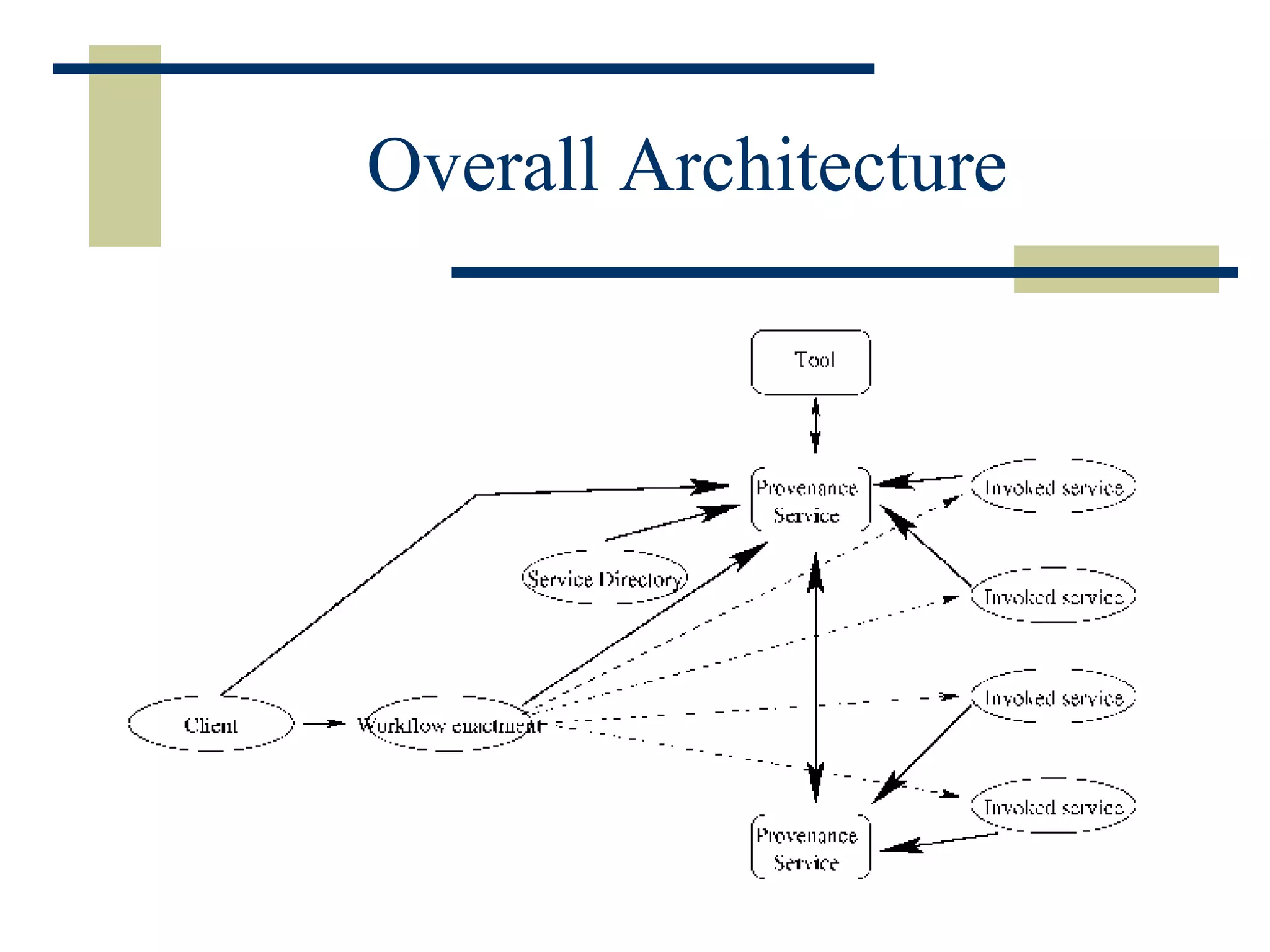
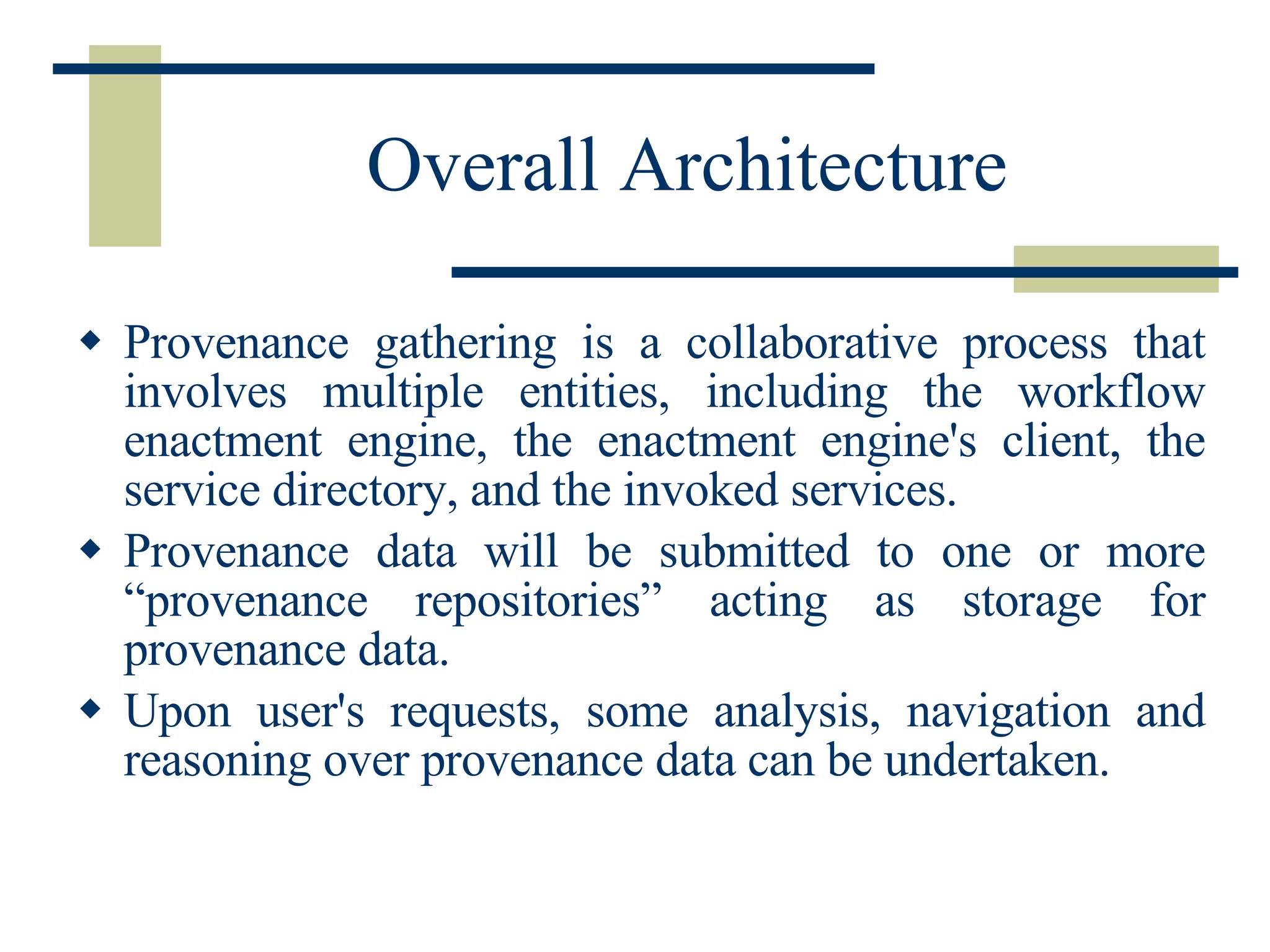
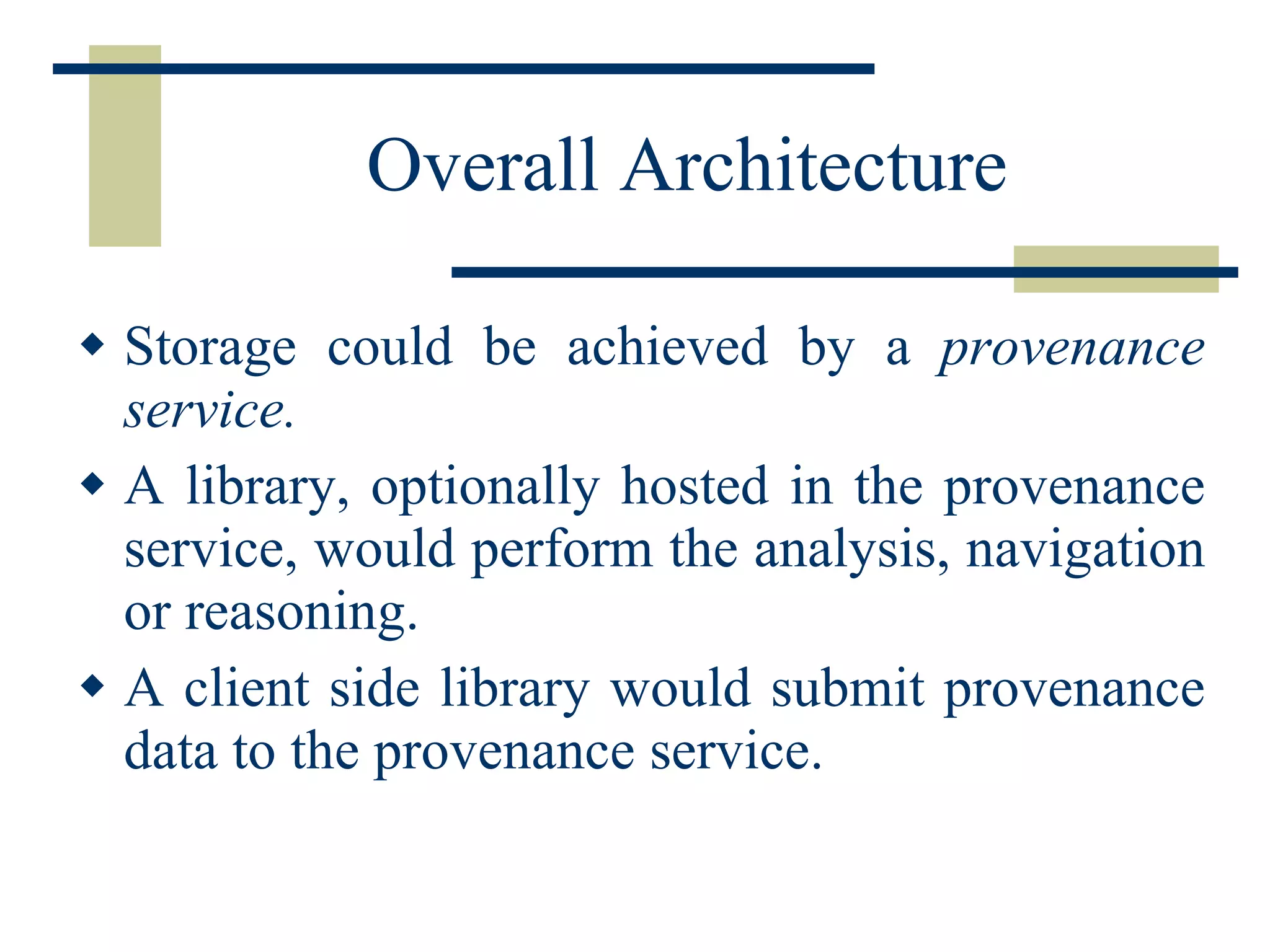
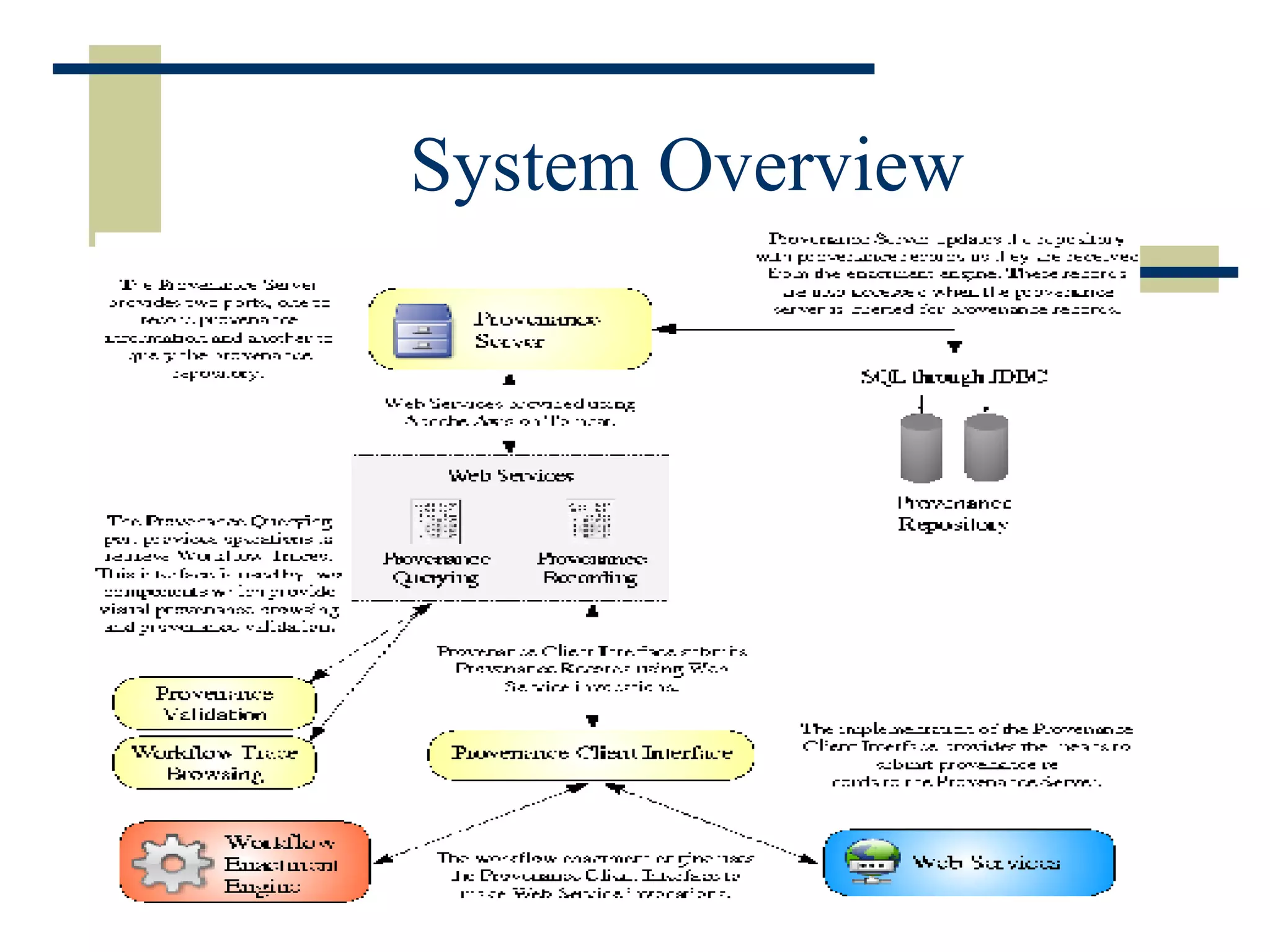
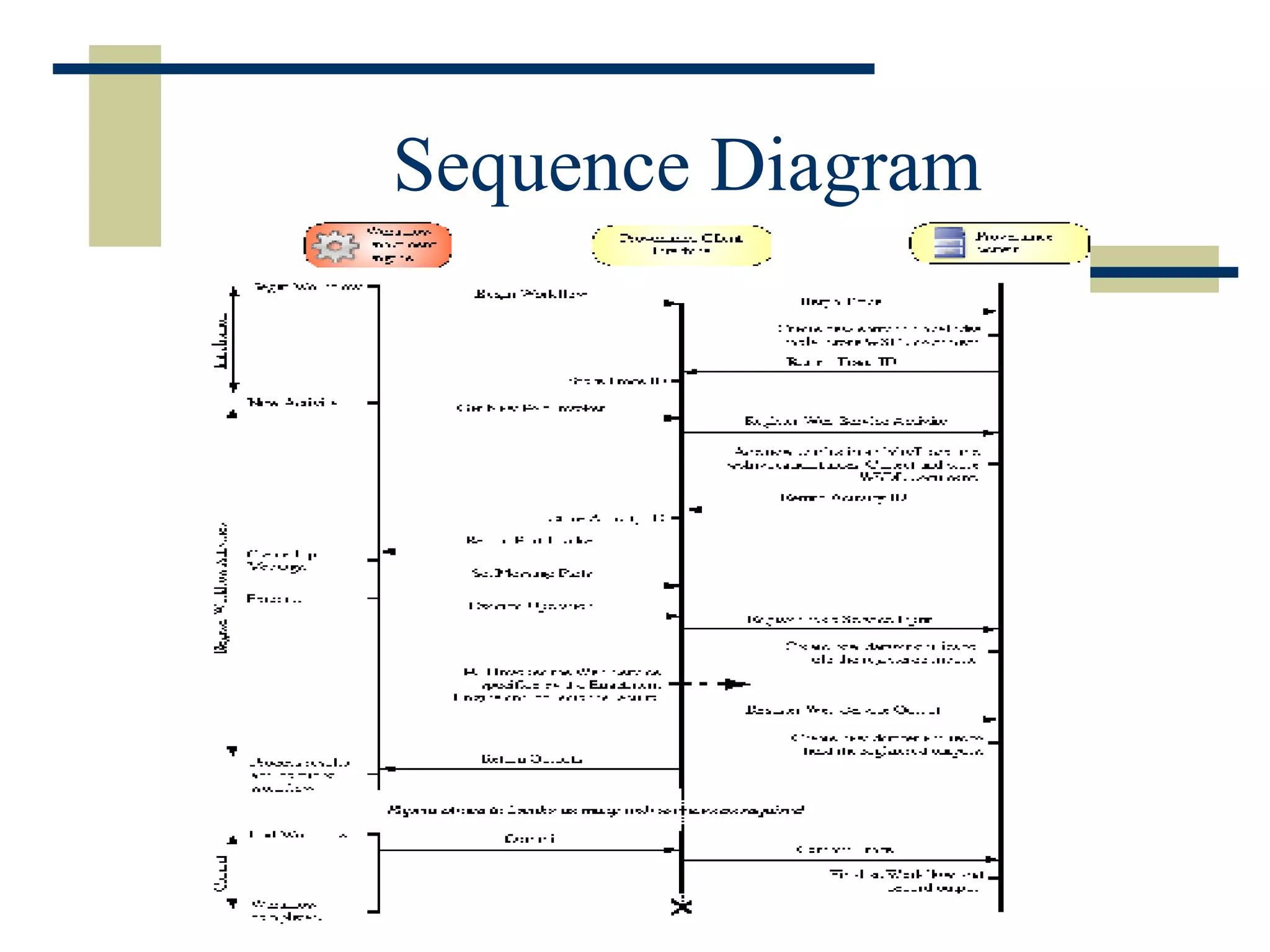
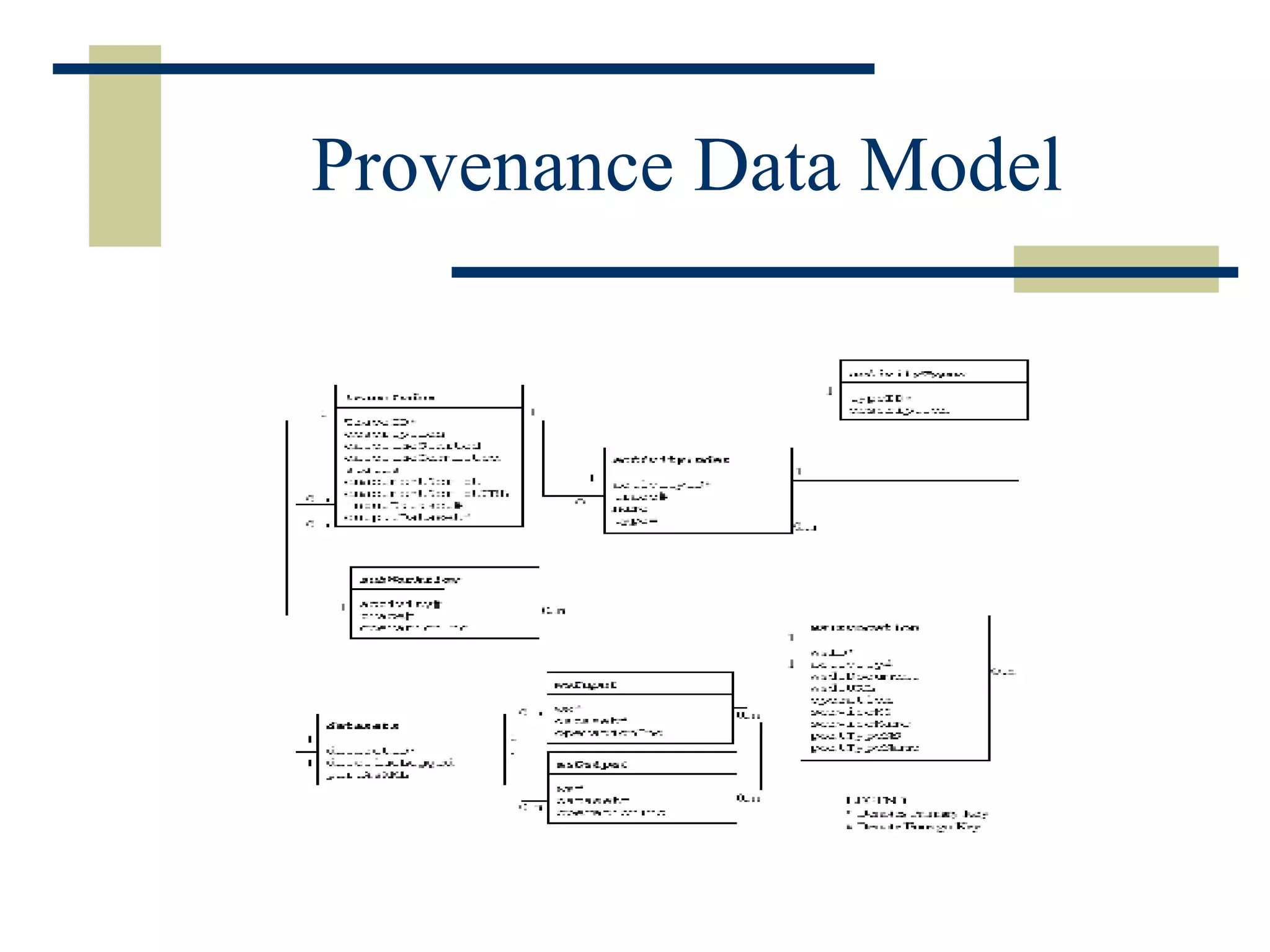
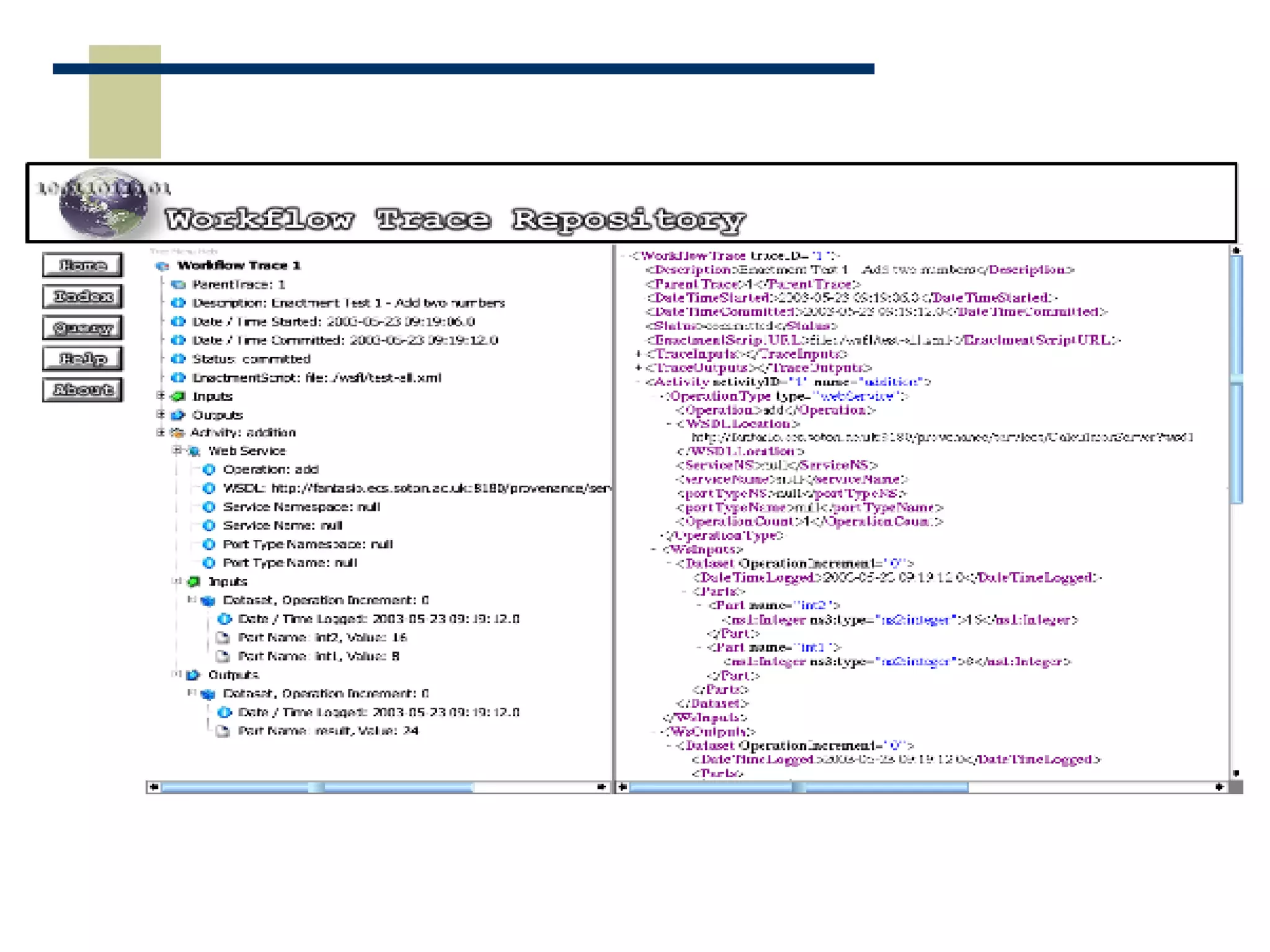
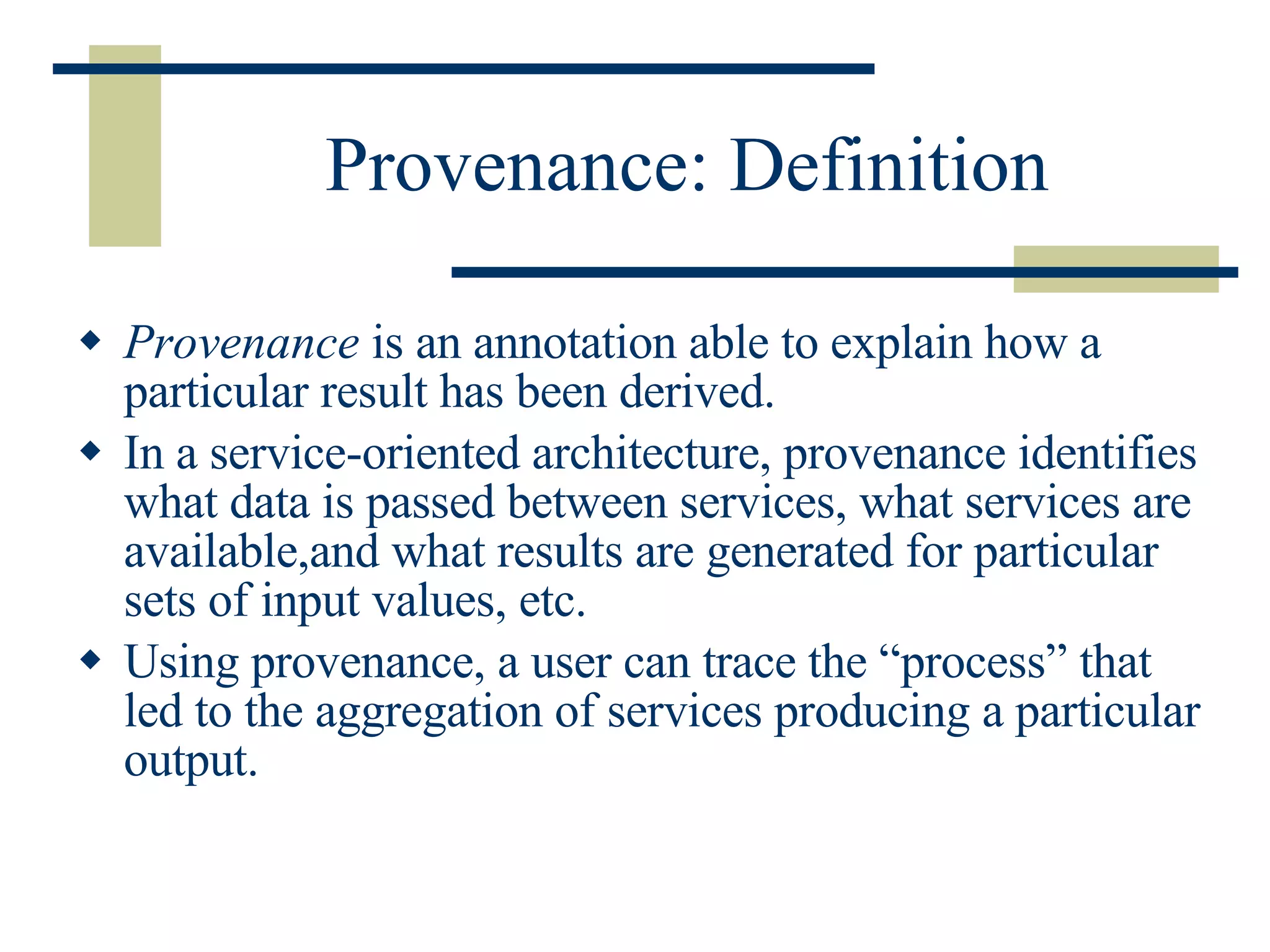
The document discusses the importance of provenance data in distributed computing environments like grids and web services. It proposes a service-oriented architecture and data model for capturing and querying provenance information. The architecture includes a provenance service for storage and analysis of provenance data gathered during workflow executions across multiple services and systems.
![Recording and Reasoning Over Data Provenance in Web and Grid Services Martin Szomszor and Luc Moreau [email_address] University of Southampton](https://image.slidesharecdn.com/odbase2003v2-1225286666317651-9/75/Recording-and-Reasoning-Over-Data-Provenance-in-Web-and-Grid-Services-1-2048.jpg)
![The Grid and Virtual Organisations The Grid problem is defined as coordinated resource sharing and problem solving in dynamic, multi-institutional virtual organisations [FKT01]. Effort is required to allow users to place their trust in the data produced by such virtual organisations Understanding how a given service is likely to modify data flowing into it, and how this data has been generated is crucial.](https://image.slidesharecdn.com/odbase2003v2-1225286666317651-9/75/Recording-and-Reasoning-Over-Data-Provenance-in-Web-and-Grid-Services-3-2048.jpg)



![Provenance in a Bioinformatics Grid (myGrid) Two major forms of provenance [Greenwood03]: The derivation path records the process by which results are generated from input data. Derivation data provides the answer to questions about what initial data was used for a result, and how was the transformation from initial data to result achieved. FDA requirement on drug companies to keep a record of provenance of drug discovery as long as the drug is in use (up to 50 years sometimes).](https://image.slidesharecdn.com/odbase2003v2-1225286666317651-9/75/Recording-and-Reasoning-Over-Data-Provenance-in-Web-and-Grid-Services-13-2048.jpg)
![Provenance in a Bioinformatics Grid (myGrid) Two major forms of provenance [Greenwood03]: Annotations are attached to objects, or collections of objects. Annotation data provides more contextual information that might be of interest: who performed an experiment, when did they supply any comments on the specific methods and materials used, when an object was created, last updated,who owns it and its format. Useful to provide personalised environment.](https://image.slidesharecdn.com/odbase2003v2-1225286666317651-9/75/Recording-and-Reasoning-Over-Data-Provenance-in-Web-and-Grid-Services-14-2048.jpg)
![Other Provenance Requirements and Uses Standard lineage representation, automated lineage recording, unobtrusive information collecting [Frew and Brose] To give reliability and quality, justification and audit, re-usability, reproducibility and repeatability, change and evolution, ownership, security, credit and copyright [Goble]](https://image.slidesharecdn.com/odbase2003v2-1225286666317651-9/75/Recording-and-Reasoning-Over-Data-Provenance-in-Web-and-Grid-Services-15-2048.jpg)