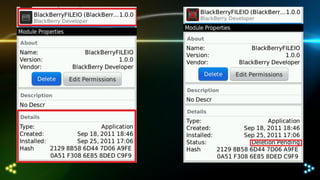
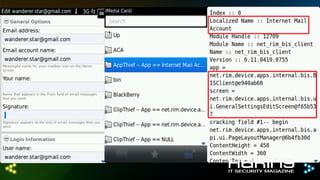
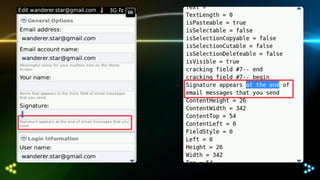
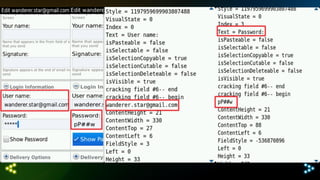
The document discusses differences in how integration features affect the security sandbox on BlackBerry devices. It notes that BlackBerry evaluates every application request to access device capabilities. However, malware boundaries can become unclear as BlackBerry handles technologies like native apps, third-party apps like Android and iOS, each with different controls through sandboxes, permissions, and device/MDM security features. Compliance standards also bring useless recommendations that are less extensive than mobile device management (MDM) features. The document outlines the various capabilities controlled on BlackBerry, Android, and iOS platforms and notes issues like useless solutions, GUI exploitation on older BlackBerry devices, and conclusions regarding oversimplified security controls through general permissions rather than concrete permissions.

![[ Yury Chemerkin ]
www.linkedin.com/in/yurychemerkin
http://sto-strategy.com
Experienced in :
Reverse Engineering & AV
Software Programming & Documentation
Mobile Security and MDM
Cyber Security & Cloud Security
Compliance & Transparency
and Security Writing
Hakin9 Magazine, PenTest Magazine, eForensics Magazine,
Groteck Business Media
Participation at conferences
InfoSecurityRussia, NullCon, CONFidence, PHDays
CYBERCRIME FORUM, Cyber Intelligence Europe/Intelligence-Sec
ICITST, CyberTimes, ITA, I-Society
yury.chemerkin@gmail.com](https://image.slidesharecdn.com/28pdf-29-20yury-chemerkin-athcon-2013-140202131816-phpapp02/85/Pdf-yury-chemerkin-_ath_con_2013-2-320.jpg)