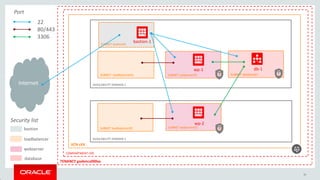
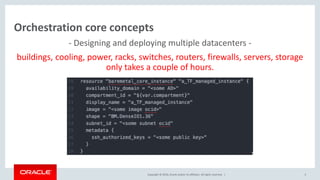
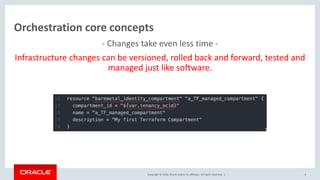
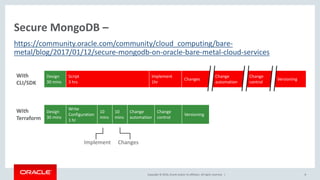
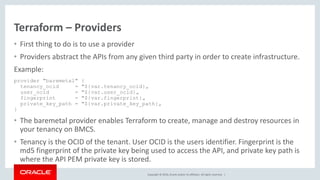
Oracle's documentation discusses the use of Terraform as a powerful orchestration tool for managing cloud infrastructure, enabling automation and lifecycle management across various cloud services without requiring new tools for existing users. It emphasizes the concept of infrastructure as code (IaC), allowing users to define and manage infrastructure through code, and highlights its benefits such as version control, quick changes, and compatibility with existing tools. Furthermore, the document outlines support and integration options for customers using the Oracle Bare Metal Cloud Services (BMCS) Terraform provider.













![Copyright © 2016, Oracle and/or its affiliates. All rights reserved. |
HCL – Basic Terraform .tf Format
• Terraform configuration is written into files named .tf files.
• It is based on the HashiCorp Configuration Language
(HCL) https://github.com/hashicorp/hcl
• JSON is supported for code generation purposes.
• Most of the configuration takes the form:
keyword1 "some_name" {
key = "value„
nested {
key = "value'
}
}
{
"keyword1": [
{
"some_name": [
{
"key": "value",
"nested": [
{
"key": "value"
}
]
}
]
}
]
}](https://image.slidesharecdn.com/ociterraform-171215153105/85/Oracle-Cloud-Infrastruktura-jako-kod-20-320.jpg)
![Copyright © 2016, Oracle and/or its affiliates. All rights reserved. |
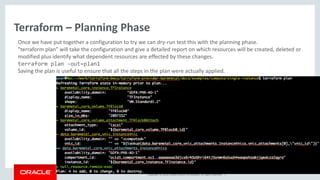
Terraform – Resources
Resources
Once a provider is configured we can start using that providers resources.
With the BMCS baremetal provider, we can start creating instances, block and object storage, networks, etc.
The following example starts an instance:
resource "baremetal_core_instance" "TFInstance" {
availability_domain = "${lookup(data.baremetal_identity_availability_domains.ADs.availability_domains[var.AD
- 1],"name")}"
compartment_id = "${var.compartment_ocid}"
display_name = "TFInstance"
hostname_label = "instance1"
image = "${lookup(data.baremetal_core_images.OLImageOCID.images[0], "id")}"
shape = "${var.InstanceShape}"
subnet_id = "${var.SubnetOCID}"
metadata {
ssh_authorized_keys = "${var.ssh_public_key}"
user_data = "${base64encode(file(var.BootStrapFile))}"
}
}
component provider type name](https://image.slidesharecdn.com/ociterraform-171215153105/85/Oracle-Cloud-Infrastruktura-jako-kod-22-320.jpg)

![Copyright © 2016, Oracle and/or its affiliates. All rights reserved. |
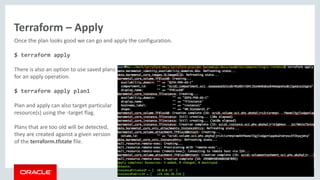
Terraform – Outputs
Terraform can be directed to display the variables that are generated dynamically as pat of the process of creating the
infrastructure.
For example, after a run we might want to see the public ip of the host:
$ cat outputs.tf
output "InstancePrivateIP" { value = ["${data.baremetal_core_vnic.InstanceVnic.private_ip_address}"]}
output "InstancePublicIP" { value = ["${data.baremetal_core_vnic.InstanceVnic.public_ip_address}"]}
After a terraform apply:
Apply complete! Resources: 4 added, 0 changed, 0 destroyed.
State path:
Outputs:
InstancePrivateIP = [ 10.0.0.10 ]
InstancePublicIP = [ 129.146.3.173]
Outputs are often used to facilitate interaction with other infrastructure tools. Terraform show (human readable) and
terraform.tfstate file also store these outputs.](https://image.slidesharecdn.com/ociterraform-171215153105/85/Oracle-Cloud-Infrastruktura-jako-kod-28-320.jpg)
![Copyright © 2016, Oracle and/or its affiliates. All rights reserved. |
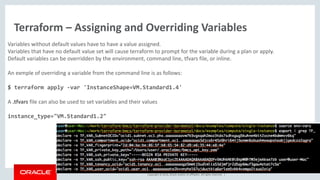
Terraform – Provisioners
Terraform can also integrate with provisioners like Chef, puppet, Ansible, shells scripts.
An example below is using a provisioner to remote-exec a command to touch a file.
$ cat remote-exec.tf
resource "null_resource" "remote-exec" {
depends_on = ["baremetal_core_instance.TFInstance"]
provisioner "remote-exec" {
connection {
agent = false
timeout = "10m"
host = "${data.baremetal_core_vnic.InstanceVnic.public_ip_address}"
user = "opc"
private_key = "${var.ssh_private_key}"
}
inline = [
"touch ~/IMadeAFile.Right.Here",
]
}
}](https://image.slidesharecdn.com/ociterraform-171215153105/85/Oracle-Cloud-Infrastruktura-jako-kod-29-320.jpg)