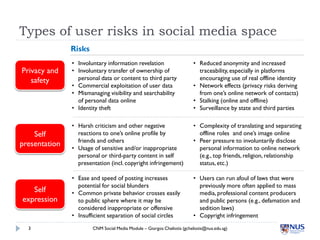
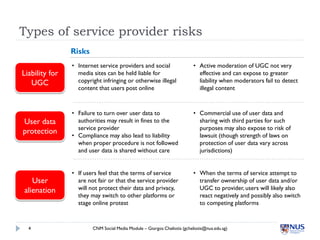
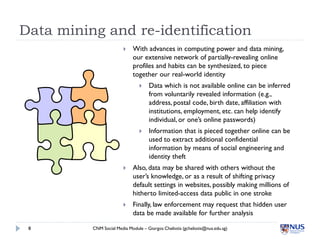
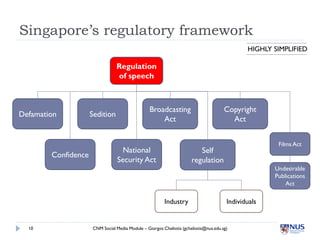
Social media poses several privacy and safety risks to users. Some key risks include involuntary sharing of personal information, commercial exploitation of user data, identity theft, and stalking. Users must also be careful of how they present themselves online to avoid issues like harsh criticism, inappropriate sharing of sensitive content, and legal issues from sharing content like copyrighted material. Service providers also face risks, including liability for illegal user-generated content and how they handle and protect user data. Proper privacy settings and awareness of these issues are important for safe social media use.