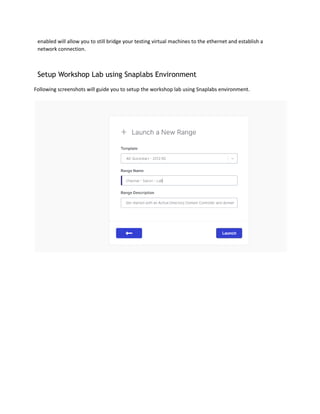
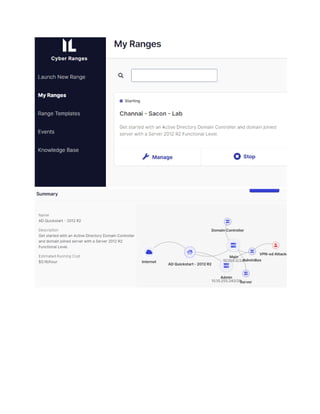
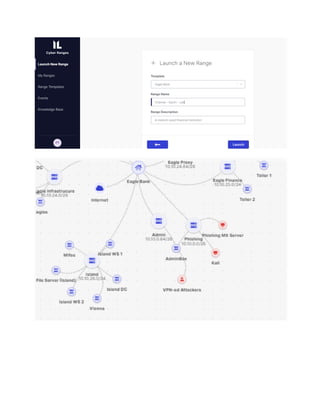
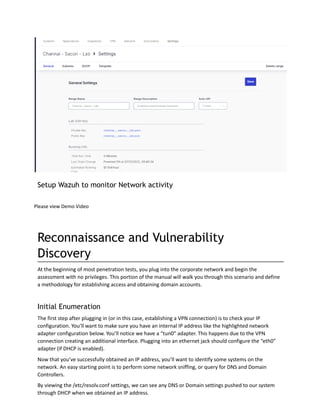
The document outlines the lab manual for a purple teaming workshop at Sacon 2022, focusing on penetration testing and red team training. It provides a comprehensive overview of the workshop's features, methodologies, prerequisites, tools, and the connection process, emphasizing the realistic simulation of a corporate network and various technical vulnerabilities. The goal is to equip participants with essential skills for performing effective network penetration tests in real-world environments.