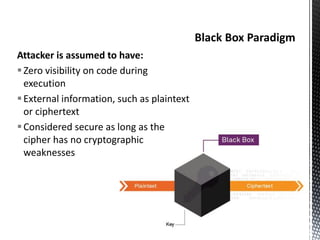
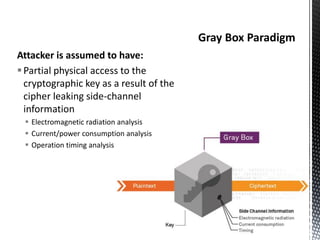
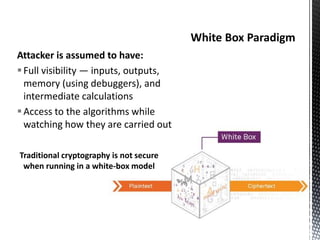
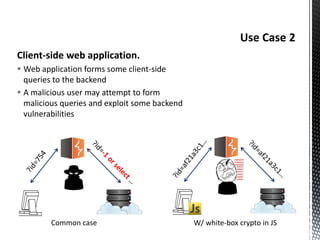
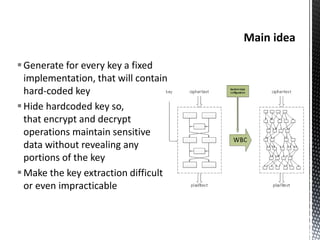
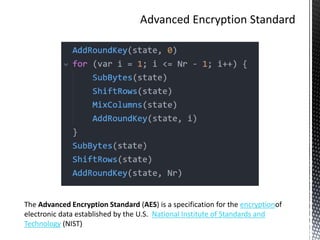
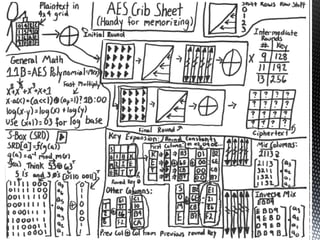
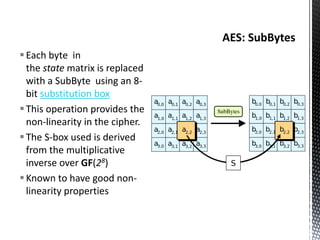
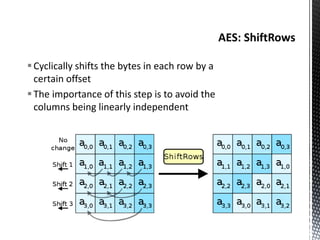
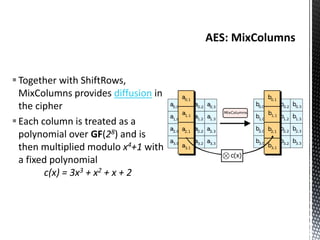
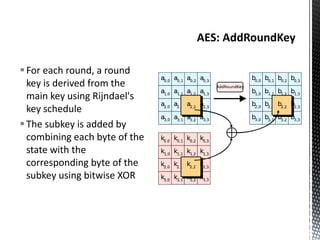
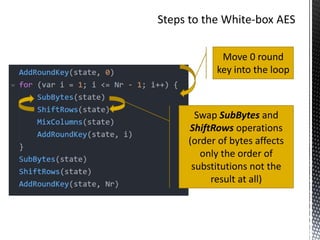
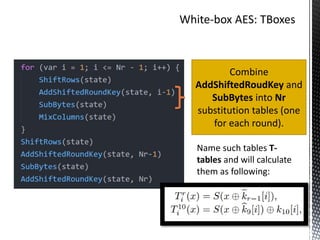
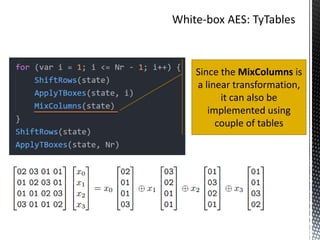
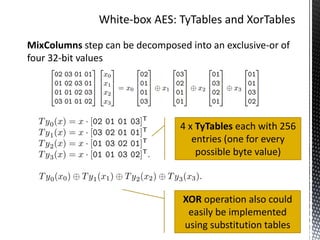
The document discusses the vulnerabilities in traditional cryptography when utilized in a white-box model, highlighting various attack methods such as side-channel information leakage and physical access to keys. It focuses on the Advanced Encryption Standard (AES), explaining its structure, transformations, and the creation of substitution tables for enhanced security. Additionally, it references resources for tutorials and implementations of white-box AES and discusses implications for digital rights management systems.