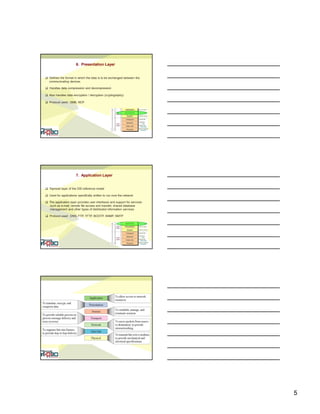
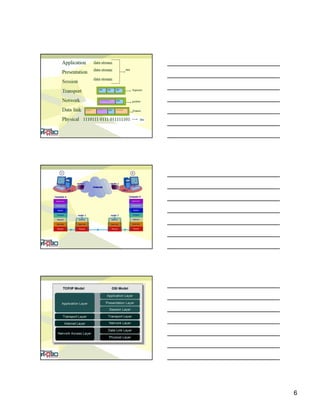
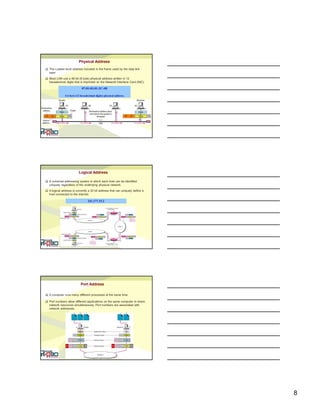
The document discusses network reference models, specifically comparing the OSI model and TCP/IP model. It provides details on each of the seven layers of the OSI model and describes their functions. It also compares the OSI model to the TCP/IP model, noting they have a different number of layers and the TCP/IP model combines some OSI layers. The document concludes by defining different types of addresses used in TCP/IP like physical, logical, and port addresses.

![2
The OSI Model [continued]
The OSI model describes how information or data makes its way from
application programs (such as spreadsheets) through a network medium
(such as wire) to another application program located on another
network.
The OSI reference model divides the problem of moving information
between computers over a network medium into SEVEN smaller and
more manageable problems .
The OSI (Open System Interconnection) is a layered framework of
network systems that allows communication between all types of
computer systems.](https://image.slidesharecdn.com/networkreferencemodels-211111183232/85/Network-Reference-Model-Computer-Networks-Cybernetics-Robo-Academy-2-320.jpg)