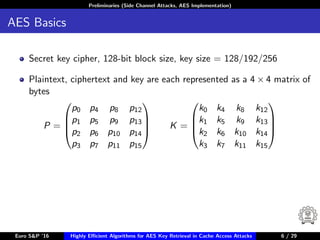
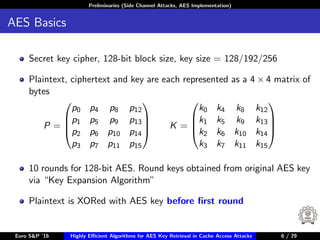
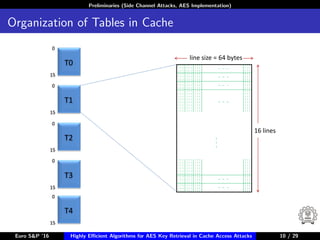
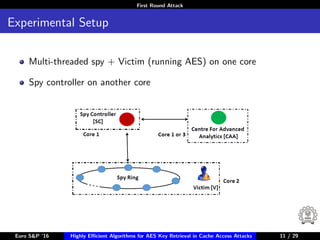
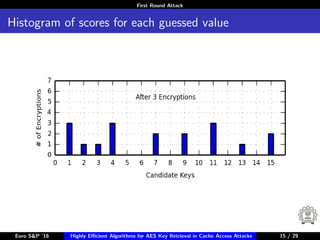
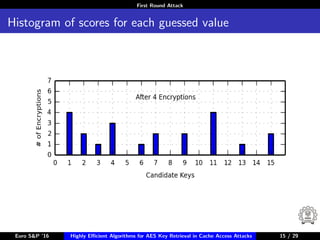
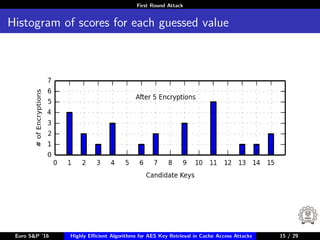
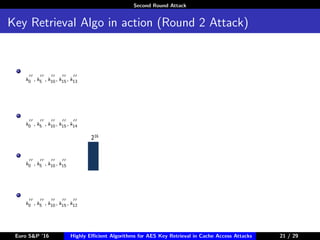
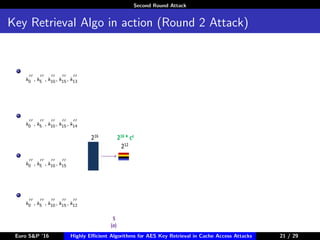
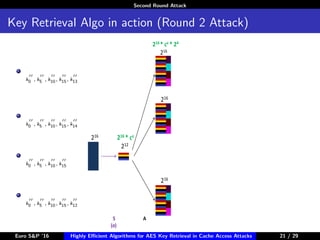
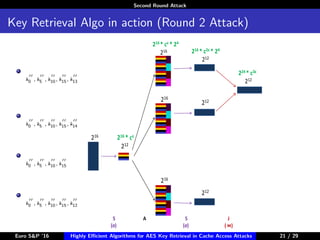
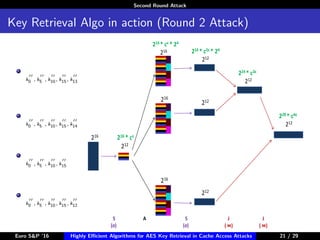
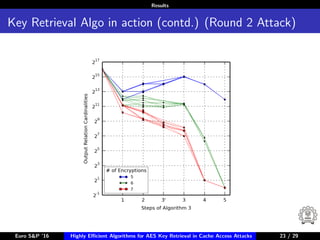
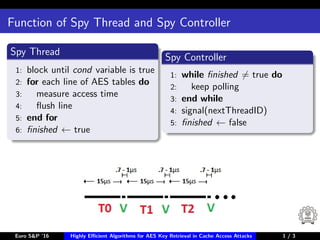
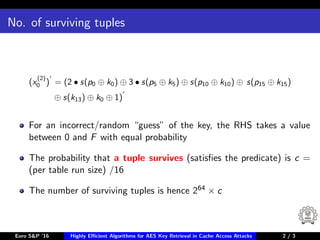
The document describes algorithms for retrieving the 128-bit AES encryption key from cache access patterns. It outlines preliminaries on side channel attacks, AES implementation and operations. It then presents a first round attack and second round attack to retrieve the key from known plaintext/ciphertext blocks and corresponding cache access patterns of table elements during AES encryption/decryption. Evaluation results and limitations/extensions are also discussed.