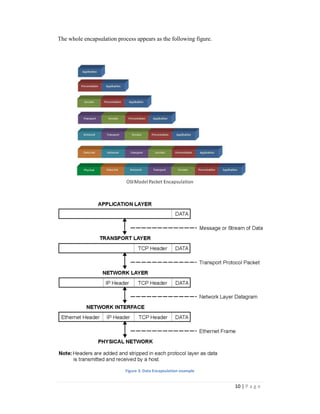
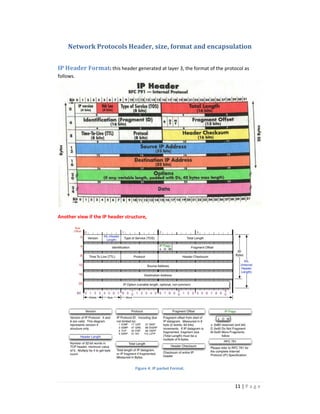
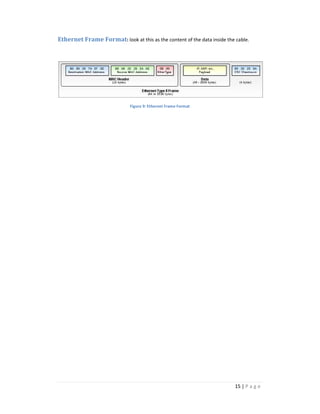
The document discusses the seven layers of the OSI model and provides details about each layer. It describes the functions and protocols associated with each layer, including the physical, data link, network, transport, session, presentation, and application layers. Examples are provided to illustrate concepts like encapsulation and the OSI model's role in network communication.