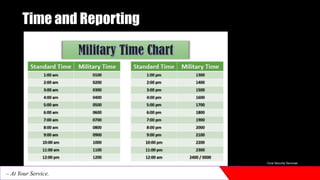
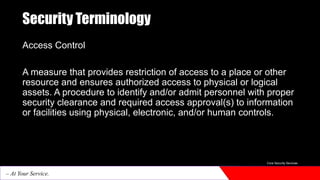
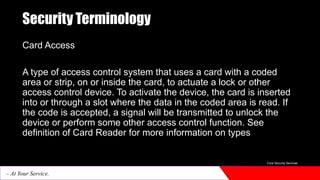
The document provides an introduction to physical security. It discusses how physical security aims to create secure environments through layers of defense like physical barriers, access control systems, surveillance technologies, security personnel, and emergency response protocols. These measures are used to deter threats, detect and respond to incidents, and mitigate impacts. Physical security is important for protecting assets, infrastructure, and individuals from unauthorized access and threats.