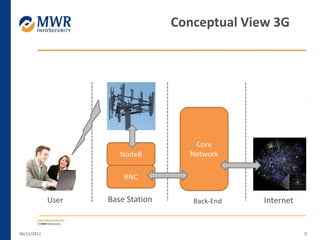
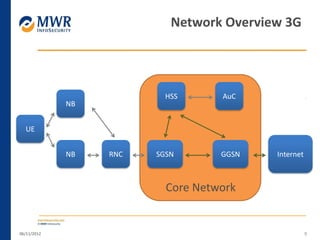
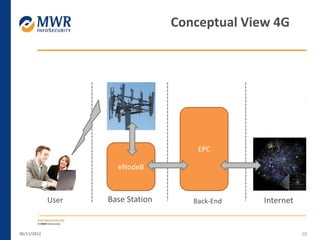
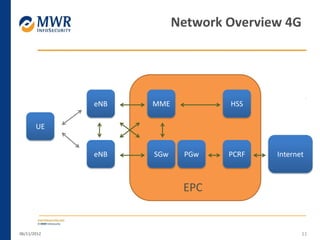
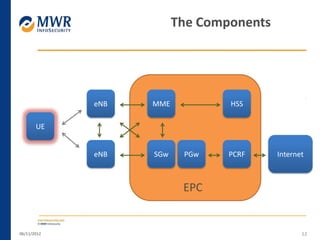
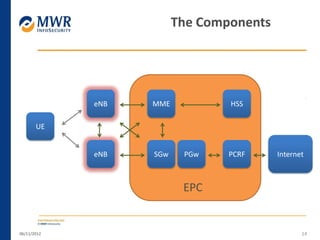
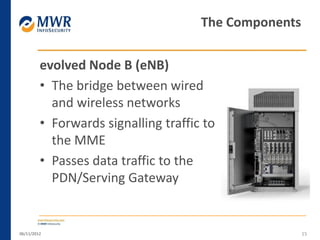
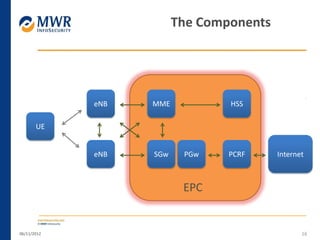
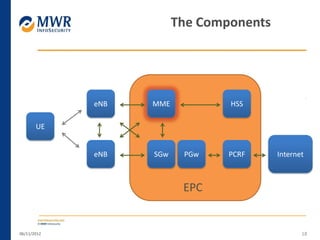
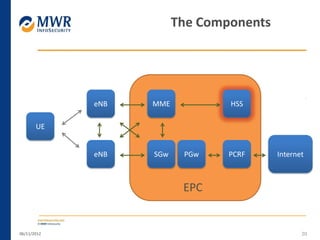
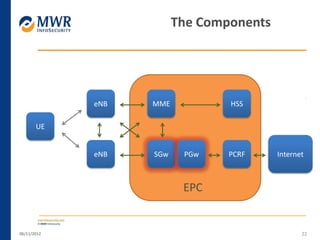
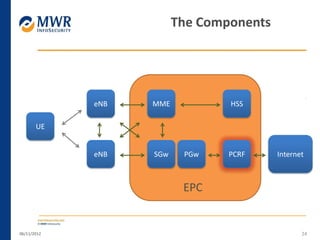
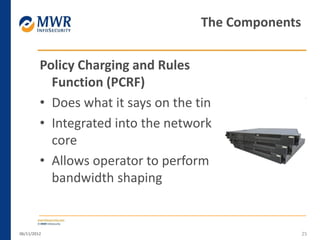
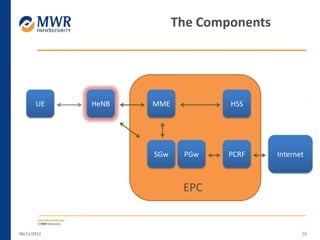
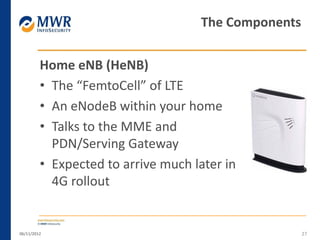
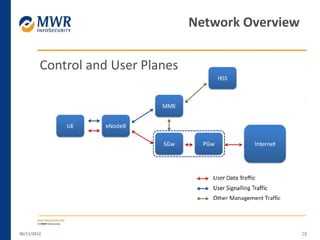
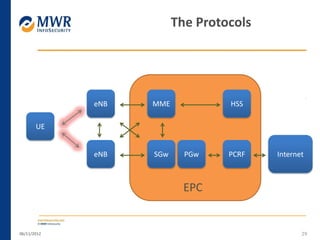
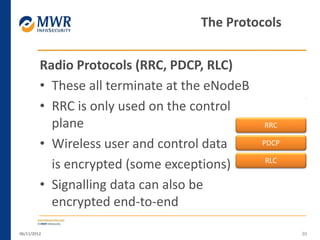
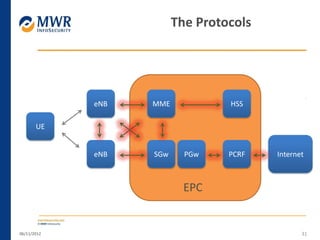
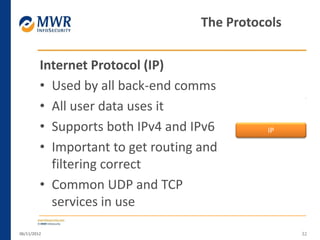
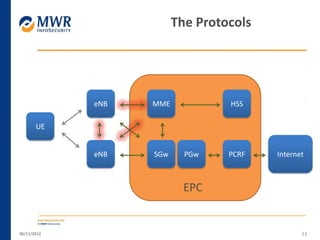
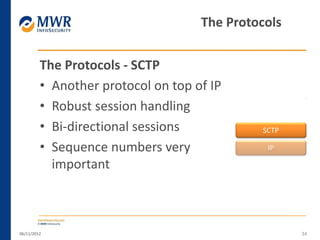
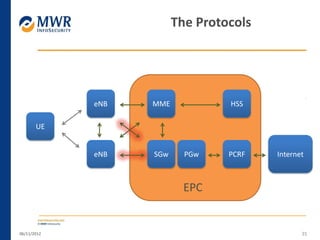
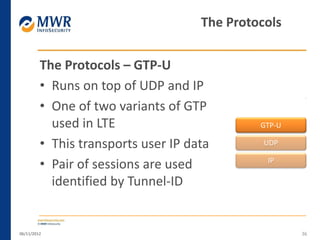
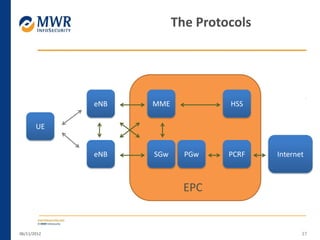
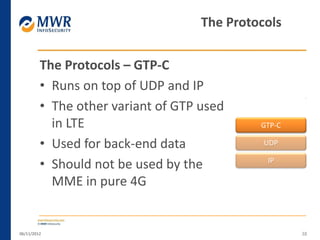
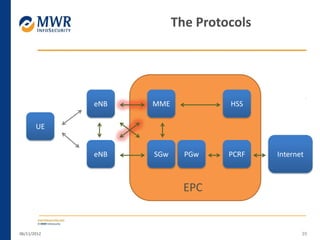
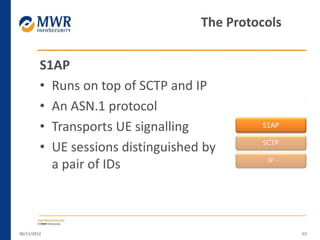
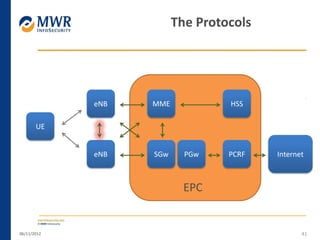
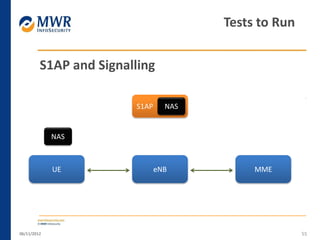
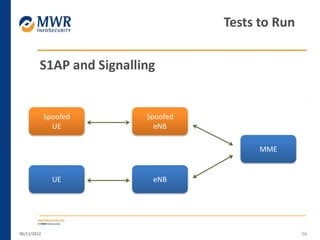
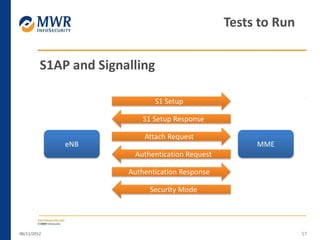
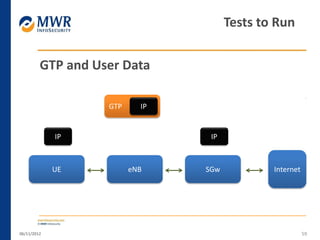
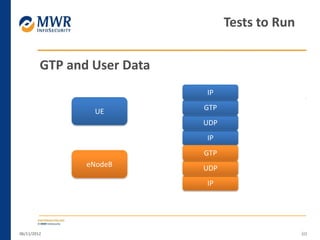
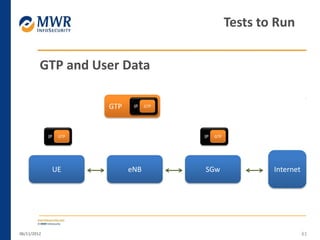
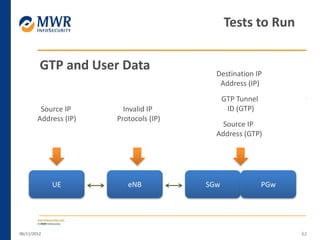
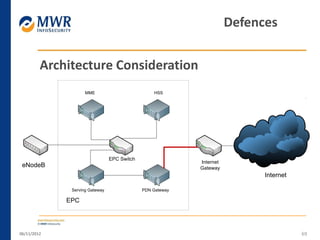
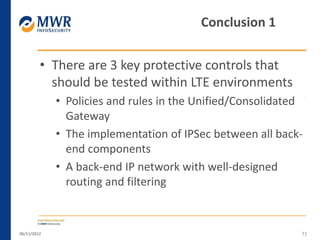
The document provides an overview of LTE networks and outlines potential security testing approaches. It describes the components of LTE networks including eNodeBs, MMEs, and gateways. The document discusses protocols like S1AP, GTP, and potential attacks such as spoofing signaling or manipulating encapsulated user data. It recommends testing key controls enforced by the gateway, IPSec implementation, and network routing/filtering to evaluate the security of LTE networks.