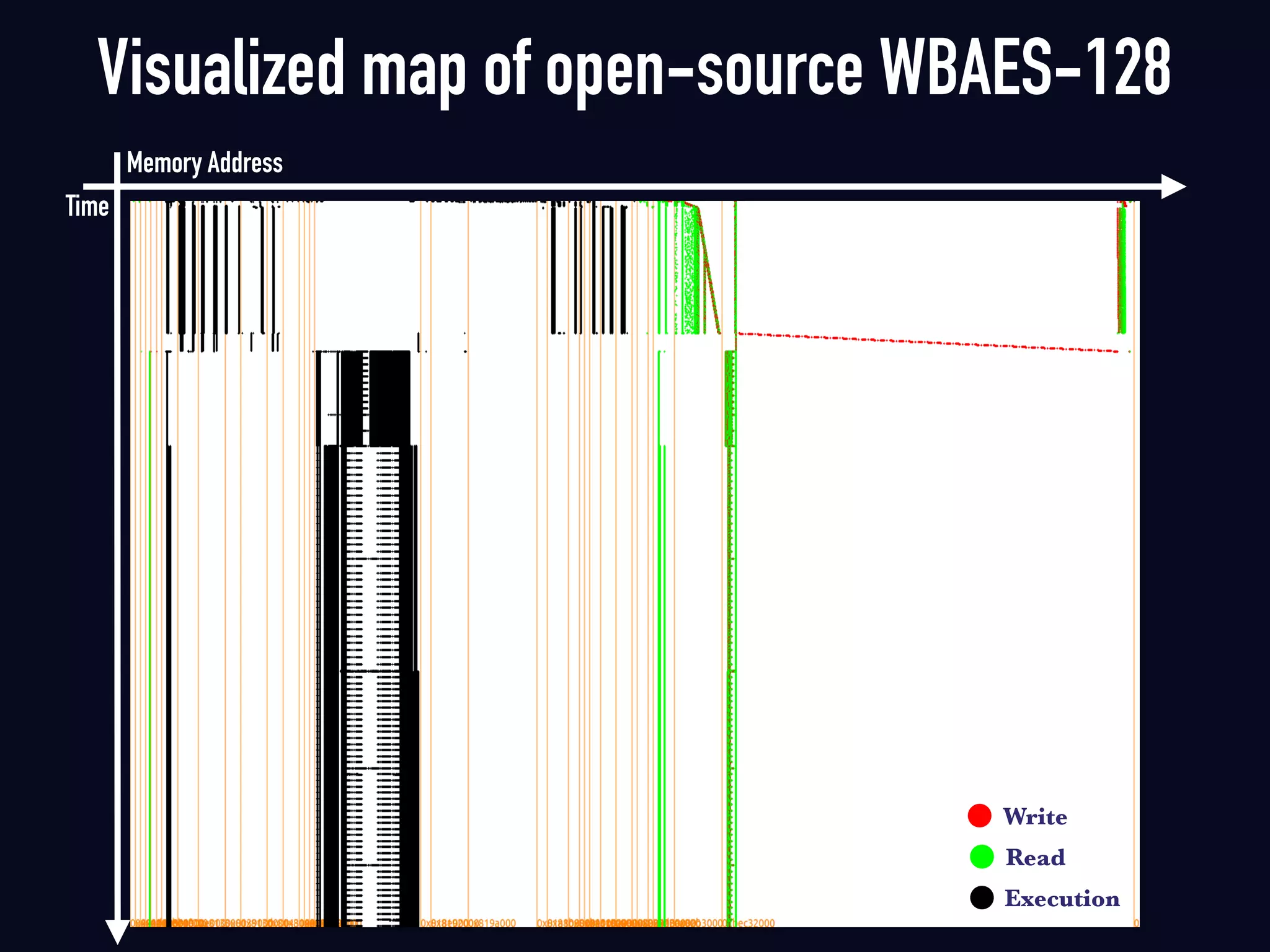
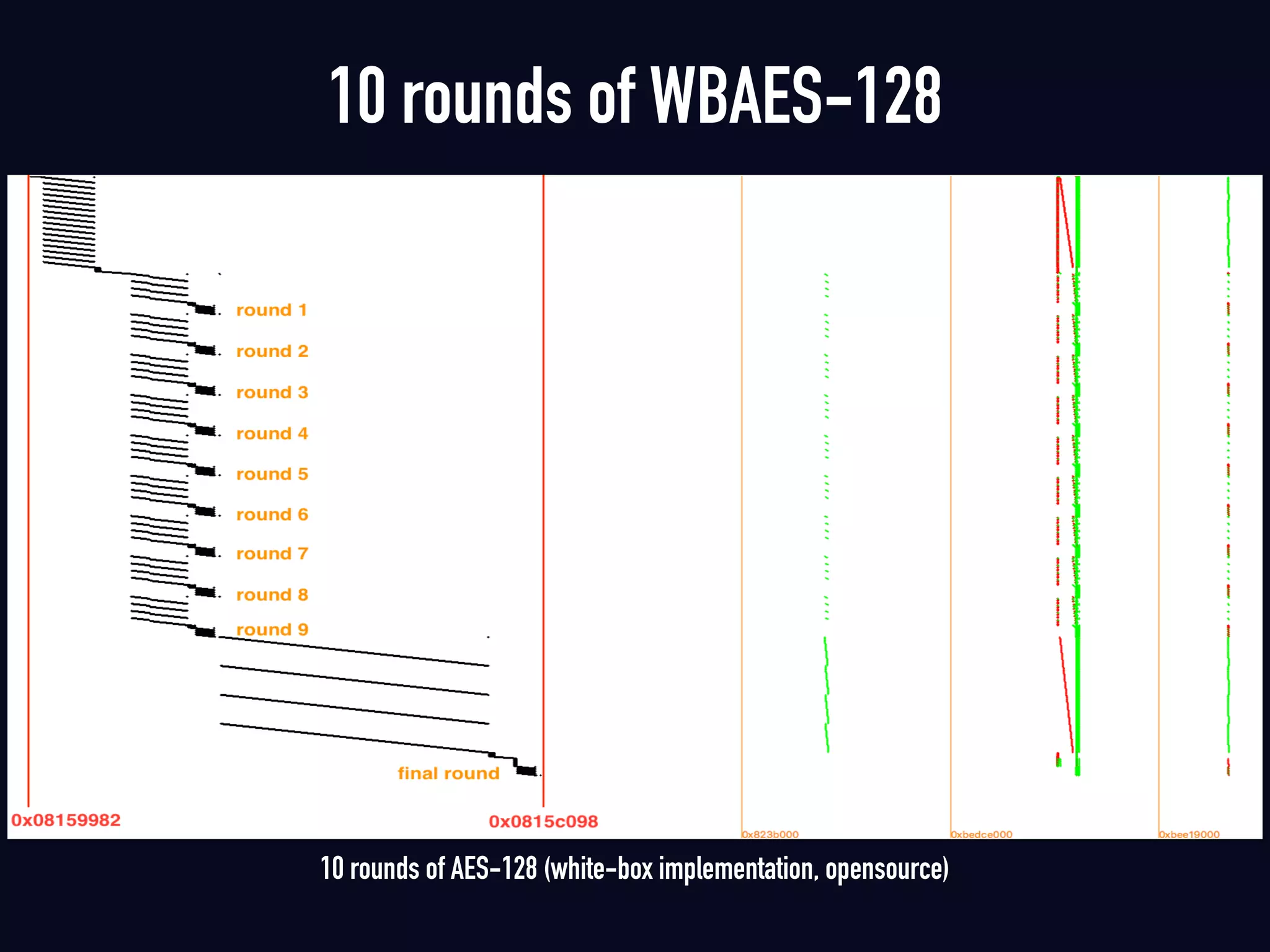
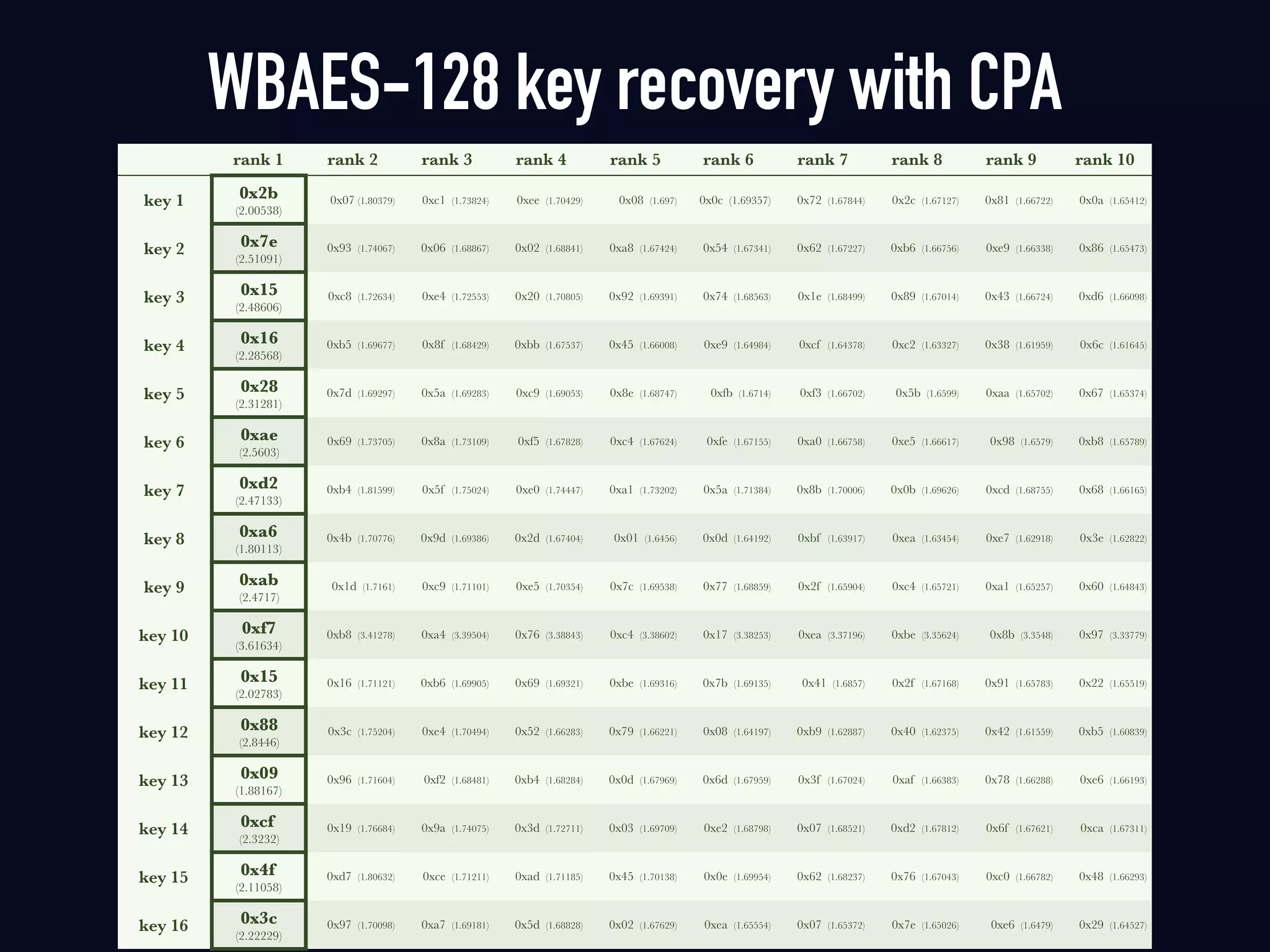
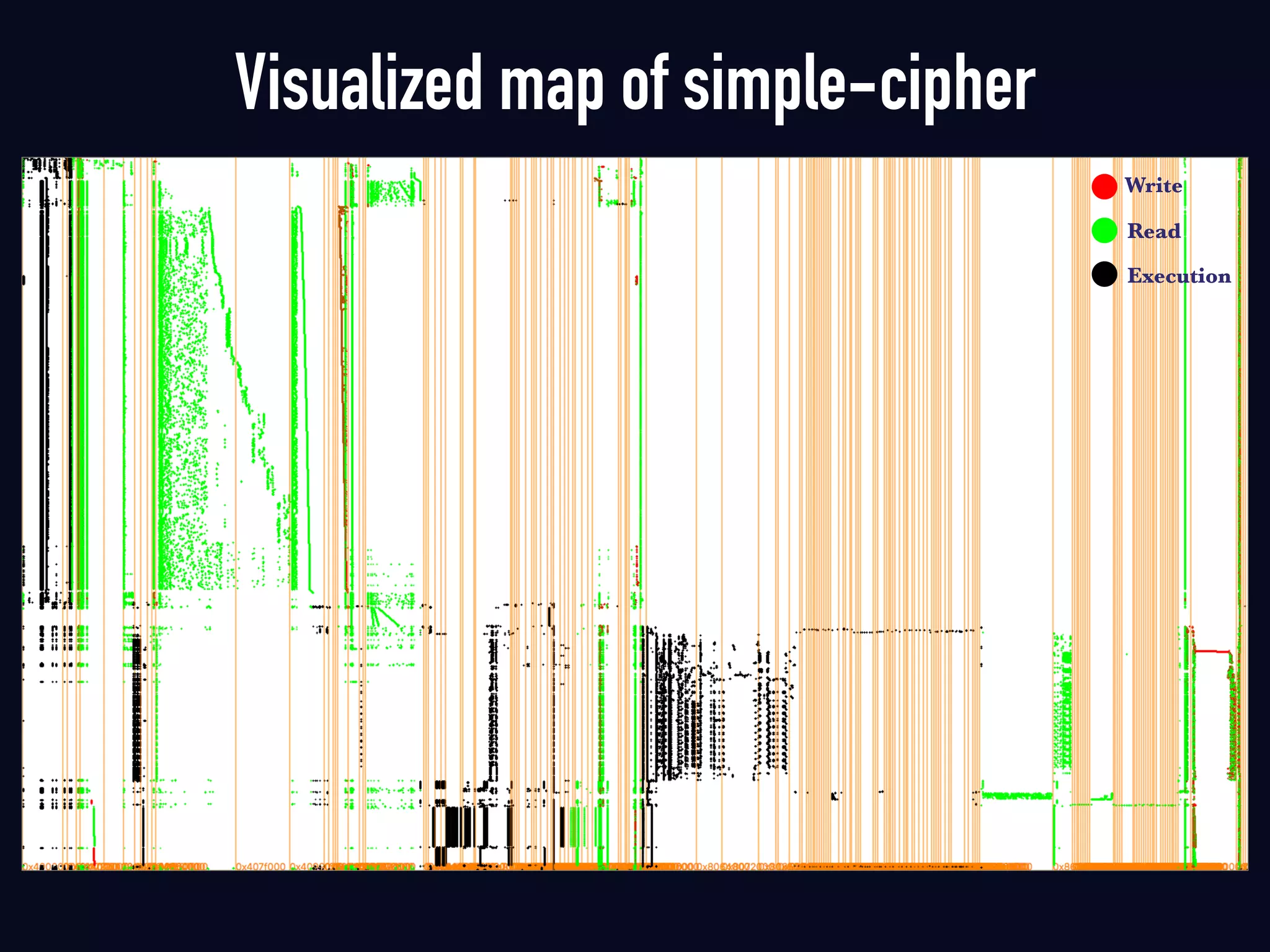
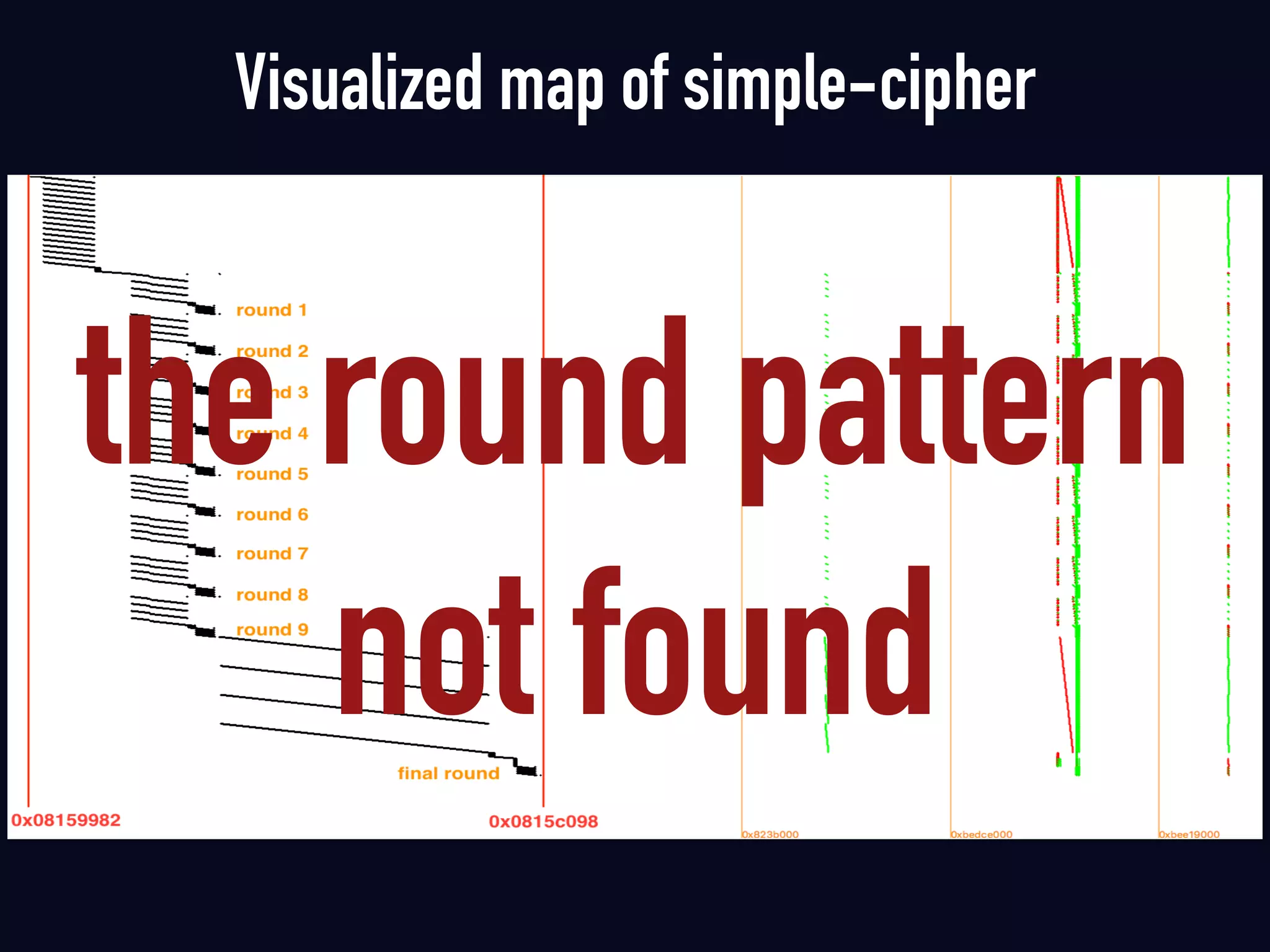
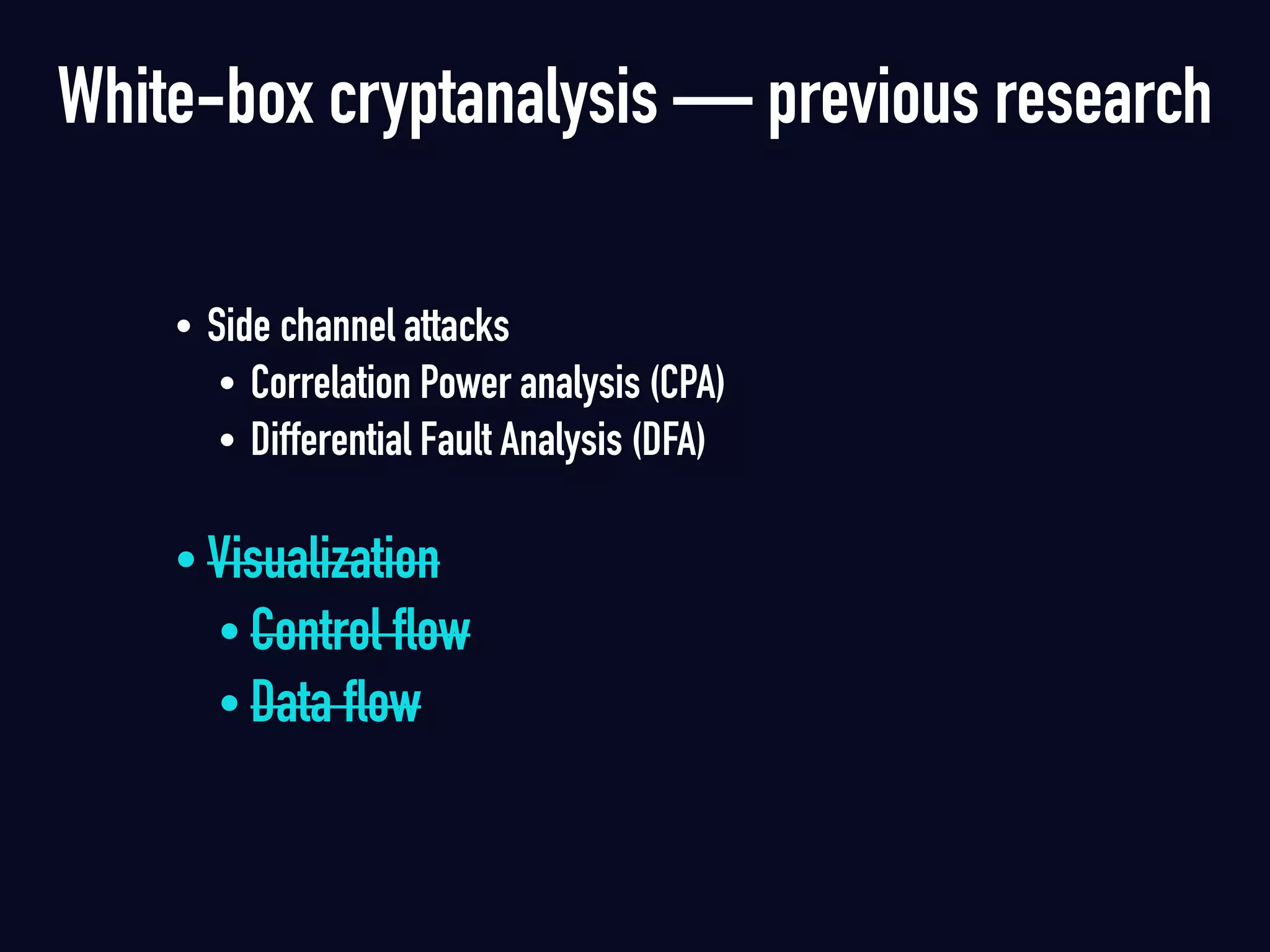
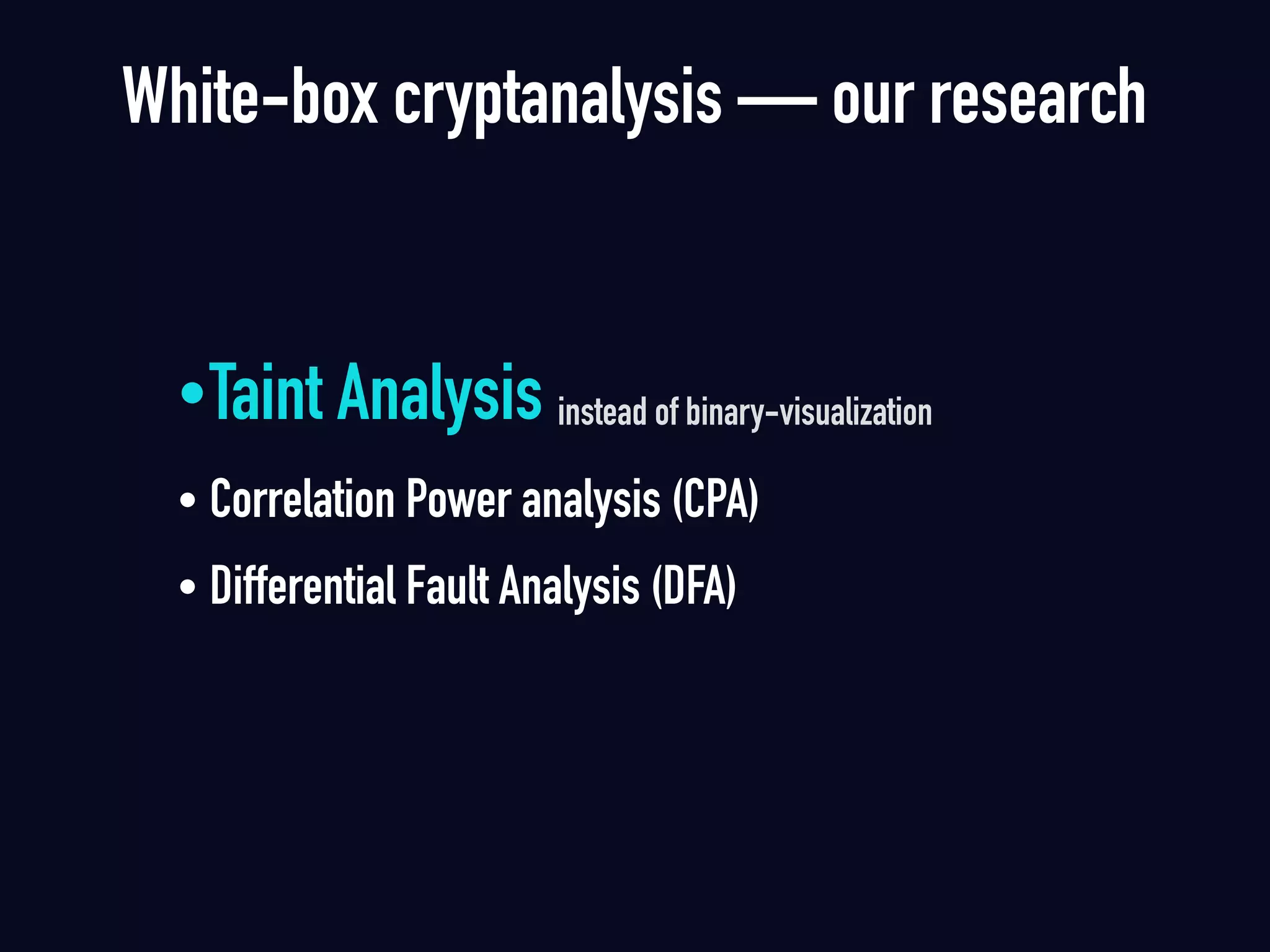
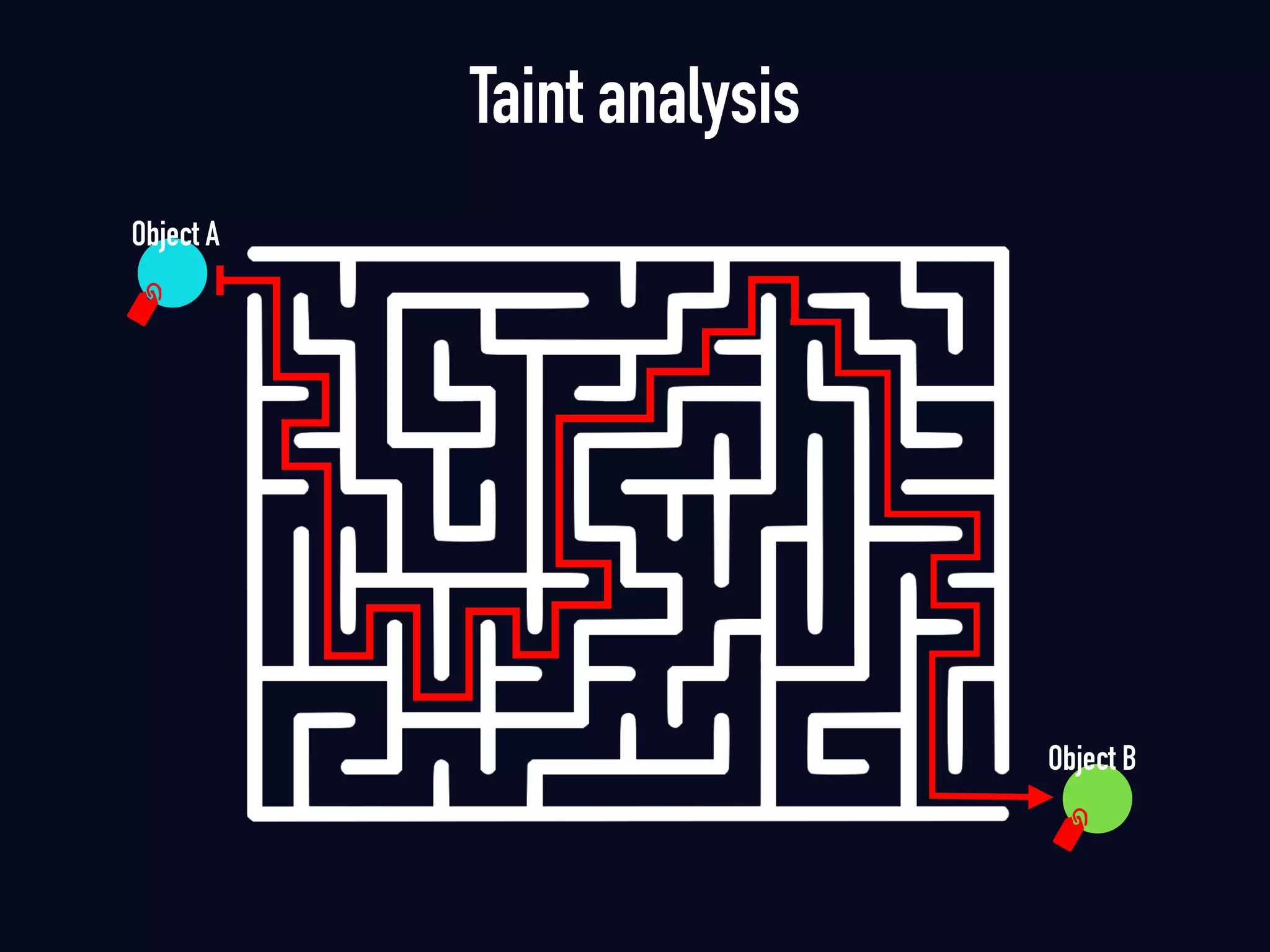
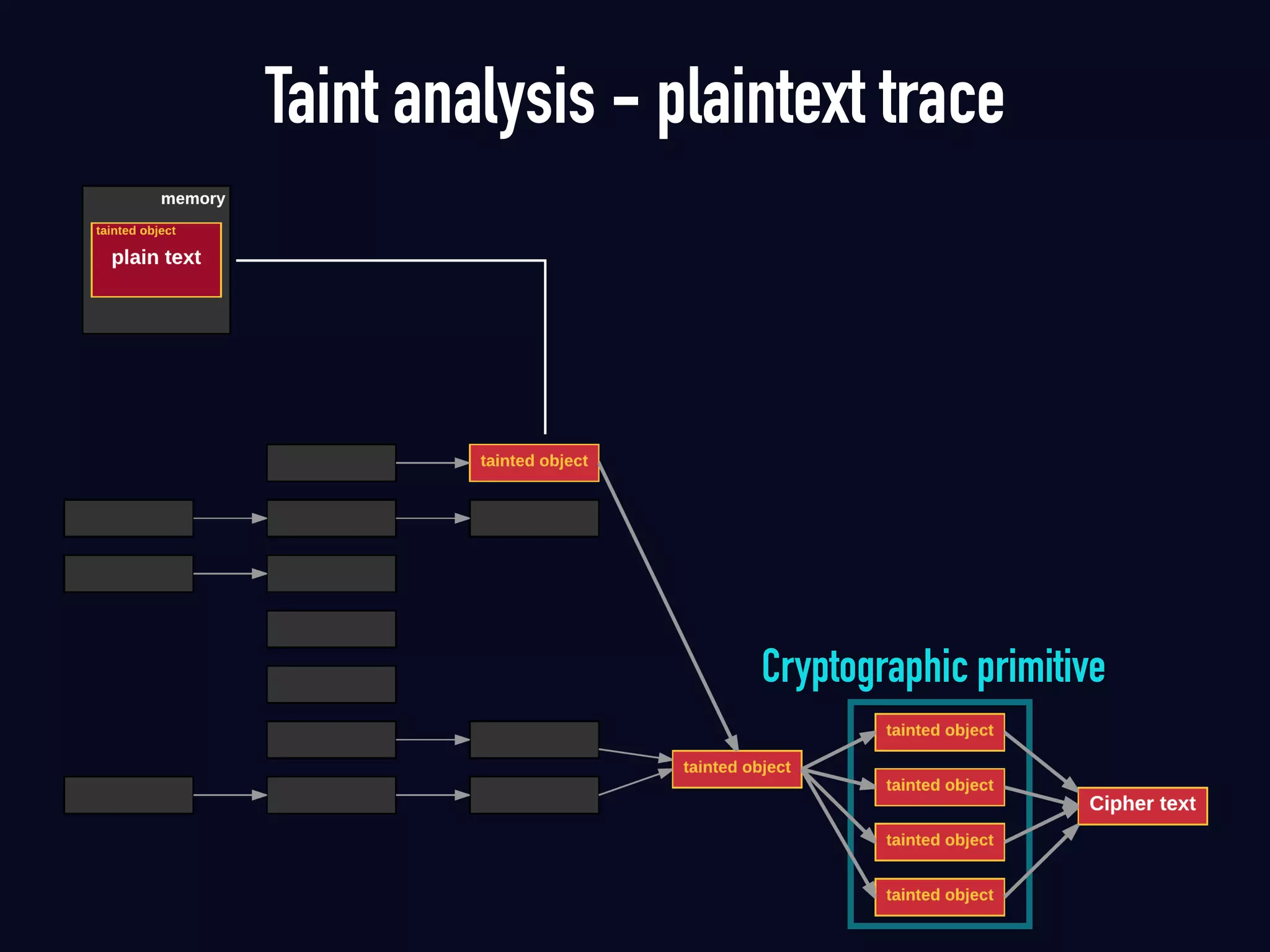
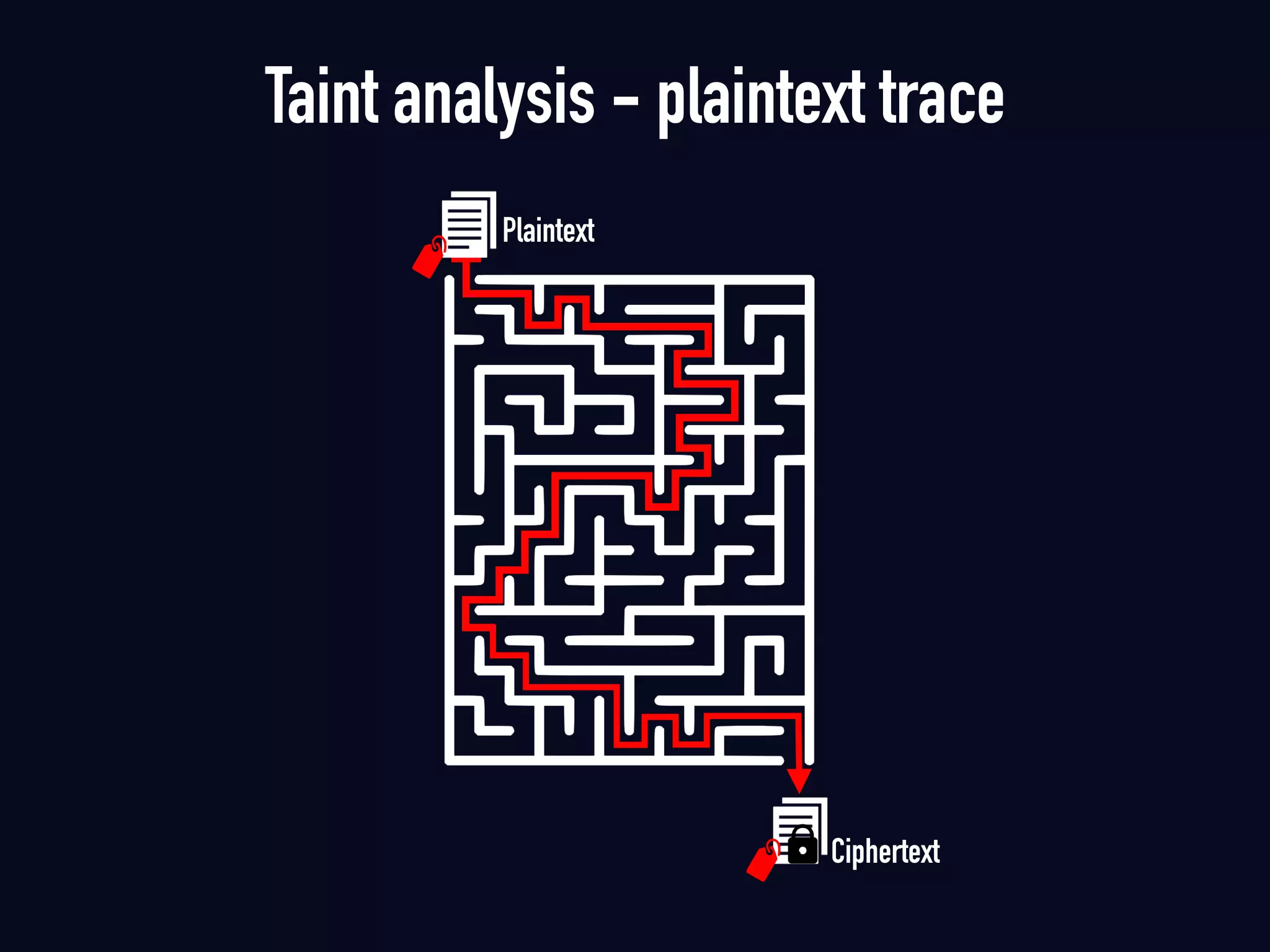
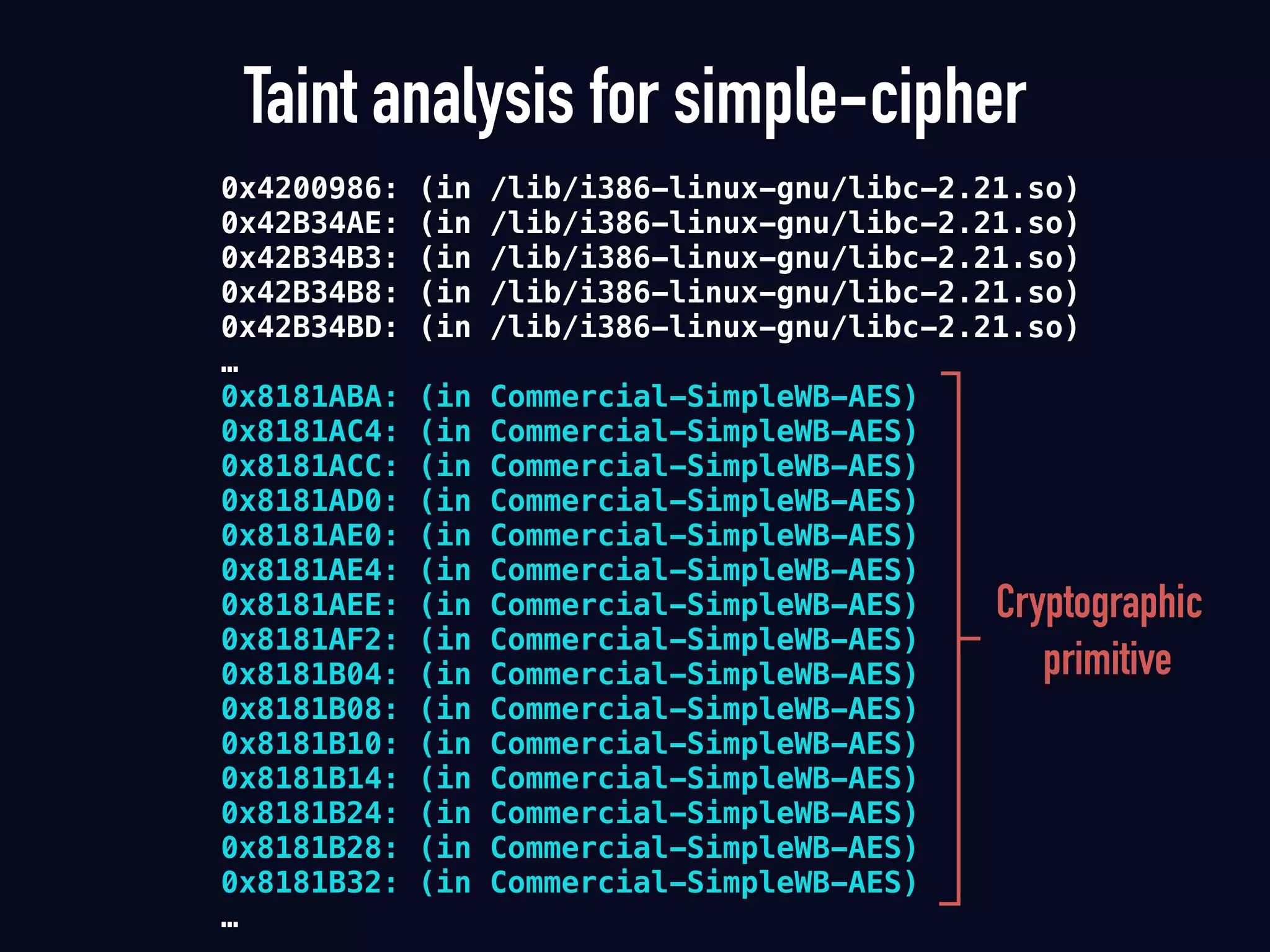
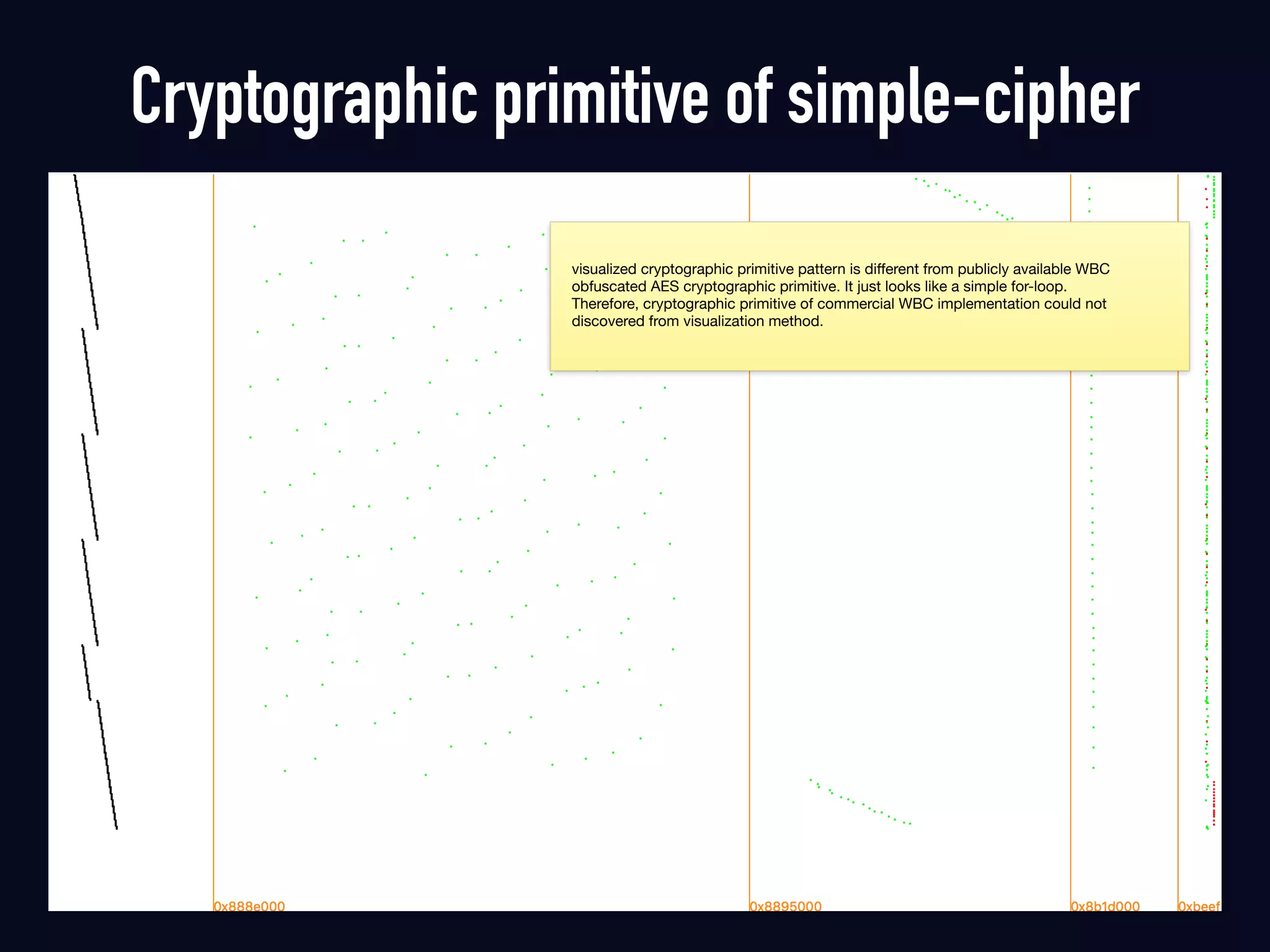
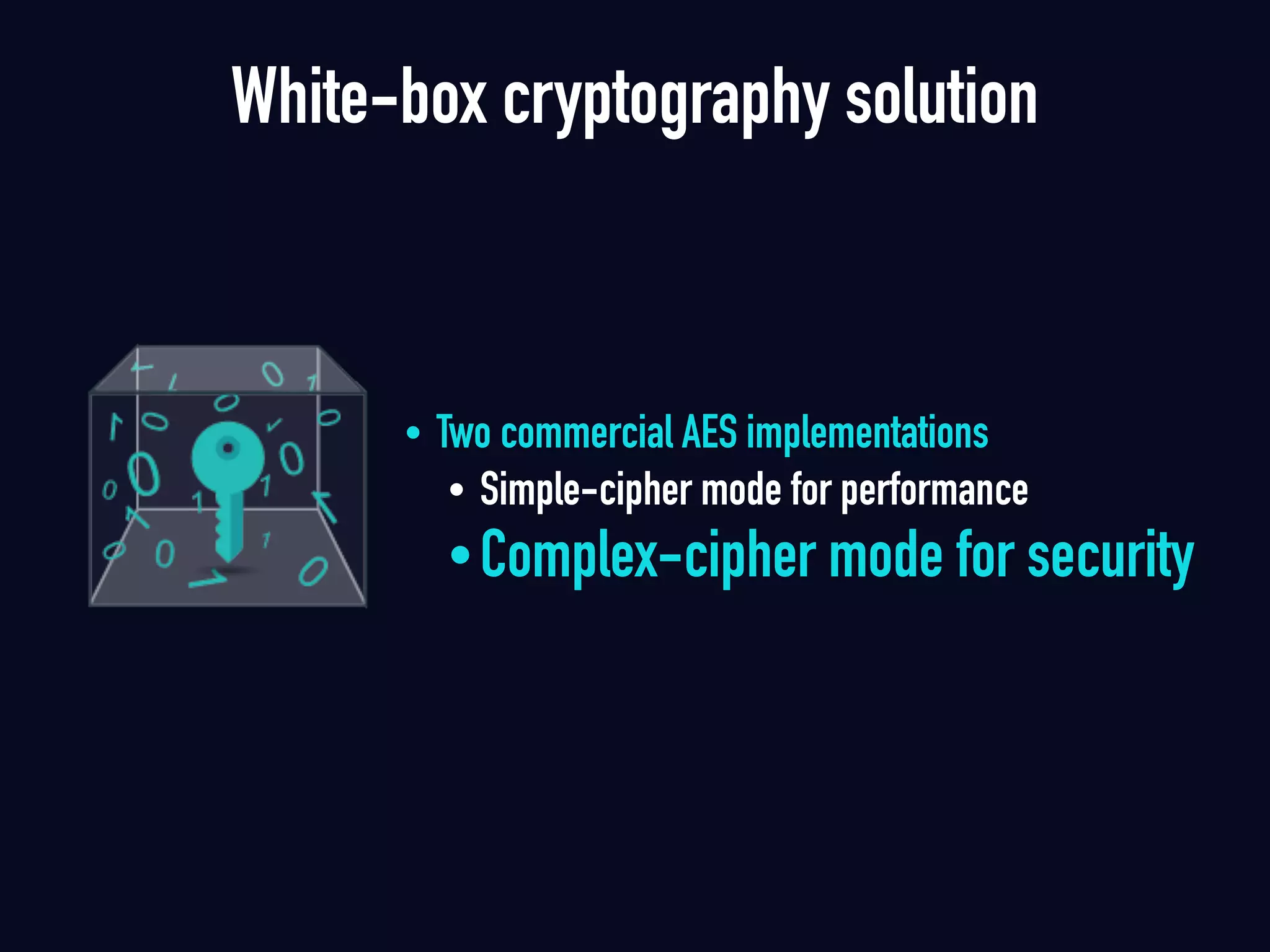
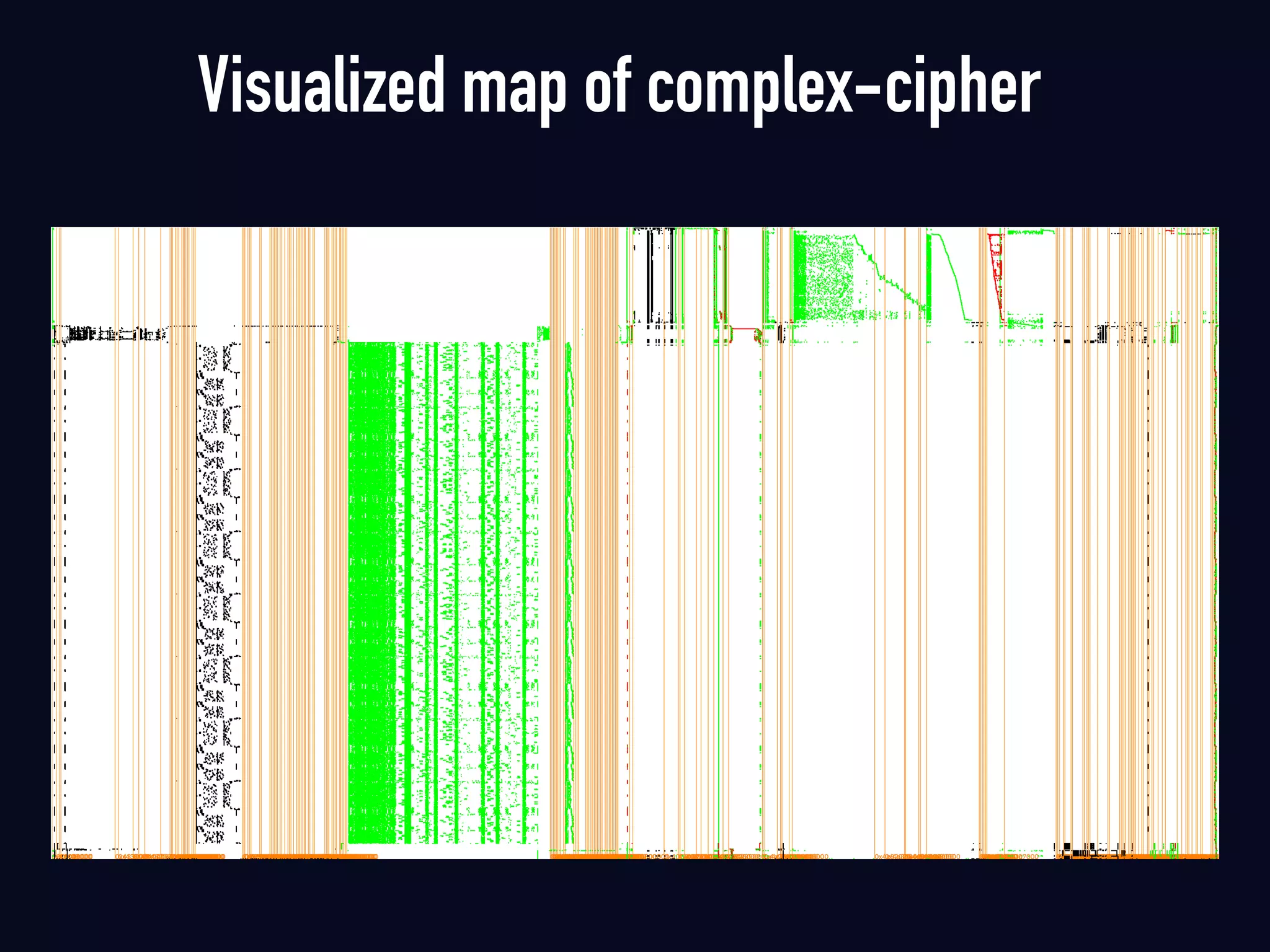
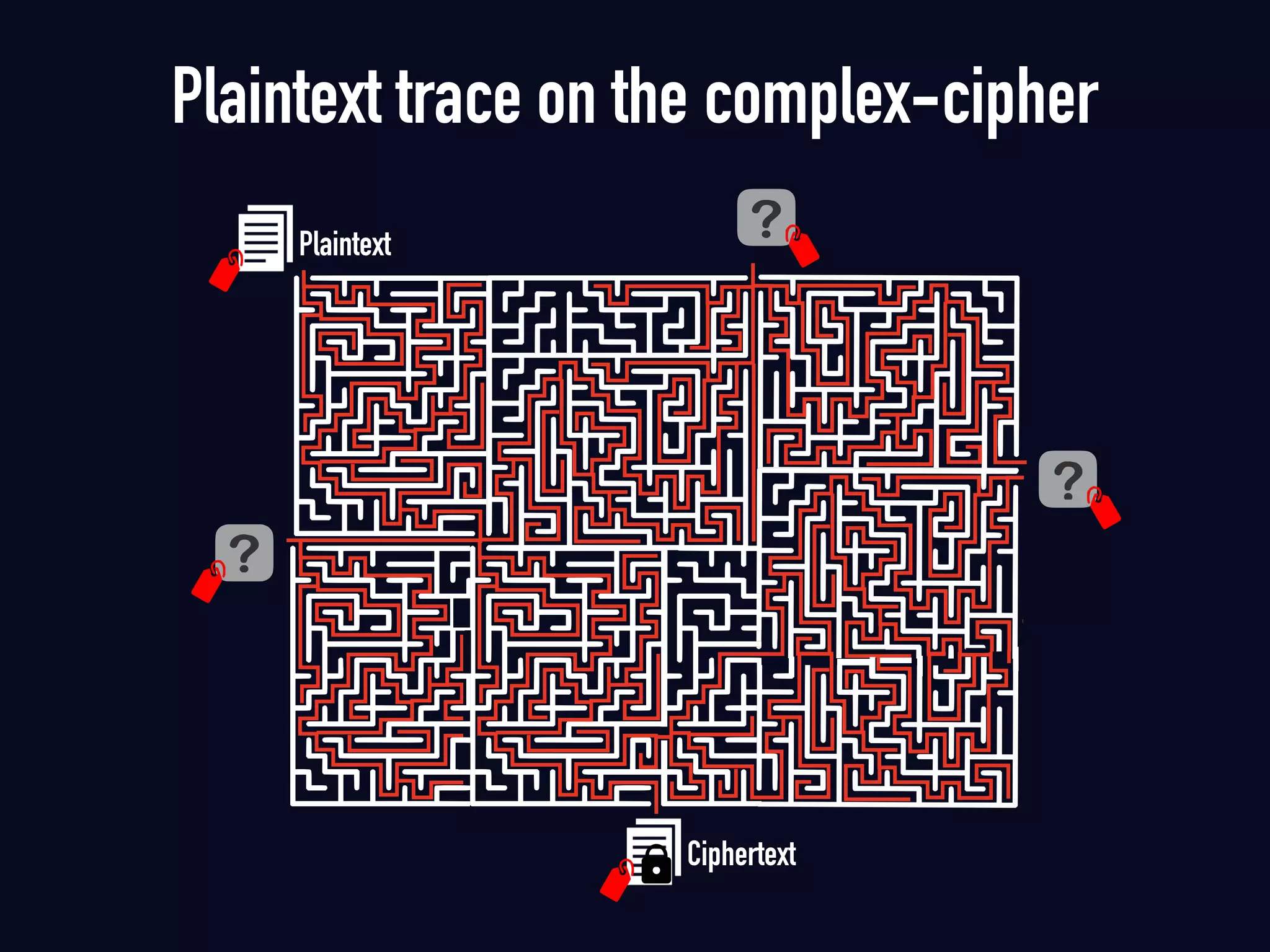
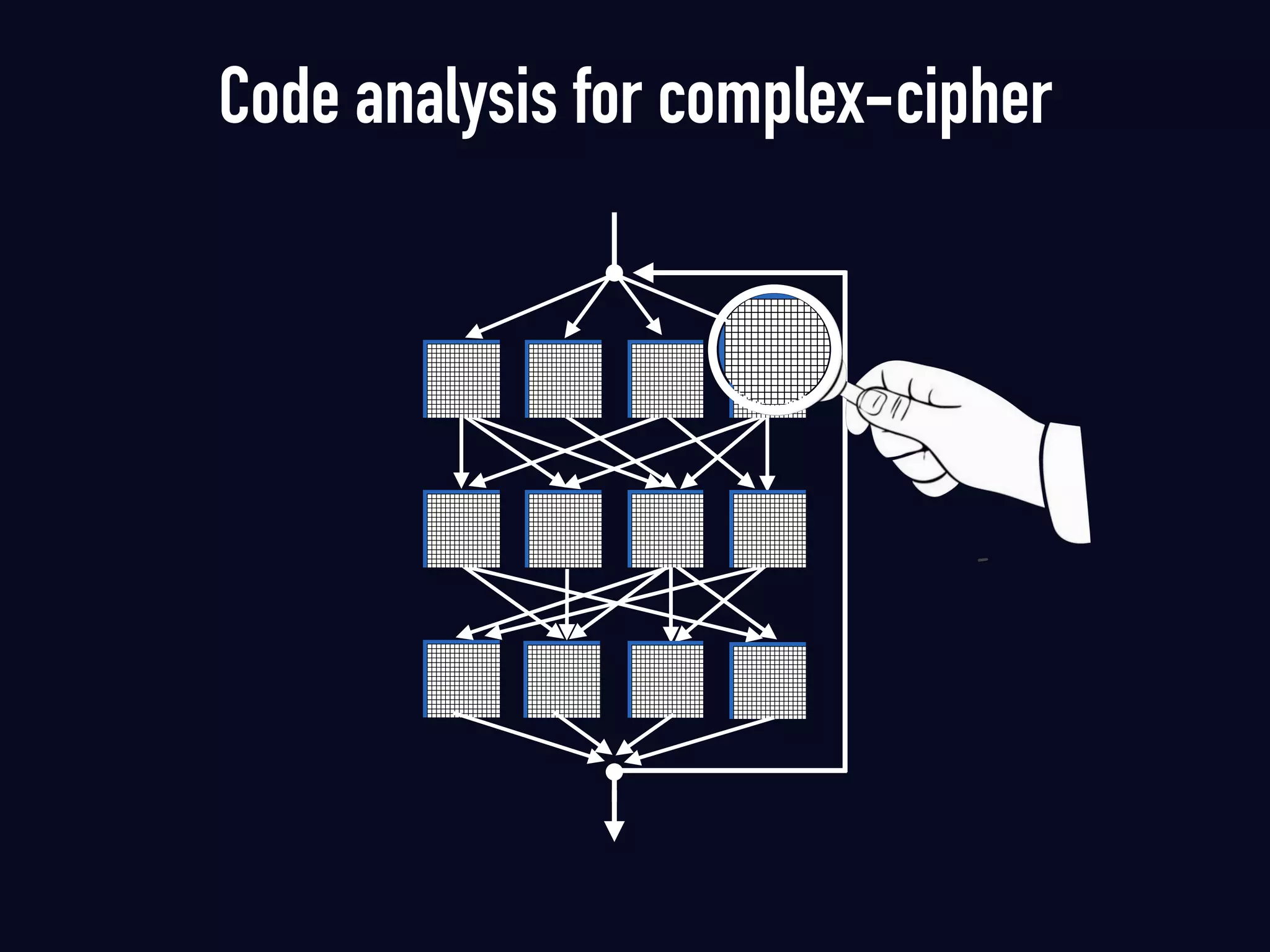
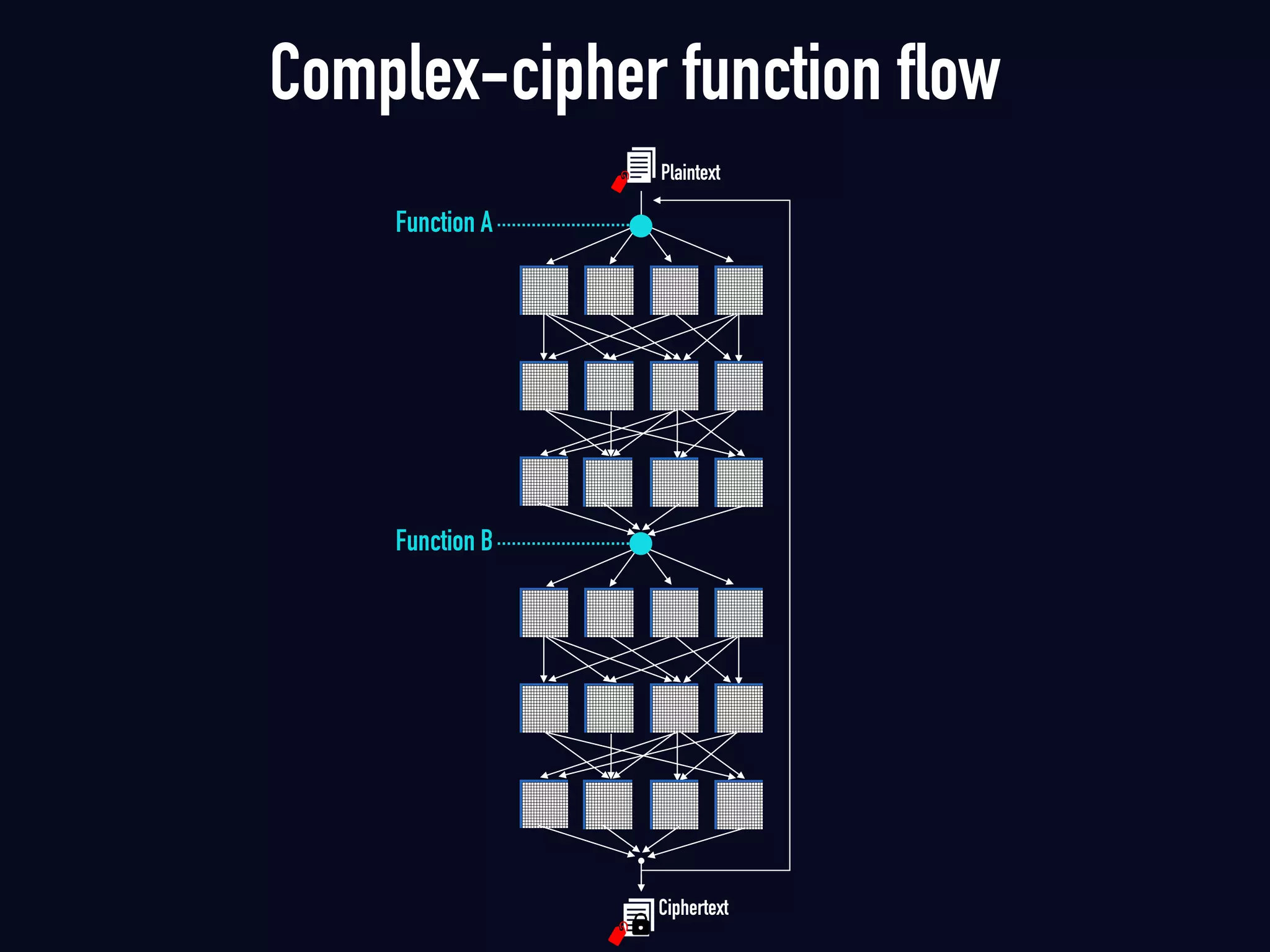
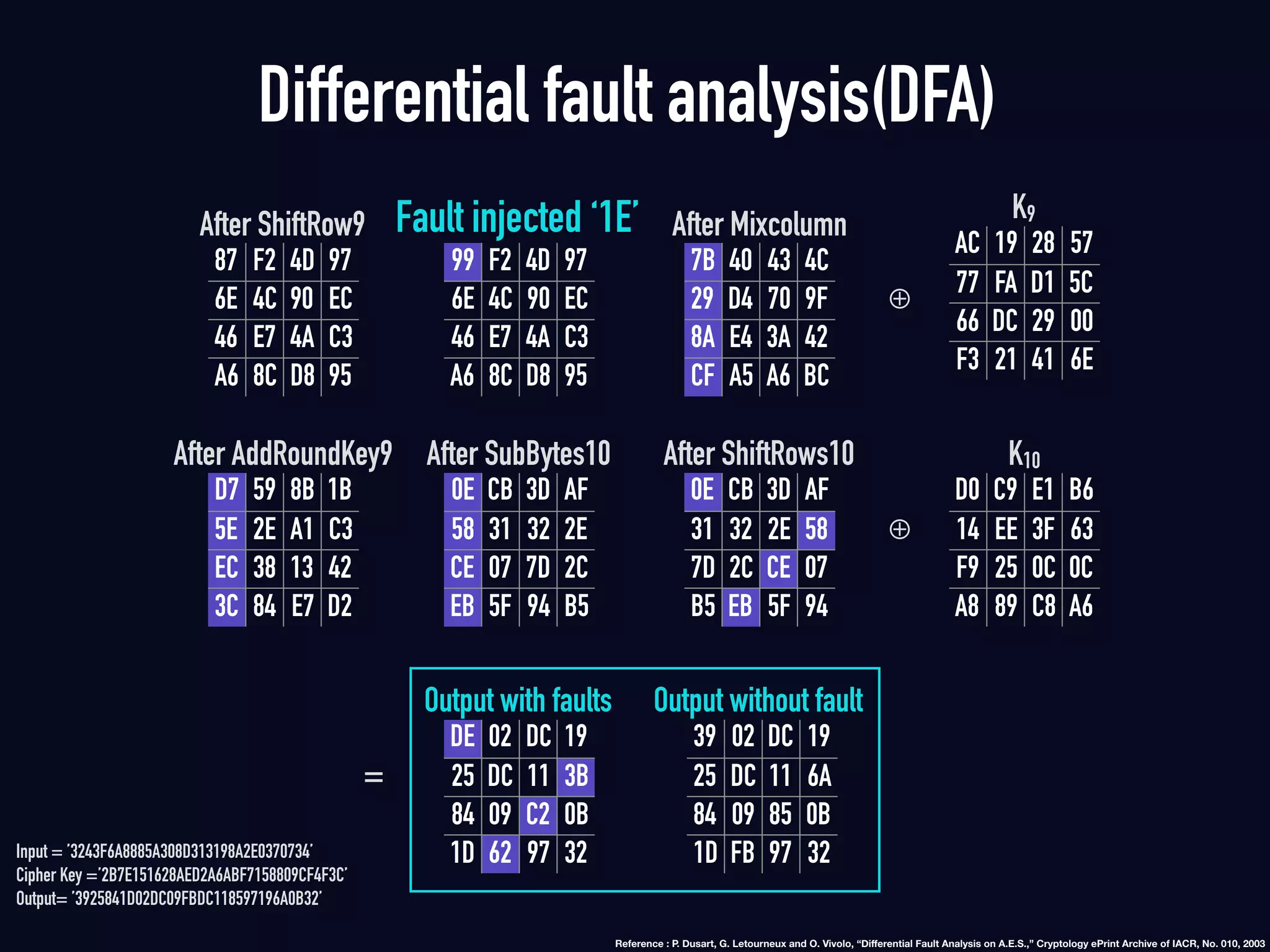
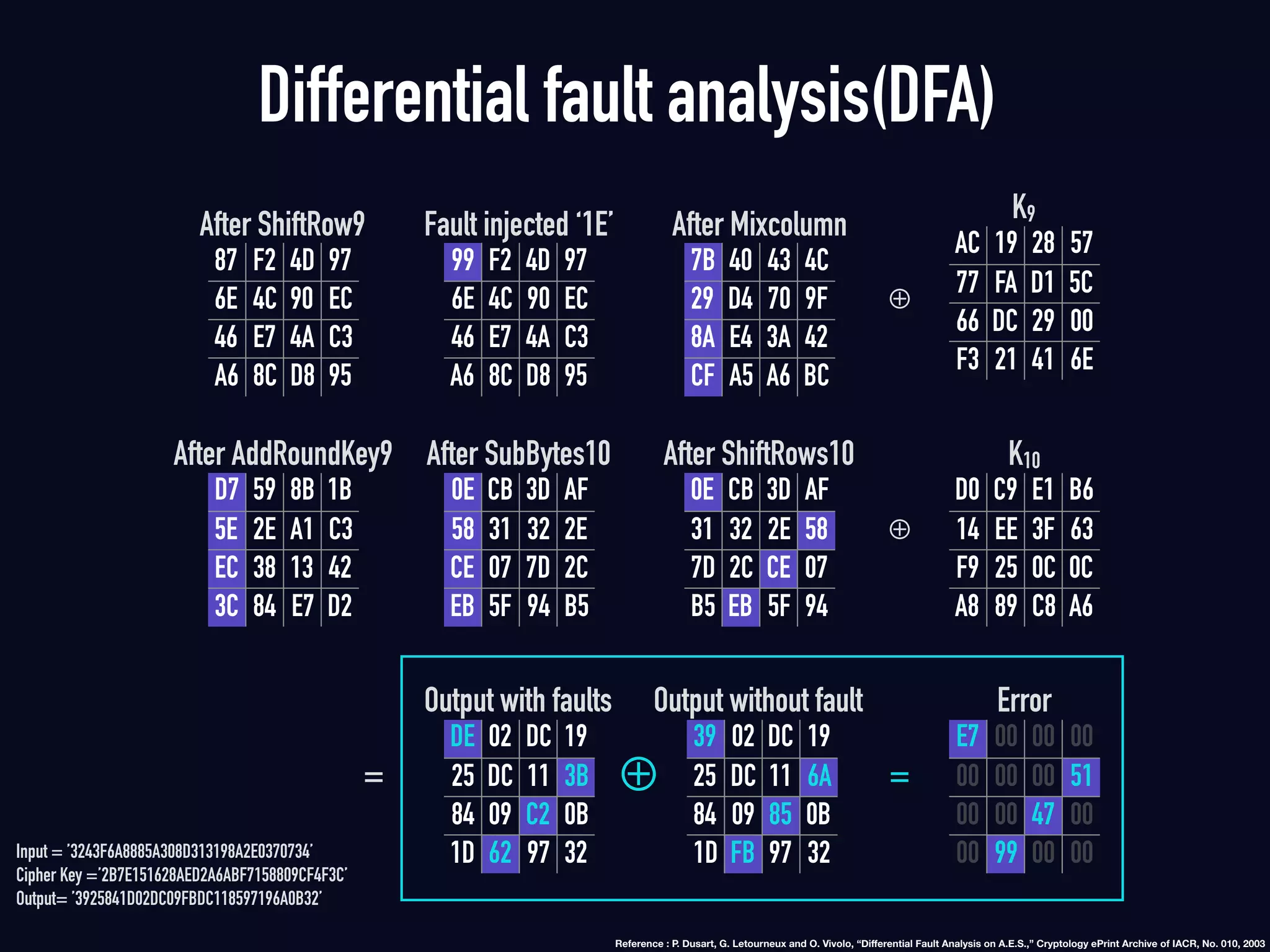
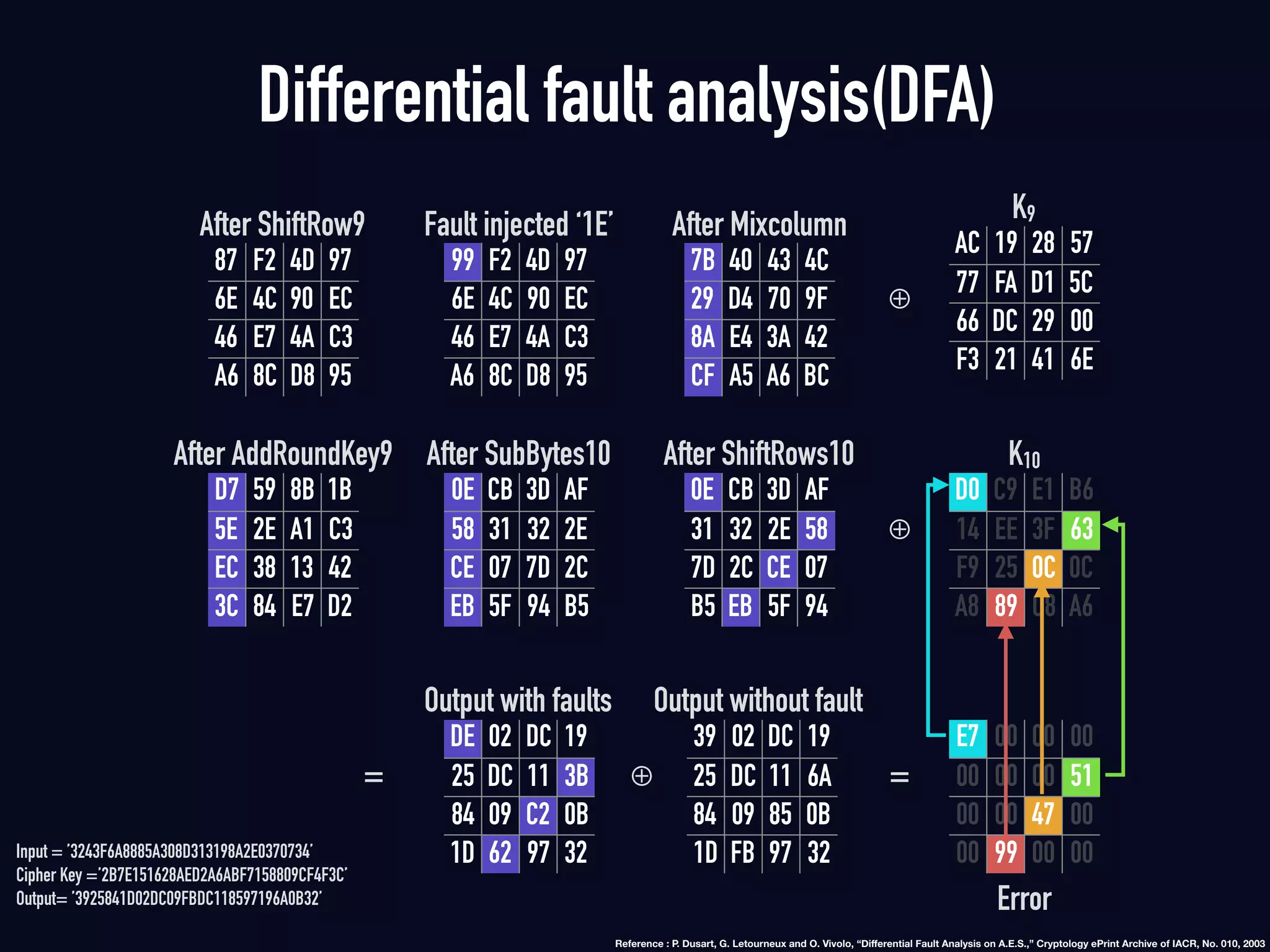
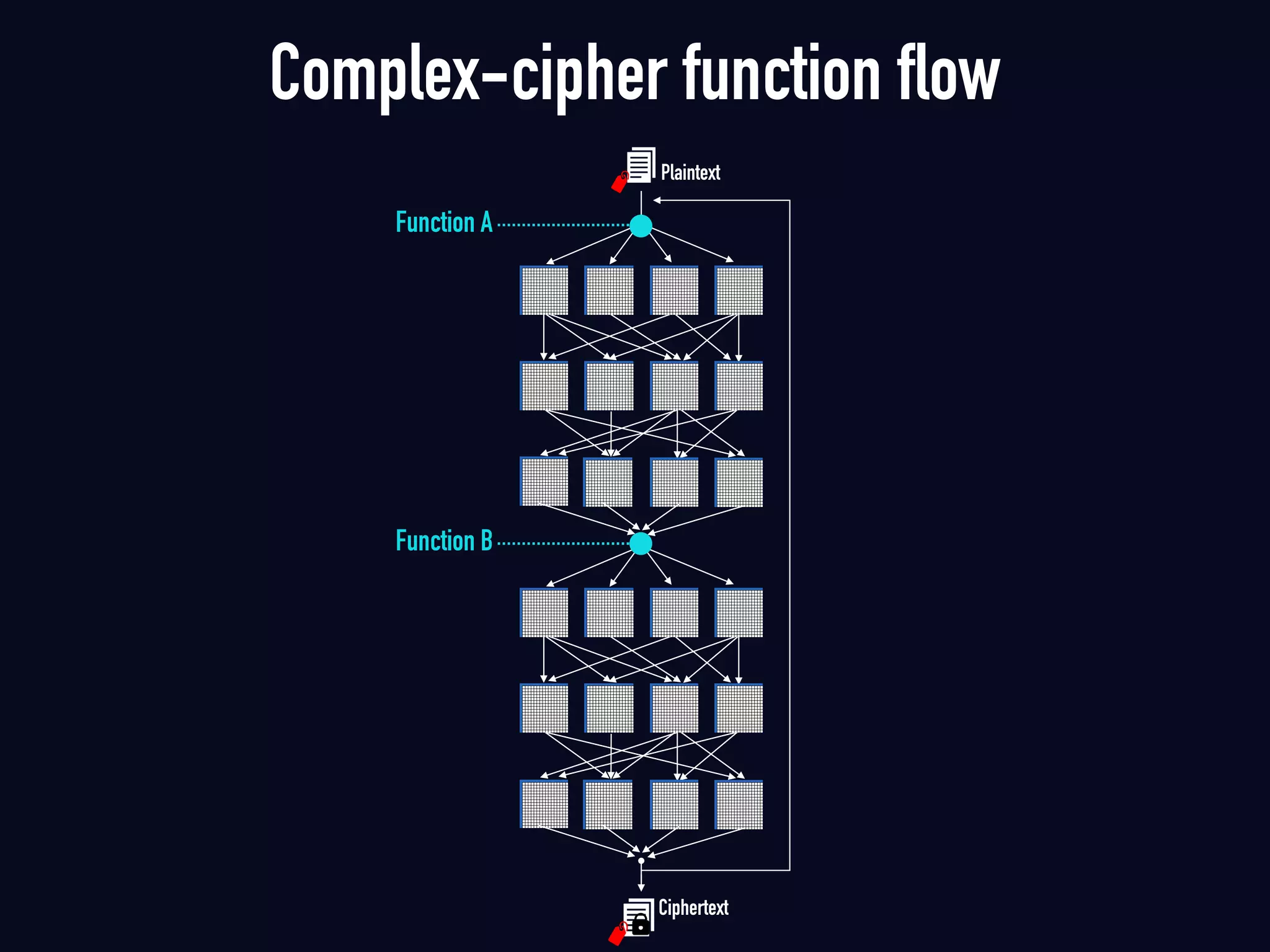
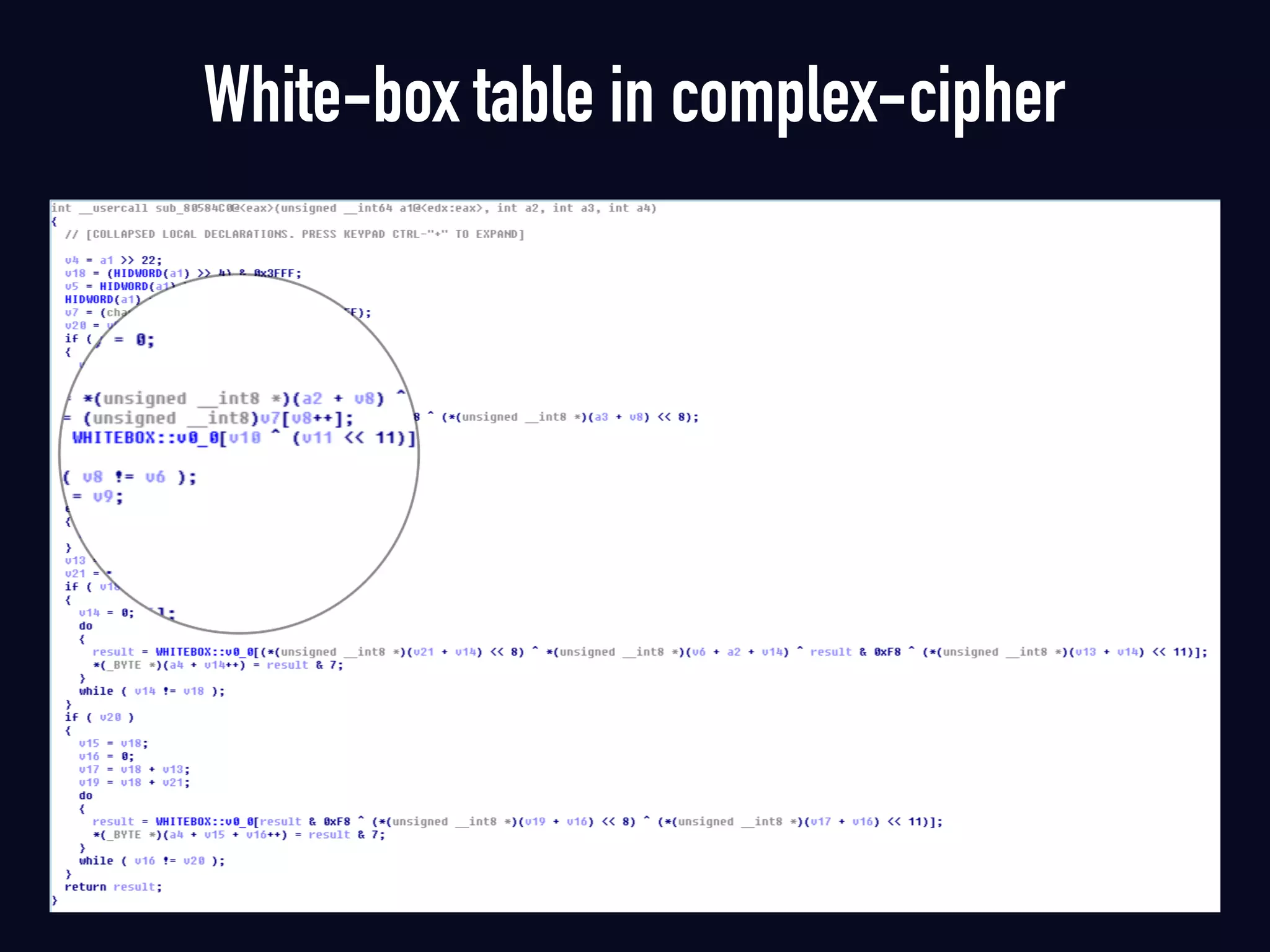
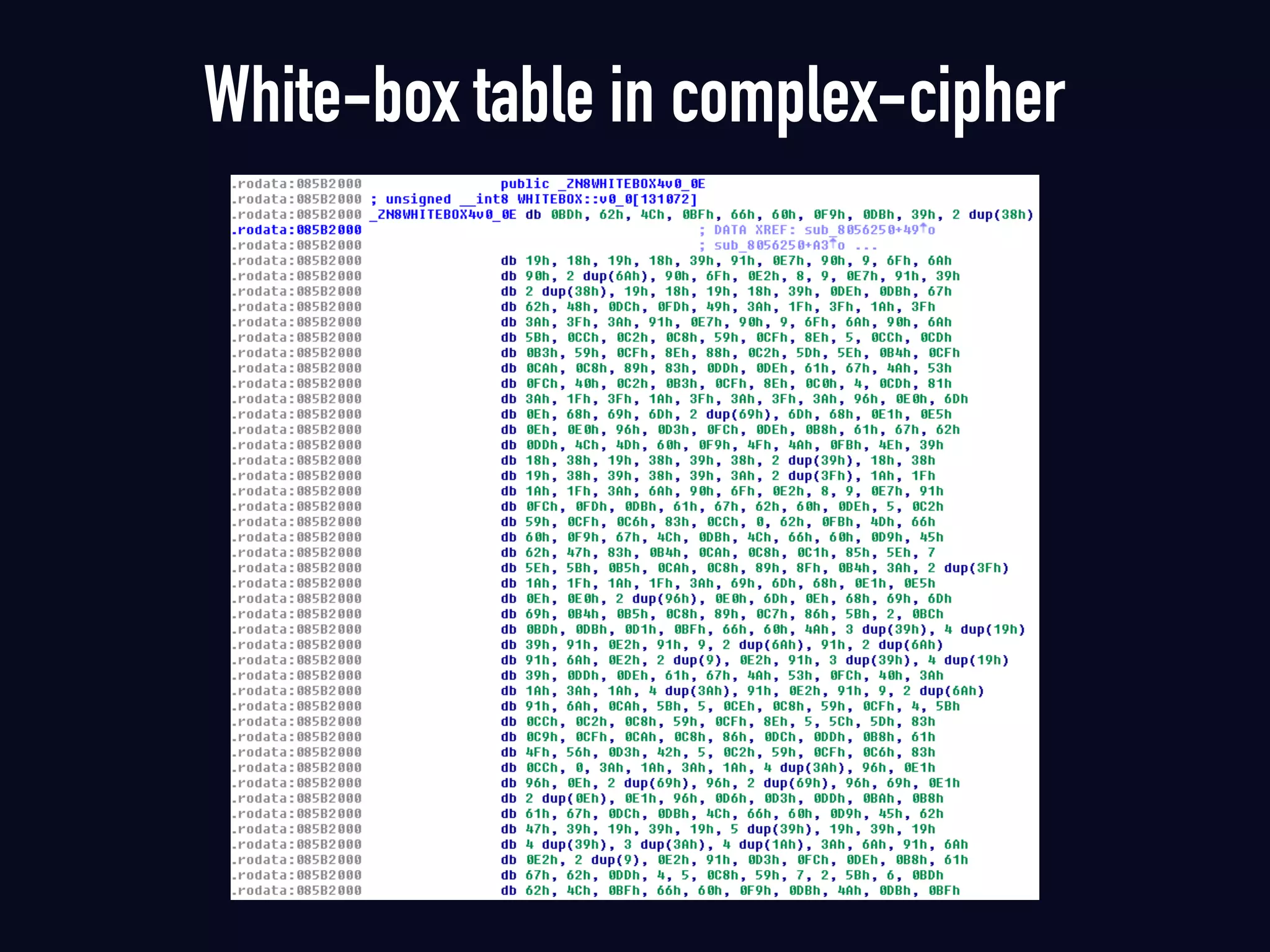
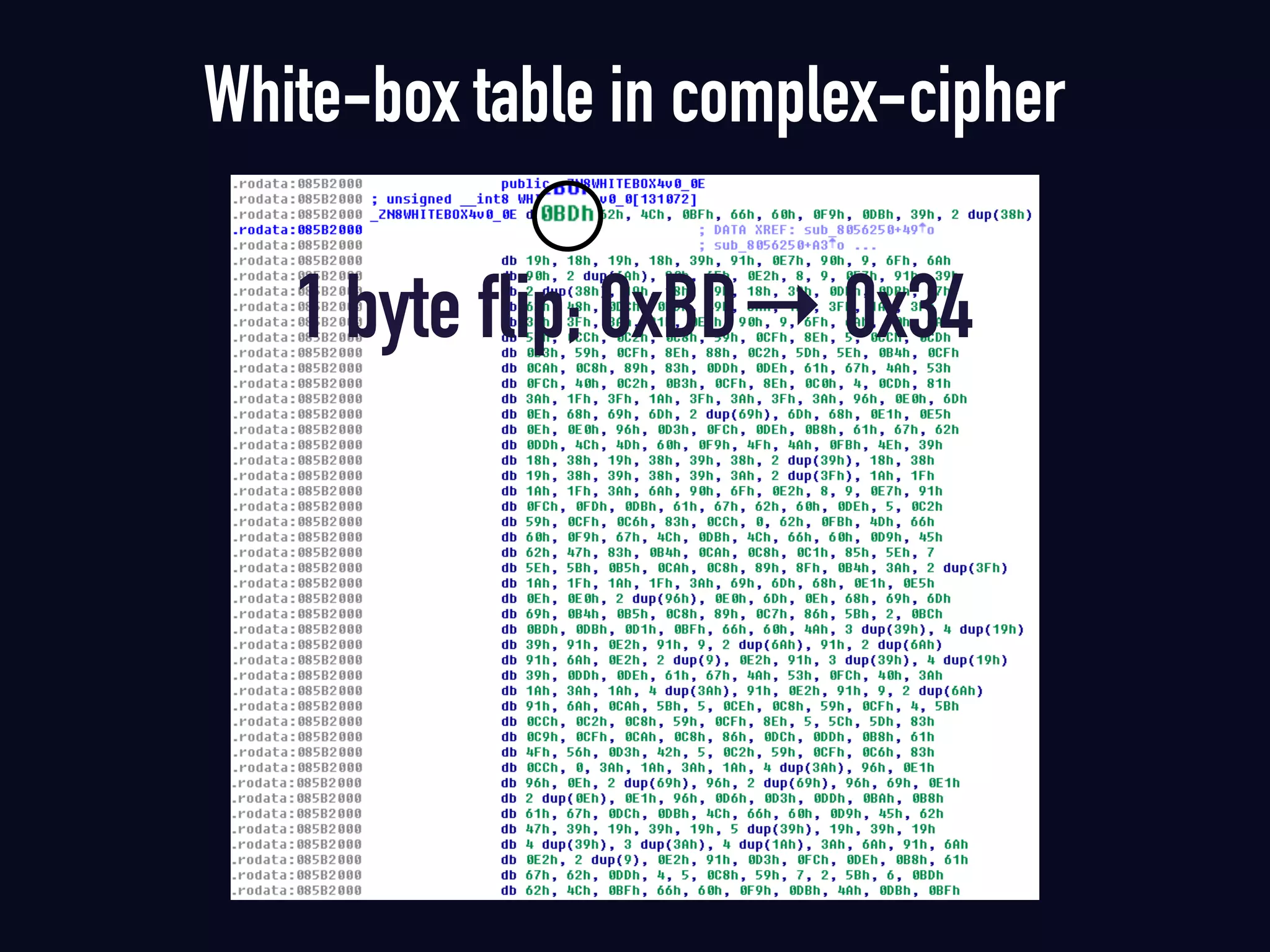
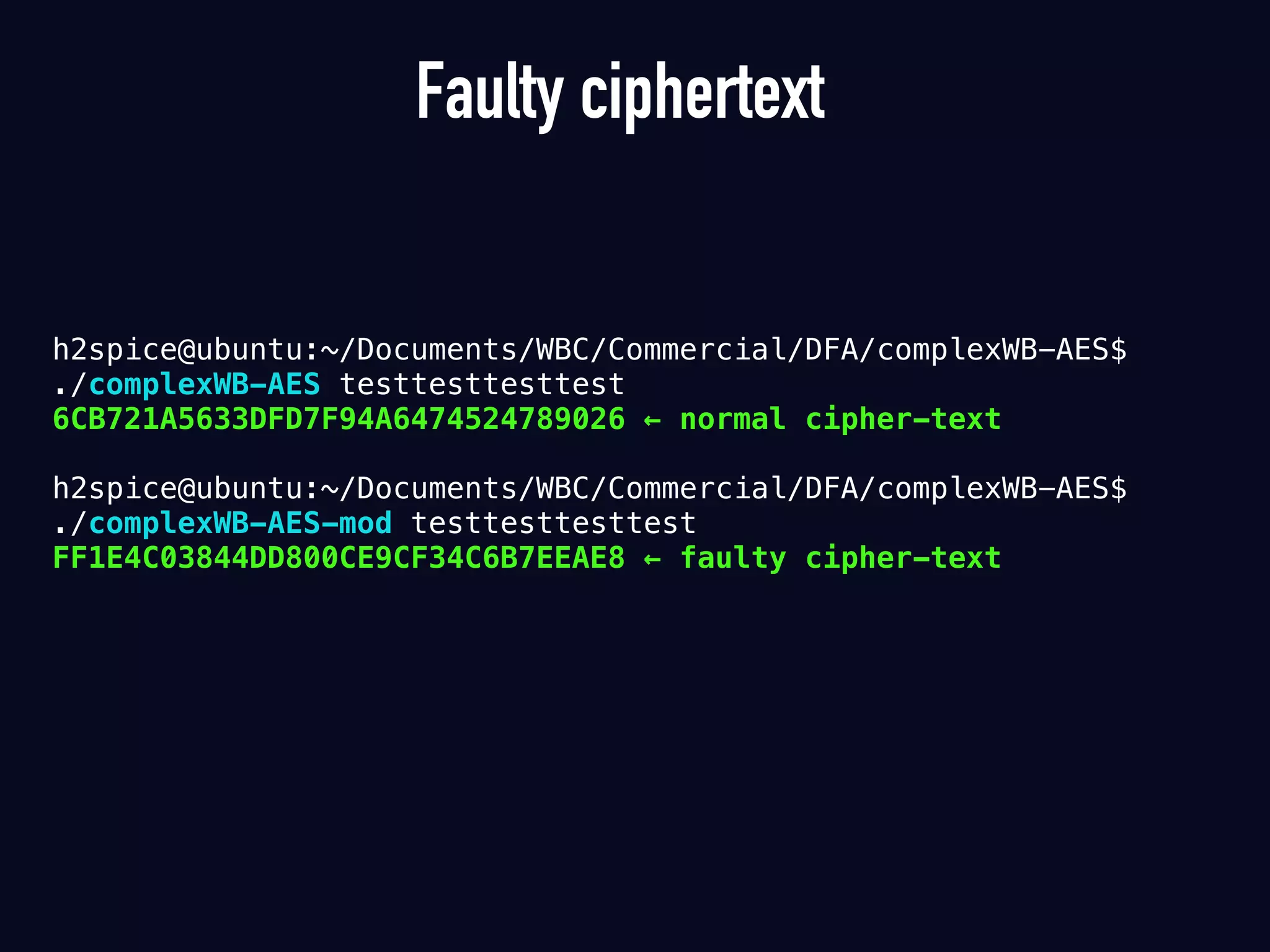
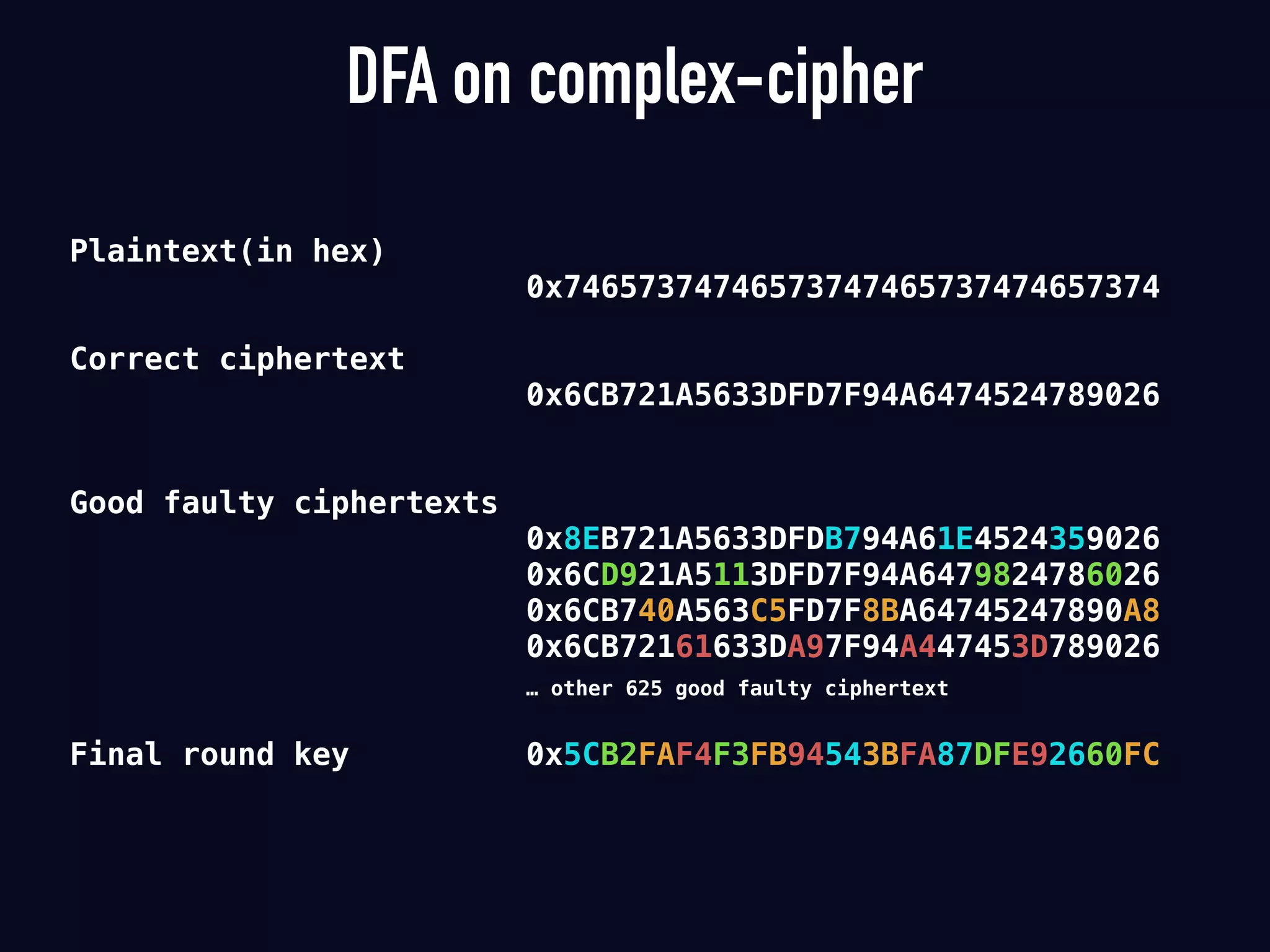
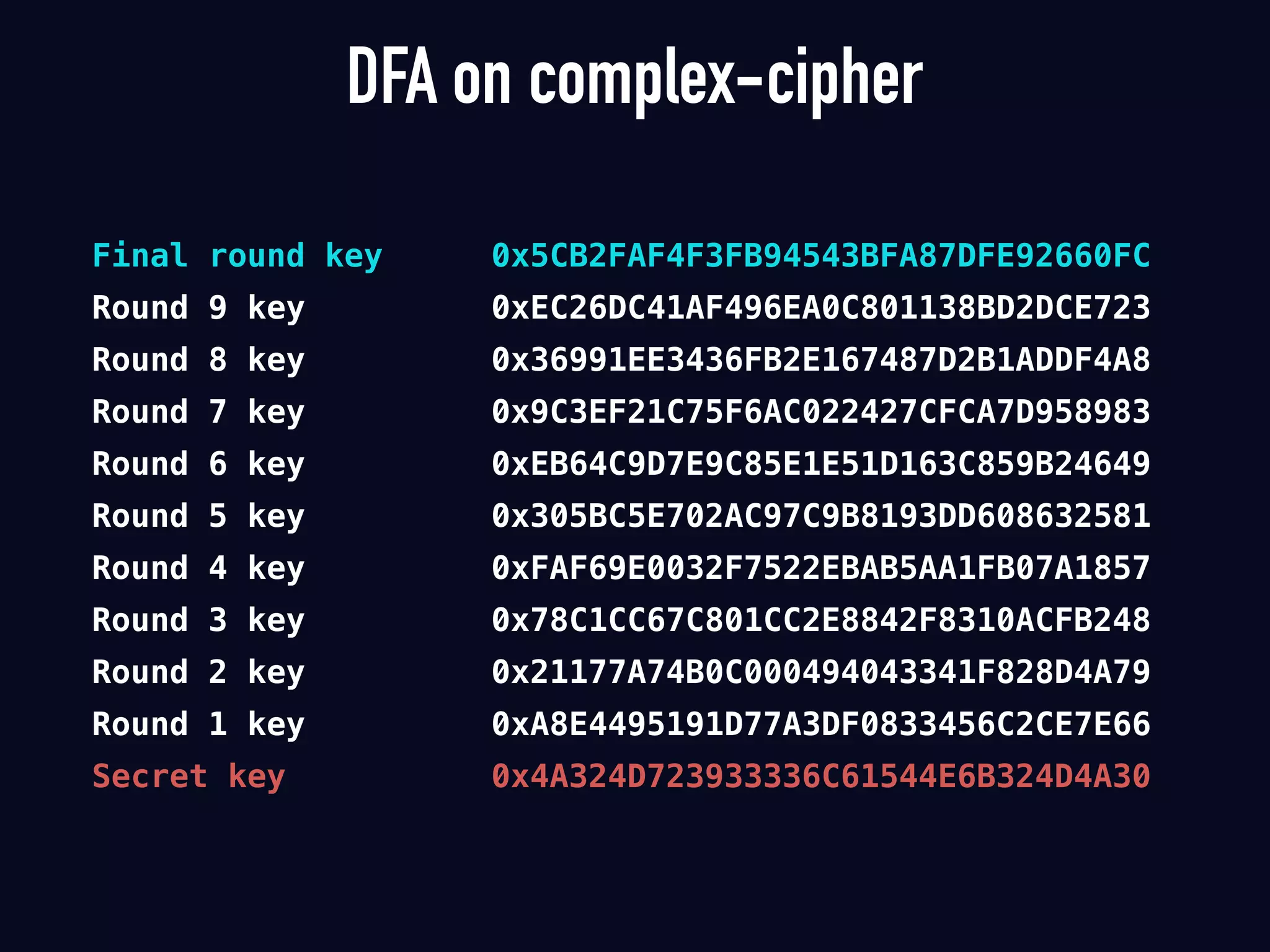
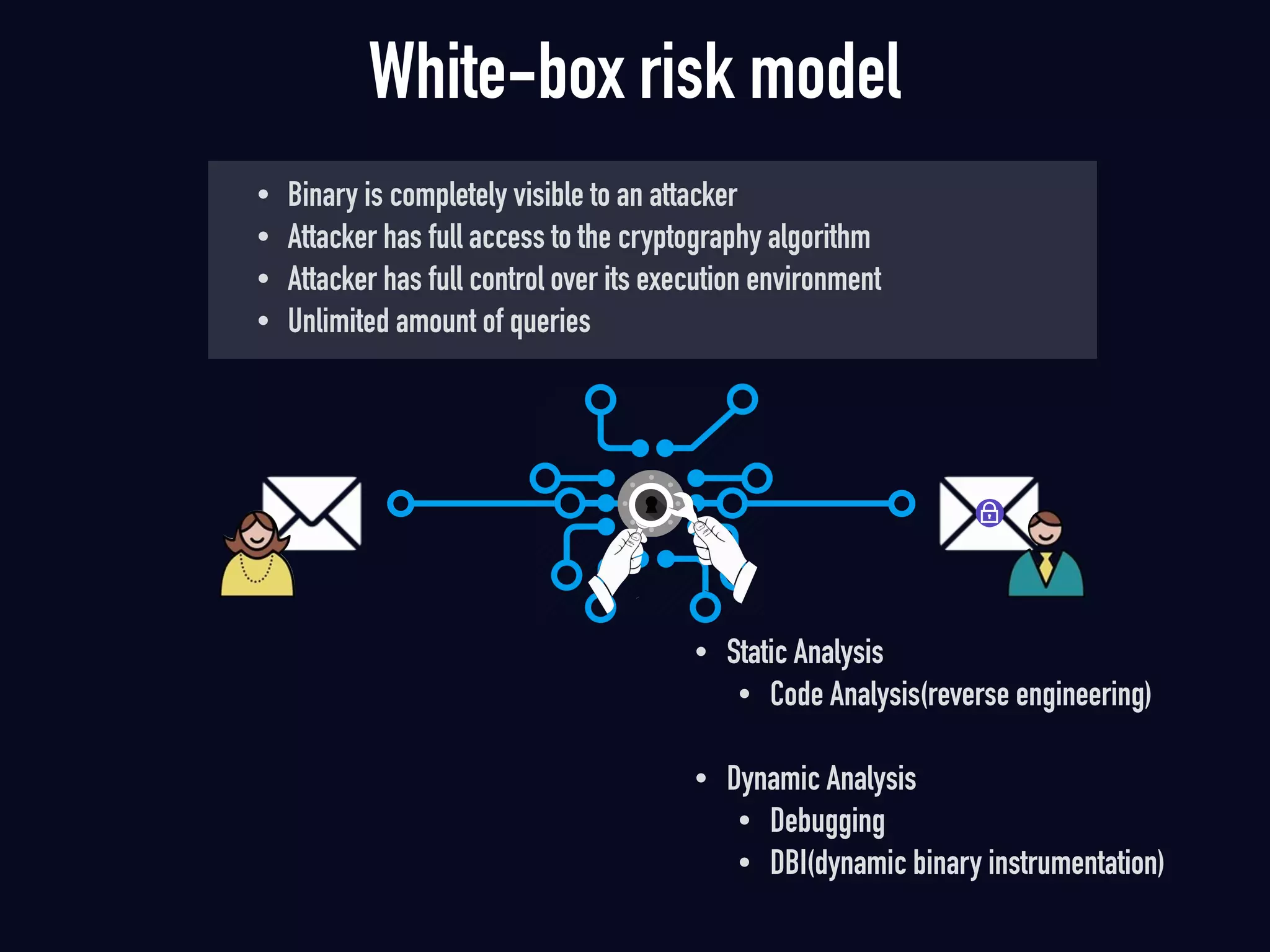
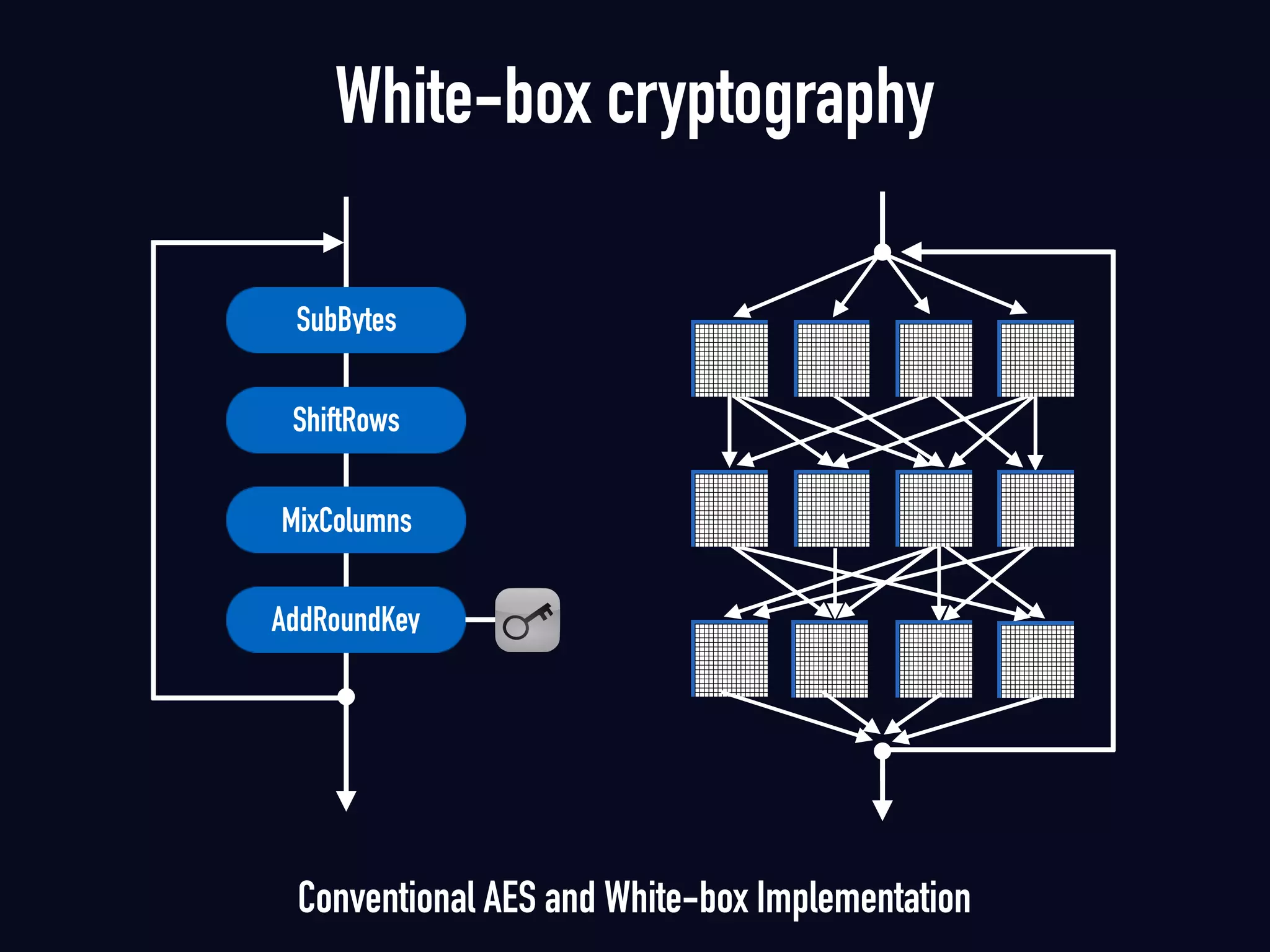
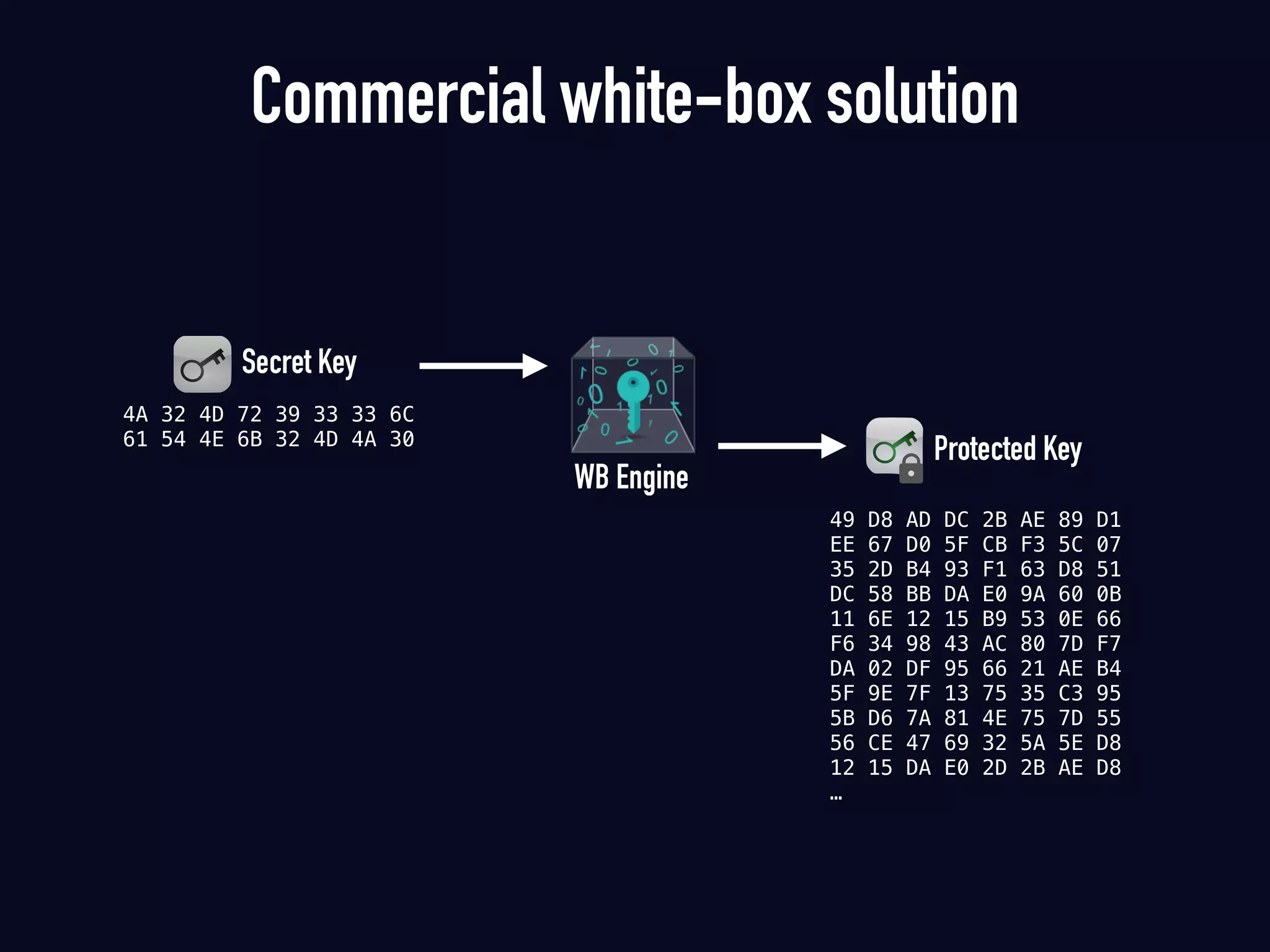
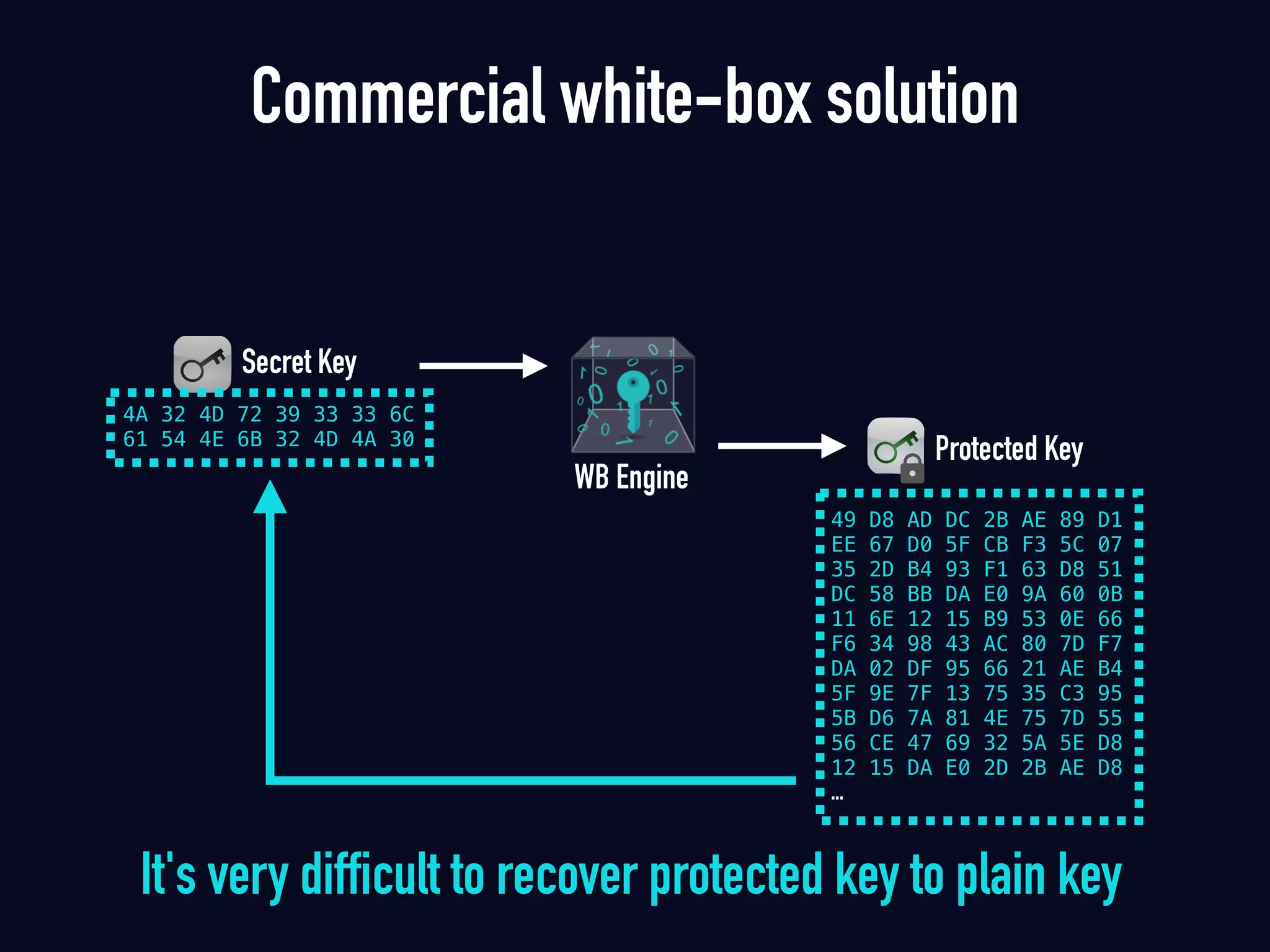
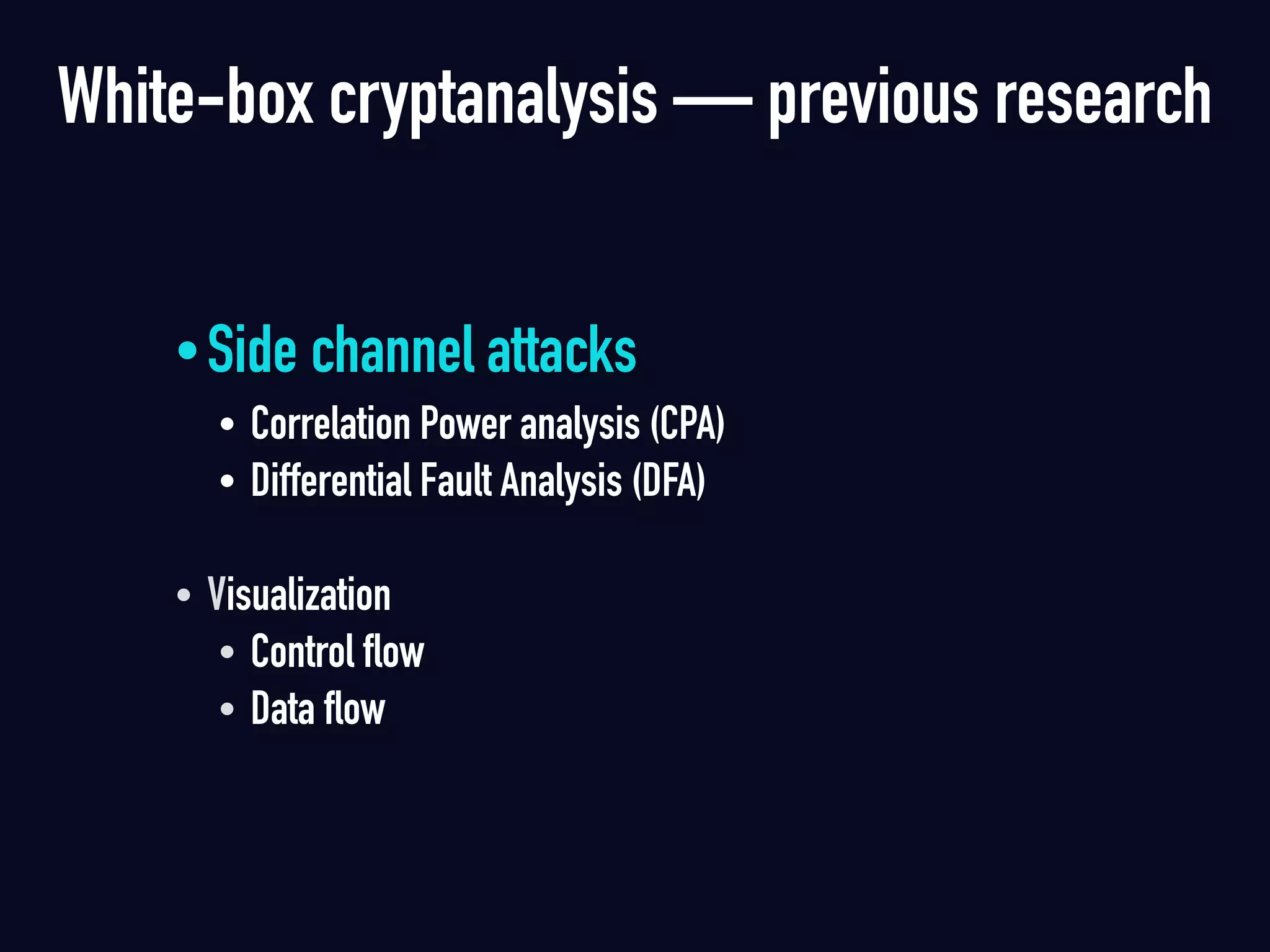
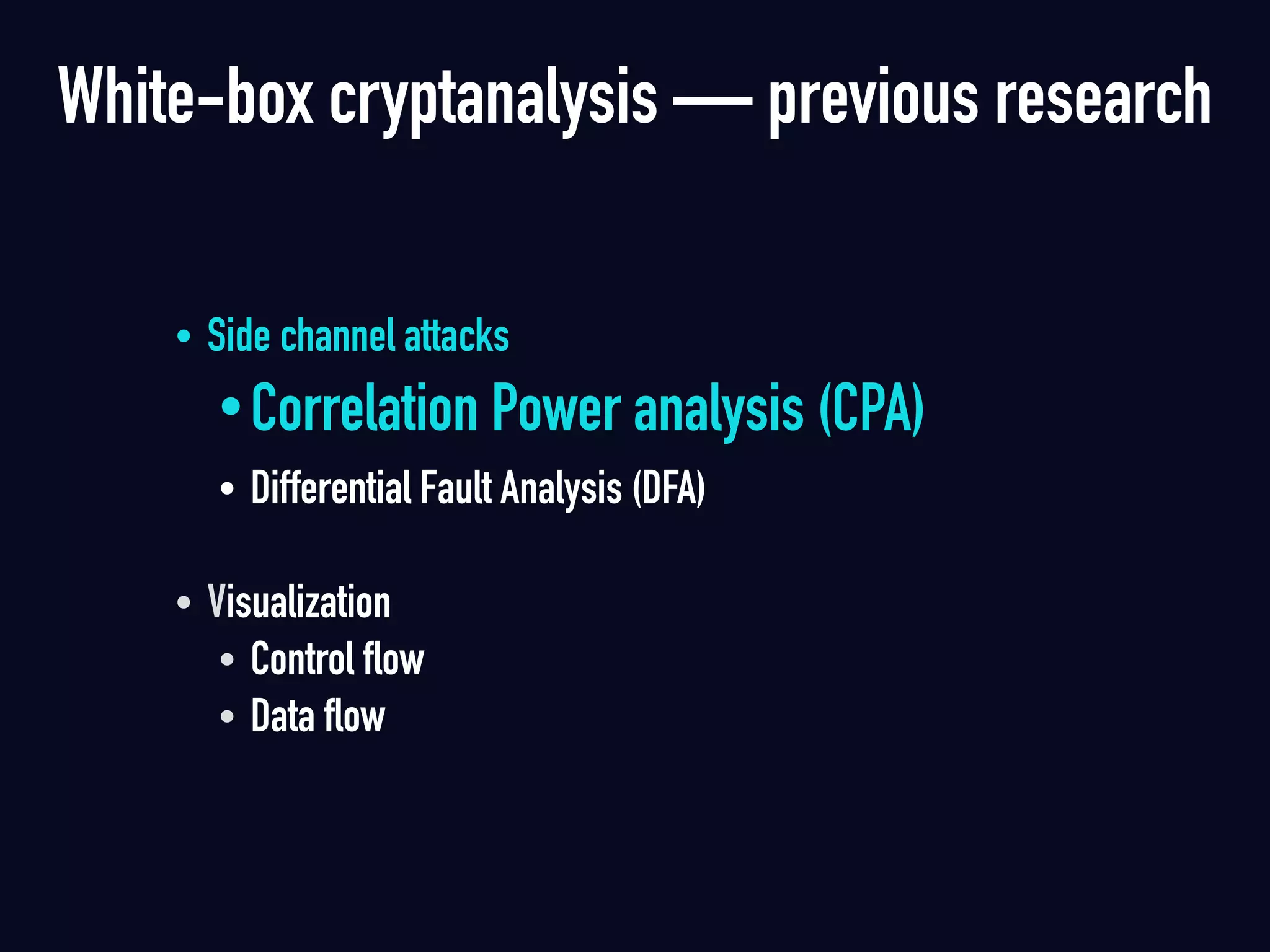
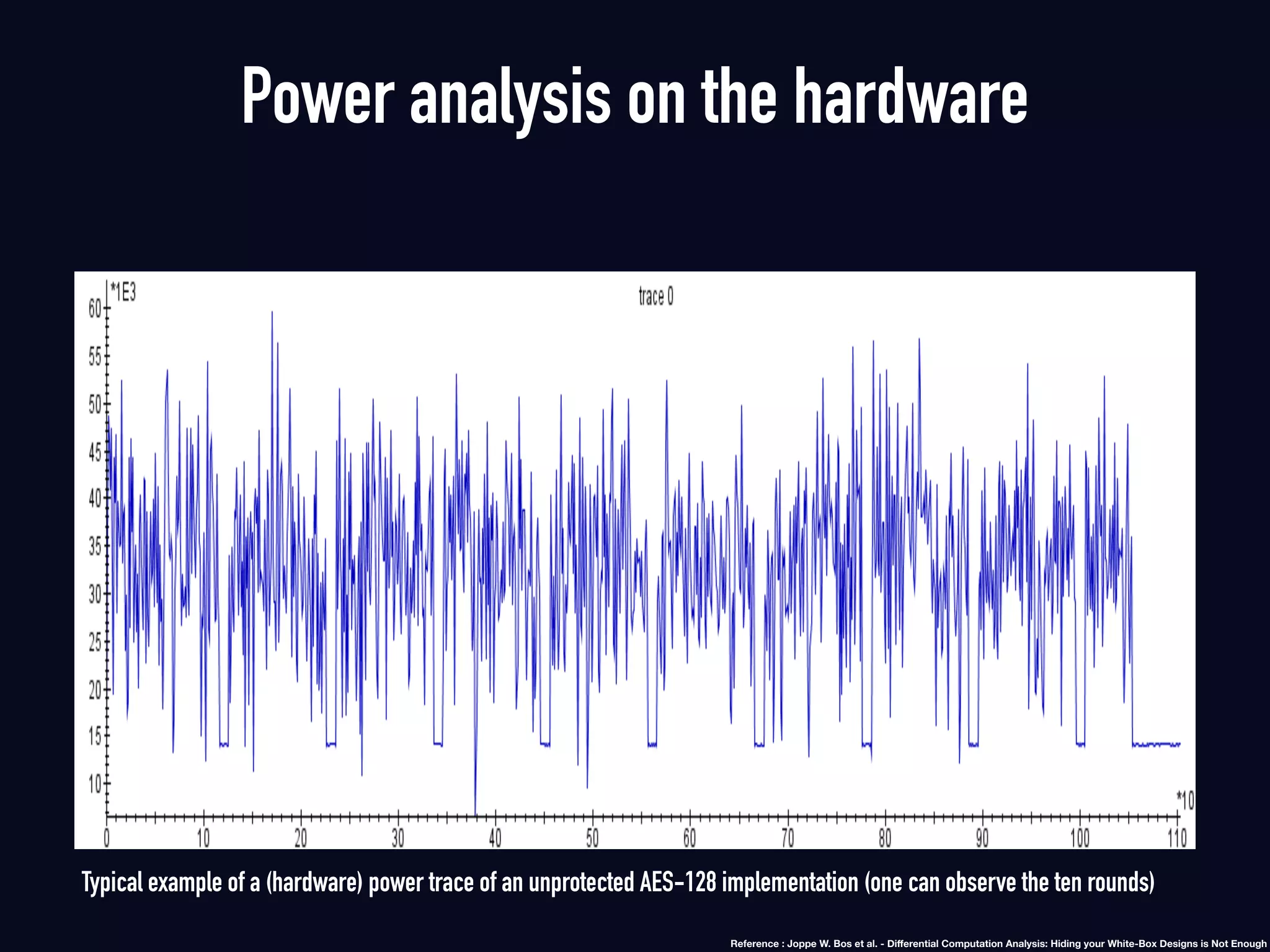
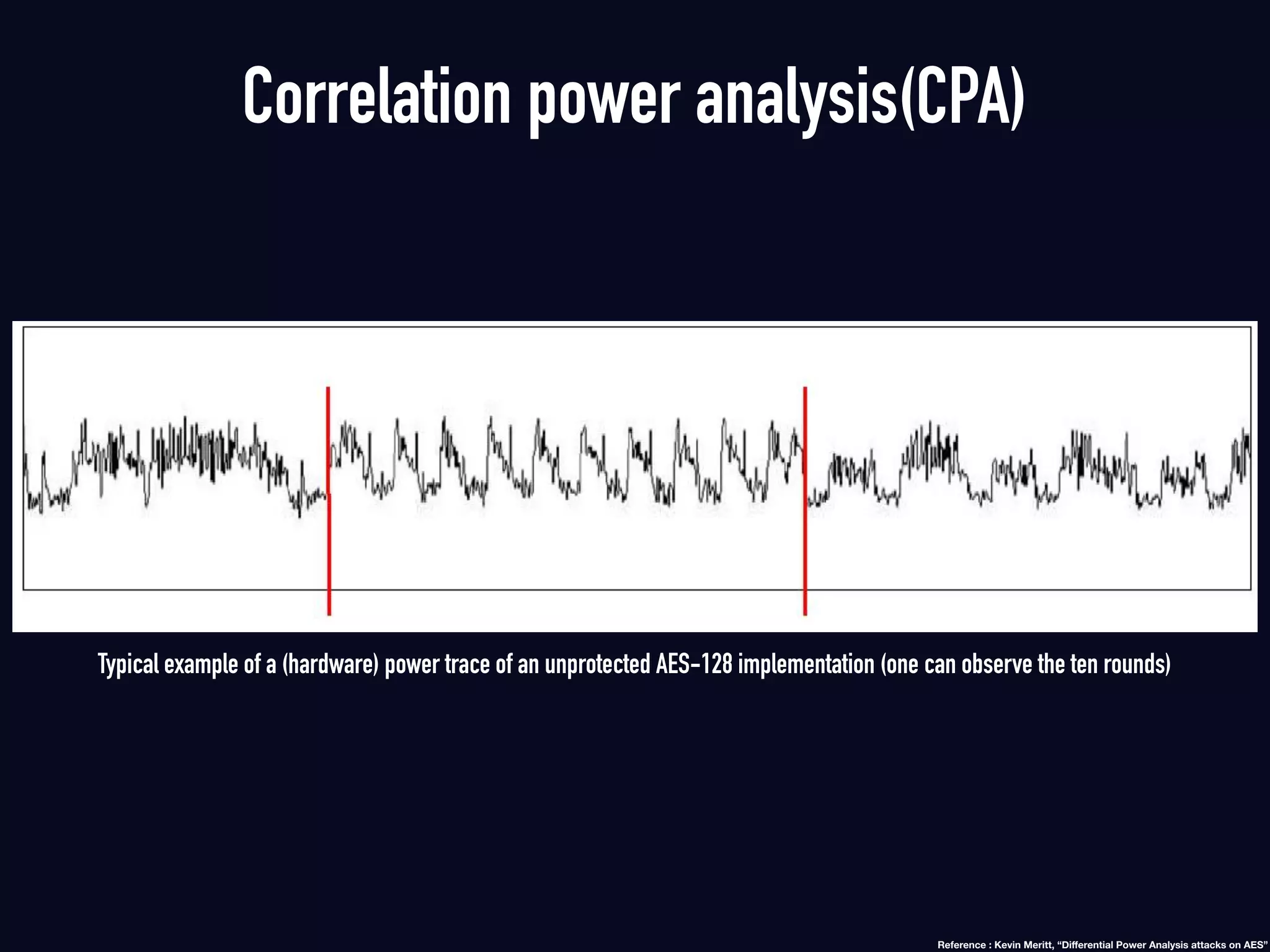
The document summarizes previous research on attacking white-box cryptography implementations and proposes new research directions. It discusses how white-box cryptography aims to protect secret keys by obscuring them in code, but all academic solutions have been broken. Previous attacks included power analysis, fault injection, code visualization and analysis. The document proposes using taint analysis to trace plaintext/ciphertext through code as an alternative to visualization. It also proposes differential fault analysis and code analysis to attack white-box implementations.


![Software execution trace with DBI
[.code execution]
start_addr : 000000000400c1b7
end_addr : 000000000400c1d0
instruction info
000000000400c1b7: mov eax, dword ptr [ebp + 8]
000000000400c1ba: add dword ptr [ebx + 0x550], 1
000000000400c1c1: mov edx, dword ptr [eax + 0x228]
000000000400c1c7: mov edi, dword ptr [eax + 0x224]
000000000400c1cd: mov dword ptr [ebp - 0x44], edx
000000000400c1d0: jmp 0x400b3c1
[.mem write]
code_addr : 000000000400c1ba
mem_addr : 0000000004023550
size : 4
data : 30040000
[.mem write]
code_addr : 000000000400c1c1
mem_addr : 0000000004025da8
size : 4
data : 347b0608
[.mem write]
code_addr : 000000000400c1c7
mem_addr : 0000000004025da4
size : 4
data : 38390204
[.mem read]
code_addr : 000000000400c1b7
mem_addr : 00000000beef7470
size : 4
data : 805b0204
[.mem read]
code_addr : 000000000400c1b7
mem_addr : 00000000beef7470
size : 4
data : 805b0204
[.mem read]
code_addr : 000000000400c1ba
mem_addr : 0000000004023550
size : 4
data : 2f040000](https://image.slidesharecdn.com/lineandintertrustsecuritysummit08-170720090822/75/Practical-attacks-on-commercial-white-box-cryptography-solutions-16-2048.jpg)