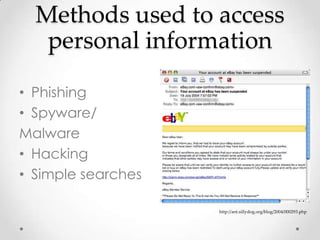
This document discusses protecting personal privacy and securing online information. It outlines how personal information can be disclosed on many websites and used for identity theft or other crimes. Simple steps are recommended to help protect privacy such as using strong passwords, updating security programs, and installing antivirus software. The document also notes that while identity theft is punishable by law, apprehending violators can be difficult.