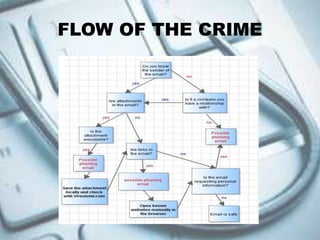
This document discusses phishing and how it works. It defines phishing as sending fraudulent emails pretending to be a legitimate company to trick users into revealing private information like passwords, credit cards, or bank details. The document includes a flow chart that color codes safe and dangerous email elements, advising users to check attachments from unknown senders online before opening. It lists the typical steps of a phishing attack, such as embedding links to fake websites asking for sensitive data, installing malware via attachments to steal information, spoofing the sender address to appear trustworthy, and impersonating company vendors over the phone.