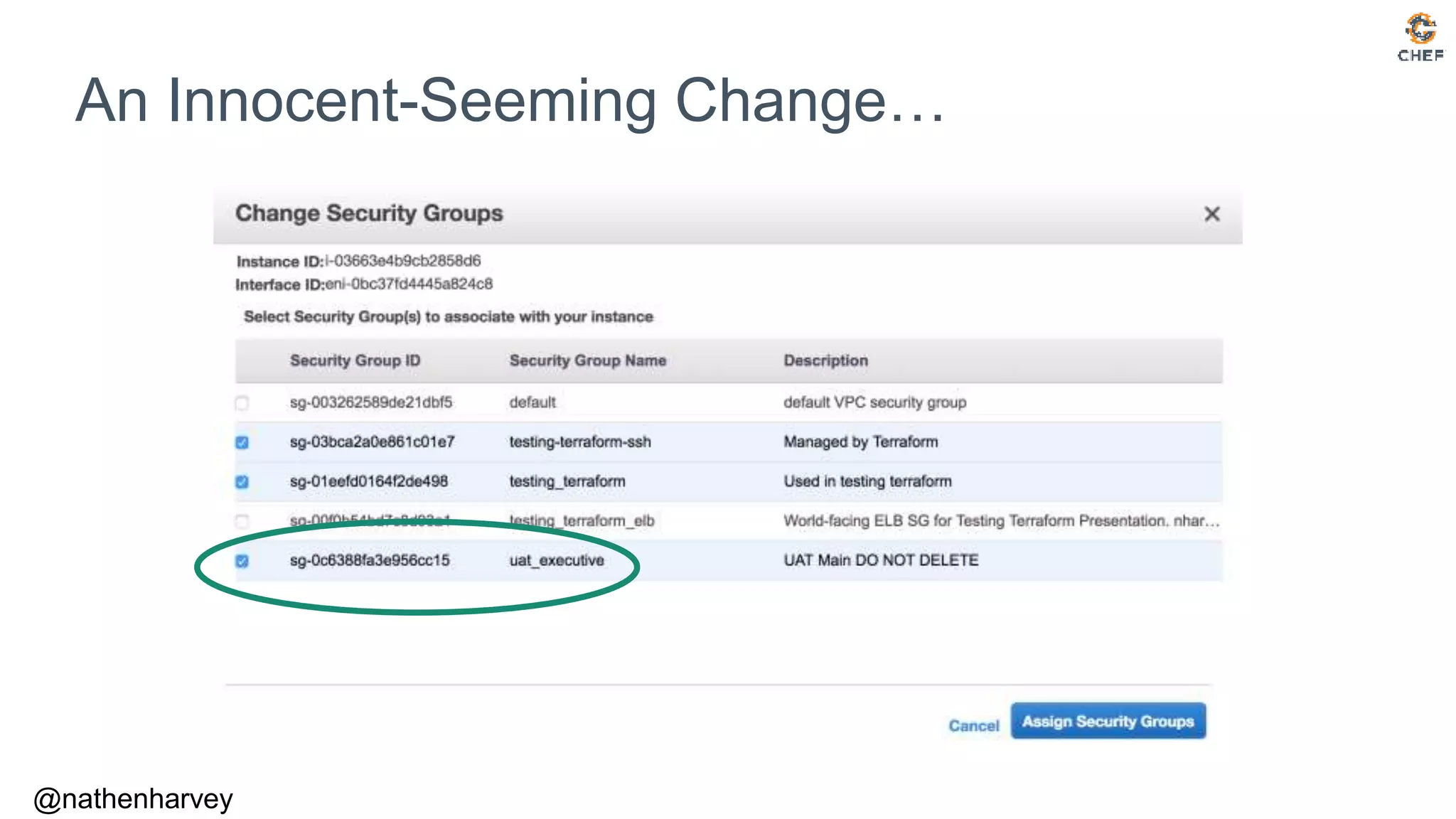
![$
Audit with Terraform
terraform plan
An execution plan has been generated and is shown below.
Resource actions are indicated with the following symbols:
~ update in-place
Terraform will perform the following actions:
~ aws_instance.web[0]
vpc_security_group_ids.#: "3" => "2"
vpc_security_group_ids.1298918294: "sg-01eefd0164f2de498" => "sg-01eefd0164f2de498"
vpc_security_group_ids.35497876: "sg-0c6388fa3e956cc15" => ""
vpc_security_group_ids.645334896: "sg-03bca2a0e861c01e7" => "sg-03bca2a0e861c01e7”
Plan: 0 to add, 1 to change, 0 to destroy.](https://image.slidesharecdn.com/testing-terraform-180621135054/75/Testing-Terraform-19-2048.jpg)
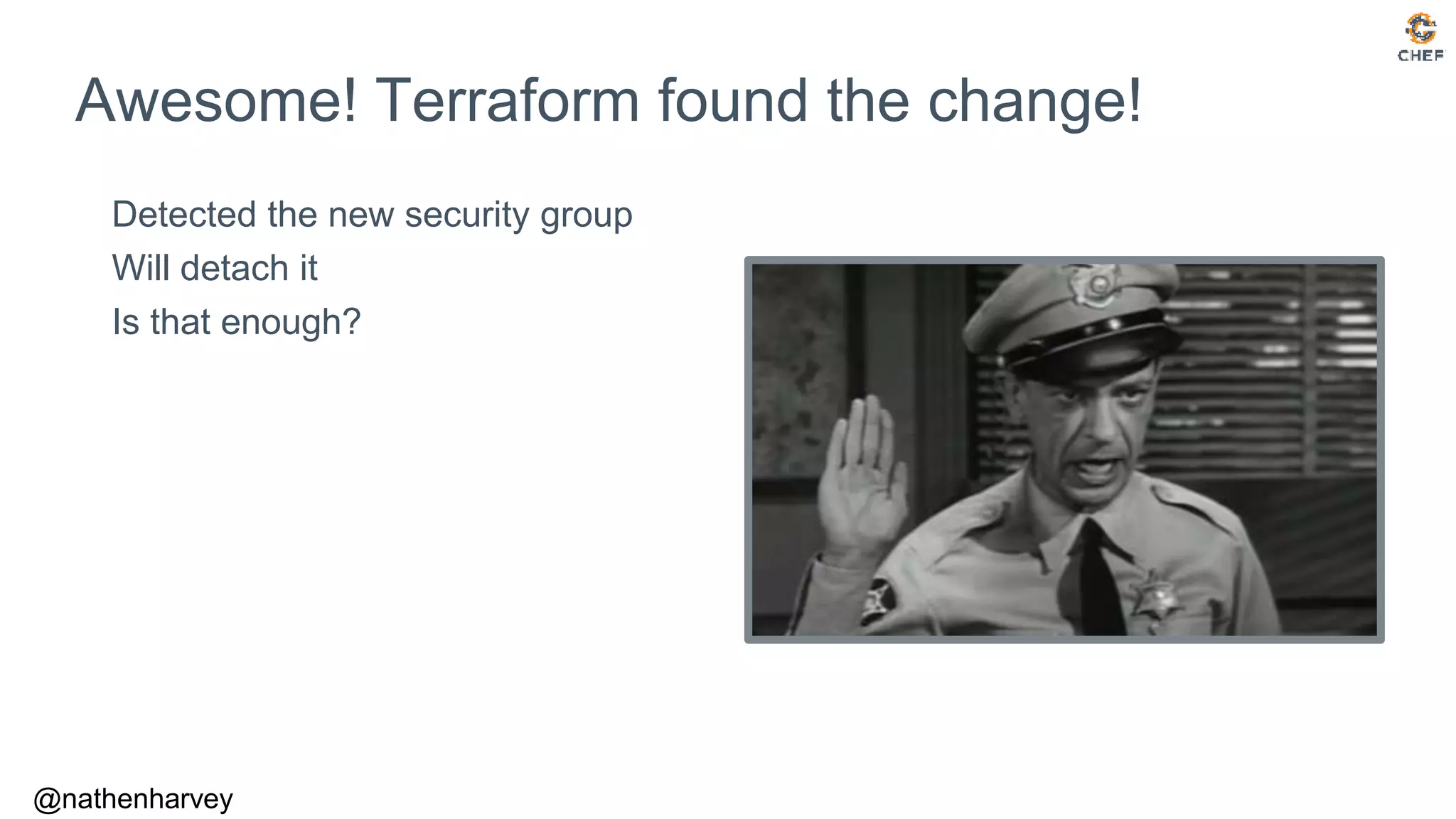



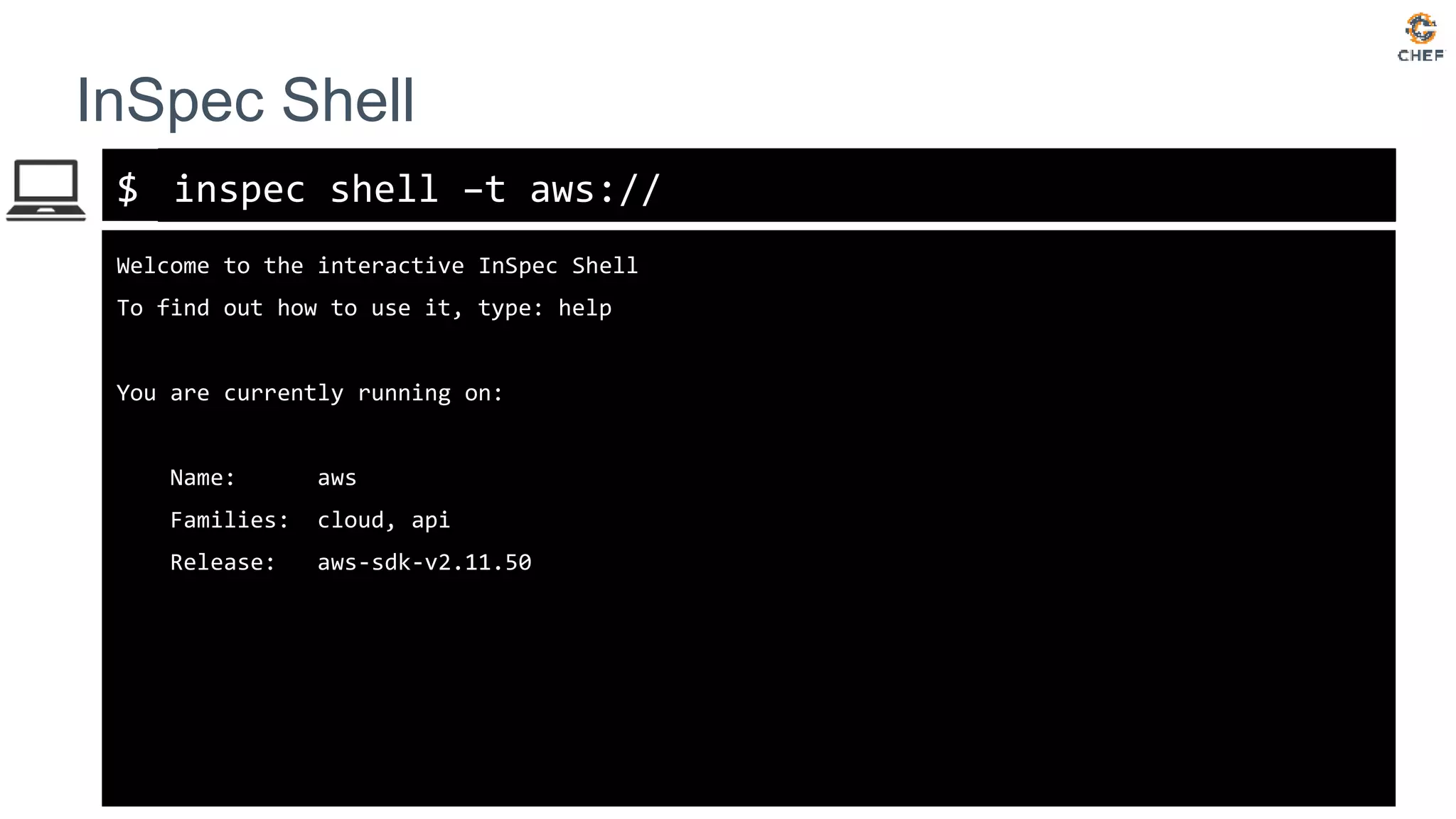
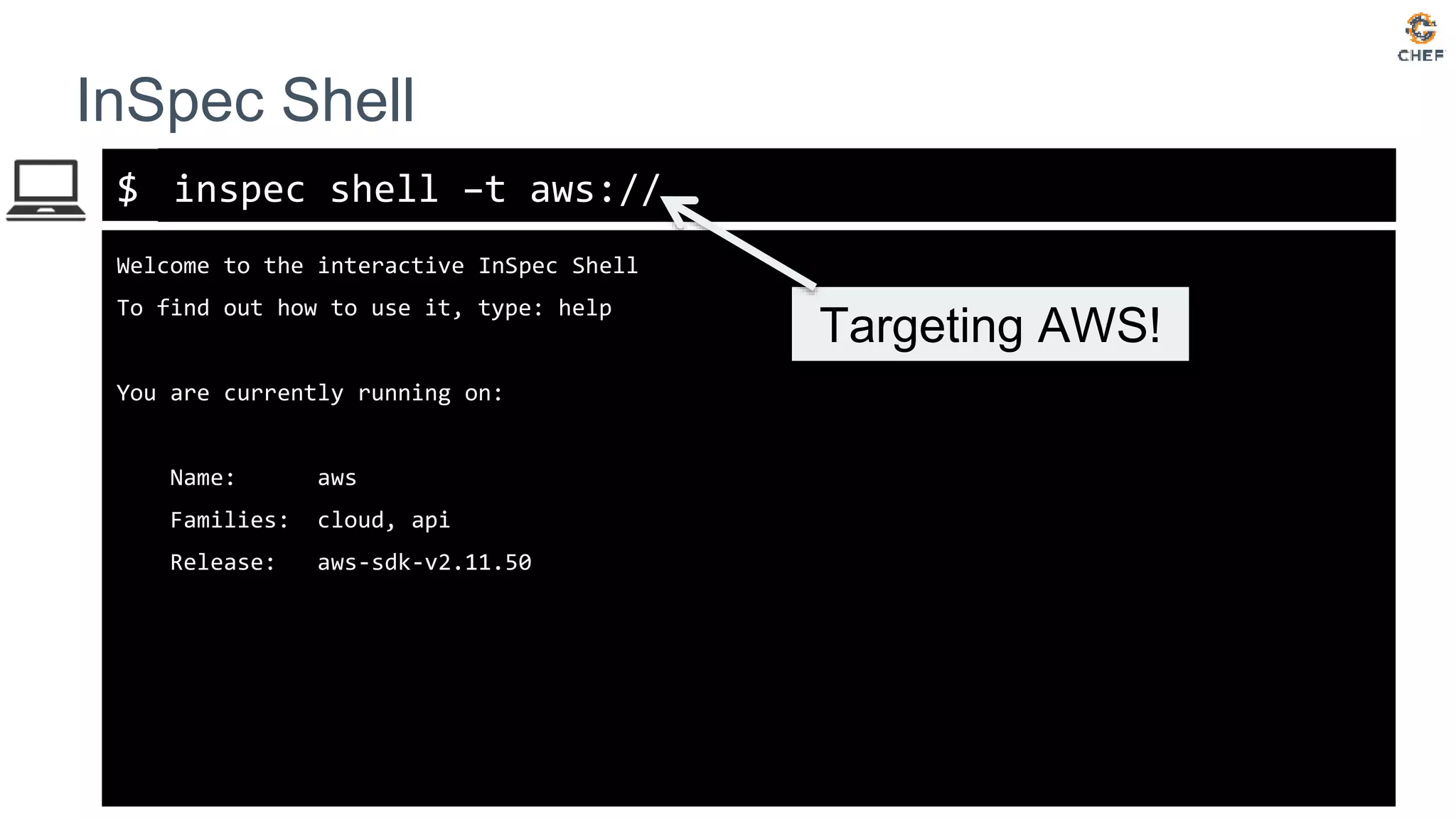
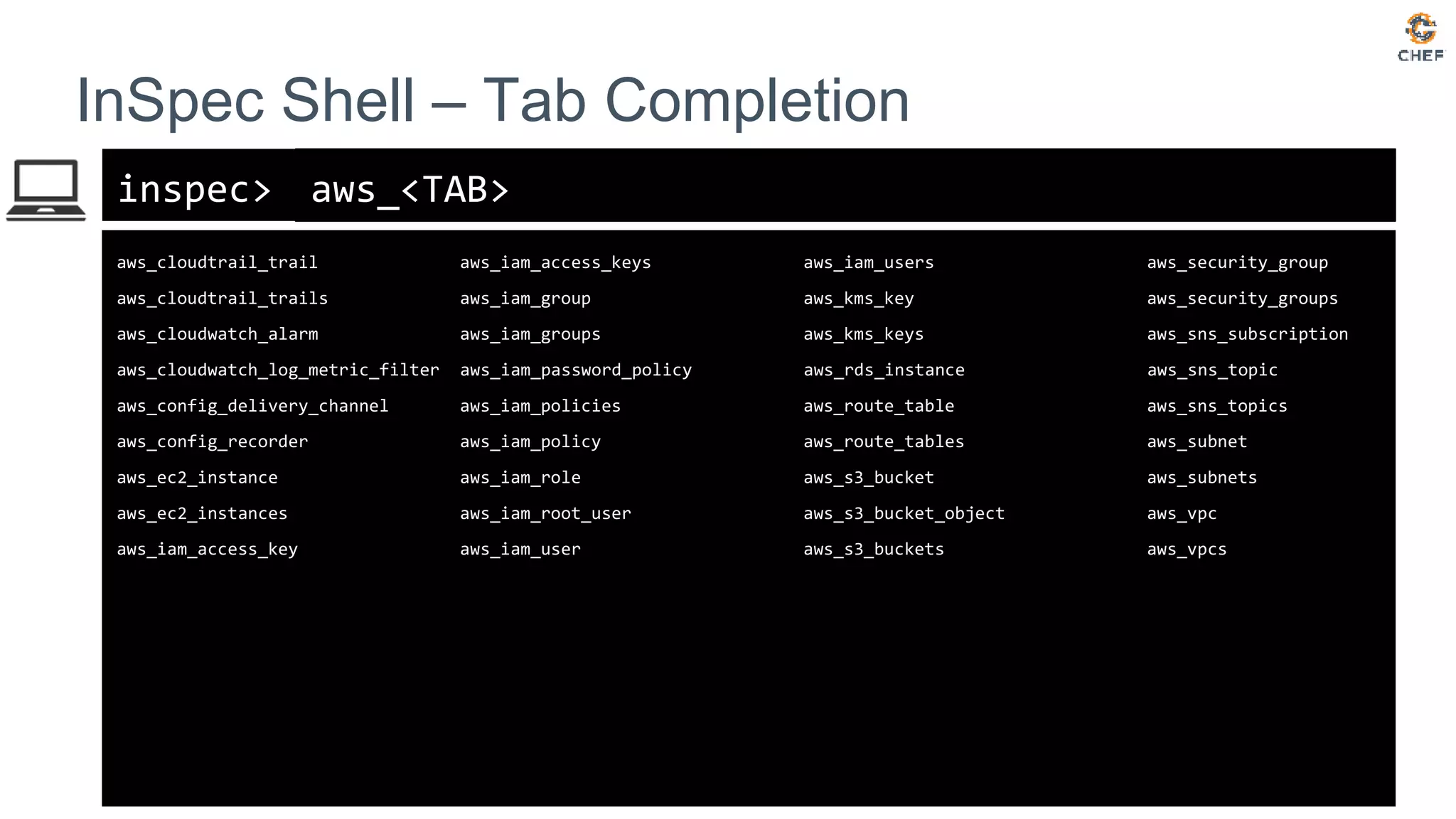
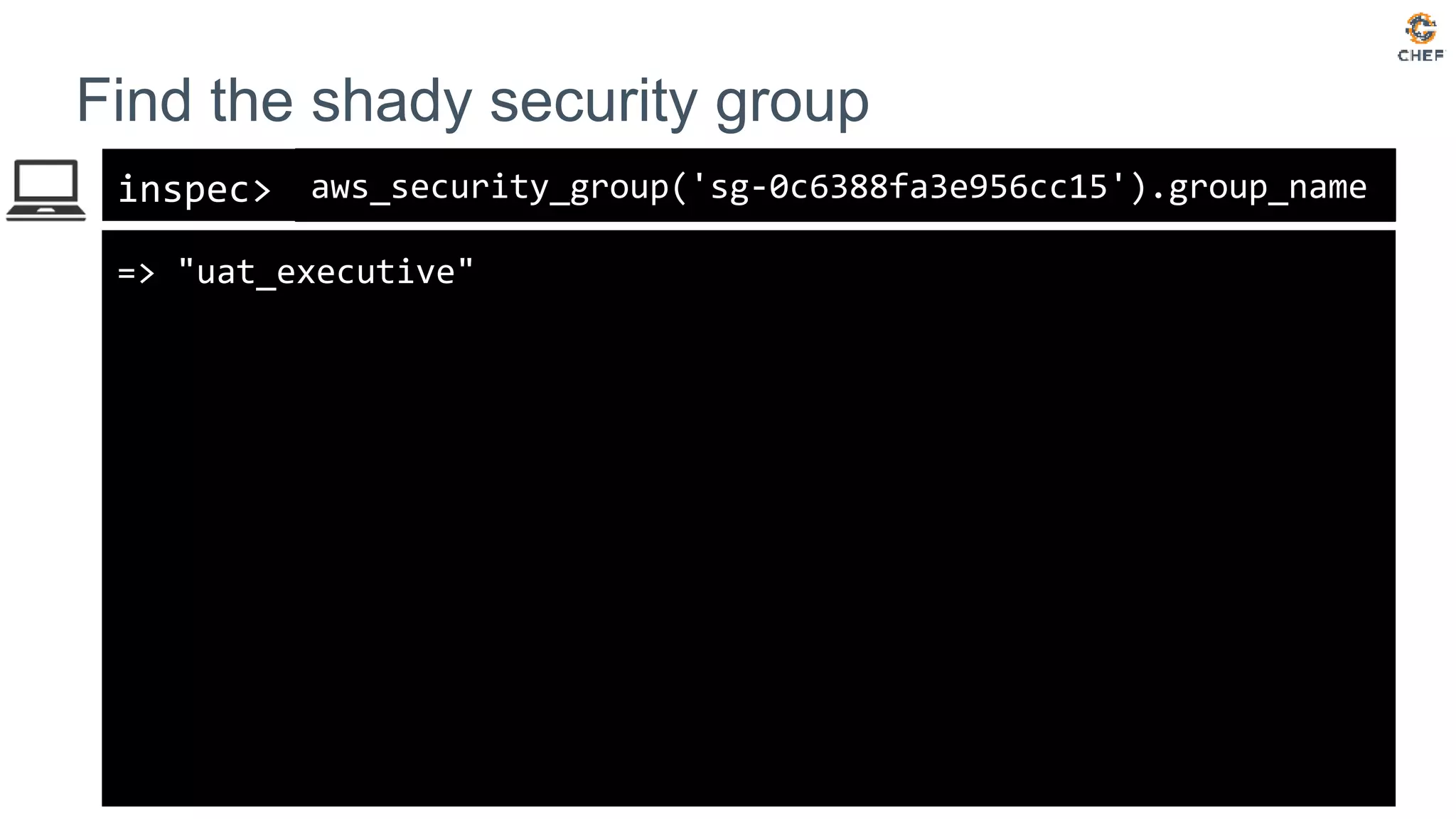
![inspec>
Check the Rules
aws_security_group('sg-0c6388fa3e956cc15').inbound_rules
=> [{:from_port=>22,
:ip_protocol=>"tcp",
:ip_ranges=>[{:cidr_ip=>"0.0.0.0/0"}],
:ipv_6_ranges=>[{:cidr_ipv_6=>"::/0"}],
:prefix_list_ids=>[],
:to_port=>22,
:user_id_group_pairs=>[]}]](https://image.slidesharecdn.com/testing-terraform-180621135054/75/Testing-Terraform-29-2048.jpg)