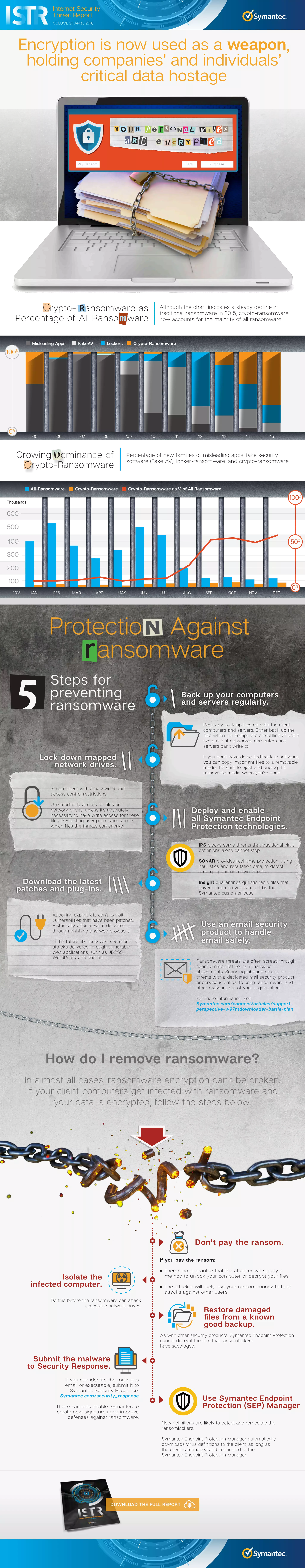
Encryption is now being used as a weapon by cybercriminals to hold hostage critical data from companies and individuals through crypto-ransomware attacks. Regular backups and keeping systems updated are key steps to prevent ransomware, as paying ransoms provides no guarantee files will be recovered and only encourages more attacks. While Symantec Endpoint Protection cannot decrypt files encrypted by ransomware, it provides technologies like IPS, SONAR, and Insight to block threats and detect emerging malware that definitions alone may miss.