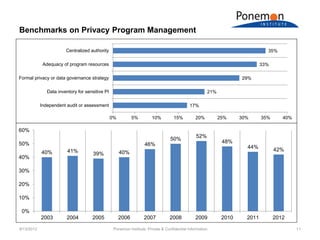
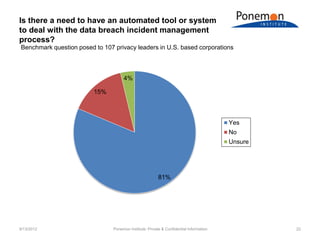
The document discusses benchmarks from a survey of privacy programs and the costs of privacy programs. It finds that organizations with more effective information security programs spend more on privacy. The highest spending categories for privacy programs are data security and program management, while the lowest are policies/procedures and redress/enforcement.