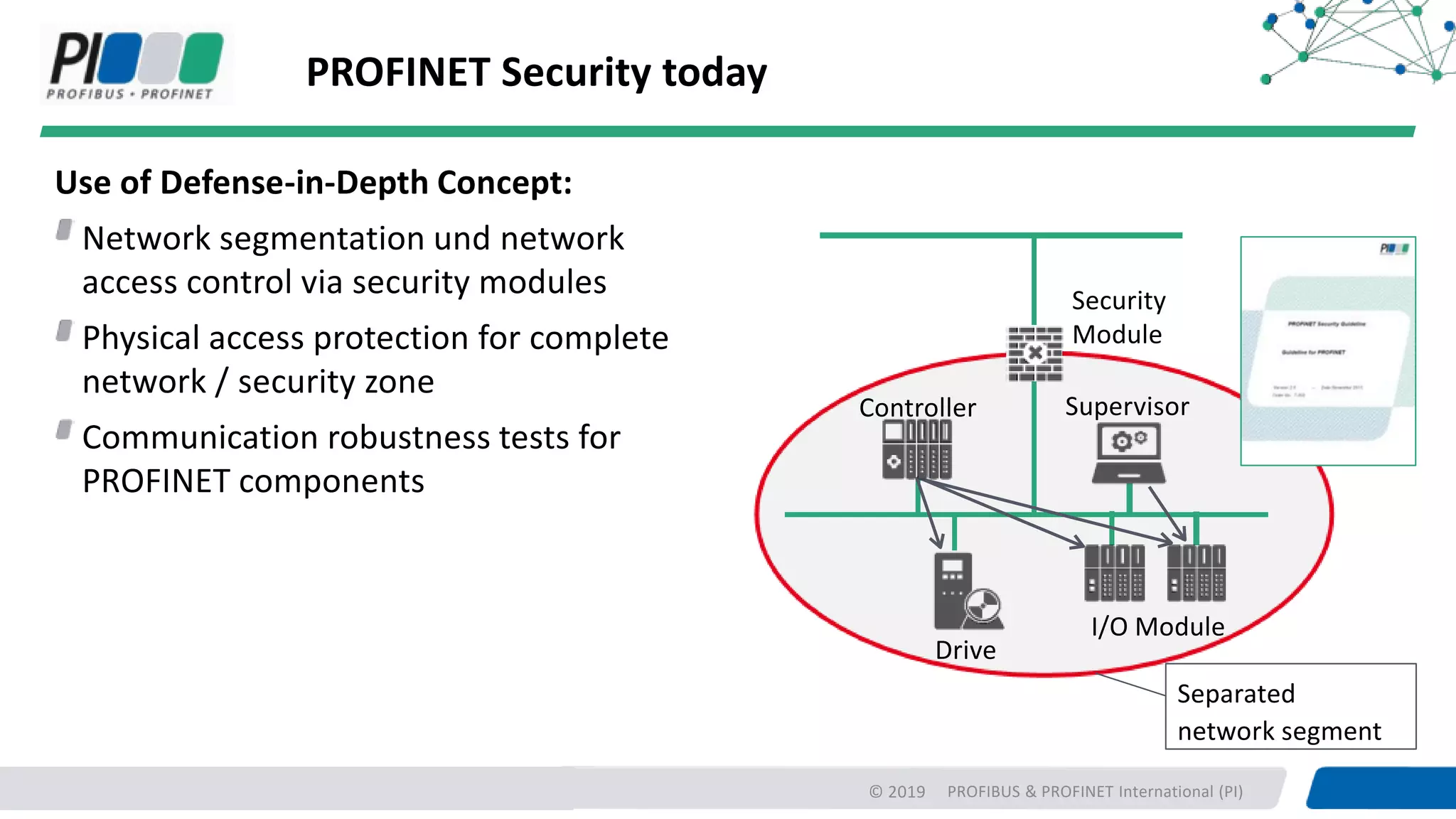
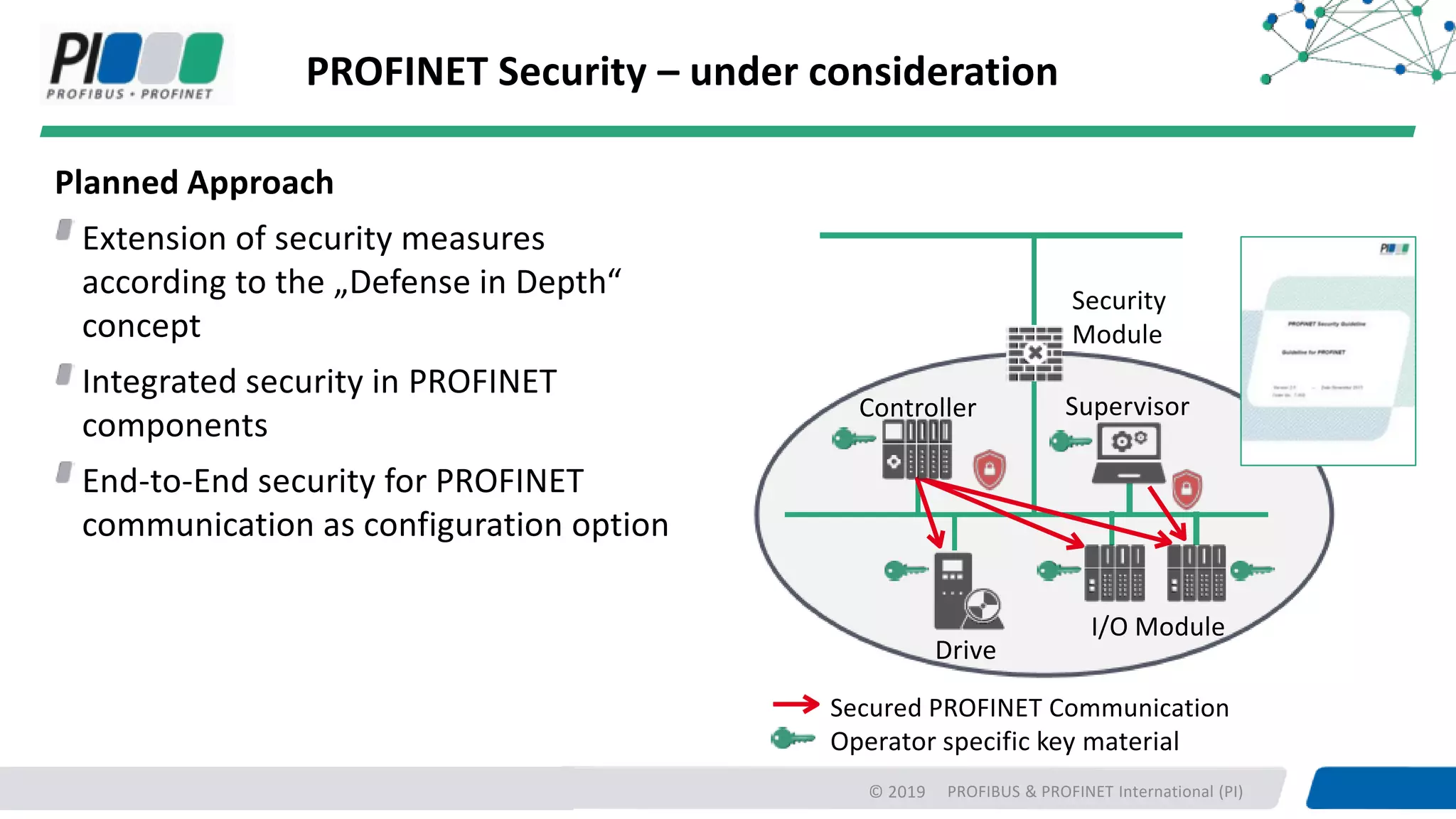
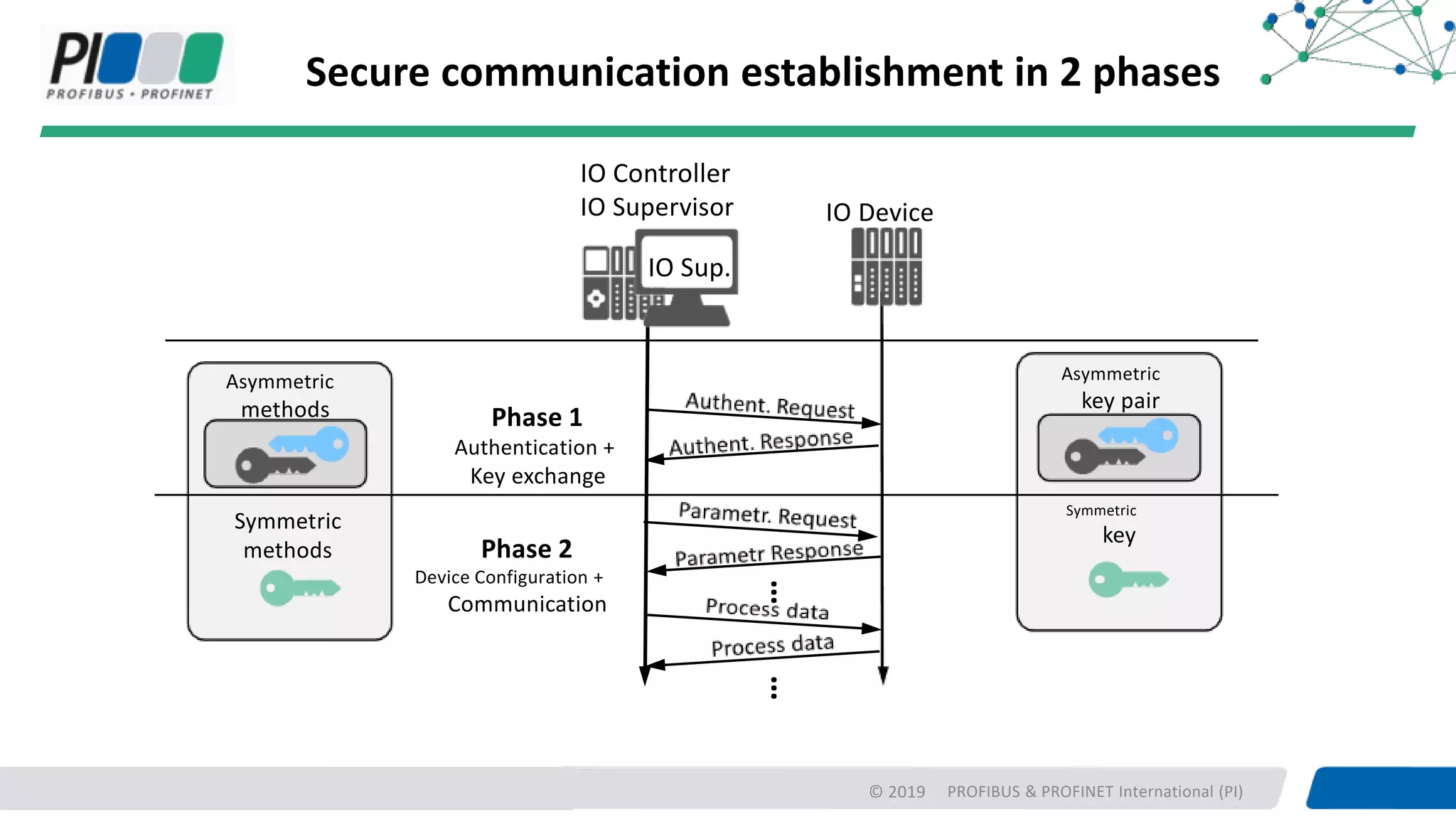
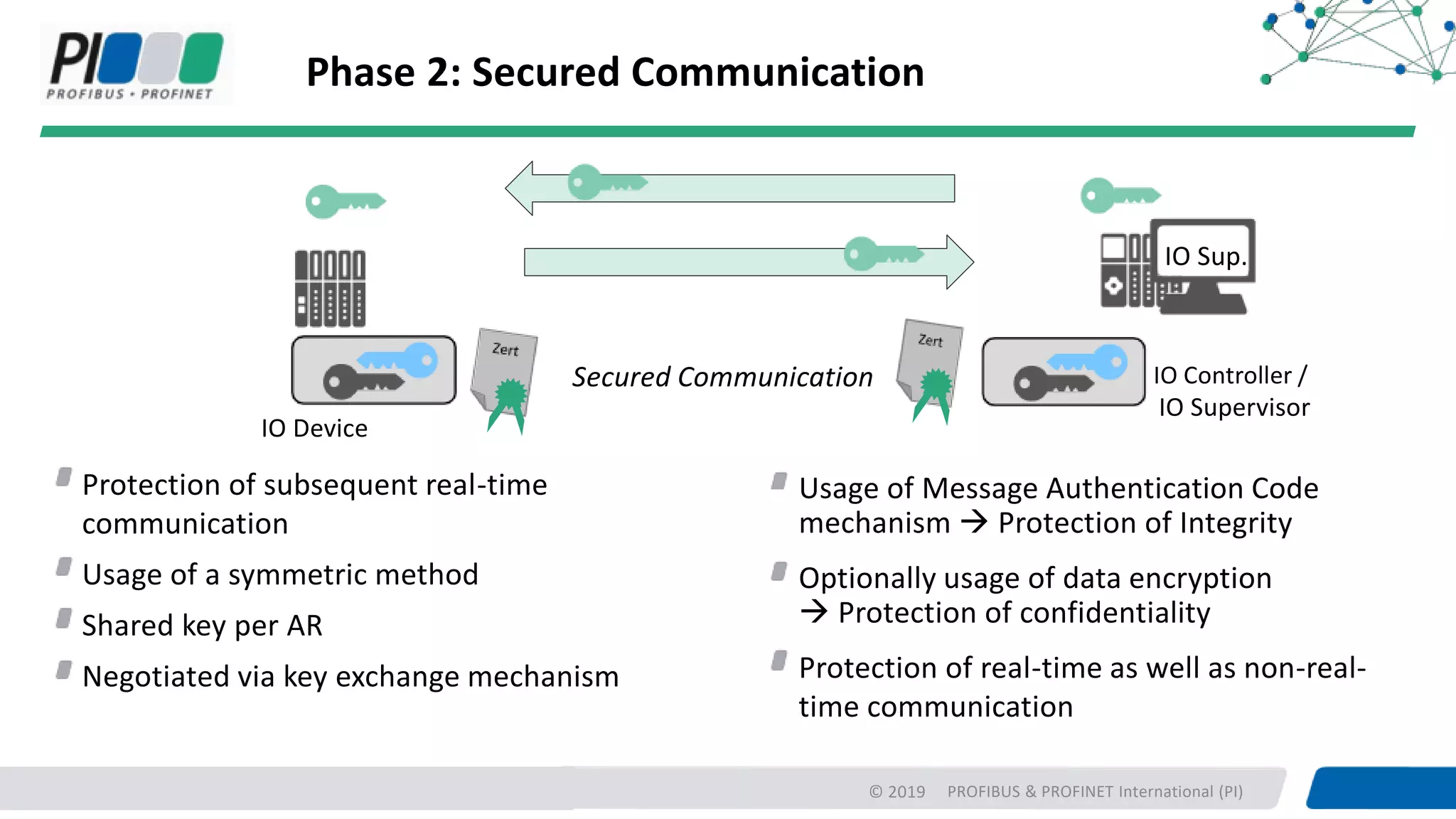
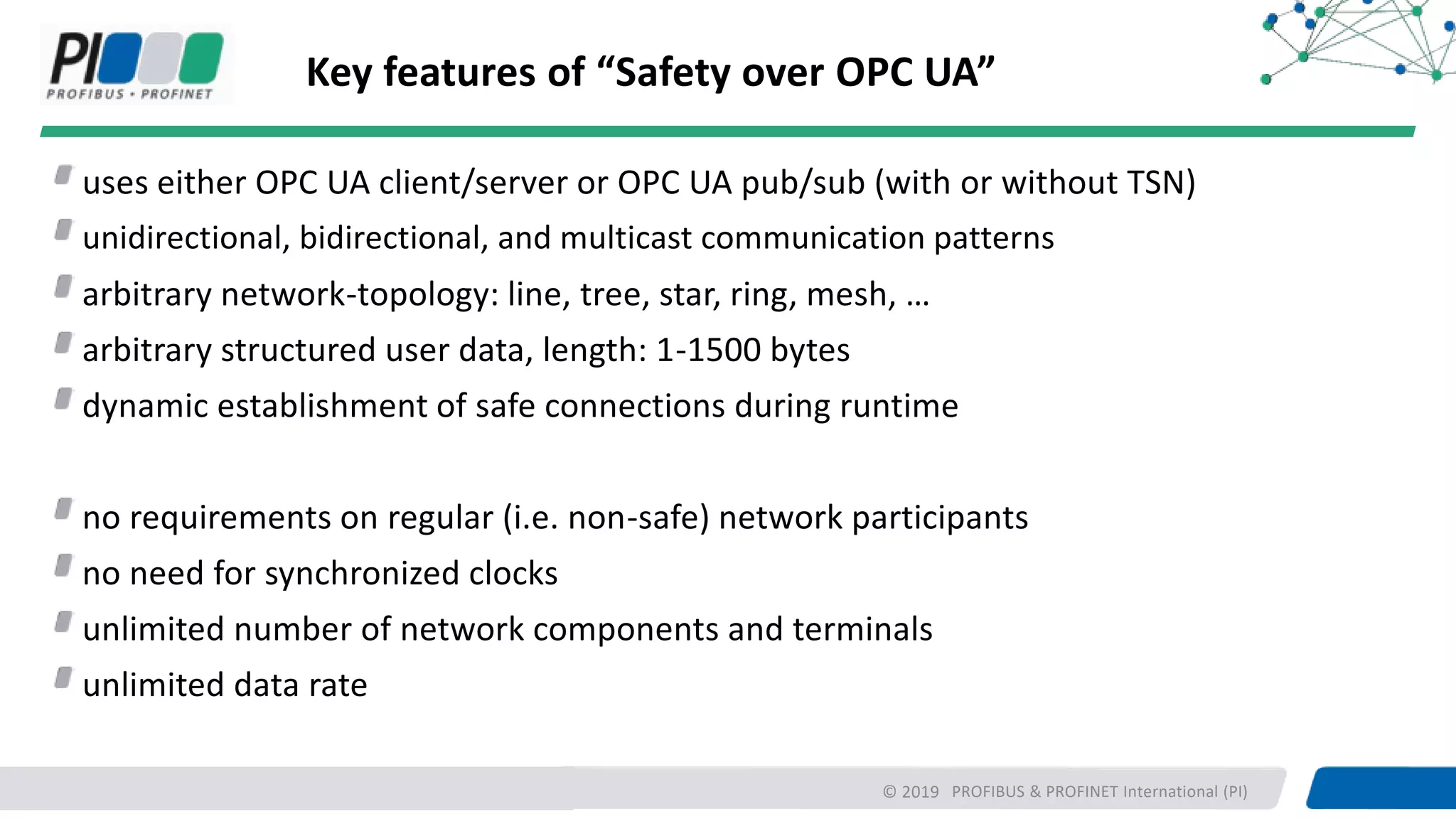
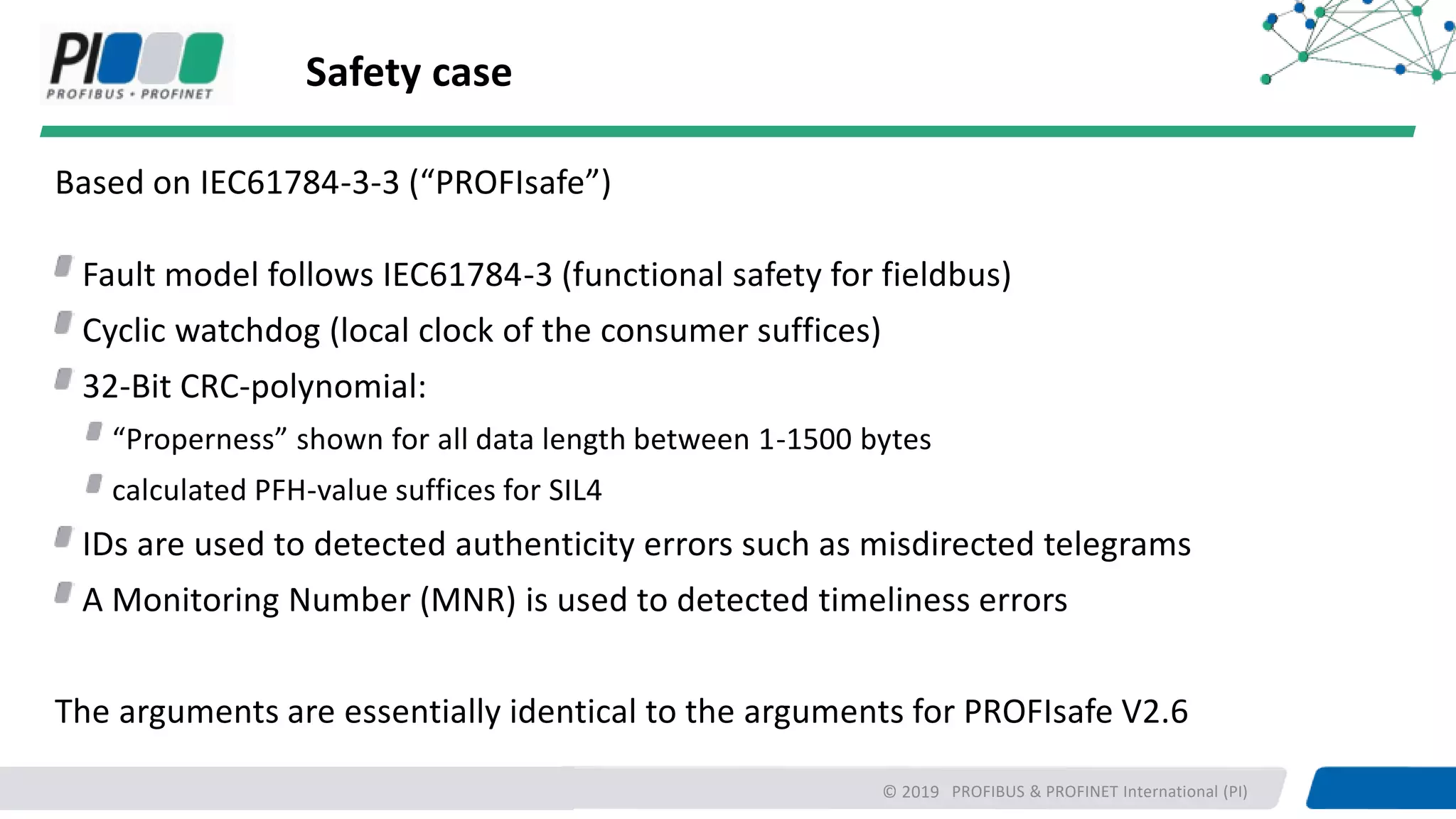
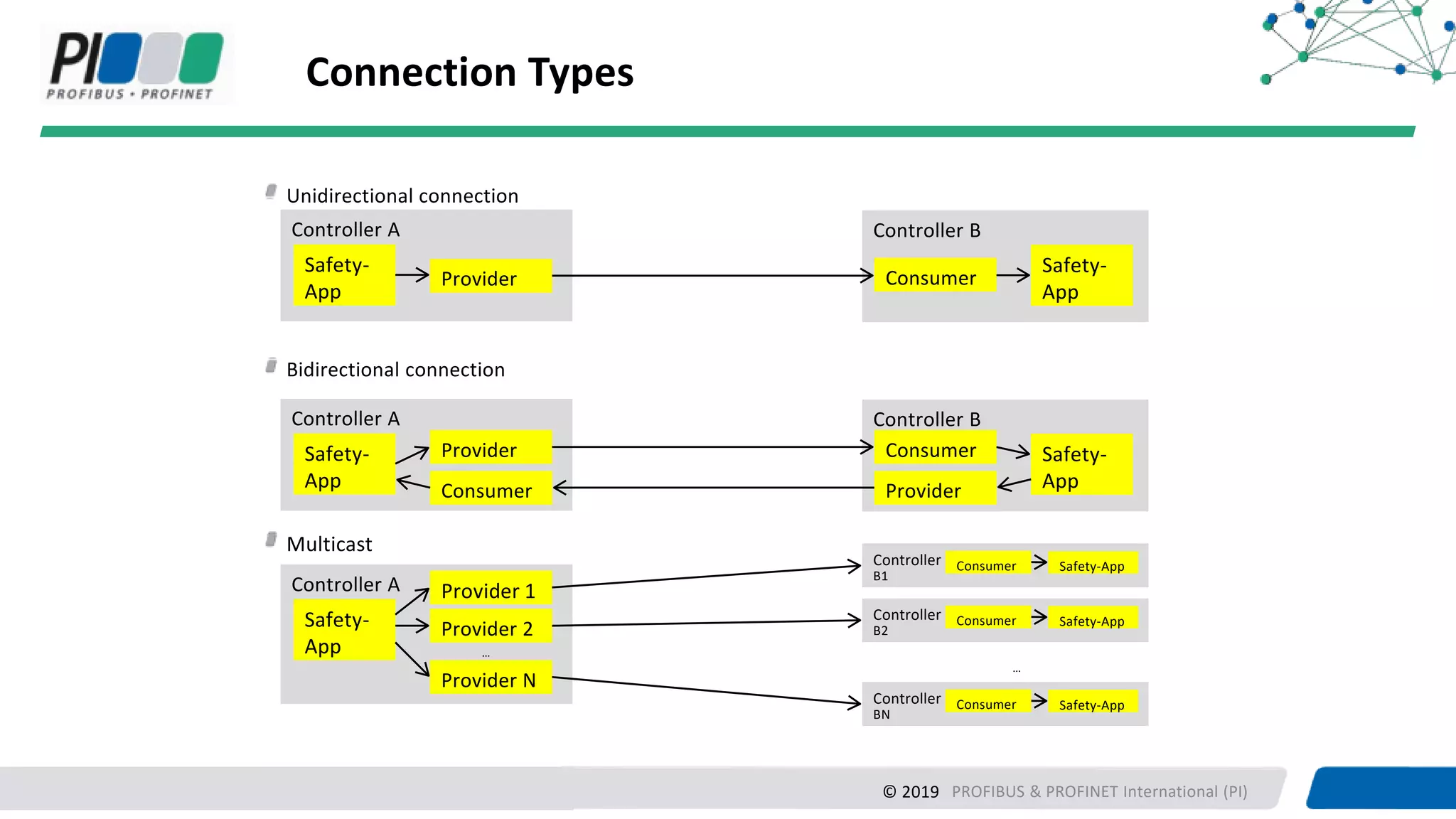
PROFIBUS & PROFINET International (PI) is working to enhance security for PROFINET networks. Current security measures include network segmentation, access control, and component testing. Planned improvements include extending the "Defense in Depth" concept with integrated security and optional end-to-end encryption. PROFINET will define security classes based on requirements for integrity, authenticity, confidentiality, and availability. A new "Safety over OPC UA" approach is also being developed to enable plant-wide functional safety communication using OPC UA.