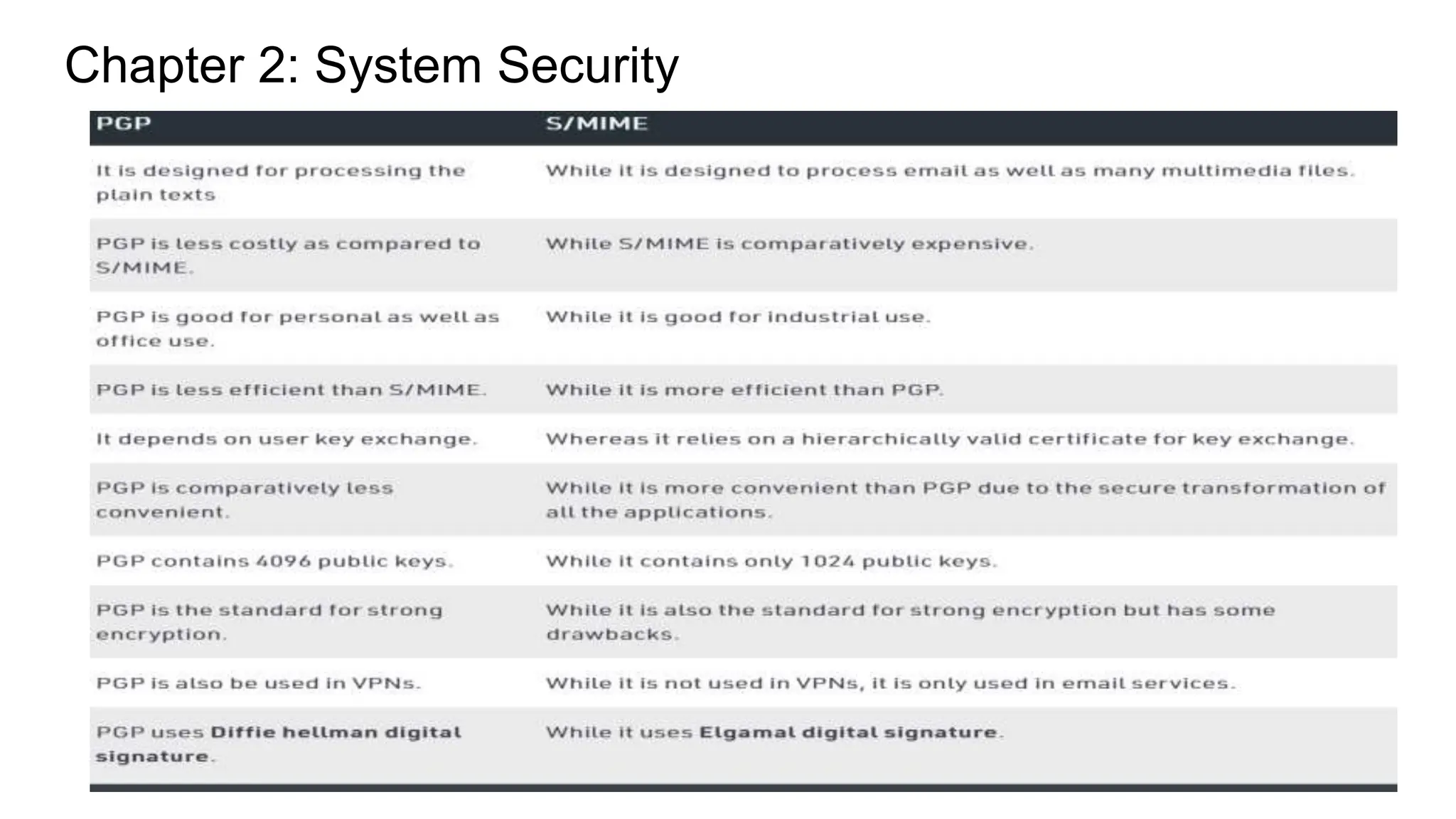
The document outlines various aspects of cybersecurity with a focus on system and application security across multiple modules. It discusses secure operating systems, security controls, information security models, and practical applications like desktop and email security. It emphasizes the importance of using encryption, following security protocols, and implementing various protective measures to safeguard data and systems.