The document provides an overview of industrial security management. It discusses:
- The course covers security measures like asset protection, loss prevention, security surveys, and risk assessment to comply with Philippine laws on private security.
- It is a 3-unit course for criminology students interested in careers in security.
- The document then provides historical background on security, including private security forces in ancient times, and the development of private security organizations in the USA and Philippines.
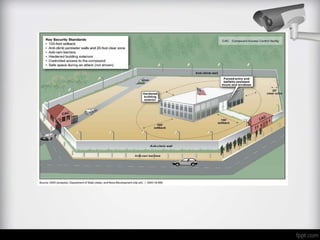
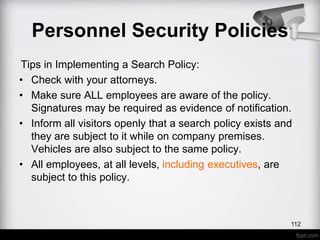
- It defines important security terms and discusses the three dimensions of security - physical, personnel, and information security. It focuses on physical security and barriers as the first line of defense.