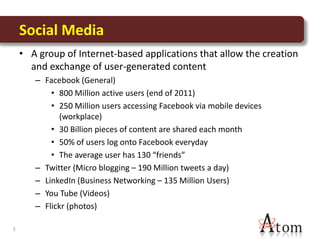
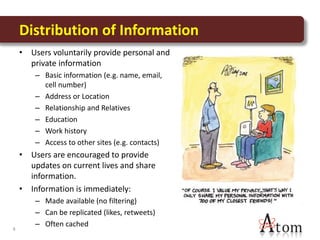
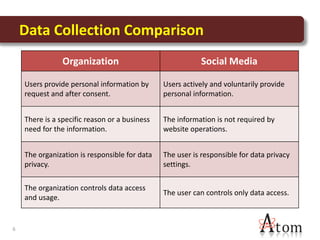
This document discusses privacy and social media. It notes that personal information shared on social media can be at risk if settings are not managed properly. Some key risks include information being shared broadly by users or accessed due to security issues. The document reviews examples of privacy issues that have occurred on Facebook and with Google. It emphasizes the importance of education about privacy, independent security controls, and involvement in legislative and policy changes to help protect personal information on social media.