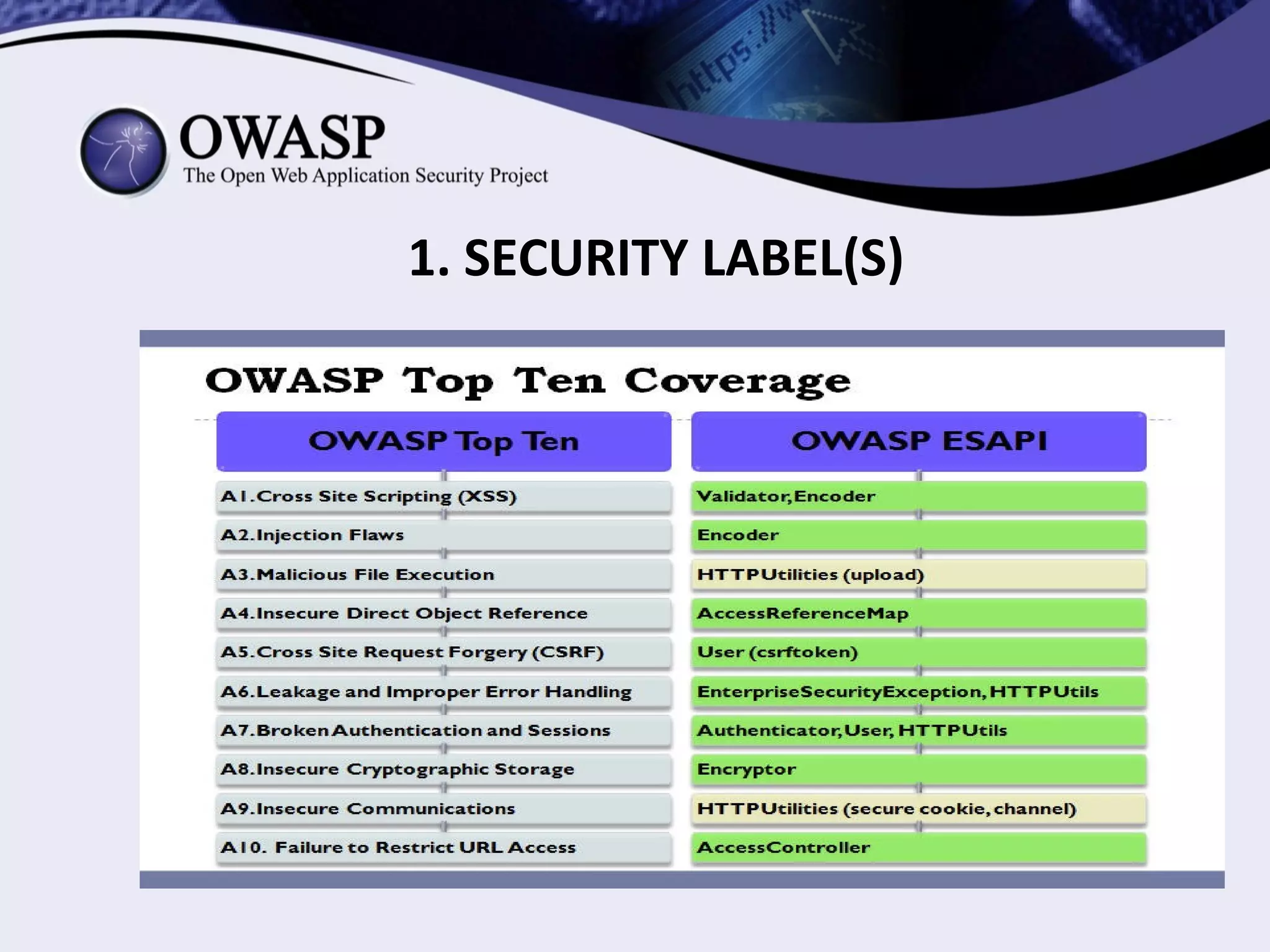
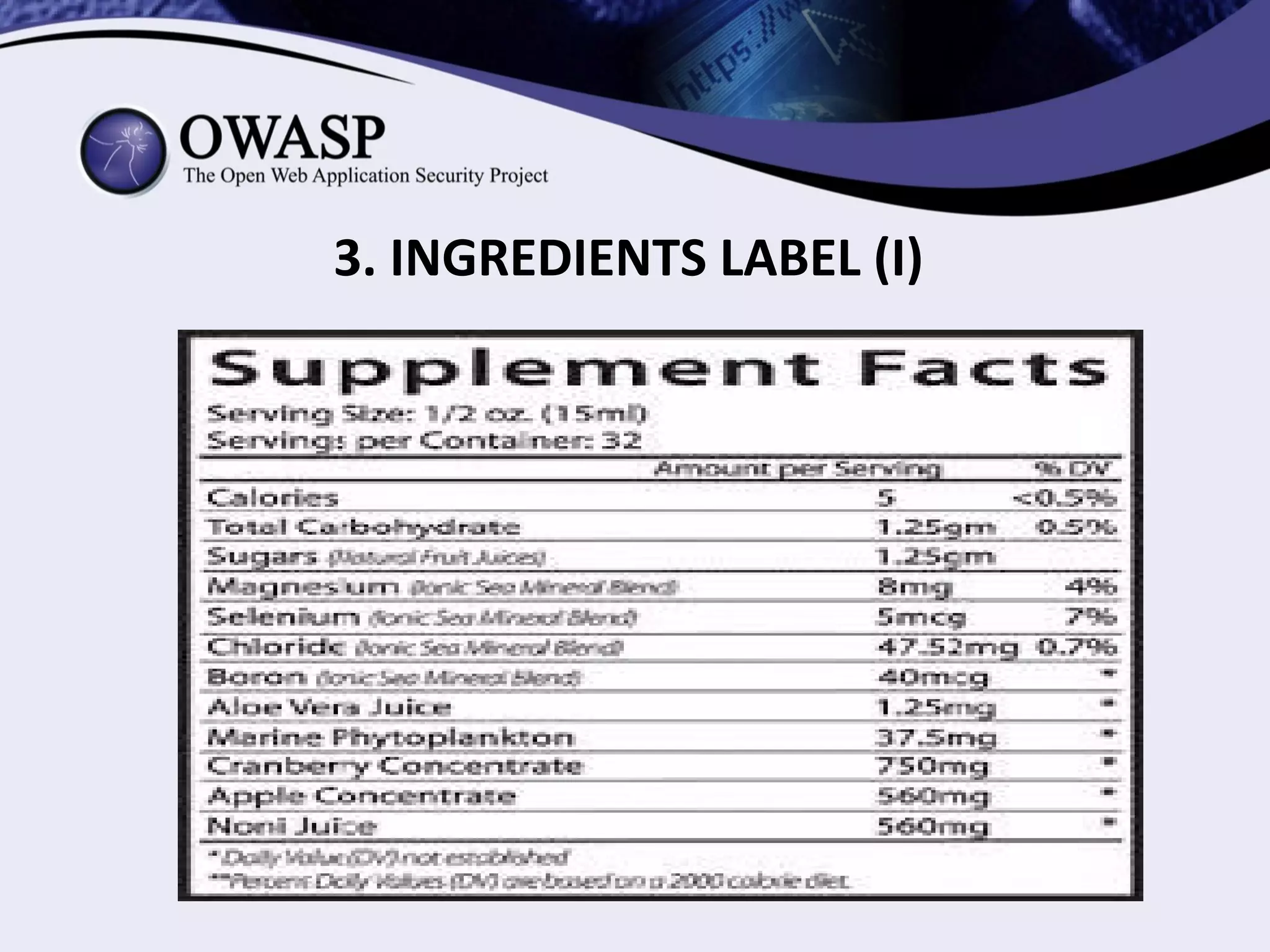
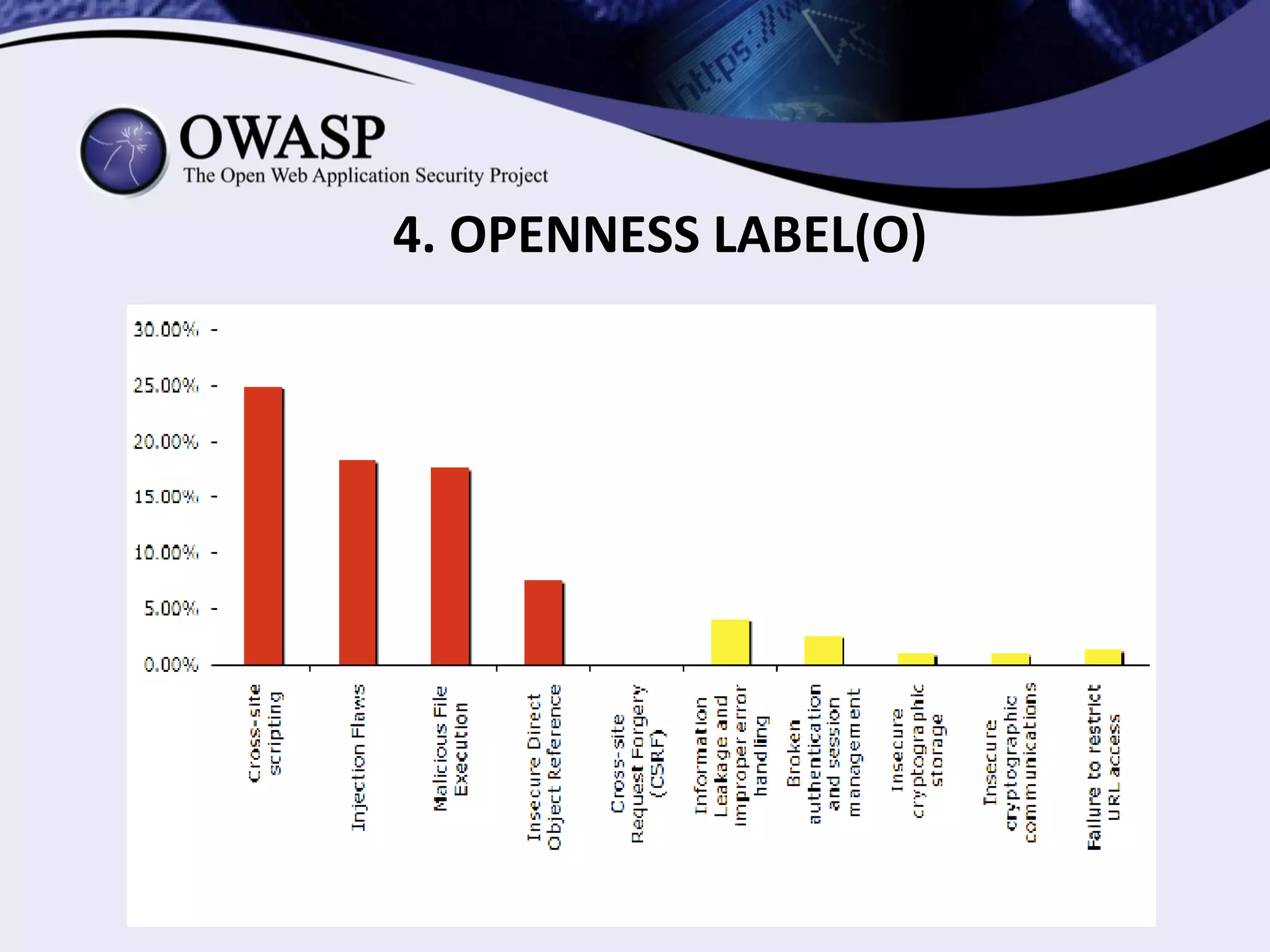
(1) The document proposes an OWASP security labeling system project to provide labels for software indicating its security, privacy, transparency, and openness. (2) The labels would be in the form of logos and clauses added to software licenses and policies. (3) The project aims to make security more visible to users and incentivize developers to share vulnerabilities.