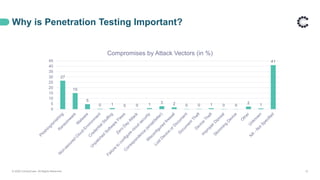
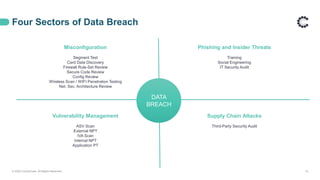
The document discusses a webinar on penetration testing basics hosted by ControlCase, highlighting its role as a compliance partner in IT. It details the importance of penetration testing for enhancing security posture, preventing data breaches, and complying with regulations. ControlCase offers comprehensive compliance services, including its proprietary tools and a partnership approach to simplify compliance while serving over 1,000 clients globally.